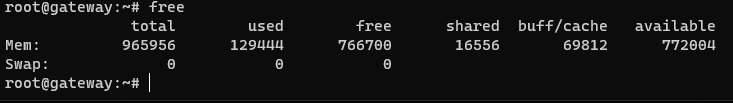
I'm seeing dnsmasq getting hit by the oom-killer cleanup
proc, but I'm not sure why. According to the logs, there's physical free RAM when it's called.
Can anyone suggest a way to track down this leak?
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.833478] sh invoked oom-killer: gfp_mask=0xcc0(GFP_KERNEL), order=1, oom_score_adj=0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.841683] CPU: 0 PID: 2334 Comm: sh Not tainted 5.10.64 #0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.847439] Stack : 003000140000091e 0000000000000008 b61482848ffe9f11 b61482848ffe9f11
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.855558] 0000000000000000 8000000006e737e0 ffffffff818a3150 8000000006e736b0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.863674] 0000000000000000 c0000000ffffefff 0000000000000003 ffffffffffffffea
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.871790] 0000000000000010 ffffffff814daee0 0000000000000001 8000000006e736d6
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.879906] fffe000000000000 0000000000000001 0000000000000000 ffffffff818a0000
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.888022] ffffffff81a49310 8000000006e73b98 0000000000001000 ffffffff8199b5b0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.896137] 00000000fffffffe ffffffff81521ba8 0000000000000000 ffffffff81b90000
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.904252] 8000000006e70000 8000000006e737e0 0000000000000001 ffffffff814c16c0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.912368] 0000000000000000 ffffffff814c15cc 0000000000000000 ffffffff818a3150
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.920483] 0000000000000000 ffffffff81117dc8 0000000000000000 0000000000000000
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.928598] ...
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.931139] Call Trace:
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.933688] [<ffffffff81117dc8>] show_stack+0x30/0x100
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.938932] [<ffffffff814c16c0>] dump_stack+0xa0/0xd0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.944083] [<ffffffff81229c80>] dump_header+0x50/0x1d0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.949406] [<ffffffff8122a54c>] oom_kill_process+0x20c/0x218
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.955250] [<ffffffff8122af98>] out_of_memory+0x218/0x3a8
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.960837] [<ffffffff812754a8>] __alloc_pages_slowpath.constprop.0+0xa98/0xcd8
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.968247] [<ffffffff81275938>] __alloc_pages_nodemask+0x250/0x280
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.974612] [<ffffffff81275984>] __get_free_pages+0x1c/0x78
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.980284] [<ffffffff811261c8>] pgd_alloc+0x18/0x58
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.985346] [<ffffffff8113183c>] mm_init+0xec/0x1f8
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.990320] [<ffffffff81132344>] dup_mm+0xa4/0x488
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393372.995208] [<ffffffff811331dc>] copy_process+0x7ec/0x1568
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.000791] [<ffffffff81134008>] kernel_clone+0x58/0x358
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.006200] [<ffffffff8113451c>] sys_fork+0x4c/0x58
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.011174] [<ffffffff811204e8>] syscall_common+0x34/0x58
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.016670]
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.018432] Mem-Info:
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.020967] active_anon:5713 inactive_anon:17821 isolated_anon:0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.020967] active_file:978 inactive_file:528 isolated_file:0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.020967] unevictable:0 dirty:0 writeback:0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.020967] slab_reclaimable:546 slab_unreclaimable:3156
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.020967] mapped:1073 shmem:8092 pagetables:160 bounce:0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.020967] free:98287 free_pcp:59 free_cma:0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.053451] Node 0 active_anon:22868kB inactive_anon:71288kB active_file:3860kB inactive_file:2160kB unevictable:0kB isolated(anon):0kB isolated(file):0kB mapped:4272kB dirty:0kB writeback:0kB shmem:32368kB writeback_tmp:0kB kernel_stack:1088kB all_unreclaimable? no
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.077295] DMA32 free:393376kB min:16384kB low:20480kB high:24576kB reserved_highatomic:0KB active_anon:22868kB inactive_anon:71324kB active_file:3860kB inactive_file:2360kB unevictable:0kB writepending:0kB present:1010540kB managed:965956kB mlocked:0kB pagetables:596kB bounce:0kB free_pcp:240kB local_pcp:236kB free_cma:0kB
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.106332] lowmem_reserve[]: 0 0 0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.110036] DMA32: 98336*4kB (UME) 0*8kB 6*16kB (U) 0*32kB 0*64kB 0*128kB 0*256kB 0*512kB 0*1024kB 0*2048kB 0*4096kB = 393440kB
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.121810] 9596 total pagecache pages
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.125678] 0 pages in swap cache
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.129107] Swap cache stats: add 0, delete 0, find 0/0
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.134435] Free swap = 0kB
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.137409] Total swap = 0kB
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.140394] 252635 pages RAM
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.143368] 0 pages HighMem/MovableOnly
Mon Oct 18 01:53:27 2021 kern.warn kernel: [393373.147296] 11146 pages reserved
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.150625] Tasks state (memory values in pages):
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.155424] [ pid ] uid tgid total_vm rss pgtables_bytes swapents oom_score_adj name
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.164195] [ 537] 81 537 358 73 32768 0 0 ubusd
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.172524] [ 538] 0 538 259 8 28672 0 0 askfirst
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.181118] [ 572] 0 572 290 9 24576 0 0 urngd
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.189447] [ 815] 514 815 357 44 36864 0 0 logd
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.197809] [ 816] 0 816 386 22 32768 0 0 logread
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.206406] [ 868] 0 868 619 99 36864 0 0 rpcd
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.214631] [ 1087] 0 1087 312 13 28672 0 0 dropbear
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.223226] [ 1197] 0 1197 511 71 32768 0 0 netifd
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.231641] [ 1381] 0 1381 393 13 24576 0 0 udhcpc
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.240059] [ 1395] 0 1395 412 32 32768 0 0 odhcpd
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.248469] [ 1647] 0 1647 974 173 40960 0 0 uhttpd
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.256845] [ 2259] 0 2259 393 14 28672 0 0 ntpd
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.265089] [ 2334] 0 2334 481 318 36864 0 0 sh
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.273159] [ 2876] 0 2876 1510 524 36864 0 0 tcpdump
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.281665] [ 28356] 453 28356 15547 15040 151552 0 0 dnsmasq
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.290170] oom-kill:constraint=CONSTRAINT_NONE,nodemask=(null),cpuset=/,mems_allowed=0,global_oom,task_memcg=/,task=dnsmasq,pid=28356,uid=453
Mon Oct 18 01:53:27 2021 kern.err kernel: [393373.303138] Out of memory: Killed process 28356 (dnsmasq) total-vm:62188kB, anon-rss:59076kB, file-rss:1084kB, shmem-rss:0kB, UID:453 pgtables:148kB oom_score_adj:0
Mon Oct 18 01:53:27 2021 kern.info kernel: [393373.335060] oom_reaper: reaped process 28356 (dnsmasq), now anon-rss:0kB, file-rss:0kB, shmem-rss:0kB
Mon Oct 18 01:53:35 2021 daemon.info dnsmasq[32620]: started, version 2.86 cachesize 150