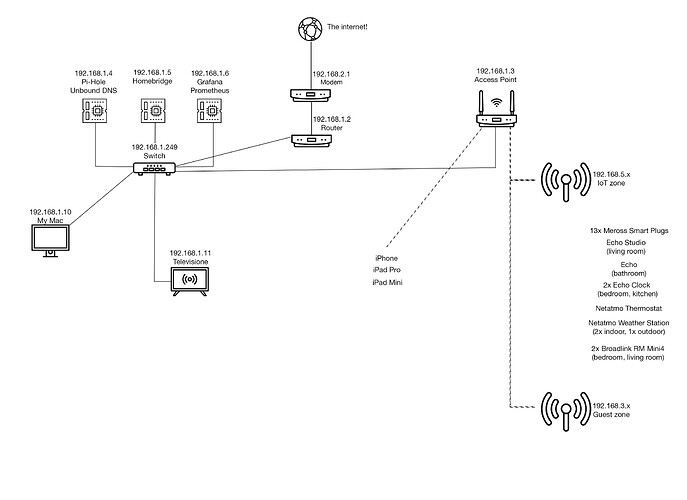
Yes this is what I was saying, if they don't have an IP, how they can talk? I'll try the reboot when they are inside the lan and I will check if they get a valid
[quote="spence, post:19, topic:149133"]
please do a capture on the WAX206 with this:
tcpdump -ennv -i br-lan
and verify that the IP address on the WAX206, 192.168.1.3 , shows up as a source in some packets[/quote]
Yes but it shows up only in the (current) SSH session with the Mac I'm using, nothing else...
17:48:40.904910 80:cc:9c:eb:8d:37 > f8:e4:3b:a3:5f:54, ethertype IPv4 (0x0800), length 1326: (tos 0x4a,ECT(0), ttl 64, id 25025, offset 0, flags [DF], proto TCP (6), length 1312)
192.168.1.3.22 > 192.168.1.10.50721: Flags [P.], cksum 0x8870 (incorrect -> 0x4fbc), seq 20940704:20941964, ack 13177, win 1002, options [nop,nop,TS val 3344280471 ecr 547442437], length 1260
It's what I'm trying to say, Avahi is not working as expected, and I think the host inside 'iot' interface are working only because there's the Avahi istance running on Homebridge, because all the queries are sent to them but from them
I see only traffic from other sources like smart plugs/TV/etcc..and the Homebridge server where Avahi is running and is running fine:
Homebridge server
192.168.1.5.5353 > 224.0.0.251.5353: 0 PTR (QM)? _hap._tcp.local. (33)
18:10:39.713126 e4:5f:01:b3:3a:8d > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 1248: (tos 0x0, ttl 255, id 38789, offset 0, flags [DF], proto UDP (17), length 1234)
Random iot device
192.168.1.109.5353 > 224.0.0.251.5353: 0*- [0q] 3/0/2 Giulios-iPhone.local. (Cache flush) AAAA fe80::109a:cc7a:4eaf:87d5, Giulios-iPhone.local. (Cache flush) A 192.168.1.109, Giulios-iPhone.local. (Cache flush) AAAA fd91:e81d:cbd3:4623:1076:22e4:f83b:8ceb (153)
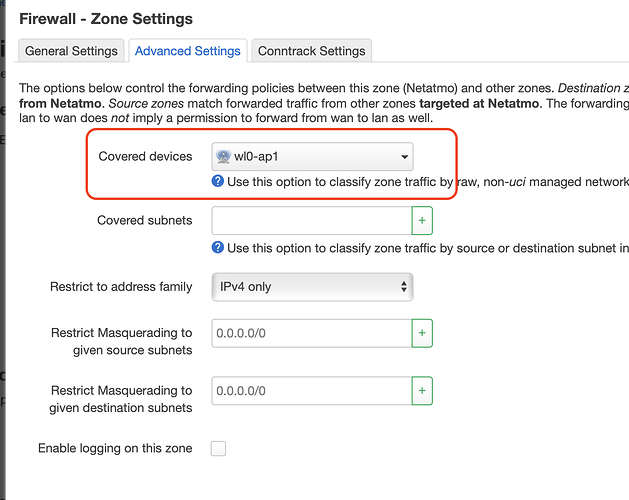
About the rule... hmmm but all the traffic can already go from 'lan' to 'netatmo', what rule I can try to add other than this that is already in firewall?
config rule
option name 'LAN to Netatmo'
option src 'lan'
option target 'ACCEPT'
option dest 'Netatmo'
list proto 'all'
I also have to go out, I'll think on it!
Thanks!
EDIt:
Uhm, Avahi is running as I've always noticed but I noticed only now that assigned to the useless 'nobody' user! This could be the issue (?) no permissions?
19252 nobody 2684 S avahi-daemon: running [WAX206.local]