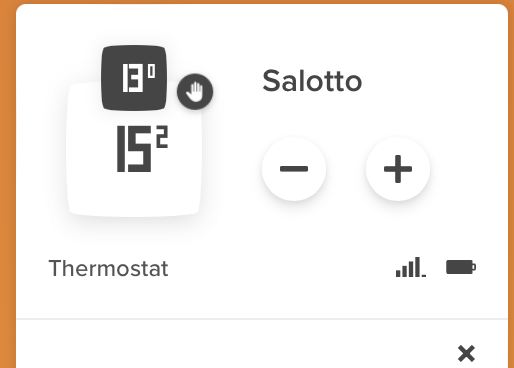
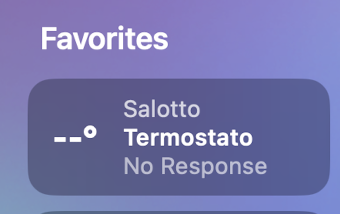
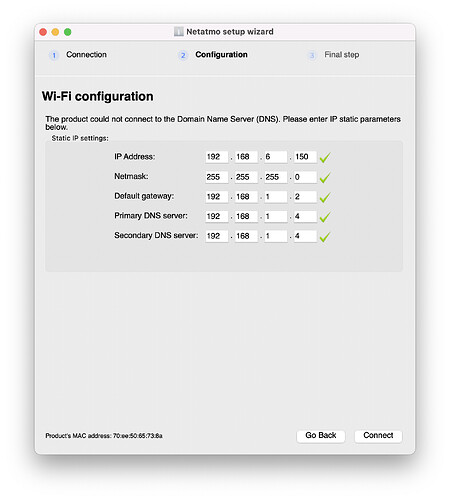
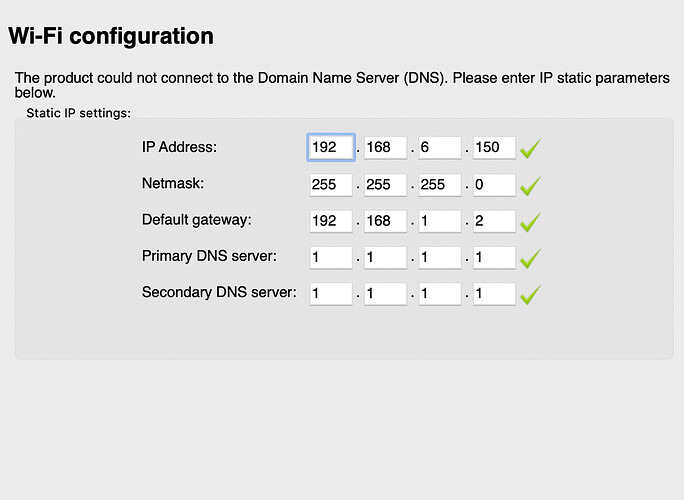
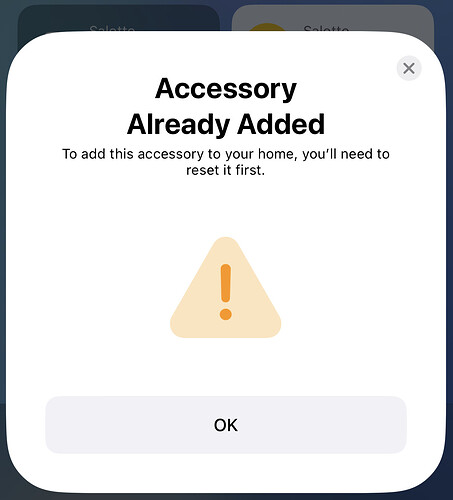
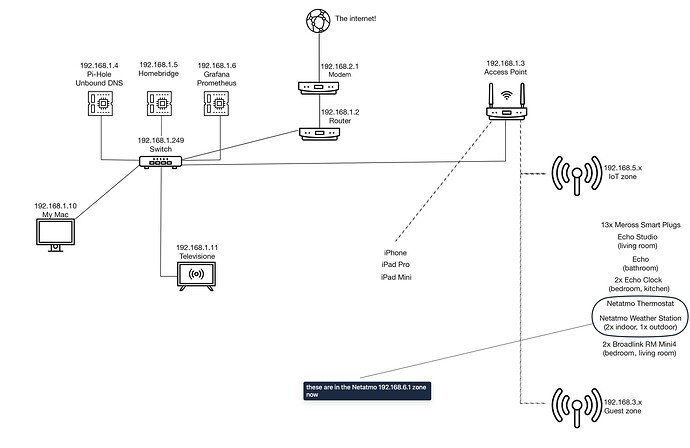
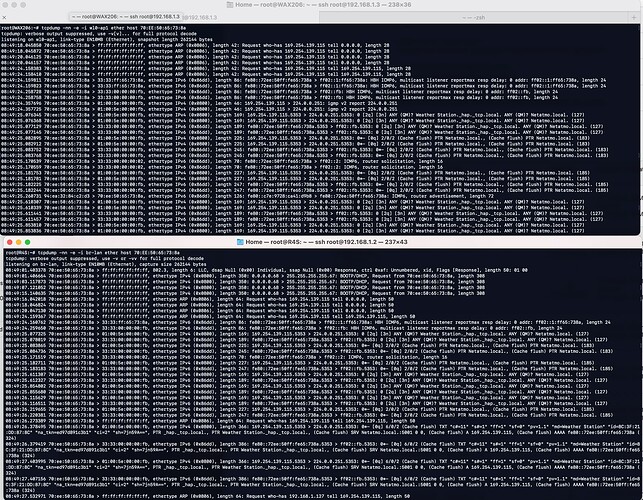
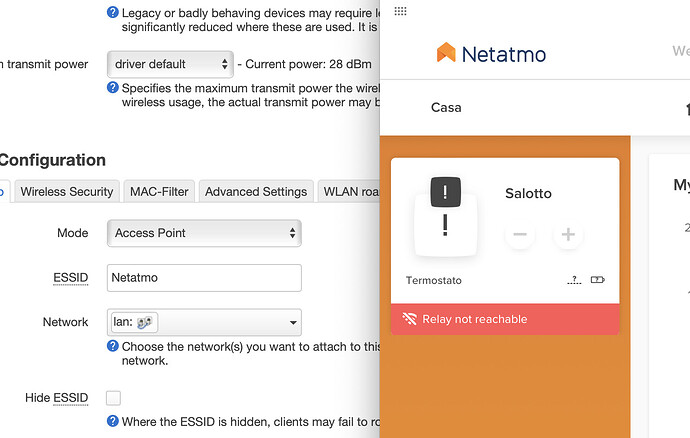
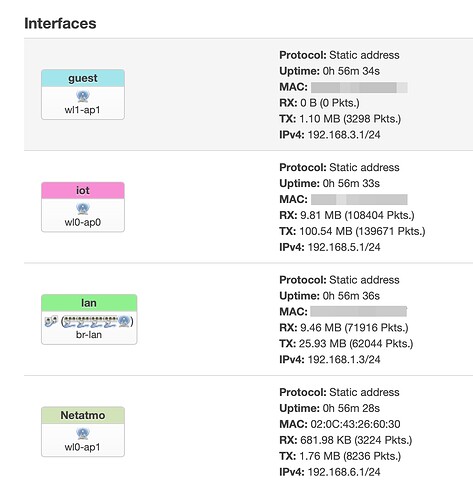
Yes yes but when they are inside the main LAN they were working always! Probably the devices keeps the old DHCP settings
Yes but the DHCP server was working also before. The devices sometimes are keeping their static addresses, this is why I have to reconfigure them.
Summary
root@WAX206:~# tcpdump -nn -e -i wl0-ap1 ether host 70:ee:50:6d:c6:80
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on wl0-ap1, link-type EN10MB (Ethernet), snapshot length 262144 bytes
19:07:10.554730 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, 802.3, length 6: LLC, dsap Null (0x00) Individual, ssap Null (0x00) Response, ctrl 0xaf: Unnumbered, xid, Flags [Response], length 6: 01 00
19:07:12.444822 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype IPv4 (0x0800), length 350: 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 70:ee:50:6d:c6:80, length 308
19:07:12.444853 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype IPv4 (0x0800), length 350: 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 70:ee:50:6d:c6:80, length 308
19:07:12.445932 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 342: 192.168.6.1.67 > 192.168.6.247.68: BOOTP/DHCP, Reply, length 300
19:07:12.448932 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype IPv4 (0x0800), length 350: 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 70:ee:50:6d:c6:80, length 308
19:07:12.448964 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype IPv4 (0x0800), length 350: 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 70:ee:50:6d:c6:80, length 308
19:07:12.450948 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 342: 192.168.6.1.67 > 192.168.6.247.68: BOOTP/DHCP, Reply, length 300
19:07:12.452514 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.247 tell 0.0.0.0, length 28
19:07:12.452542 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.247 tell 0.0.0.0, length 28
19:07:12.945743 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.247 tell 0.0.0.0, length 28
19:07:12.945782 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.247 tell 0.0.0.0, length 28
19:07:12.946910 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.247 tell 0.0.0.0, length 28
19:07:12.946930 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.247 tell 0.0.0.0, length 28
19:07:13.445868 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.247 tell 192.168.6.247, length 28
19:07:13.445912 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.247 tell 192.168.6.247, length 28
19:07:13.446754 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 46: 192.168.6.247 > 224.0.0.251: igmp v2 report 224.0.0.251
19:07:13.446782 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 86: fe80::72ee:50ff:fe6d:c680 > ff02::fb: HBH ICMP6, multicast listener reportmax resp delay: 0 addr: ff02::fb, length 24
19:07:13.446797 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 46: 192.168.6.247 > 224.0.0.251: igmp v2 report 224.0.0.251
19:07:13.446797 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 86: fe80::72ee:50ff:fe6d:c680 > ff02::fb: HBH ICMP6, multicast listener reportmax resp delay: 0 addr: ff02::fb, length 24
19:07:13.448000 70:ee:50:6d:c6:80 > 33:33:ff:6d:c6:80, ethertype IPv6 (0x86dd), length 86: fe80::72ee:50ff:fe6d:c680 > ff02::1:ff6d:c680: HBH ICMP6, multicast listener reportmax resp delay: 0 addr: ff02::1:ff6d:c680, length 24
19:07:13.448021 70:ee:50:6d:c6:80 > 33:33:ff:6d:c6:80, ethertype IPv6 (0x86dd), length 86: fe80::72ee:50ff:fe6d:c680 > ff02::1:ff6d:c680: HBH ICMP6, multicast listener reportmax resp delay: 0 addr: ff02::1:ff6d:c680, length 24
19:07:13.452195 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.1 tell 192.168.6.247, length 28
19:07:13.452214 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.1 tell 192.168.6.247, length 28
19:07:13.452243 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype ARP (0x0806), length 42: Reply 192.168.6.1 is-at 02:0c:43:26:60:30, length 28
19:07:13.946537 70:ee:50:6d:c6:80 > 33:33:00:00:00:02, ethertype IPv6 (0x86dd), length 70: fe80::72ee:50ff:fe6d:c680 > ff02::2: ICMP6, router solicitation, length 16
19:07:13.946581 70:ee:50:6d:c6:80 > 33:33:00:00:00:02, ethertype IPv6 (0x86dd), length 70: fe80::72ee:50ff:fe6d:c680 > ff02::2: ICMP6, router solicitation, length 16
19:07:14.947569 70:ee:50:6d:c6:80 > 33:33:00:00:00:02, ethertype IPv6 (0x86dd), length 70: fe80::72ee:50ff:fe6d:c680 > ff02::2: ICMP6, router solicitation, length 16
19:07:14.947609 70:ee:50:6d:c6:80 > 33:33:00:00:00:02, ethertype IPv6 (0x86dd), length 70: fe80::72ee:50ff:fe6d:c680 > ff02::2: ICMP6, router solicitation, length 16
19:07:15.338805 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 173: 192.168.6.247.5353 > 224.0.0.251.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:15.338829 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 173: 192.168.6.247.5353 > 224.0.0.251.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:15.339812 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 193: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:15.339848 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 278: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 3/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local., PTR _hap._tcp.local. (236)
19:07:15.339863 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 193: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:15.339864 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 278: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 3/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local., PTR _hap._tcp.local. (236)
19:07:15.340637 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 298: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 3/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local., PTR _hap._tcp.local. (236)
19:07:15.340658 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 298: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 3/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local., PTR _hap._tcp.local. (236)
19:07:15.442582 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 231: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:15.442612 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 231: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:15.443389 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 251: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:15.443406 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 251: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:15.846066 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 173: 192.168.6.247.5353 > 224.0.0.251.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:15.846094 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 173: 192.168.6.247.5353 > 224.0.0.251.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:15.846815 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 193: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:15.846837 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 193: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:15.946777 70:ee:50:6d:c6:80 > 33:33:00:00:00:02, ethertype IPv6 (0x86dd), length 70: fe80::72ee:50ff:fe6d:c680 > ff02::2: ICMP6, router solicitation, length 16
19:07:15.946816 70:ee:50:6d:c6:80 > 33:33:00:00:00:02, ethertype IPv6 (0x86dd), length 70: fe80::72ee:50ff:fe6d:c680 > ff02::2: ICMP6, router solicitation, length 16
19:07:16.136050 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 173: 192.168.6.247.5353 > 224.0.0.251.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:16.136084 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 173: 192.168.6.247.5353 > 224.0.0.251.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:16.136794 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 193: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:16.136817 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 193: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:16.396051 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 173: 192.168.6.247.5353 > 224.0.0.251.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:16.396087 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 173: 192.168.6.247.5353 > 224.0.0.251.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:16.397048 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 193: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:16.397072 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 193: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0 [2q] [3n] ANY (QM)? Netatmo Relay._hap._tcp.local. ANY (QM)? Netatmo Relay.local. (131)
19:07:16.496658 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 231: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:16.496695 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 231: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:16.497523 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 251: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:16.497546 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 251: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:16.639754 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 368: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:16.639792 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 368: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:16.640727 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 388: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:16.640748 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 388: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:17.454152 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.247 tell 192.168.6.1, length 28
19:07:17.455787 70:ee:50:6d:c6:80 > 02:0c:43:26:60:30, ethertype ARP (0x0806), length 42: Reply 192.168.6.247 is-at 70:ee:50:6d:c6:80, length 28
19:07:17.668639 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 368: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:17.668676 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 368: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:17.669609 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 388: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:17.669629 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 388: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:18.548651 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 231: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:18.548689 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 231: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:18.550070 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 251: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:18.550096 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 251: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 2/0/2 (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local. (189)
19:07:18.554221 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.1 tell 192.168.6.247, length 28
19:07:18.554243 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.1 tell 192.168.6.247, length 28
19:07:18.554285 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype ARP (0x0806), length 42: Reply 192.168.6.1 is-at 02:0c:43:26:60:30, length 28
19:07:18.659214 70:ee:50:6d:c6:80 > 02:0c:43:26:60:30, ethertype IPv4 (0x0800), length 80: 192.168.6.247.37123 > 192.168.6.1.53: 12122+ A? netcomv2.netatmo.net. (38)
19:07:18.661059 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 147: 192.168.6.1.53 > 192.168.6.247.37123: 12122 3/0/0 CNAME nv2.netatmo.net., CNAME nv2.trafficmanager.net., A 51.105.245.118 (105)
19:07:18.663724 70:ee:50:6d:c6:80 > 02:0c:43:26:60:30, ethertype IPv4 (0x0800), length 62: 192.168.6.247.56878 > 51.105.245.118.25050: Flags [S], seq 499896734, win 3000, options [mss 1000,nop,nop,nop,eol], length 0
19:07:18.701017 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 58: 51.105.245.118.25050 > 192.168.6.247.56878: Flags [S.], seq 2376679884, ack 499896735, win 64240, options [mss 1452], length 0
19:07:18.702397 70:ee:50:6d:c6:80 > 02:0c:43:26:60:30, ethertype IPv4 (0x0800), length 54: 192.168.6.247.56878 > 51.105.245.118.25050: Flags [.], ack 1, win 3000, length 0
19:07:18.741511 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 78: 51.105.245.118.25050 > 192.168.6.247.56878: Flags [P.], seq 1:25, ack 1, win 64240, length 24
19:07:18.743333 70:ee:50:6d:c6:80 > 02:0c:43:26:60:30, ethertype IPv4 (0x0800), length 108: 192.168.6.247.56878 > 51.105.245.118.25050: Flags [P.], seq 1:55, ack 25, win 2976, length 54
19:07:18.780246 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 54: 51.105.245.118.25050 > 192.168.6.247.56878: Flags [.], ack 55, win 64186, length 0
19:07:18.780980 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 62: 51.105.245.118.25050 > 192.168.6.247.56878: Flags [P.], seq 25:33, ack 55, win 64186, length 8
19:07:18.782493 70:ee:50:6d:c6:80 > 02:0c:43:26:60:30, ethertype IPv4 (0x0800), length 58: 192.168.6.247.56878 > 51.105.245.118.25050: Flags [P.], seq 55:59, ack 33, win 2968, length 4
19:07:18.867504 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 54: 51.105.245.118.25050 > 192.168.6.247.56878: Flags [.], ack 59, win 64182, length 0
19:07:18.868902 70:ee:50:6d:c6:80 > 02:0c:43:26:60:30, ethertype IPv4 (0x0800), length 86: 192.168.6.247.56878 > 51.105.245.118.25050: Flags [P.], seq 59:91, ack 33, win 2968, length 32
19:07:18.905994 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 54: 51.105.245.118.25050 > 192.168.6.247.56878: Flags [.], ack 91, win 64150, length 0
19:07:18.906052 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 78: 51.105.245.118.25050 > 192.168.6.247.56878: Flags [P.], seq 33:57, ack 91, win 64150, length 24
19:07:18.914671 70:ee:50:6d:c6:80 > 02:0c:43:26:60:30, ethertype IPv4 (0x0800), length 54: 192.168.6.247.56878 > 51.105.245.118.25050: Flags [.], ack 57, win 2944, length 0
19:07:19.720712 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 368: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:19.720749 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 368: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:19.721729 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 388: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:19.721751 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 388: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 6/0/2 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (326)
19:07:22.653606 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 526: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 8/0/4 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (484)
19:07:22.653645 70:ee:50:6d:c6:80 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 526: 192.168.6.247.5353 > 224.0.0.251.5353: 0*- [0q] 8/0/4 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (484)
19:07:22.654871 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 546: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 8/0/4 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (484)
19:07:22.654892 70:ee:50:6d:c6:80 > 33:33:00:00:00:fb, ethertype IPv6 (0x86dd), length 546: fe80::72ee:50ff:fe6d:c680.5353 > ff02::fb.5353: 0*- [0q] 8/0/4 (Cache flush) TXT "c#=9" "s#=1" "ff=1" "sf=0" "pv=1.1" "md=Netatmo Relay^@" "id=70:60:BB:30:BF:3C" "na_tkn=ea8a693cc5c6" "ci=2" "sh=LJ/KDg==", PTR _hap._tcp.local., PTR Netatmo Relay._hap._tcp.local., (Cache flush) PTR Netatmo Relay.local., (Cache flush) PTR Netatmo Relay.local., (Cache flush) SRV Netatmo Relay.local.:5001 0 0, (Cache flush) A 192.168.6.247, (Cache flush) AAAA fe80::72ee:50ff:fe6d:c680 (484)
19:07:23.659273 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.1 tell 192.168.6.247, length 28
19:07:23.659315 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.1 tell 192.168.6.247, length 28
19:07:23.659351 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype ARP (0x0806), length 42: Reply 192.168.6.1 is-at 02:0c:43:26:60:30, length 28
19:07:26.087383 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 78: 51.105.245.118.25050 > 192.168.6.247.56878: Flags [P.], seq 57:81, ack 91, win 64150, length 24
19:07:26.091772 70:ee:50:6d:c6:80 > 02:0c:43:26:60:30, ethertype IPv4 (0x0800), length 809: 192.168.6.247.56878 > 51.105.245.118.25050: Flags [P.], seq 91:846, ack 81, win 2920, length 755
19:07:26.170821 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype IPv4 (0x0800), length 54: 51.105.245.118.25050 > 192.168.6.247.56878: Flags [.], ack 846, win 63420, length 0
19:07:28.764265 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.1 tell 192.168.6.247, length 28
19:07:28.764306 70:ee:50:6d:c6:80 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 192.168.6.1 tell 192.168.6.247, length 28
19:07:28.764340 02:0c:43:26:60:30 > 70:ee:50:6d:c6:80, ethertype ARP (0x0806), length 42: Reply 192.168.6.1 is-at 02:0c:43:26:60:30, length 28
^C
107 packets captured
110 packets received by filter
0 packets dropped by kernel
root@WAX206:~#