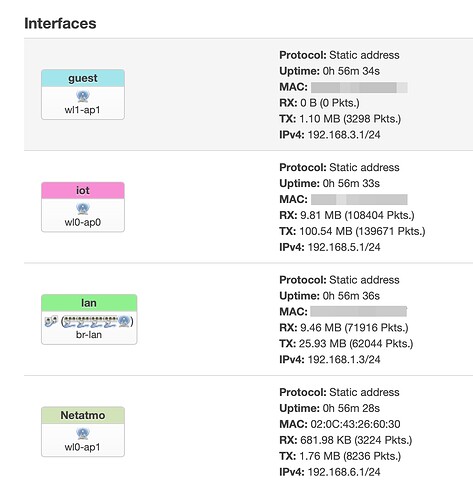
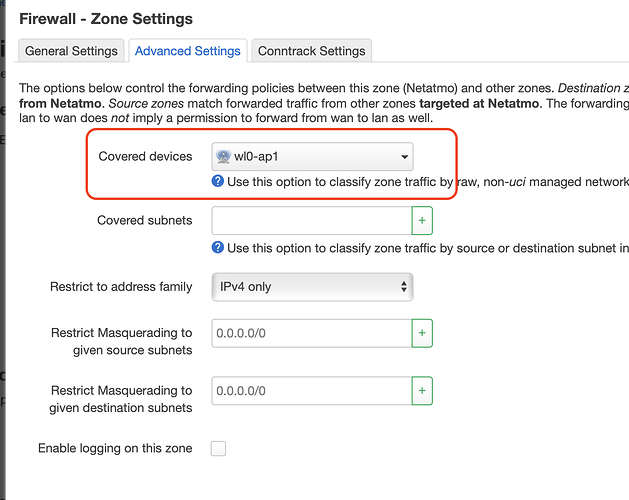
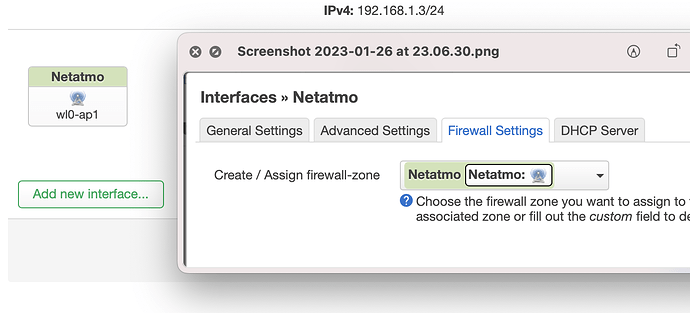
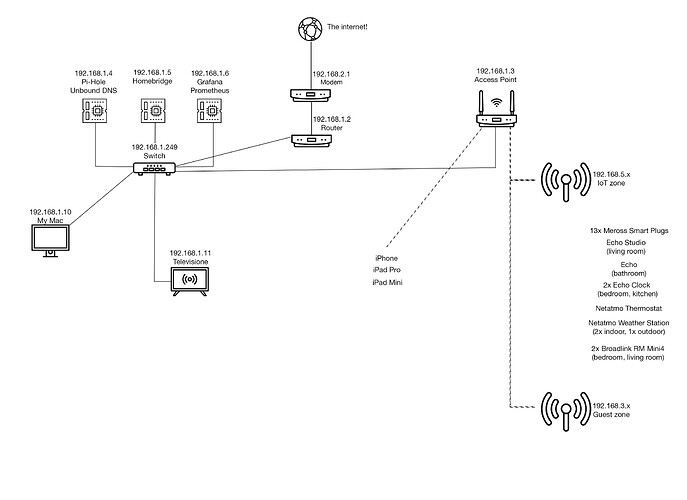
I will go through that capture and comment on a few things later.
For future captures, please add the 'v' (verbose) option unless a specific capture doesn't need it. I would like to see 'tcp' vs 'udp' clearly showing in the output.
tcpdump -ennv -i wl0-ap1 ...
Using the filter expression 'ether host 70:ee:50:6d:c6:80' and the -e option is useful in early investigation to see what the hosts are doing, ether host usually only applies when capturing on the same layer2 network. Use the appropriate ethernet address that applies on a different l2 segment to see the related traffic on the different network or use the related ip addresses etc. as appropriate.
Using the ether host expression was useful because it showed the DHCP traffic and it show that the Netatmo device (thermostat?) is also using IPv6. It could be that the Netatmo devices work with HomeKit using IPv6 when on the same L2 network. It is possible unless proven to be false.
.
.
.
Notice that the first is from 192.168.6.127.49406 > 192.168.6.149.25050 and the second is in the opposite direction: 192.168.6.149.25050 > 192.168.6.127.49407, not that it matters for this discussion. Port randomization usually picks non-sequential port numbers. It is common with many protocols that a different source port is used for each new connection so what you shared is expected unless you know that the protocol in use by Netatmo is different.
.
.
.
If IP addresses are working, let us dig into mDNS.
If you still have your Netatmo thermostat and weather station on the Netatmo SSID and network (192.168.6.0/24) with the WAX206 interface of wl0-ap1, please do a new, different tcpdump. Run it long enough to see repeated mDNS queries from the Netatmo devices and any responses from the other side. Same for queries and responses in the opposite direction:
tcpdump -ennv -i wl0-ap1 port 5353
If nothing is seen coming back from the "LAN" through avahi, 192.168.1.0/24 then from a new terminal window, do 2 new captures, still on WAX206 starting at the same time with a similar capture on the br-lan side in the added ssh session:
tcpdump -ennv -i br-lan port 5353
and a new one for tcpdump -ennv -i wl0-ap1 port 5353 .
Use the appropriate 'wlX-apY' for network "LAN" if needed to see wifi traffic for network 192.168.1.0/24.
Please share the complete output as quoted text. Feel free to PM them and any other communications to me if you don't want to share with the world. You can update the "solution" at the end.
EDIT: Please include any traffic from the "iot" network. It is useful for comparisons.
Please identify what host the IP addresses belong to and describe the function if you think it may not be clear to me. Netatmo thermostat, weather station, router, HomeBridge, HomeHub, Mac, etc.
We should avoid using pronouns or other terms that may be ambiguous or otherwise unclear. This one can be a challenge for me ![]()
.
.
Are all the hosts of interest on wifi?
Is Avahi still running on WAX206?
.
.
.
Info: Keeping the captures on each interface separate helps keep track of what is seen where.
I will try to work on keeping future questions / responses to a narrow focus. ![]()