Sorry I didn't explain my network properly. Here's a quick overview (I'm not much of an ASCII artist):
SSID1, SSID2
|
OpenWRT AP (Cisco/Linksys E3000)
Port 1 (shown as "LAN 1" on the LuCI UI)
|
Port 3
Switch (D-Link DES-1252)
Port 1 Port 2 - SUBNET 2
| |
SUBNET 1 |
| |
Port 1 |
Firewall/router |
Port 2 ------------|
Port 3
|
Internet
This is a simplified version of the network, just to get things working properly.
SUBNET 1 is a set of switches and client hosts that usually just access Internet or a subset of services on SUBNET 2 through a Firewall/Router.
Firewall/router is a Linux OS with DHCPD and BIND. It serves these types of requests on SUBNET 1.
SUBNET 2 is a set of switches, computers and servers (in other words, the "main LAN"). Among these servers, there's another DHCPD and BIND/DNS.
Hosts on SUBNET 2 may access hosts on SUBNET 1 and Internet but always through the Firewall/Router.
Wireless clients that can authenticate with SSID1 will only be able to access SUBNET 1 (they might access some services on SUBNET 2, Firewall withstanding),
Wireless clients connected to SSID2 (different authentication scheme) will only have access to SUBNET 2 and whatever the Firewall/Router allows.
To sum it all up, it's as if I were to connect an AP directly to SUBNET 1 and another AP directly to SUBNET 2. However, I can't physically do that, so I'm trying to use VLANs and multiple SSIDs for the same purpose.
I can't even use 2 ethernet cables to connect 1 AP with 2 SSIDs and VLANs to 2 different switches on SUBNETS 1 and 2 because I only have one eth cable available to connect each AP (that's why I'm trying to use just AP port 1 with 2 tagged VIDs as a "trunk").
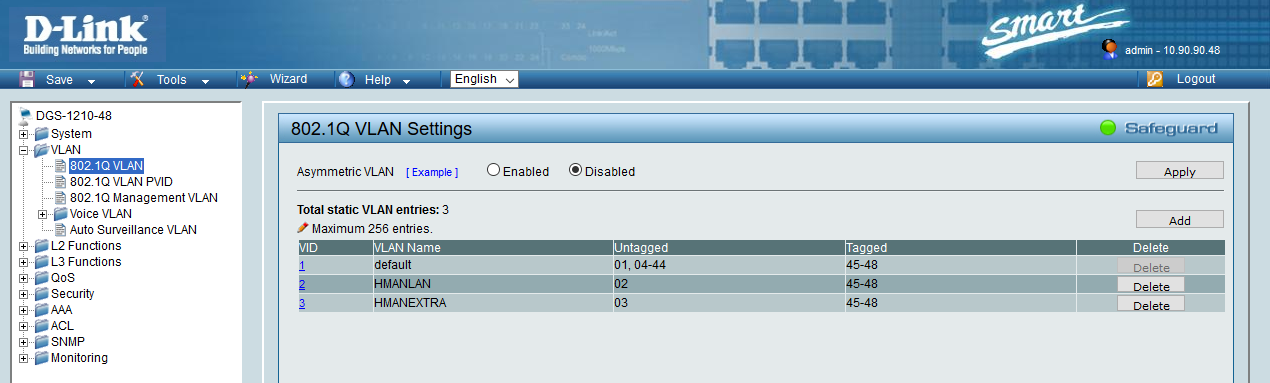
Here's how the D-Link DES-1252 switch is configured:
VID "VLAN Name" "Untagged VLAN Ports" "Tagged VLAN Ports"
01 default 01 03
02 LAN 02,04-52 03
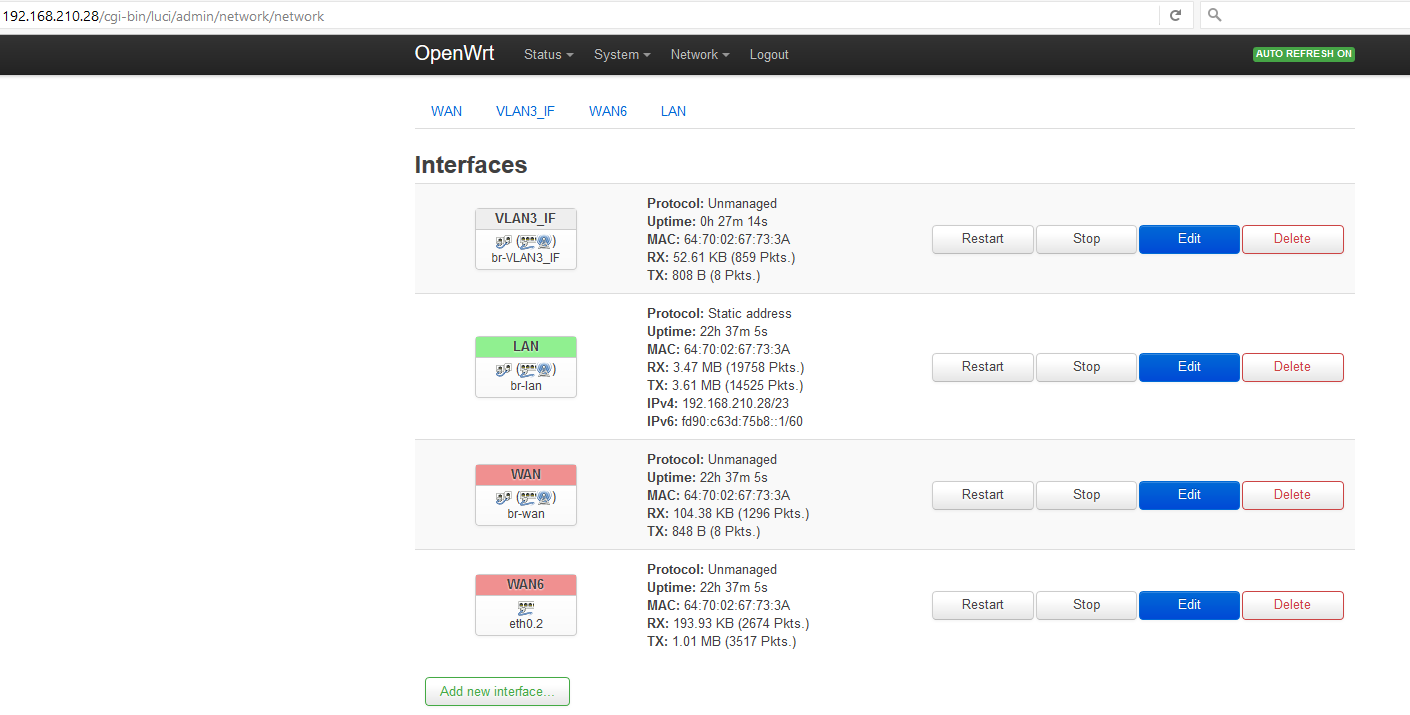
So, SUBNET 1 is connected to Switch Port 1, SUBNET 2 is connected to Switch Port 2 (and for now also to ports 4-52), the OpenWRT AP Port 1 is connected to Switch Port 3.
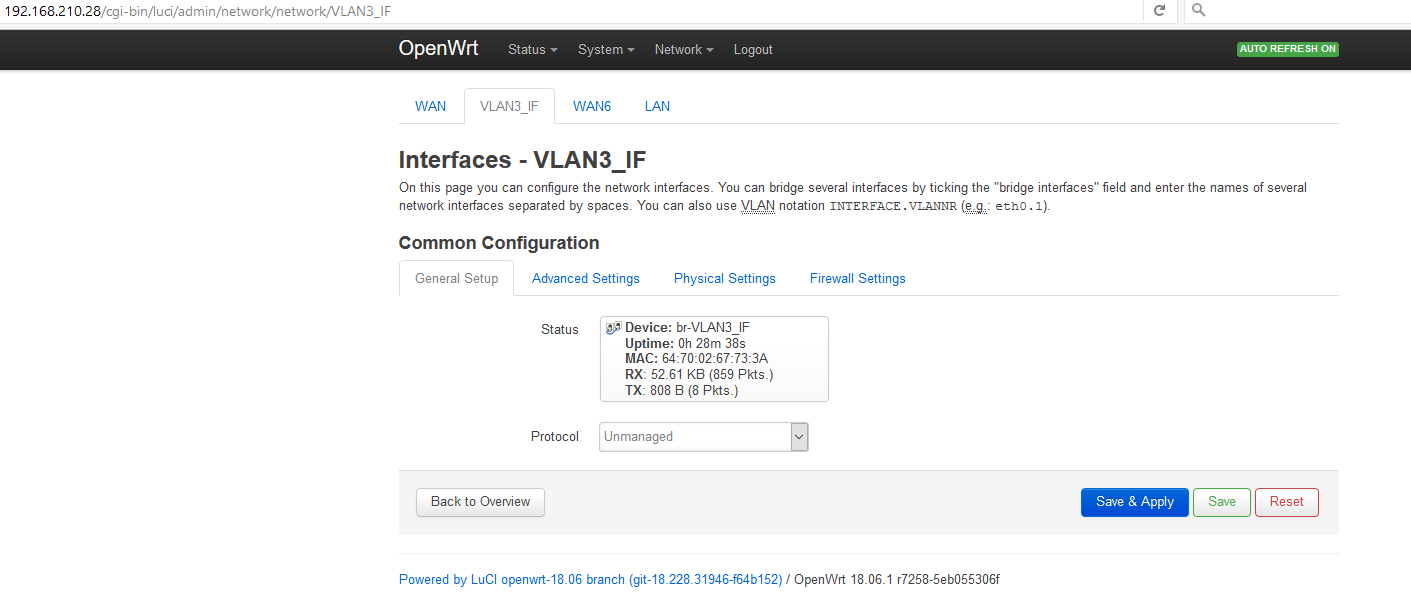
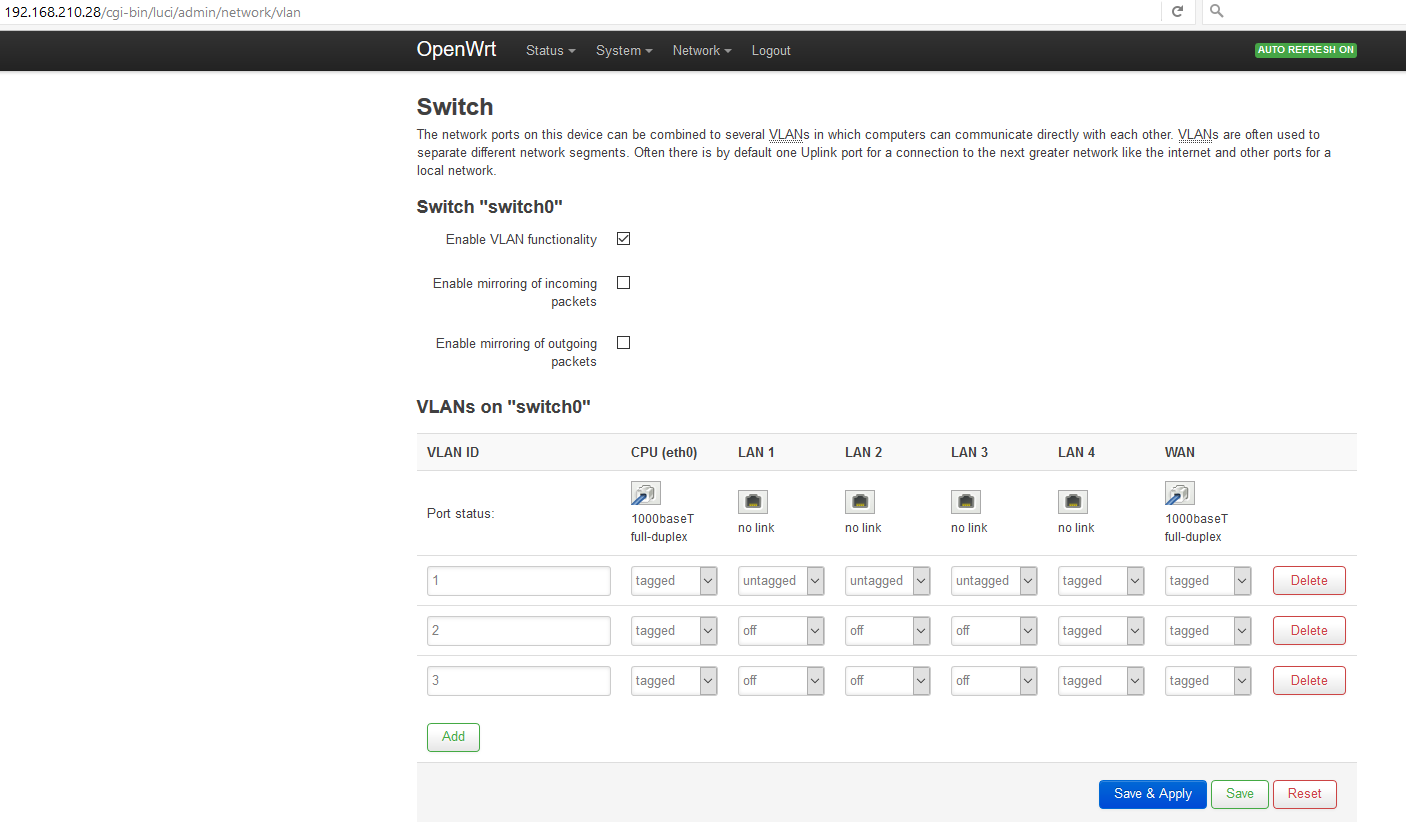
Finally, here's my OpenWRT Linksys E3000 AP config.
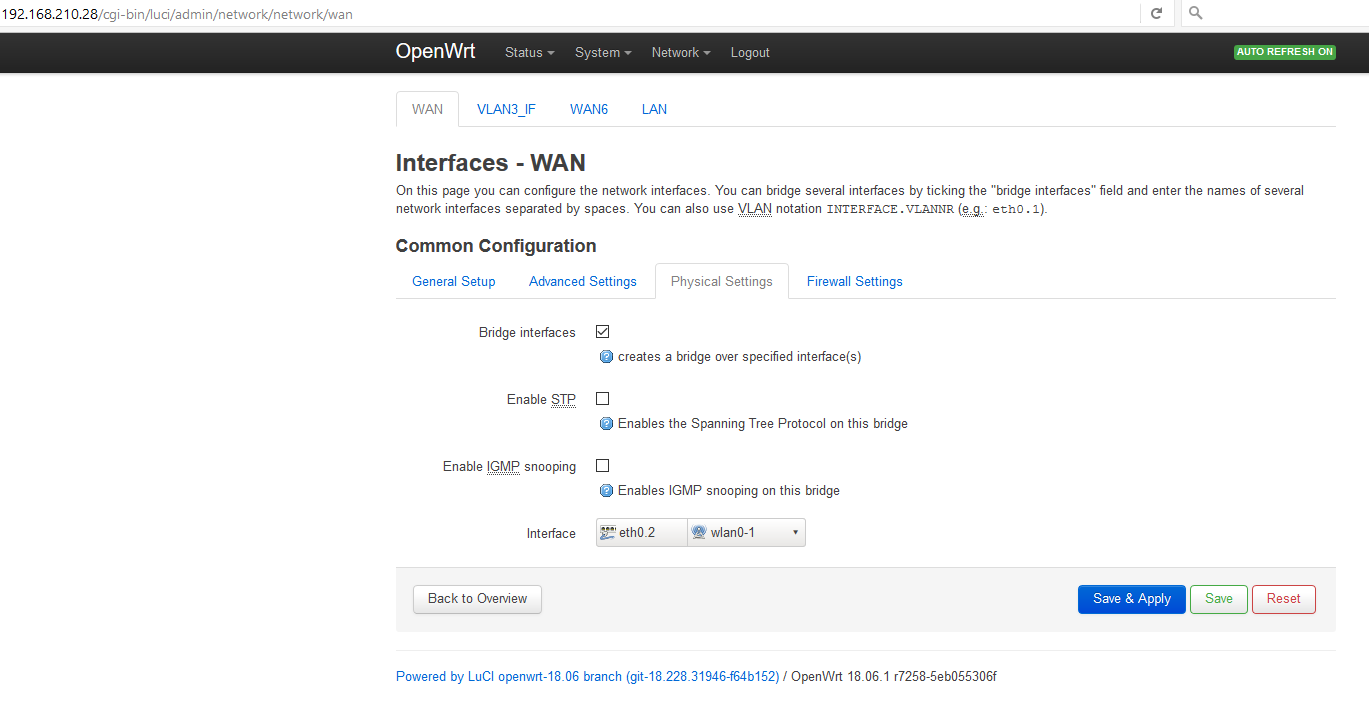
LuCI -> Network -> Switch:
"VLAN ID" "CPU (eth0)" "LAN 1" "LAN 2" "LAN 3" "LAN 4" "WAN"
"Port status" "1000f-duplex" "1000f-duplex" "no link" "no link" "no link" "no link"
1 tagged tagged off untagged off off
2 tagged tagged off off untagged off
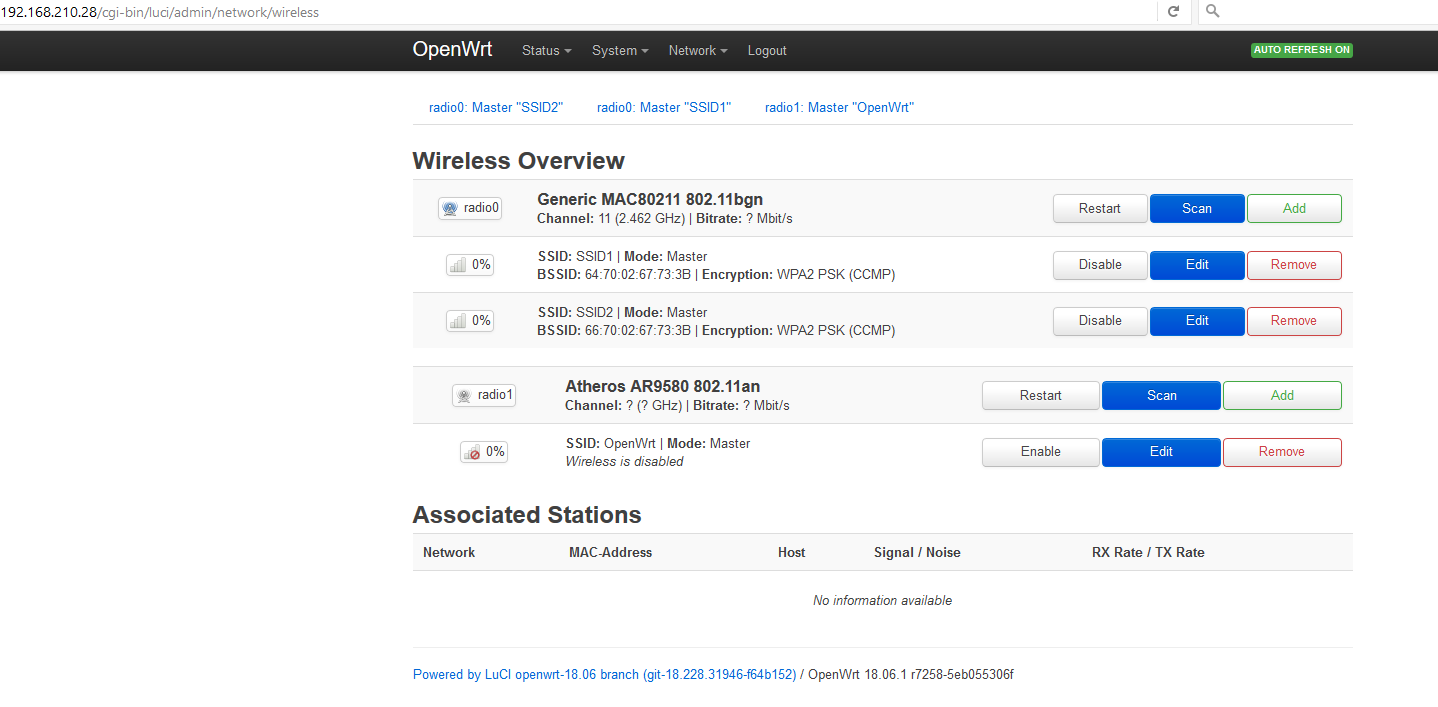
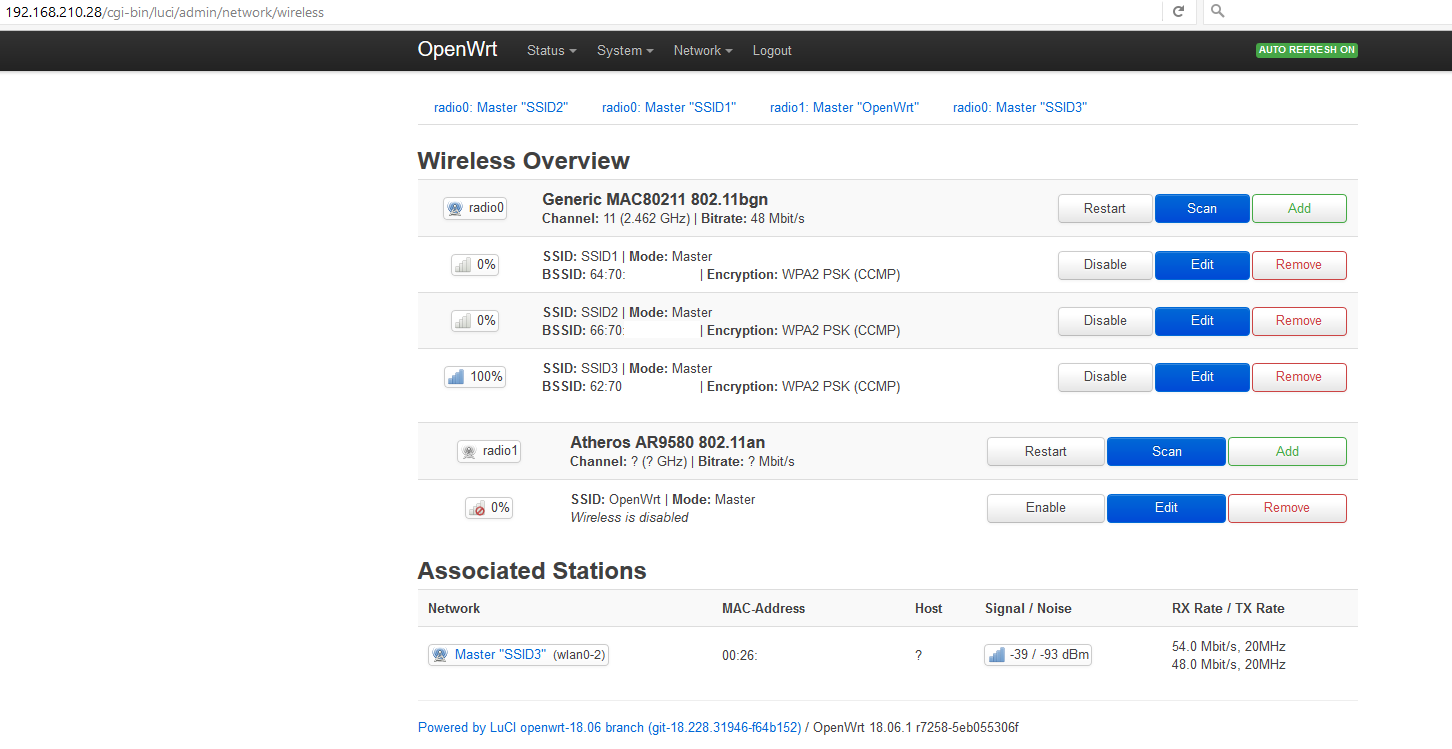
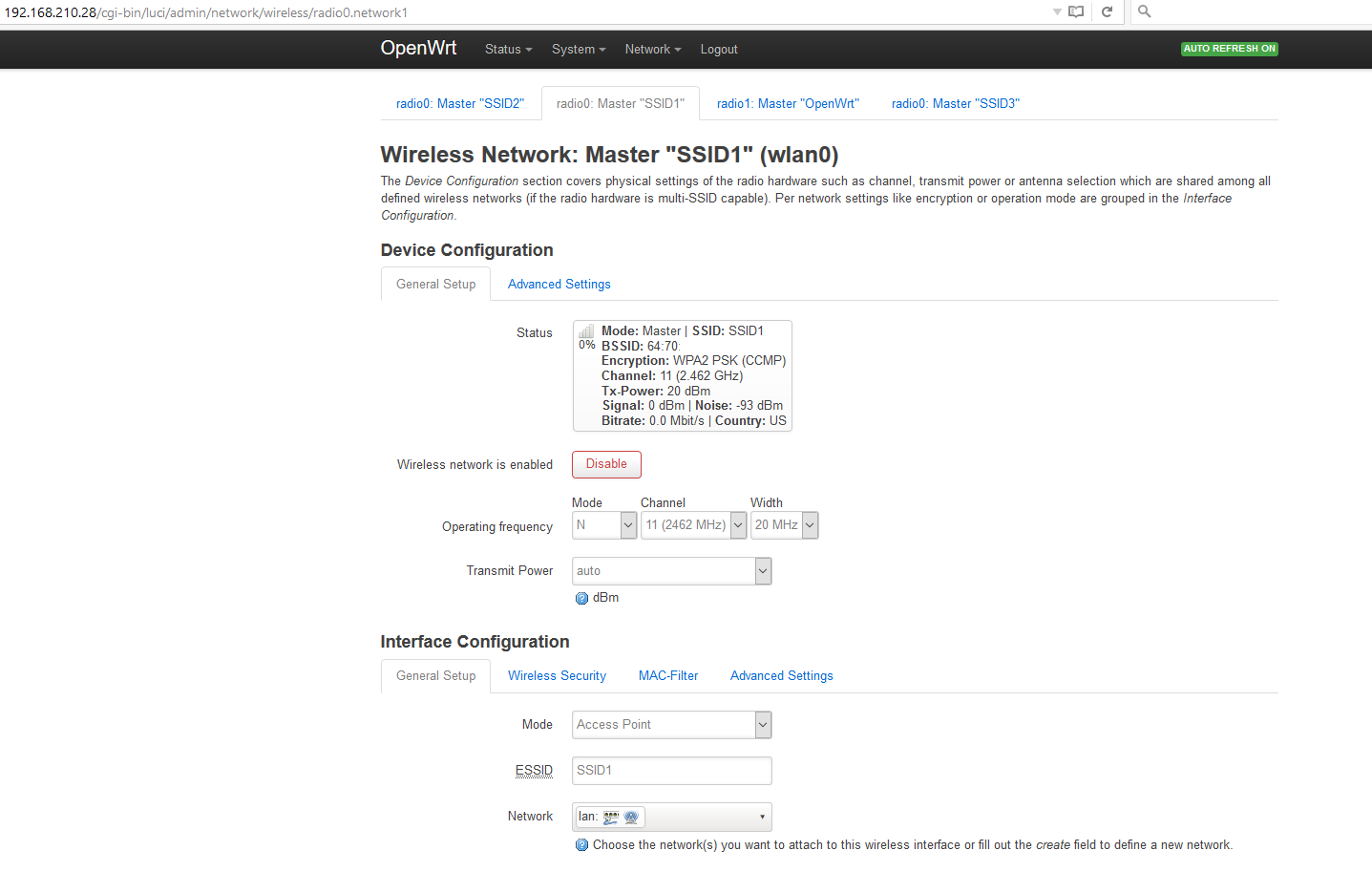
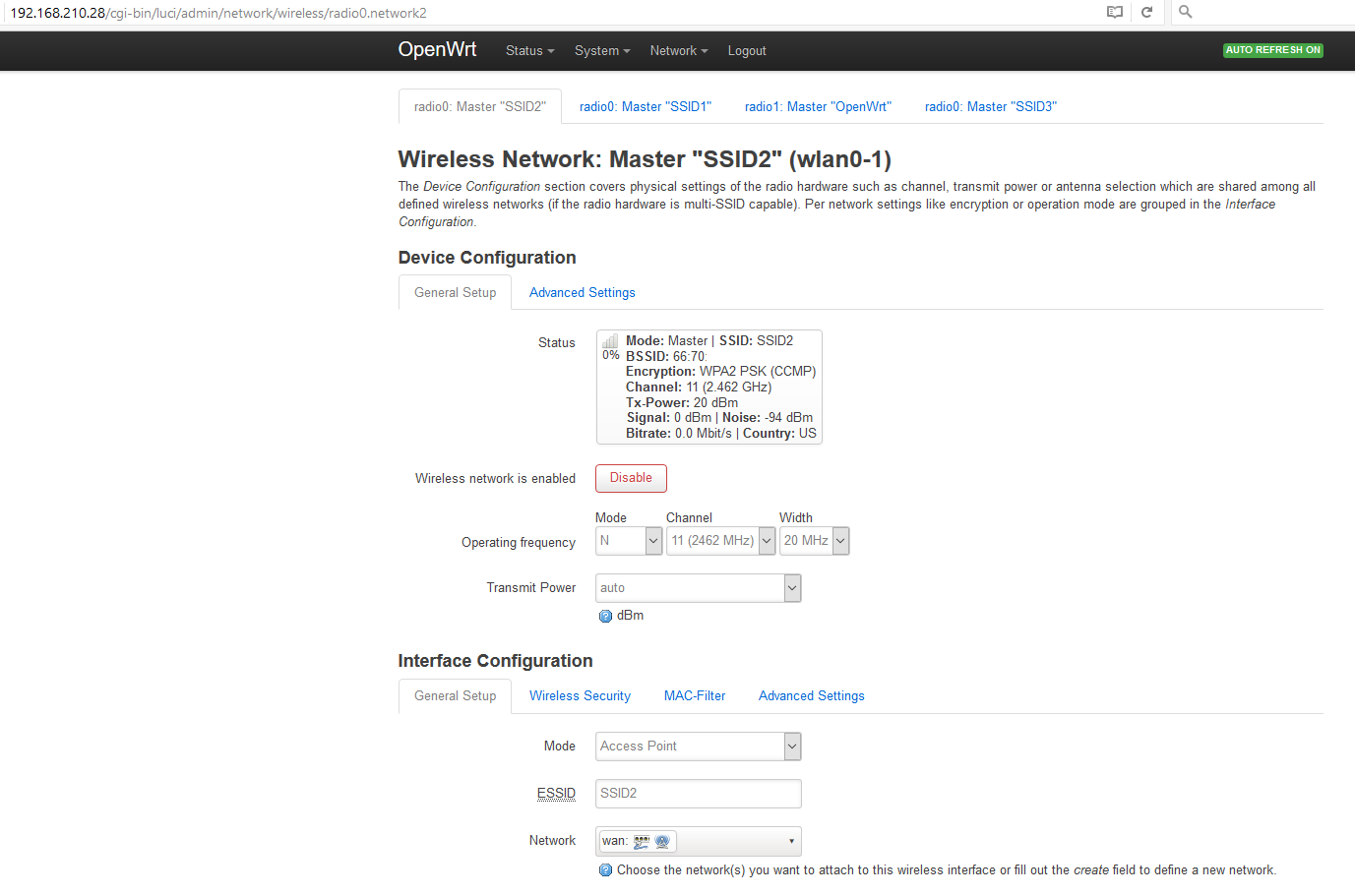
LuCI -> Network -> Wireless:
radio0 Generic MAC80211 802.11bg
SSID1 Mode: Master
SSID2 Mode: Master
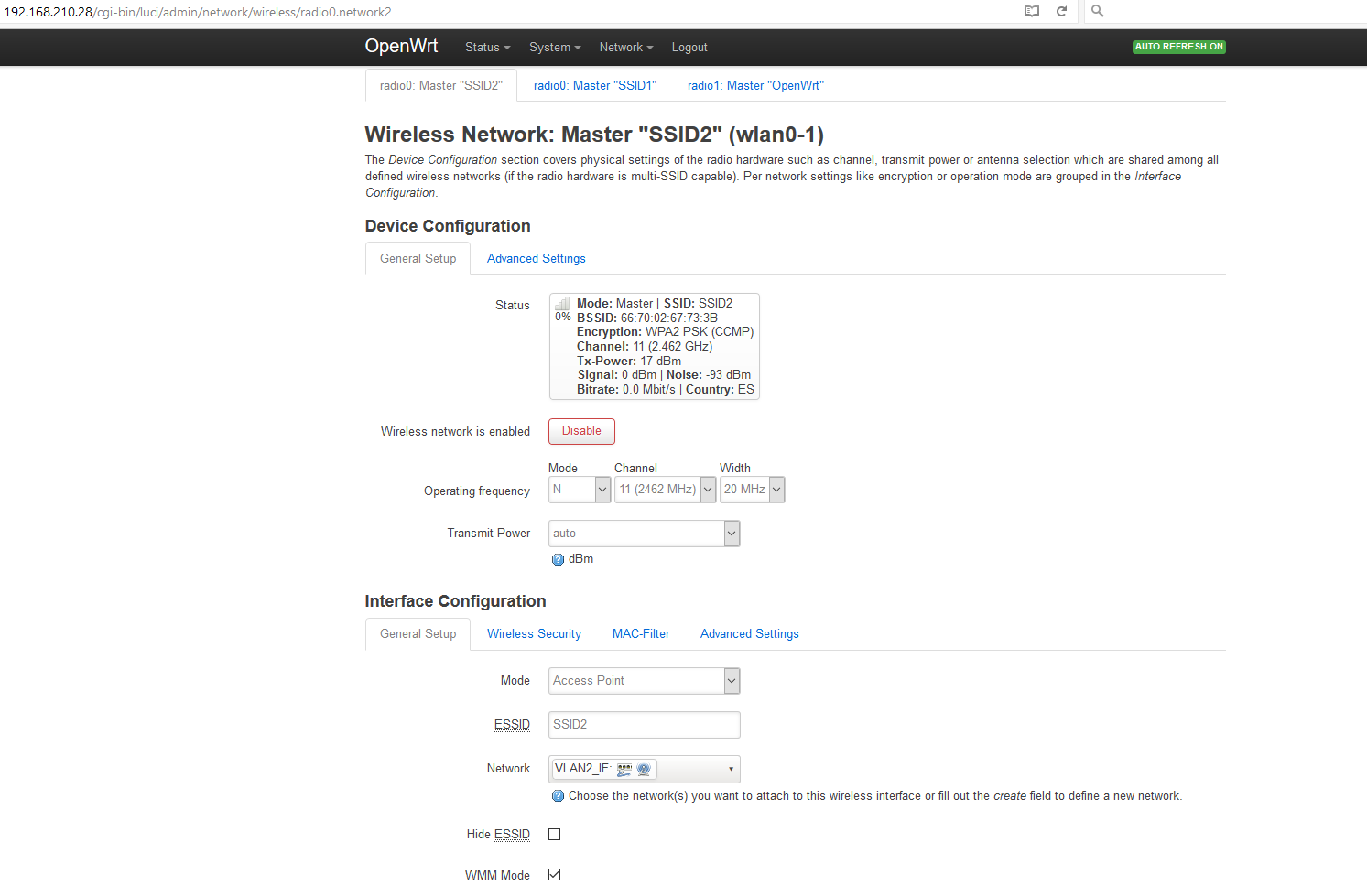
If I edit both SSIDs then under "Interface Configuration" both SSID1 and SSID2 have "Network = lan" at this point.
@aczlan, thanks for your detailed instructions. There are a few things I don't understand though.
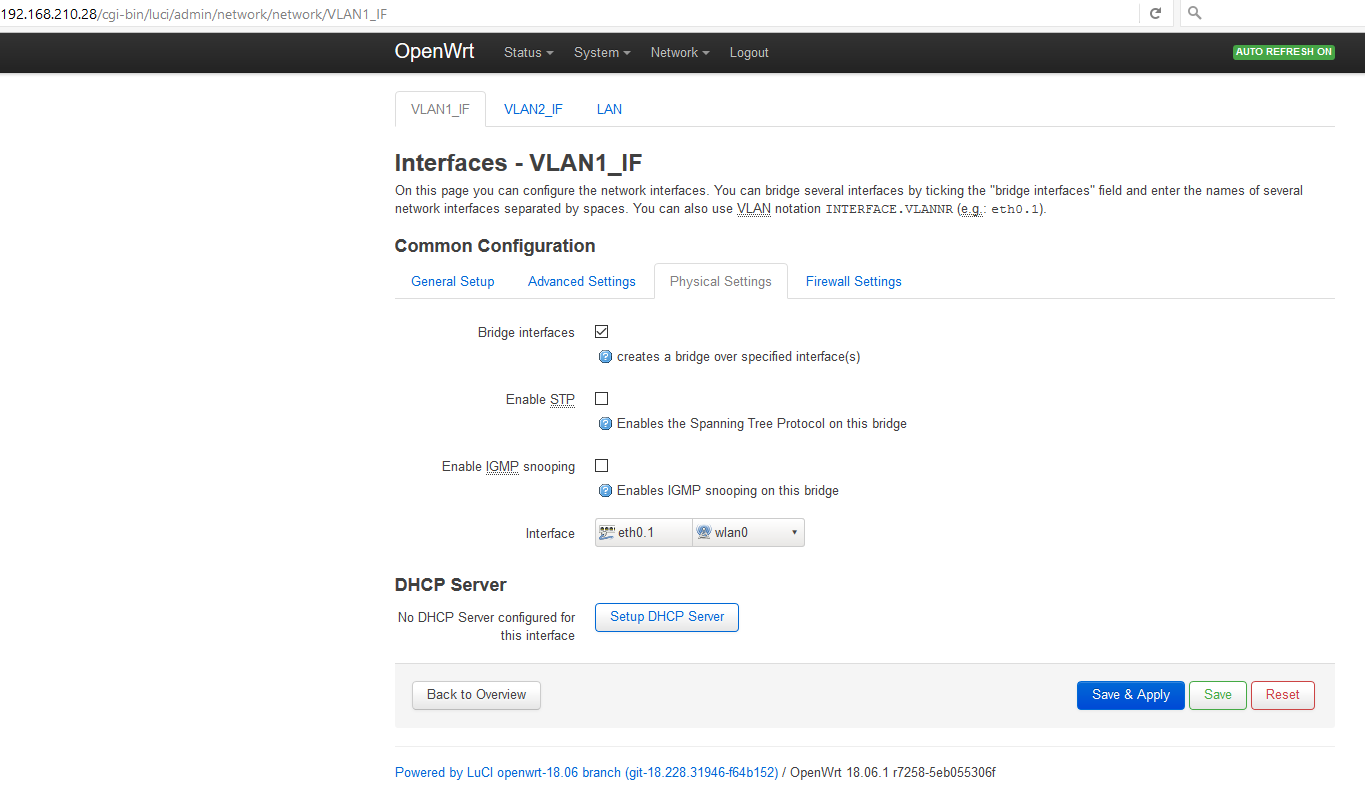
Step 1: you mention eth1.1 for VLAN1 and eth1.2 for VLAN2. Is that because your hardware shows up as eth1 instead of eth0 as in my case?
Step 1b: if I try to translate what you say in terms of LuCI configuration then I guess you're saying that I should do the following:
LuCI -> Network -> Switch:
"VLAN ID" "CPU (eth0)" "LAN 1" "LAN 2" "LAN 3" "LAN 4" "WAN"
"Port status" "1000f-duplex" "no link" "no link" "no link" "1000f-duplex" "no link"
1 tagged untagged off tagged off off
2 tagged off untagged tagged off off
That's confusing to me, or I got it all wrong...
In my first post (and here), I mentioned that my "trunk" link from the AP to the SWITCH is from AP Port 1 to Switch Port 3.
If I translated your instructions right then you are using AP Port 3 as the "trunk" link that should be connected to Switch Port 3, right?
You also mention to switch ports 1 and 2 to "off" for the existing VLAN, but there is none. VLANs 1 and 2 are the defaults, and I'd rather use them instead of creating VLANs 3 and 4 for instance.
I'm a VLAN newbie so I'm probably going to ask a dumb question now. If "LAN 4" (ie. AP port 4) is not a member of VLAN ID 1 and VLAN ID 2 then will a host connected to it still access the OpenWRT web UI or ssh console (listening on eth0 I suppose)?
I thought it wouldn't. That's why in my OpenWRT "switch" setup example earlier above I defined "LAN 4" as untagged VLAN 2, "LAN 3" as untagged VLAN 1, so I could connect a host to either one of these in order to access the OpenWRT/LuCI services via HTTP or SSH on eth0.
Step 2: here's where I went:
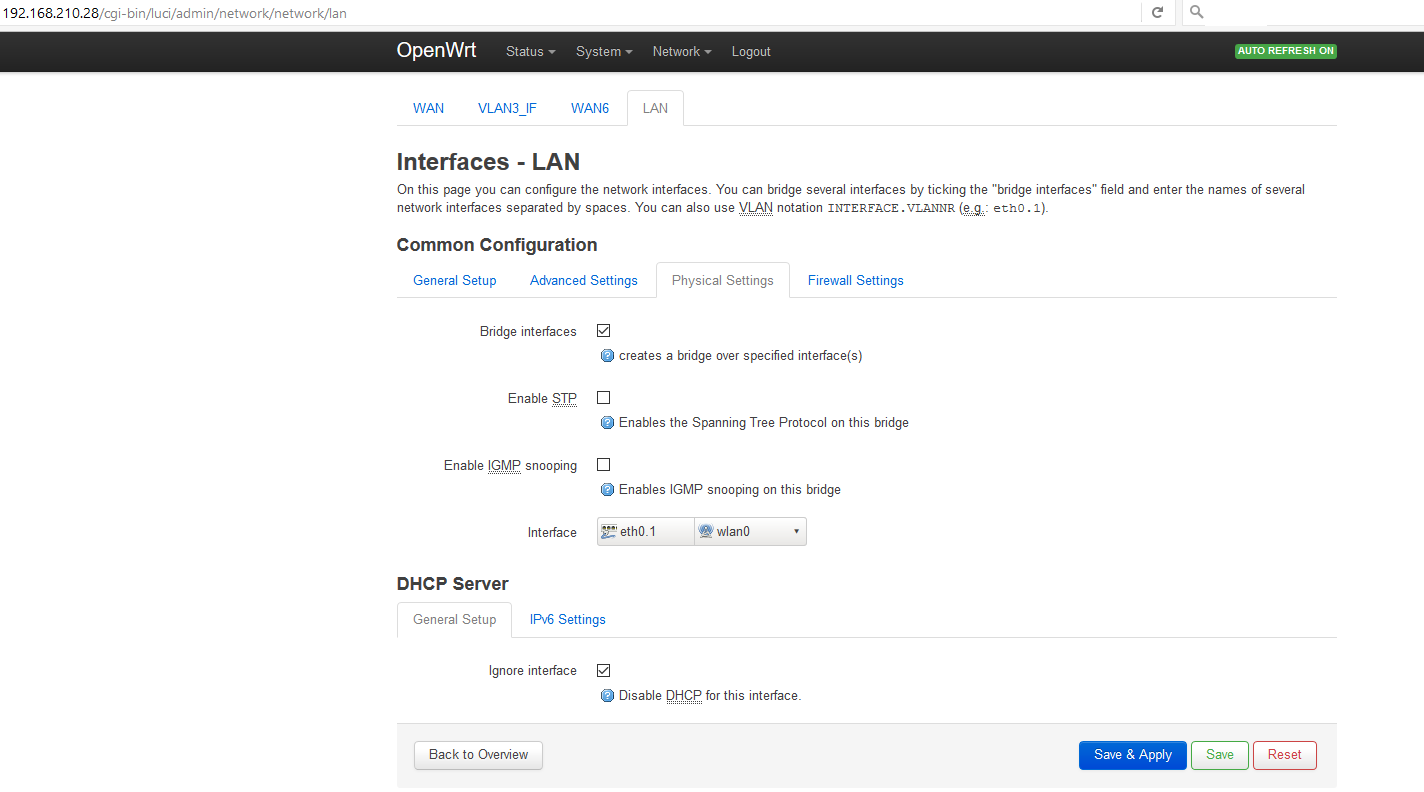
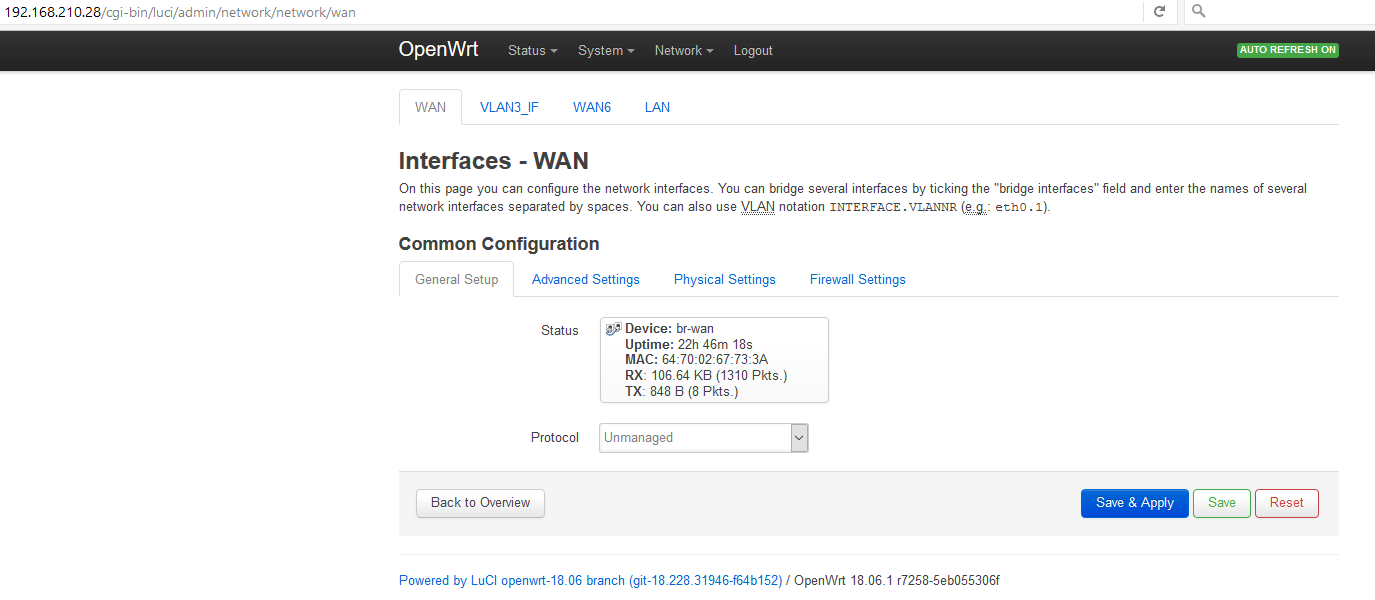
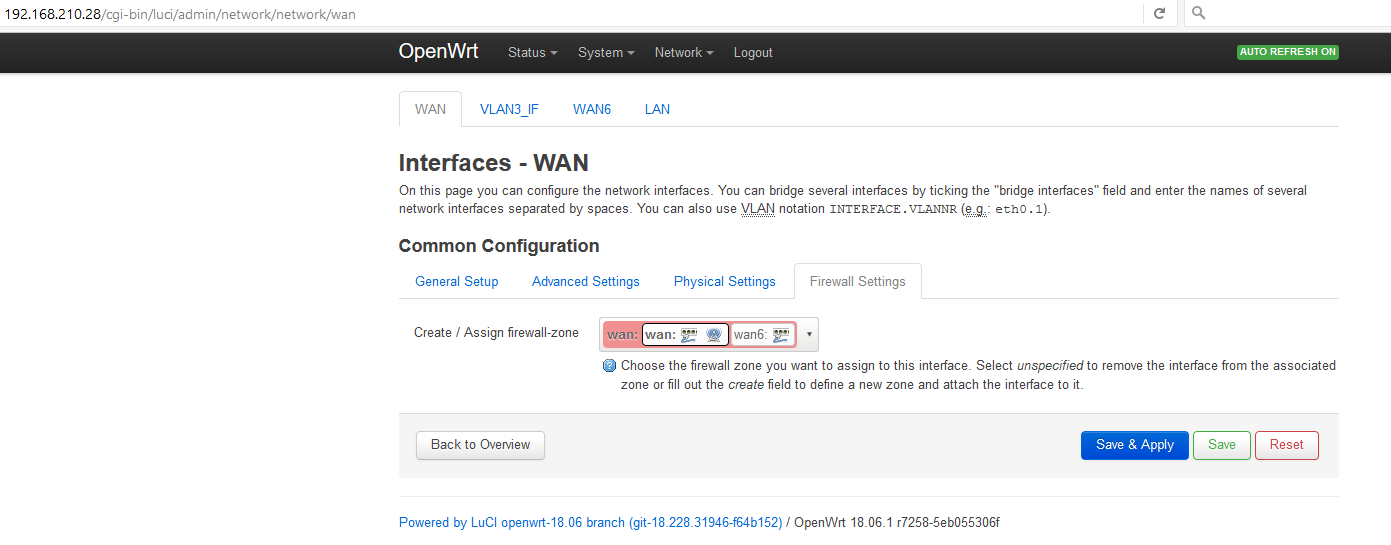
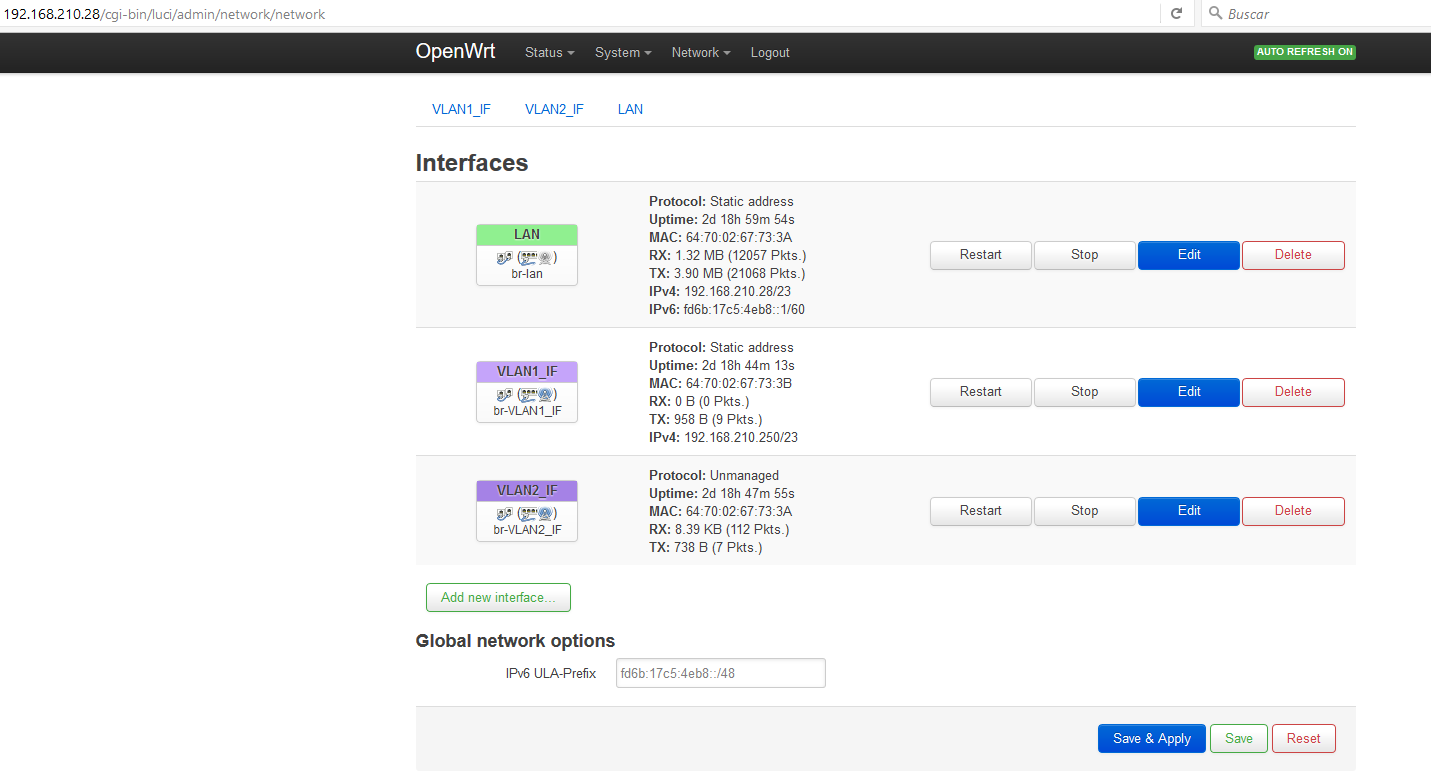
LuCI -> Network -> Interfaces:
WAN LAN WAN6
Add new Interface (I clicked this button)
Create Interface:
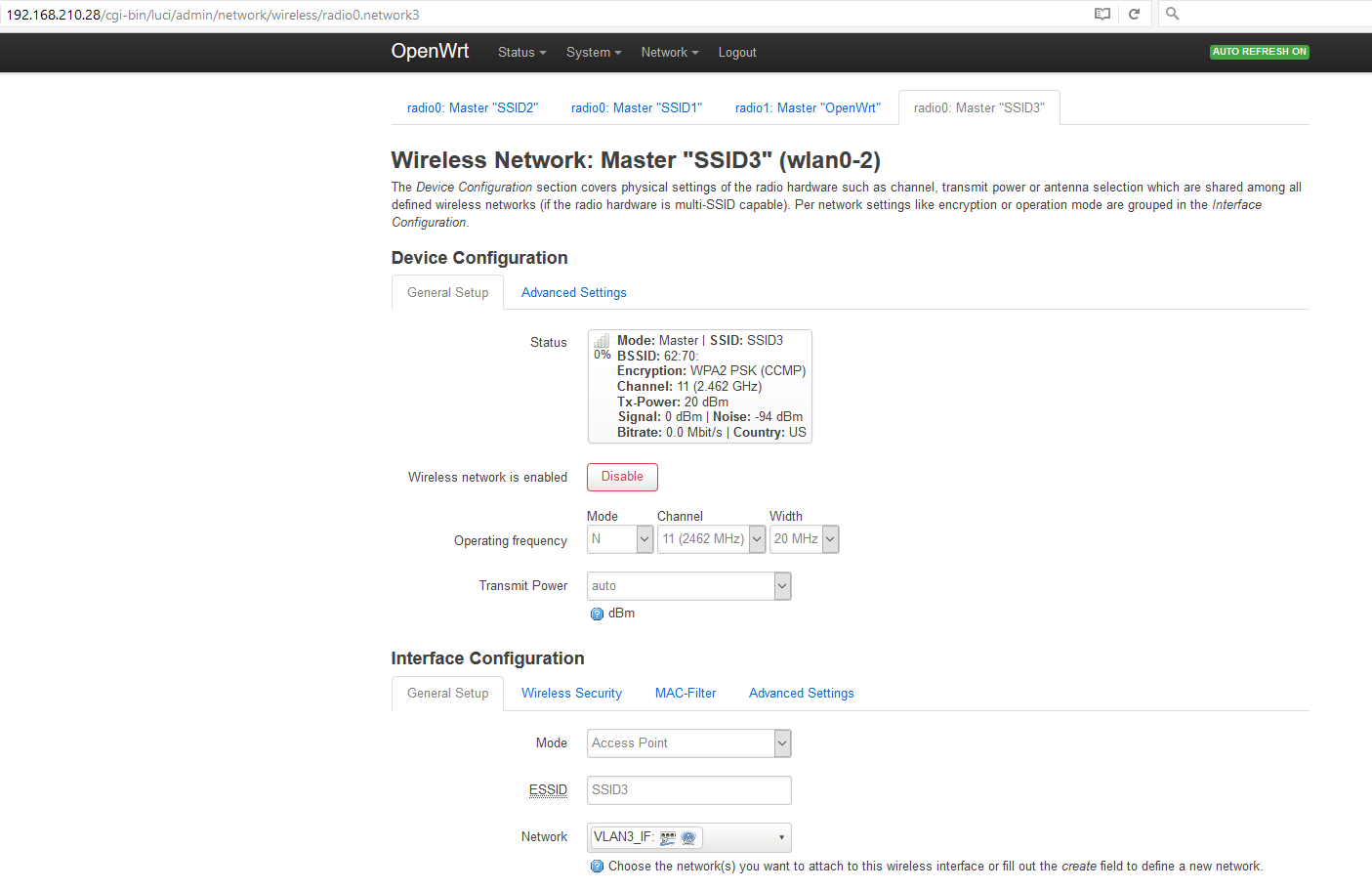
Name of the new interface: VLAN1_IF (instead of INTERFACE1 in your example)
Protocol of the new interface: Static address
Create a bridge over multiple interfaces (unchecked)
Cover the following interfaces: ** this is where I don't know what to select **
In your example you mention "Switch VLAN: eth1.1". My drop-down menu shows these options:
Ethernet Switch: "eth0"
Switch VLAN: "eth0.1" (wan, wan6)
Switch VLAN: "eth0.2" (lan)
Wireless Network: Master "SSID1" (lan)
Wireless Network: Master "SSID2" (lan)
Should I select 'Switch VLAN: "eth0.1" (wan, wan6)'?
I decided to wait for your reply/replies before screwing things up because the AP is in production and I wouldn't want to disrupt the users too much (let alone brick the device which happened when I tried to add a 5GHz WiFi SSID, but that's another story).
Also, on step 5 you mention that I should set up an IP address for INTERFACE1 (VLAN1_IF).
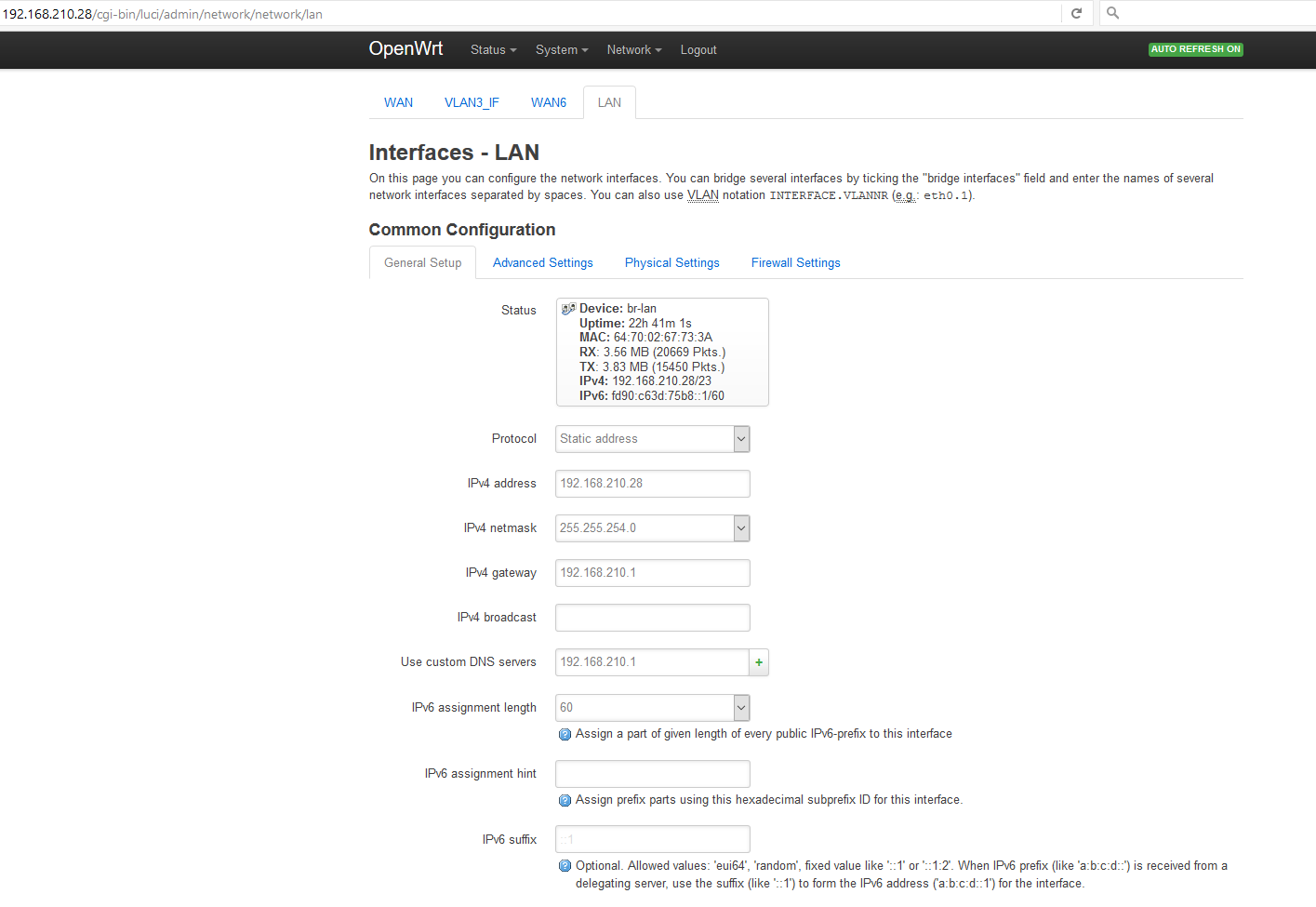
I currently have a static IP address in:
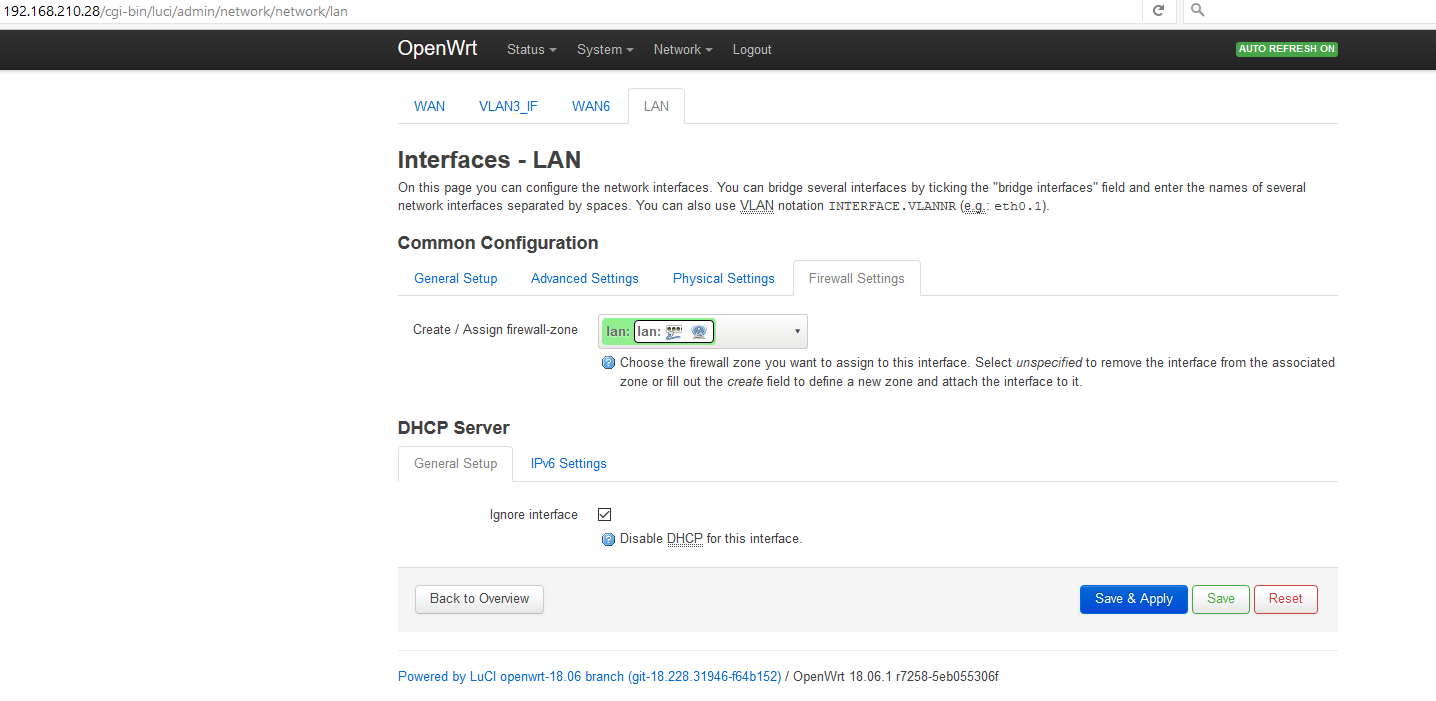
LuCI -> Network -> Interfaces -> LAN
Its settings are:
192.168.210.10/23
gw: 192.168.210.1
DNS: 192.168.210.1
I require this IP address to be the AP's management IP address in SUBNET1 that I can access on ports 80,22 from either SUBNET1 or SUBNET2 via Firewall/Router.
I wouldn't want to use up a second IP address, so can I set the same for INTERFACE1 (VLAN1_IF) and/or remove/move the IP settings from "LAN" to INTERFACE1 (VLAN1_IF)?
Thanks!
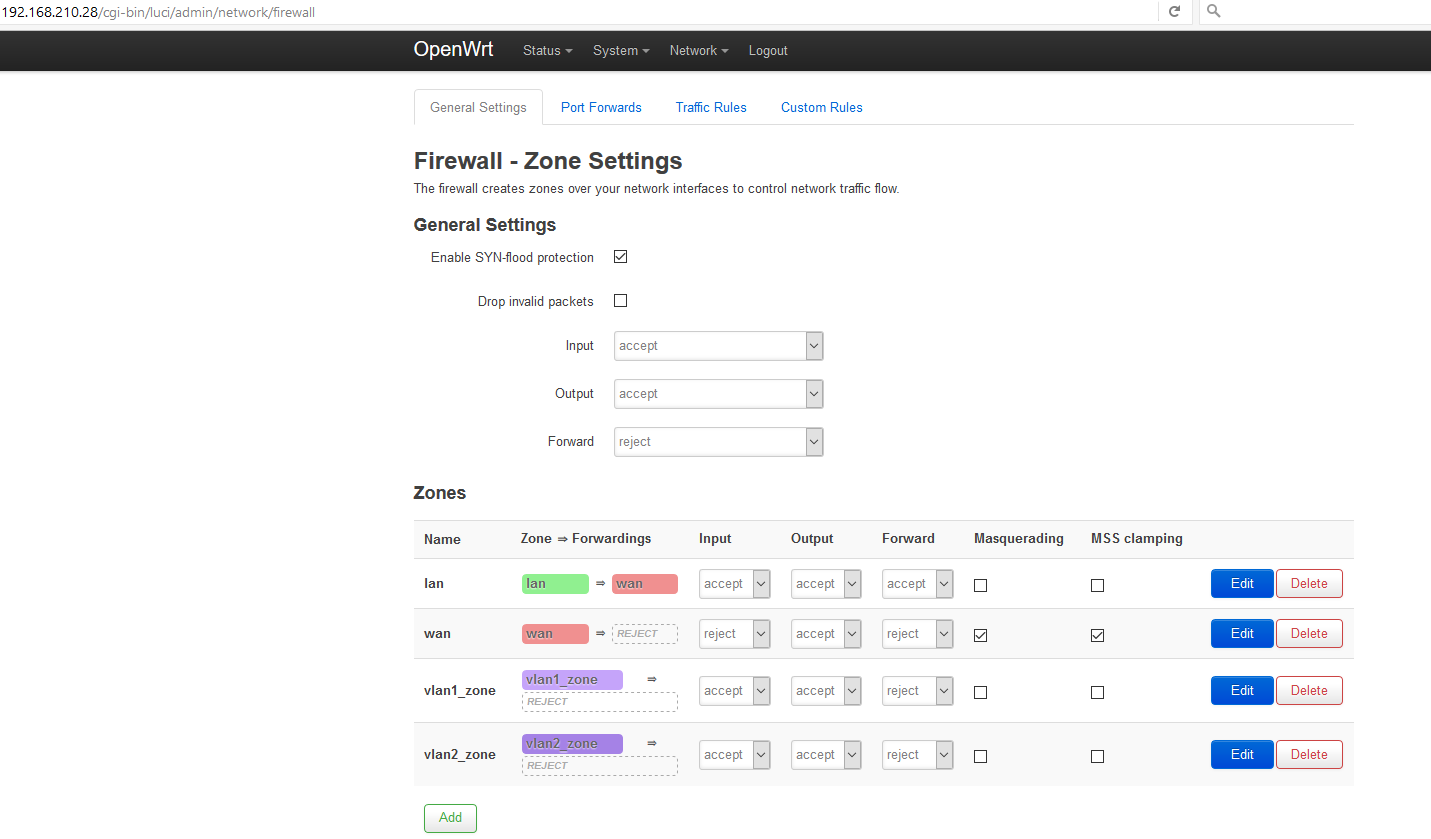
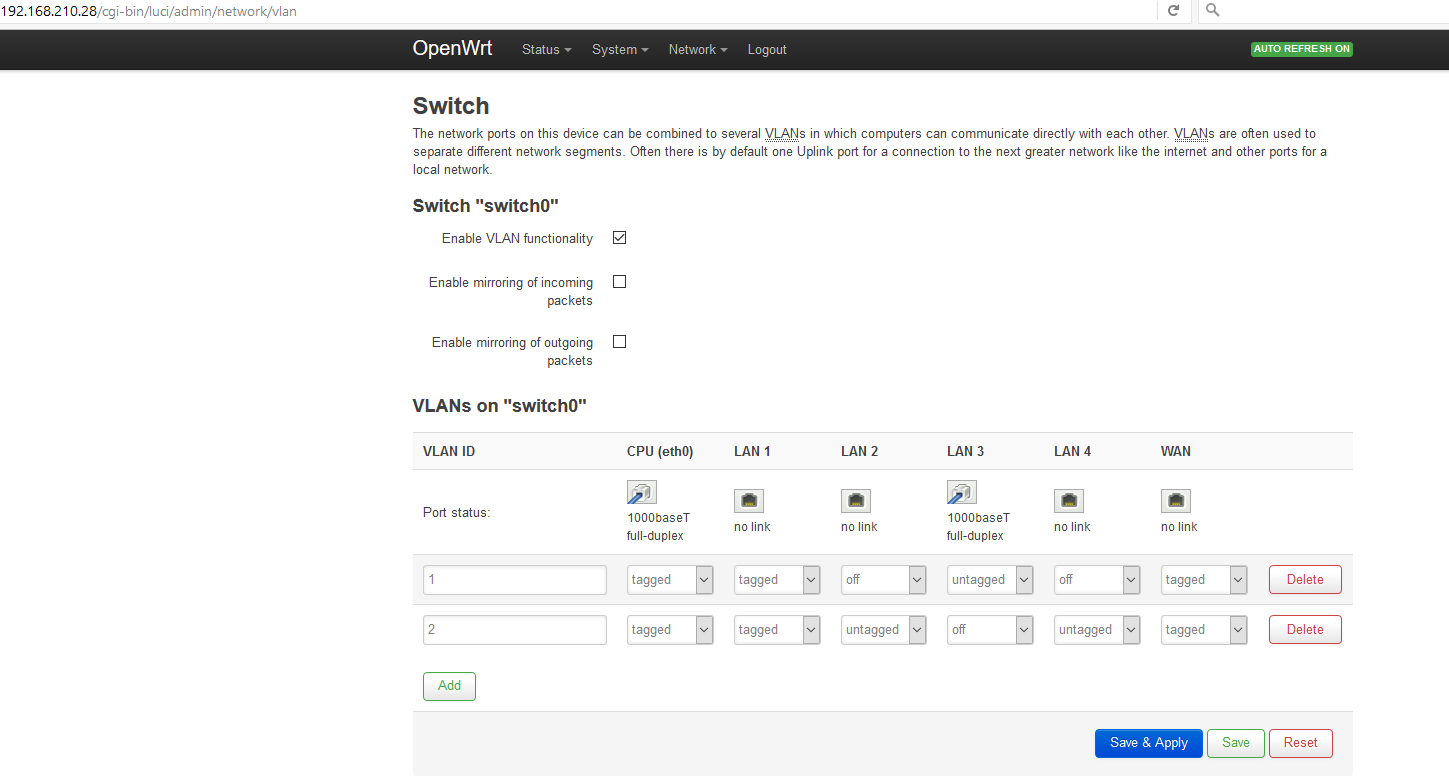 (ignore for now which ports are "connected")
(ignore for now which ports are "connected")