Hi,
please double check on upgrade the sysupgrade path.
I add the release and the date on build to better understand (../openwrt/bin/2024-11-30-rxxxx..)
If you install the latest:
You can install the package you want. It is a basic rom with mtk patch and my mod.
The next stable will be out when busybox update is merged on master.
How many mtk vendor patches/features use more codes in their firmware blobs than existing OpenWrt components?
I know 100% FOSS isn't possible, but I prefer having my devices as clean as possible.
And again, thanks for your works! ![]()
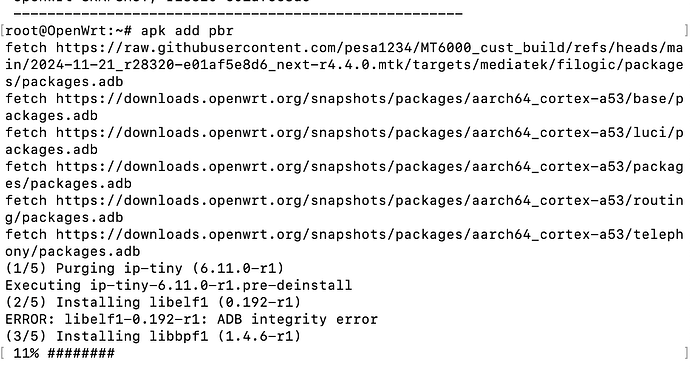
I've just added pbr successfully on a fresh router I am setting up with Pesa's build:
root@MT6000:~# apk add pbr
(1/5) Purging ip-tiny (6.11.0-r1)
Executing ip-tiny-6.11.0-r1.pre-deinstall
(2/5) Installing libelf1 (0.192-r1)
Executing libelf1-0.192-r1.post-install
(3/5) Installing libbpf1 (1.4.6-r1)
Executing libbpf1-1.4.6-r1.post-install
(4/5) Installing ip-full (6.11.0-r1)
Executing ip-full-6.11.0-r1.post-install
add alternative: /sbin/ip -> /usr/libexec/ip-full
(5/5) Installing pbr (1.1.7-r61)
Executing pbr-1.1.7-r61.post-install
ERROR: The pbr service is currently disabled!
Installing rc.d symlink for pbr... OK
OK: 77 MiB in 240 packages
This is from the developers repo:
-- Add Repo
echo 'https://apk.openwrt.melmac.net/packages.adb' > /etc/apk/repositories.d/apk.openwrt.melmac.net.list
wget https://dev.melmac.net/apk/apk.openwrt.melmac.net.pem -O /etc/apk/keys/apk.openwrt.melmac.net.pem
apk update
@pesa1234 I see you have unbound as a pre-installed package, do you have it active & configured along with dnsmasq-full? Or just installed, but not active? Just asking for curiosity sake. ![]() And as always - thank you for all you do.
And as always - thank you for all you do.
In latest release it is not installed and not compiled.
In previous it is only compiled. You can find it on packages.
I just started from scratch again. It works now perfectly. Thank you so much!
Hardware Interrupt and Packet Steering
I'd like to share what I've found.
The new script uses a different strategy compared to the previous one.
Instead of trying to split flows by hash and spread them to all CPUs, use RPS to redirect packets to a single core only.
Try to spread NAPI thread and RPS target CPUs across available CPUs and try to ensure that the NAPI thread is on a different CPU than the RPS target.
This significantly reduces cycles wasted on the scheduler.
Based on this strategy, I tried setting up the MT6000 hardware.
In the smp_affinity script by @pesa1234 (based on the one distributed by gl-inet), hardware IRQs are
eth0 -> CPU#1
eth1 -> CPU#3
In this case, the CPU allocation to the napi kernel thread in the strategy above is
mtk_eth-5 must not be assigned to CPU#1
mtk_eth-6 must not be assigned to CPU#3
Although not considered here, you can also adjust the hardware IRQ settings for the mt7915e and the CPU allocation to the mt76-tx napi kernel thread.
There was a discussion on the openwrt issue that the hardware IRQ assignment for mt7915e could be handled by napi, so it could be anywhere.
However, it should be better to assign it to a different CPU than eth0 and eth1. (I'm not using the interrupt for xhci-hcd:usb1, so I'm not considering it.)
mt7915e -> CPU#2
mt76-tx napi kernel thread imust not be assigned to CPU#2
Looking at /proc/interrupts, the mt7915e has a lot of interrupts, so I tried to avoid using CPU#2 as much as possible.
Currently, I have the following settings.
echo 2 > /proc/irq/120/smp_affinity
echo 8 > /proc/irq/121/smp_affinity
echo 4 > /proc/irq/133/smp_affinity
taskset -p -c 3 `pgrep mtk_eth-5`
taskset -p -c 0 `pgrep mtk_eth-6`
taskset -p -c 1 `pgrep mt76-tx`
RPS: Receive Packet Steering is assigned to a single CPU according to the new packet steering strategy. Since it is more efficient to assign it to an interrupt CPU, rps_cpus is set to the default value of 0.
for q in /sys/class/net/eth0/queues/rx-*/rps_cpus; do echo 0 > $q; done
for q in /sys/class/net/eth1/queues/rx-*/rps_cpus; do echo 0 > $q; done
for q in /sys/class/net/phy?-ap?/queues/rx-*/rps_cpus; do echo 0 > $q; done
RFS: Receive Flow Steering is only useful when running applications on a router (e.g. for benchmarking), so it is sufficient to set it to 64 or 128 as it is set in openwrt. Although the value 32768 is often recommended, please set the value according to your intended use.
With the above settings, good results have been obtained.
This is my first time using this build. My understanding is this build includes the latest MTK drivers with some optimizations? I have enabled hardware offload, WEB, and iBF. Is there anything else I should enable?
I am able to get my subscribed speeds on my wired PC using ookla speed test. However, when I run waveforms bufferbloat test the highest speed I am able to achieve on the same PC is about 400mb instead of 1200mb. Is it that the waveform speed test is not able to test faster connections accurately, or could it be a matter of my ISP just prioritizing ookla speed test since it is more popular? I heard ISP's can do this to make customers think they are getting faster speeds than they really are.
I don't suggest to enable WED but the better choice is test and make your decision..
Regarding speed it's maybe a server issue or maybe ookla use parallel stream and the others no.
iBF you can see some advantages only on older wifi device... Test it...
And regarding flow offload and packet steering it is better to test and choose...
For example if you use a VPN it is better (in my case) to enable hardware flow offload... If you use for gaming maybe it is better to enable a sqm script.
Thanks
Thanks a lot for the detailed explanation. That helped me out a lot. Thanks ![]()
pesa1234 or another user, could you please explain to me the usefulness of this function and how to use it?
When I tested it by connecting 2.5GbE to lan1 port, I found some CPU saturation, so I set it up like this now.
echo 2 > /proc/irq/120/smp_affinity
echo 8 > /proc/irq/121/smp_affinity
echo 4 > /proc/irq/133/smp_affinity
taskset -p -c 0,2,3 `pgrep mtk_eth-5`
taskset -p -c 0,1,2 `pgrep mtk_eth-6`
taskset -p -c 0,1,3 `pgrep mt76-tx`
I don't know if it's a bug or something like that, but I noticed that, at times, the 5GHz Wi-Fi disconnects and doesn't reconnect with any device, requiring a restart to make it work again. This started when I installed the latest version available on GitHub.
When I accessed the logs, these warnings appeared:
Wed Dec 4 01:16:23 2024 daemon.notice hostapd: phy1-ap0: DFS-CAC-COMPLETED success=1 freq=5500 ht_enabled=0 chan_offset=0 chan_width=5 cf1=5570 cf2=0 radar_detected=0
Wed Dec 4 01:16:24 2024 kern.info kernel: [ 101.209578] br-lan: port 7(phy1-ap0) entered blocking state
Wed Dec 4 01:16:24 2024 kern.info kernel: [ 101.215157] br-lan: port 7(phy1-ap0) entered forwarding state
Wed Dec 4 01:16:24 2024 daemon.notice netifd: Network device 'phy1-ap0' link is up
Wed Dec 4 01:16:24 2024 daemon.notice hostapd: phy1-ap0: interface state DFS->ENABLED
Wed Dec 4 01:16:24 2024 daemon.notice hostapd: phy1-ap0: AP-ENABLED
Wed Dec 4 01:16:24 2024 daemon.notice hostapd: phy1-ap0: DFS-CAC-START freq=5180 chan=36 chan_offset=0 width=160 MHz seg0=50 seg1=0 cac_time=60s (background)
Wed Dec 4 01:16:27 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:44 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:44 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:45 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:45 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:46 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:46 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:47 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:47 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:48 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:48 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:49 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:49 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:50 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:50 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:51 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:51 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:51 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:52 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:52 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:53 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:53 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:54 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:54 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:16:56 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:56 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:57 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:16:57 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:00 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:00 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:00 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:01 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:01 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:02 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:02 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:02 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:03 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:03 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:04 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:04 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:05 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:05 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:06 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:06 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:06 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:07 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:08 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:08 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:08 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:09 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:09 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:09 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:10 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:10 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:10 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:10 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:11 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:12 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:12 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:12 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:12 2024 daemon.info hostapd: phy0-ap0: STA 8c:f8:c5:ee:98:1e IEEE 802.11: authenticated
Wed Dec 4 01:17:12 2024 daemon.info hostapd: phy0-ap0: STA 8c:f8:c5:ee:98:1e IEEE 802.11: associated (aid 2)
Wed Dec 4 01:17:12 2024 daemon.notice hostapd: phy0-ap0: AP-STA-CONNECTED 8c:f8:c5:ee:98:1e auth_alg=open
Wed Dec 4 01:17:12 2024 daemon.info hostapd: phy0-ap0: STA 8c:f8:c5:ee:98:1e RADIUS: starting accounting session 2B46A137037F5E42
Wed Dec 4 01:17:12 2024 daemon.info hostapd: phy0-ap0: STA 8c:f8:c5:ee:98:1e WPA: pairwise key handshake completed (RSN)
Wed Dec 4 01:17:12 2024 daemon.notice hostapd: phy0-ap0: EAPOL-4WAY-HS-COMPLETED 8c:f8:c5:ee:98:1e
Wed Dec 4 01:17:14 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:14 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:15 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:15 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:15 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:15 2024 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.239 8c:f8:c5:ee:98:1e
Wed Dec 4 01:17:15 2024 daemon.warn dnsmasq-dhcp[1]: Ignoring domain IQVIA-AZ.local for DHCP host name APTLAWLB9SV9V3
Wed Dec 4 01:17:15 2024 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.239 8c:f8:c5:ee:98:1e APTLAWLB9SV9V3
Wed Dec 4 01:17:16 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:16 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:16 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:19 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:19 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:23 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:23 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:24 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:24 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:24 2024 daemon.notice hostapd: phy1-ap0: DFS-CAC-COMPLETED success=1 freq=5180 ht_enabled=0 chan_offset=0 chan_width=5 cf1=5250 cf2=0 radar_detected=0
Wed Dec 4 01:17:24 2024 daemon.warn hostapd: Can't set DFS state for freq 5180 MHz
Wed Dec 4 01:17:24 2024 daemon.warn hostapd: Can't set DFS state for freq 5200 MHz
Wed Dec 4 01:17:24 2024 daemon.warn hostapd: Can't set DFS state for freq 5220 MHz
Wed Dec 4 01:17:24 2024 daemon.warn hostapd: Can't set DFS state for freq 5240 MHz
Wed Dec 4 01:17:26 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:26 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:30 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:30 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:17:36 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:36 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:36 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:39 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:17:44 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:00 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:03 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:07 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:07 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:16 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:16 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:24 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:28 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:46 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:48 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:48 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:52 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:55 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:18:55 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:08 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:08 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:12 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:16 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:29 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:29 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:36 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:39 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:40 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:44 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:44 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:44 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:46 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:47 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:19:49 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:49 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:49 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:49 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:49 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:19:50 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:50 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:53 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:53 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:19:54 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:54 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:54 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:19:57 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:20:00 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:20:04 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:20:14 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:20:14 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:20:18 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:20:18 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:20:21 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:20:41 2024 daemon.warn odhcpd[2495]: No default route present, overriding ra_lifetime to 0!
Wed Dec 4 01:20:52 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:20:53 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:21:00 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:21:13 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:21:17 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:21:27 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:21:27 2024 daemon.notice hostapd: send_auth_reply: send failed
Wed Dec 4 01:21:37 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:21:57 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:21:57 2024 daemon.info hostapd: phy1-ap0: STA 72:5a:26:82:74:88 IEEE 802.11: deauthenticated due to inactivity (timer DEAUTH/REMOVE)
Wed Dec 4 01:21:58 2024 daemon.err uhttpd[3554]: [info] luci: accepted login on /admin/status/logs for root from 192.168.1.100
Wed Dec 4 01:22:15 2024 daemon.info hostapd: phy1-ap0: STA 92:08:3c:8b:10:3e IEEE 802.11: deauthenticated due to inactivity (timer DEAUTH/REMOVE)
Wed Dec 4 01:22:16 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:22:17 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:22:18 2024 daemon.notice hostapd: handle_probe_req: send failed
Wed Dec 4 01:22:18 2024 daemon.notice hostapd: send_auth_reply: send failed
Thanks!
for q in /sys/class/net/eth0/queues/rx-*/rps_cpus; do echo 0 > $q; done
for q in /sys/class/net/eth1/queues/rx-*/rps_cpus; do echo 0 > $q; done
for q in /sys/class/net/phy?-ap?/queues/rx-*/rps_cpus; do echo 0 > $q; done
These setting are still used? If yes, packet steering script should be disabled right?
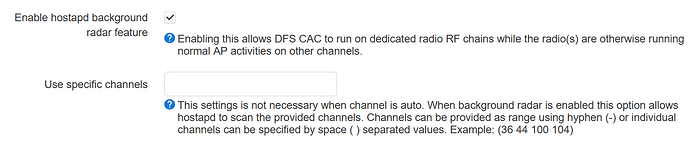
1- Do you have radar background enabled? If yes, please try to deactivate it
2- Do you have set-up a fixed channel? Bandwidth?
I am using the apk test version and I haven't had any issues with package installs or wifi or anything.
It might be technical related but I fail to set up pbr.
Errors:
Service Status
Version 1.1.7-61 - Running (fw4 nft file mode).
Service Gateways
digi/pppoe-digi/10.0.15.57 ✓
The ✓ indicates default gateway. See the README for details.
Please donate to support development of this project.
Service Errors
Unknown error!
Failed to set up 'SPProton/0.0.0.0'!
Unknown error!
Failed to set up 'ProtonUS/10.2.0.2'!
Unknown error!
Failed to set up 'openvpn/tun0/0.0.0.0'!
Errors encountered, please check the README!
Someone else already had this issue? I have two wireguard interfaces and on OpenVPN. Ping works in all of them using "ping -I "interface" 8.8.8.8"
A post was split to a new topic: Question about Bandwidth & Buffer Bloat test results for x86 + MT6000 AP
I've got pbr working fine on my MT6000 using this firmware (be it with only 1 wg tunnel).
I suggest you post in the pbr thread, you are more likely to get the support you require there (they are very helpful and know their stuff about pbr):