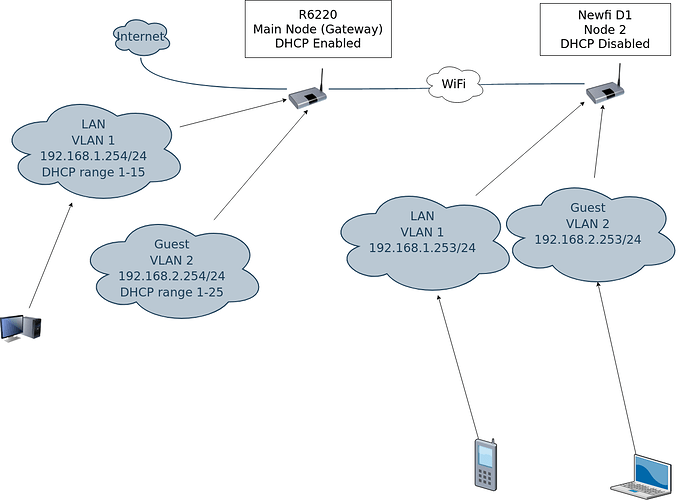
The goal of the network is to create a mesh network with VLAN, so guests are isolated from the LAN, as I've understood, the only way for me to get VLAN over wifi is using batman-adv, since just making a guest network on the 2nd node will not allow the clients to recieve IPs from DHCP.
For now I'm using a working WDS solution, but it requires the same WiFi networks on both devices in order to expand them, so an AP at main with wds enabled, in the 2nd node -> a guest AP(wds) + actual guest AP.
I've just recently tried setting up a mesh network with batman-adv and now I'm having wpa_supplicant problems, where the mesh does go up with 5Ghz, with 2.4Ghz the interface doesn't even initialize, no idea why it can't set channel or hw_mode according to the logread.
I'm assuming it's either how I've installed the kernel modules(self-compiled) or it's a problem specifically with wpad_mesh_openssl, or even a configuration error, I hope to find the cause of the problem instead of re-compiling, so any help is appreciated.
1st node is an R6220
2nd node is a Newfi D1 (this one seems to work and it shows as a peer in the following logread)
![]() Update:
Update:
It seems both devices don't support mesh point(even though iw dev shows they do) with their 2.4Ghz radio, 5Ghz the only one that works, the problem isn't batman-adv, it's obviously the native mesh and I'm guessing the driver.
Batman still doesn't work and is disabled (batctl n tells bat0 is disabled) even though mesh in radio1 works.
![]() Update 2:
Update 2:
Seems that mac80211's driver just failed a command, the weird thing is I can set that very same command afterwards with no error, bat0 is still disabled though.
logread | grep 'mac80211'
Sat Sep 4 02:28:01 2021 user.notice mac80211: Failed command: iw dev wlan1 set mesh_param mesh_fwding 0
Sat Sep 4 02:27:57 2021 user.notice mac80211: Failed command: iw phy phy0 set antenna 0xffffffff 0xffffffff
service network restart && logread | grep 'netifd|command failed|bat0'
Sat Sep 4 02:27:49 2021 daemon.notice netifd: VLAN 'eth0.4' link is down
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Interface 'lan' is now down
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Interface 'lan' is disabled
Sat Sep 4 02:27:49 2021 daemon.notice netifd: bridge 'br-guest' link is down
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Interface 'guest' has link connectivity loss
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Network device 'bat0' link is down
Sat Sep 4 02:27:49 2021 daemon.notice netifd: VLAN 'bat0.1' link is down
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Network device 'wlan1' link is down
Sat Sep 4 02:27:49 2021 daemon.notice netifd: VLAN 'eth0.1' link is down
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Interface 'lan' has link connectivity loss
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Interface 'loopback' is now down
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Interface 'loopback' is disabled
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Network device 'lo' link is down
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Interface 'loopback' has link connectivity loss
Sat Sep 4 02:27:49 2021 daemon.notice netifd: Interface 'wlan' is now down
Sat Sep 4 02:27:50 2021 daemon.notice netifd: Interface 'wlan' is disabled
Sat Sep 4 02:27:50 2021 daemon.notice netifd: Network device 'wlan0' link is down
Sat Sep 4 02:27:50 2021 daemon.notice netifd: VLAN 'eth0.3' link is down
Sat Sep 4 02:27:50 2021 daemon.notice netifd: bridge 'br-wlan' link is down
Sat Sep 4 02:27:50 2021 daemon.notice netifd: Interface 'wlan' has link connectivity loss
Sat Sep 4 02:27:50 2021 daemon.notice netifd: Network device 'wlan1-1' link is down
Sat Sep 4 02:27:51 2021 daemon.notice netifd: Network device 'pppoe-wan' link is down
Sat Sep 4 02:27:51 2021 daemon.notice netifd: Interface 'wan' is now down
Sat Sep 4 02:27:51 2021 daemon.notice netifd: Interface 'wan' is disabled
Sat Sep 4 02:27:51 2021 daemon.notice netifd: VLAN 'eth0.2' link is down
Sat Sep 4 02:27:51 2021 daemon.notice netifd: Interface 'wan' has link connectivity loss
Sat Sep 4 02:27:51 2021 daemon.notice netifd: Network device 'eth0' link is down
Sat Sep 4 02:27:55 2021 daemon.notice netifd: Interface 'guest' is enabled
Sat Sep 4 02:27:55 2021 daemon.notice netifd: Interface 'guest' is setting up now
Sat Sep 4 02:27:55 2021 daemon.notice netifd: Interface 'guest' is now up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'wlan' is enabled
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'wlan' is setting up now
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'wlan' is now up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'bat0' is setting up now
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'lan' is enabled
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'lan' is setting up now
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'lan' is now up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'loopback' is enabled
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'loopback' is setting up now
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'loopback' is now up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'wan' is enabled
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Network device 'eth0' link is up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: VLAN 'eth0.4' link is up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: VLAN 'eth0.3' link is up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: VLAN 'eth0.1' link is up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'lan' has link connectivity
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Network device 'lo' link is up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'loopback' has link connectivity
Sat Sep 4 02:27:56 2021 daemon.notice netifd: VLAN 'eth0.2' link is up
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'wan' has link connectivity
Sat Sep 4 02:27:56 2021 daemon.notice netifd: Interface 'wan' is setting up now
Sat Sep 4 02:27:56 2021 kern.info kernel: [23926.904368] 8021q: adding VLAN 0 to HW filter on device bat0
Sat Sep 4 02:27:56 2021 kern.info kernel: [23926.945983] br-guest: port 2(bat0.2) entered blocking state
Sat Sep 4 02:27:56 2021 kern.info kernel: [23926.957613] br-guest: port 2(bat0.2) entered disabled state
Sat Sep 4 02:27:56 2021 kern.info kernel: [23926.969599] device bat0.2 entered promiscuous mode
Sat Sep 4 02:27:56 2021 kern.info kernel: [23926.979210] device bat0 entered promiscuous mode
Sat Sep 4 02:27:56 2021 kern.info kernel: [23926.988850] br-guest: port 2(bat0.2) entered blocking state
Sat Sep 4 02:27:56 2021 kern.info kernel: [23927.000040] br-guest: port 2(bat0.2) entered listening state
Sat Sep 4 02:27:57 2021 kern.info kernel: [23927.148973] br-wlan: port 2(bat0.1) entered blocking state
Sat Sep 4 02:27:57 2021 kern.info kernel: [23927.160016] br-wlan: port 2(bat0.1) entered disabled state
Sat Sep 4 02:27:57 2021 kern.info kernel: [23927.171520] device bat0.1 entered promiscuous mode
Sat Sep 4 02:27:57 2021 kern.info kernel: [23927.181497] br-wlan: port 2(bat0.1) entered blocking state
Sat Sep 4 02:27:57 2021 kern.info kernel: [23927.192514] br-wlan: port 2(bat0.1) entered listening state
Sat Sep 4 02:27:57 2021 daemon.notice netifd: Network device 'bat0' link is up
Sat Sep 4 02:27:57 2021 daemon.notice netifd: VLAN 'bat0.2' link is up
Sat Sep 4 02:27:57 2021 daemon.notice netifd: VLAN 'bat0.1' link is up
Sat Sep 4 02:27:57 2021 daemon.notice netifd: Interface 'bat0' is now up
Sat Sep 4 02:27:59 2021 kern.info kernel: [23929.045740] br-guest: port 2(bat0.2) entered learning state
Sat Sep 4 02:27:59 2021 kern.info kernel: [23929.277183] br-wlan: port 2(bat0.1) entered learning state
Sat Sep 4 02:27:59 2021 daemon.notice netifd: Network device 'pppoe-wan' link is up
Sat Sep 4 02:27:59 2021 daemon.notice netifd: Interface 'wan' is now up
Sat Sep 4 02:27:59 2021 daemon.notice netifd: bridge 'br-guest' link is up
Sat Sep 4 02:27:59 2021 daemon.notice netifd: Interface 'guest' has link connectivity
Sat Sep 4 02:28:00 2021 daemon.notice netifd: bridge 'br-wlan' link is up
Sat Sep 4 02:28:00 2021 daemon.notice netifd: Interface 'wlan' has link connectivity
Sat Sep 4 02:28:00 2021 daemon.notice netifd: Network device 'wlan0' link is up
Sat Sep 4 02:28:01 2021 kern.info kernel: [23931.117149] br-guest: port 2(bat0.2) entered forwarding state
Sat Sep 4 02:28:01 2021 kern.info kernel: [23931.357378] br-wlan: port 2(bat0.1) entered forwarding state
Sat Sep 4 02:28:01 2021 daemon.notice netifd: radio1 (14092): command failed: Link has been severed (-67)
Sat Sep 4 02:28:02 2021 daemon.notice netifd: Network device 'wlan1' link is up
Sat Sep 4 02:28:05 2021 daemon.notice netifd: Network device 'wlan1-1' link is up
![]() Update 3:
Update 3:
Tried to manually add a mesh interface
iw phy phy0 interface add mesh0 type mp mesh_id mymesh
ip a # shows mesh0 is there
ip link set mesh0 up
ip link # shows mesh0 is still down
logread | grep mesh0 && dmesg | grep mesh0 show the same thing:
IPv6: ADDRCONF(NETDEV_UP): mesh0: link is not ready
Weird thing is, I may have IPv6 support but I don't use IPv6 and it's cancelled in the network configuration.
![]() Unfortunately, the next step is re-compiling.
Unfortunately, the next step is re-compiling.
![]() Update 4:
Update 4:
Tried using the wpad-mesh-wolfssl package, no difference, 2.4Ghz radio refuses to set up a mesh, 5.0Ghz does establish a mesh and the interface is up.
Process with wpad-mesh-wolfssl
$ iw phy phy1 interface add mesh1 type mp mesh_id mymesh
$ ip link set mesh1 up
# all good
$ iw phy phy0 interface add mesh0 type mp mesh_id mymesh
$ ip link set mesh0 up
# returns:
$ ip: SIOCSIFFLAGS: No error information
ip link
# returns:
34: mesh0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether <broadcast> brd ff:ff:ff:ff:ff:ff
35: mesh1: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN qlen 1000
link/ether <redacted> brd ff:ff:ff:ff:ff:ff
So this actually could be related to the Mediatek driver.
![]() Update 5:
Update 5:
Tried to use a pre-compiled image from the OpenWrt downloads section and used a v19.07.8 image instead of re-compiling, which should work since nothing related to my compiling environment can interfere, unforunately the problem persists.
First, I don't know if it's known, LuCI doesn't support the values for mesh, it's displayed as if the encryption set is incompatible with 802.11s, configuring the files directly is the only way and I tried setting both 2.4Ghz and 5.0Ghz, it seems that without encryption both of the radios work, but once you set the encryption to sae, psk2/sae or even psk2+ccmp, the 2.4Ghz radio stops working and doesn't initialize, 5.0Ghz does work like before, this is probably a bug..
Besides that, with both working radios without encryption, batman-adv doesn't work... still bat0 is considered disabled when using batman n...
Conclusion: 802.11s doesn't work with batman-adv on r6220 and probably other mediatek devices like my newifi D1, my only solution for now is WDS.
![]() Update 6:
Update 6:
Tried to use the full wpad-wolfssl package, didn't change the outcome when using the 2.4Ghz radio for mesh.
logread | grep wpa_supplicant
Wed Sep 8 14:30:30 2021 daemon.notice wpa_supplicant[4174]: Successfully initialized wpa_supplicant
Wed Sep 8 14:30:31 2021 daemon.notice wpa_supplicant[4333]: Successfully initialized wpa_supplicant
Wed Sep 8 14:30:33 2021 daemon.err wpa_supplicant[4375]: Could not select hw_mode and channel. (-3)
Wed Sep 8 14:30:33 2021 daemon.notice wpa_supplicant[4375]: wlan0: interface state UNINITIALIZED->DISABLED
Wed Sep 8 14:30:33 2021 daemon.notice wpa_supplicant[4375]: wlan0: AP-DISABLED
Wed Sep 8 14:30:33 2021 daemon.err wpa_supplicant[4375]: wlan0: Unable to setup interface.
Wed Sep 8 14:30:33 2021 daemon.err wpa_supplicant[4375]: Failed to initialize hostapd interface for mesh
Wed Sep 8 14:30:33 2021 daemon.err wpa_supplicant[4375]: wlan0: Failed to init mesh
Wed Sep 8 14:30:33 2021 daemon.err wpa_supplicant[4210]: Using interface wlan1 with hwaddr <redacted> and ssid ""
Wed Sep 8 14:30:33 2021 daemon.notice wpa_supplicant[4210]: wlan1: interface state UNINITIALIZED->ENABLED
Wed Sep 8 14:30:33 2021 daemon.notice wpa_supplicant[4210]: wlan1: AP-ENABLED
Wed Sep 8 14:30:33 2021 daemon.notice wpa_supplicant[4210]: wlan1: joining mesh <redacted>
Wed Sep 8 14:30:34 2021 daemon.notice wpa_supplicant[4210]: wlan1: CTRL-EVENT-CONNECTED - Connection to 00:00:00:00:00:00 completed [id=0 id_str=]
Wed Sep 8 14:30:34 2021 daemon.notice wpa_supplicant[4210]: wlan1: MESH-GROUP-STARTED ssid="<redacted>" id=0
Wed Sep 8 14:30:34 2021 daemon.notice wpa_supplicant[4375]: nl80211: Failed to set interface into station mode
Wed Sep 8 14:30:34 2021 daemon.err wpa_supplicant[4375]: wlan0: Could not join mesh
![]() Update 7:
Update 7:
Thanks to @anon77520754 I've managed to get a working mesh with the 2.4Ghz radio, but I switched to channel 1, where it was previously channel 11(where it didn't associate), it seems that using either wpad-wolfssl or wpad-mesh-wolfssl works -> everything was essentially a problem with the Newifi D1's radio not supporting channel 11 when in meshpoint mode, I no longer have space for this post so logs and problems are present in the bug tracker(https://bugs.openwrt.org/index.php?do=details&task_id=4036)
![]() Update 8:
Update 8:
Batman solution with version 21.02.0
![]() Configuration and logread
Configuration and logread
logread | grep wpa_supplicant
Fri Sep 3 13:06:51 2021 daemon.notice wpa_supplicant[8522]: Successfully initialized wpa_supplicant
Fri Sep 3 13:06:52 2021 daemon.notice wpa_supplicant[8643]: Successfully initialized wpa_supplicant
Fri Sep 3 13:06:53 2021 daemon.err wpa_supplicant[8569]: Could not select hw_mode and channel. (-3)
Fri Sep 3 13:06:53 2021 daemon.notice wpa_supplicant[8569]: wlan0: interface state UNINITIALIZED->DISABLED
Fri Sep 3 13:06:53 2021 daemon.notice wpa_supplicant[8569]: wlan0: AP-DISABLED
Fri Sep 3 13:06:53 2021 daemon.err wpa_supplicant[8569]: wlan0: Unable to setup interface.
Fri Sep 3 13:06:53 2021 daemon.err wpa_supplicant[8569]: Failed to initialize hostapd interface for mesh
Fri Sep 3 13:06:53 2021 daemon.err wpa_supplicant[8569]: wlan0: Failed to init mesh
Fri Sep 3 13:06:54 2021 daemon.err wpa_supplicant[8715]: Using interface wlan1 with hwaddr <redacted> and ssid ""
Fri Sep 3 13:06:54 2021 daemon.notice wpa_supplicant[8715]: wlan1: interface state UNINITIALIZED->ENABLED
Fri Sep 3 13:06:54 2021 daemon.notice wpa_supplicant[8715]: wlan1: AP-ENABLED
Fri Sep 3 13:06:54 2021 daemon.notice wpa_supplicant[8715]: wlan1: joining mesh <redacted>
Fri Sep 3 13:06:54 2021 daemon.notice wpa_supplicant[8715]: wlan1: CTRL-EVENT-CONNECTED - Connection to 00:00:00:00:00:00 completed [id=0 id_str=]
Fri Sep 3 13:06:54 2021 daemon.notice wpa_supplicant[8715]: wlan1: MESH-GROUP-STARTED ssid="<redacted>" id=0
Fri Sep 3 13:06:54 2021 daemon.notice wpa_supplicant[8569]: nl80211: Failed to set interface into station mode
Fri Sep 3 13:06:54 2021 daemon.err wpa_supplicant[8569]: wlan0: Could not join mesh
Fri Sep 3 13:06:55 2021 daemon.notice wpa_supplicant[8715]: wlan1: new peer notification for <redacted>
Fri Sep 3 13:06:55 2021 daemon.notice wpa_supplicant[8715]: wlan1: new peer notification for <redacted>
Fri Sep 3 13:06:55 2021 daemon.notice wpa_supplicant[8715]: wlan1: new peer notification for <redacted>
Fri Sep 3 13:06:55 2021 daemon.notice wpa_supplicant[8715]: wlan1: mesh plink with <redacted> established
Fri Sep 3 13:06:55 2021 daemon.notice wpa_supplicant[8715]: wlan1: MESH-PEER-CONNECTED <redacted>
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8569]: wlan0: MESH-GROUP-REMOVED wlan0
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8569]: wlan0: leaving mesh
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8569]: wlan0: interface state DISABLED->DISABLED
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8569]: wlan0: AP-DISABLED
Fri Sep 3 13:11:09 2021 daemon.err wpa_supplicant[8569]: hostapd_free_hapd_data: Interface wlan0 wasn't started
Fri Sep 3 13:11:09 2021 daemon.err wpa_supplicant[8569]: wlan0: mesh leave error=-134
Fri Sep 3 13:11:09 2021 daemon.err wpa_supplicant[8569]: Failed to stop hostapd AP interfaces
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8569]: nl80211: deinit ifname=wlan0 disabled_11b_rates=0
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8569]: wlan0: CTRL-EVENT-TERMINATING
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8715]: wlan1: MESH-GROUP-REMOVED wlan1
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8715]: wlan1: leaving mesh
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8715]: wlan1: interface state ENABLED->DISABLED
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8715]: wlan1: AP-DISABLED
Fri Sep 3 13:11:09 2021 daemon.err wpa_supplicant[8715]: Failed to stop hostapd AP interfaces
Fri Sep 3 13:11:09 2021 daemon.notice wpa_supplicant[8715]: nl80211: deinit ifname=wlan1 disabled_11b_rates=0
Fri Sep 3 13:11:10 2021 daemon.notice wpa_supplicant[8715]: wlan1: CTRL-EVENT-TERMINATING
Fri Sep 3 13:11:10 2021 daemon.notice wpa_supplicant[8715]: ELOOP: remaining socket: sock=25 eloop_data=0x8c73d0 user_data=0 handler=0x46c8a9
Fri Sep 3 13:11:12 2021 daemon.notice wpa_supplicant[10554]: Successfully initialized wpa_supplicant
Fri Sep 3 13:11:13 2021 daemon.notice wpa_supplicant[10689]: Successfully initialized wpa_supplicant
Fri Sep 3 13:11:13 2021 daemon.err wpa_supplicant[10583]: Could not select hw_mode and channel. (-3)
Fri Sep 3 13:11:13 2021 daemon.notice wpa_supplicant[10583]: wlan0: interface state UNINITIALIZED->DISABLED
Fri Sep 3 13:11:13 2021 daemon.notice wpa_supplicant[10583]: wlan0: AP-DISABLED
Fri Sep 3 13:11:13 2021 daemon.err wpa_supplicant[10583]: wlan0: Unable to setup interface.
Fri Sep 3 13:11:13 2021 daemon.err wpa_supplicant[10583]: Failed to initialize hostapd interface for mesh
Fri Sep 3 13:11:13 2021 daemon.err wpa_supplicant[10583]: wlan0: Failed to init mesh
Fri Sep 3 13:11:15 2021 daemon.err wpa_supplicant[10746]: Using interface wlan1 with hwaddr <redacted> and ssid ""
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10746]: wlan1: interface state UNINITIALIZED->ENABLED
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10746]: wlan1: AP-ENABLED
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10746]: wlan1: joining mesh <redacted>
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10746]: wlan1: CTRL-EVENT-CONNECTED - Connection to 00:00:00:00:00:00 completed [id=0 id_str=]
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10746]: wlan1: MESH-GROUP-STARTED ssid="<redacted>" id=0
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10746]: wlan1: new peer notification for <redacted>
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10583]: nl80211: Failed to set interface into station mode
Fri Sep 3 13:11:15 2021 daemon.err wpa_supplicant[10583]: wlan0: Could not join mesh
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10746]: wlan1: new peer notification for <redacted>
Fri Sep 3 13:11:15 2021 daemon.err wpa_supplicant[10746]: Mesh RSN: frame verification failed!
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10746]: wlan1: mesh plink with <redacted> established
Fri Sep 3 13:11:15 2021 daemon.notice wpa_supplicant[10746]: wlan1: MESH-PEER-CONNECTED <redacted>
Important notes:
- self-compiled my openwrt image (v19.08.7)
** Only minimal packages were included, the rest were installed manually (like wpad_mesh_openssl and its dependencies) - removed wpad_basic and installed wpad_mesh_openssl
- ran uci show on each configuration to make sure nothing's invalid
- force installed batman-adv because of kernel mismatch (occurs with self-compiled images, but the package was self-compiled and not downloaded)
- I've tried using psk2+ccmp instead of aes for mesh encryption with no success.
Installed packages
base-files - 204.4-r11364-ef56c85848
batctl-default - 2019.2-8
block-mount - 2020-05-12-84269037-1
busybox - 1.30.1-6
dnsmasq - 2.80-16.3
dropbear - 2019.78-2
firewall - 2019-11-22-8174814a-3
fstools - 2020-05-12-84269037-1
fwtool - 2
getrandom - 2019-06-16-4df34a4d-4
hostapd-common - 2019-08-08-ca8c2bd2-7
iftop - 2018-10-03-77901c8c-1
ip6tables - 1.8.3-1
iptables - 1.8.3-1
iptables-mod-conntrack-extra - 1.8.3-1
iptables-mod-ipopt - 1.8.3-1
irqbalance - 1.8.0-1
iw - 5.0.1-1
iwinfo - 2019-10-16-07315b6f-1
jshn - 2020-05-25-66195aee-1
jsonfilter - 2018-02-04-c7e938d6-1
kernel - 4.14.241-1-47f2710eacd794b19551333b9eba3705
kmod-batman-adv - 4.14.241+2019.2-12
kmod-cfg80211 - 4.14.241+4.19.193-1-1
kmod-crypto-acompress - 4.14.241-1
kmod-crypto-crc32 - 4.14.241-1
kmod-crypto-crc32c - 4.14.241-1
kmod-crypto-hash - 4.14.241-1
kmod-fs-exfat - 4.14.241+2018-04-17-01c30ad5-2
kmod-fs-ext4 - 4.14.241-1
kmod-fs-f2fs - 4.14.241-1
kmod-fs-vfat - 4.14.241-1
kmod-gpio-button-hotplug - 4.14.241-3
kmod-ifb - 4.14.241-1
kmod-ip6tables - 4.14.241-1
kmod-ipt-conntrack - 4.14.241-1
kmod-ipt-conntrack-extra - 4.14.241-1
kmod-ipt-core - 4.14.241-1
kmod-ipt-ipopt - 4.14.241-1
kmod-ipt-nat - 4.14.241-1
kmod-ipt-offload - 4.14.241-1
kmod-ipt-raw - 4.14.241-1
kmod-leds-gpio - 4.14.241-1
kmod-lib-crc-ccitt - 4.14.241-1
kmod-lib-crc16 - 4.14.241-1
kmod-lib-crc32c - 4.14.241-1
kmod-lib-lz4 - 4.14.241-1
kmod-lib-lzo - 4.14.241-1
kmod-mac80211 - 4.14.241+4.19.193-1-1
kmod-mt76-core - 4.14.241+2021-02-15-5c768dec-1
kmod-mt7603 - 4.14.241+2021-02-15-5c768dec-1
kmod-mt76x02-common - 4.14.241+2021-02-15-5c768dec-1
kmod-mt76x2 - 4.14.241+2021-02-15-5c768dec-1
kmod-mt76x2-common - 4.14.241+2021-02-15-5c768dec-1
kmod-nf-conntrack - 4.14.241-1
kmod-nf-conntrack6 - 4.14.241-1
kmod-nf-flow - 4.14.241-1
kmod-nf-ipt - 4.14.241-1
kmod-nf-ipt6 - 4.14.241-1
kmod-nf-nat - 4.14.241-1
kmod-nf-reject - 4.14.241-1
kmod-nf-reject6 - 4.14.241-1
kmod-nls-base - 4.14.241-1
kmod-nls-cp437 - 4.14.241-1
kmod-nls-iso8859-1 - 4.14.241-1
kmod-nls-utf8 - 4.14.241-1
kmod-ppp - 4.14.241-1
kmod-pppoe - 4.14.241-1
kmod-pppox - 4.14.241-1
kmod-sched-cake - 4.14.241+2019-03-12-057c7388-1
kmod-sched-core - 4.14.241-1
kmod-scsi-core - 4.14.241-1
kmod-slhc - 4.14.241-1
kmod-usb-core - 4.14.241-1
kmod-usb-ehci - 4.14.241-1
kmod-usb-ledtrig-usbport - 4.14.241-1
kmod-usb-storage - 4.14.241-1
kmod-usb-storage-uas - 4.14.241-1
kmod-usb2 - 4.14.241-1
kmod-zram - 4.14.241-1
libblobmsg-json - 2020-05-25-66195aee-1
libc - 1.1.24-2
libelf1 - 0.177-1
libgcc1 - 8.3.0-2
libip4tc2 - 1.8.3-1
libip6tc2 - 1.8.3-1
libiwinfo20181126 - 2019-10-16-07315b6f-1
libjson-c2 - 0.12.1-3.1
libjson-script - 2020-05-25-66195aee-1
libncurses6 - 6.1-5
libnl-tiny - 0.1-5
libopenssl1.1 - 1.1.1k-1
libpcap1 - 1.9.1-2.1
libpthread - 1.1.24-2
librt - 1.1.24-2
libubox20191228 - 2020-05-25-66195aee-1
libubus20210603 - 2021-07-01-38c7fdd8-1
libuci20130104 - 2019-09-01-415f9e48-4
libuclient20160123 - 2020-06-17-51e16ebf-1
libxtables12 - 1.8.3-1
logd - 2019-06-16-4df34a4d-4
mtd - 24
netifd - 2021-01-09-753c351b-1
odhcp6c - 2021-01-09-64e1b4e7-16
odhcpd-ipv6only - 2020-05-03-49e4949c-3
openwrt-keyring - 2021-02-20-49283916-2
opkg - 2021-01-31-c5dccea9-1
ppp - 2.4.7.git-2019-05-25-3
ppp-mod-pppoe - 2.4.7.git-2019-05-25-3
procd - 2020-03-07-09b9bd82-1
sqm-scripts - 1.4.0-2
swconfig - 12
tc - 5.0.0-2.1
terminfo - 6.1-5
ubi-utils - 2.1.1-1
ubox - 2019-06-16-4df34a4d-4
ubus - 2021-07-01-38c7fdd8-1
ubusd - 2021-07-01-38c7fdd8-1
uci - 2019-09-01-415f9e48-4
uclient-fetch - 2020-06-17-51e16ebf-1
urandom-seed - 1.0-1
urngd - 2020-01-21-c7f7b6b6-1
usign - 2020-05-23-f1f65026-1
wireless-regdb - 2020.11.20-1
wpad-mesh-openssl - 2019-08-08-ca8c2bd2-7
zlib - 1.2.11-3
zram-swap - 1.1-3
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'lan'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.254'
option gateway '192.168.1.254'
option netmask '255.255.255.0'
option dns '1.1.1.1 8.8.8.8'
option mtu '2048' # Jumbo frames, max mtu for r6220
option ipv6 'no'
option force_link 'yes' # required for static proto
option igmp_snooping '1' # multicast optimization
option stp '1' # (bridge only) STP protocol prevents network loops
config device 'lan_eth0_1_dev'
option name 'eth0.1'
option macaddr '<redacted>'
config interface 'wlan'
option type 'bridge'
option ifname 'eth0.3 bat0.1' # notice bat0 for mesh
option proto 'static'
option ipaddr '192.168.2.254'
option gateway '192.168.2.254'
option netmask '255.255.255.0'
option dns '1.1.1.1 8.8.8.8'
option mtu '2304' # Jumbo frames, max mtu for wireless
option ipv6 'no'
option force_link 'yes' # required for static proto
option igmp_snooping '1' # multicast optimization
option stp '1' # (bridge only) STP protocol prevents network loops
config interface 'guest'
option type 'bridge'
option ifname 'eth0.4 bat0.2' # notice bat0 for mesh
option proto 'static'
option ipaddr '192.168.3.254'
option gateway '192.168.3.254'
option netmask '255.255.255.0'
option dns '1.1.1.1 8.8.8.8'
option mtu '2304' # Jumbo frames support for wireless
option ipv6 'no'
option force_link 'yes'
option igmp_snooping '1'
option stp '1' # (bridge only) STP protocol prevents network loops
config interface 'wan'
option ifname 'eth0.2'
option proto 'pppoe'
option peerdns '0' # Use peer-assigned DNS servers(from ISP)
option dns '1.1.1.1 8.8.8.8' # Override peer-assigned DNS
option username '<redacted>'
option password '<redacted>'
option delegate '0' # IPv6, enable prefix delegation(DS-lite/map/464xlat)
option ipv6 '0'
option mtu '1492' # PPPoE max
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr '<redacted>'
# Mesh
config interface 'bat0'
option proto 'batadv'
option routing_algo 'BATMAN_IV'
option aggregated_ogms 1
option ap_isolation 0
option bonding 0
option fragmentation 1
option gw_mode 'server'
option gw_bandwidth '100mbit/3500kbit' # server mode only
#option gw_sel_class 20 # client mode only
option log_level 0
option orig_interval 300000 # 60sec * 5 = 300sec, 5 minutes since only 2 nodes
option bridge_loop_avoidance 1
option distributed_arp_table 1
option multicast_mode 1
option multicast_fanout 16
option network_coding 0 # need 3 nodes for this
option hop_penalty 30
option isolation_mark '0x00000000/0x00000000'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
/etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'pci0000:00/0000:00:01.0/0000:02:00.0'
option channel '11' # set channel or set auto(ACS support required)
option channels '1 6 11' # list channels to be used by auto
option hwmode '11g' # 11g is n, 11bg is b/g/n, 11b is legacy
option htmode 'HT40' # channel width 20/40 (auto set by interference)
#option require_mode 'n' # require n, b/g will not work, ac can be set
option legacy_rates '0' # don't allow 11b rates, legacy devices may need it
#option beacon_int '75' # default is 100, less drains battery but improves connectivity
#option noscan '1' # No automatic channel width, doesn't scan others
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'wlan' # defined in network file
option mode 'ap'
option ssid '<redacted>'
option hidden '1' # hide ssid
option key '<redacted>'
option encryption 'psk2+aes'
option wmm '1' # QoS, required for 11n and up
option maxassoc '15' # max clients to connect - only family
option short_preamble '1' # less error-checks but faster
option wds '0' # 4 address mode (WDS)
option wpa_disable_eapol_key_retries '1' # against key re-install attacks, delays frame transmittion, but can cause interoperability and robustness issues
option tdls_prohibit '1' # no TDLS, complicates key reinstallation attacks
option ieee80211r '1' # 802.11r fast-roaming (reqires same SSID)
option nasid '<redacted>' # unique per ap
option mobility_domain '<redacted>' # must be shared between APs with the same SSID (4 hex only)
option ft_psk_generate_local '1' # generate FT responses locally without contacting other APs
config wifi-device 'radio1'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0/0000:01:00.0'
option channel '36'
option legacy_rates '0'
option hwmode '11a' # required for 5Ghz
option htmode 'VHT80' # max support for R6220
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'wlan'
option mode 'ap'
option ssid '<redacted>'
option hidden '1'
option encryption 'psk2+aes'
option key '<redacted>'
option wmm '1' # required for 5Ghz
option maxassoc '15'
option short_preamble '1'
option wds '0'
option wpa_disable_eapol_key_retries '1'
option tdls_prohibit '1'
option ieee80211r '1'
option nasid '<redacted>'
option mobility_domain '<redacted>'
option ft_psk_generate_local '1'
# Mesh
config wifi-iface 'mesh0'
option network 'wlan' # bridge with ap's network for mesh to work + batman
option device 'radio0'
option mode 'mesh'
option mesh_fwding '0' # For Batman
option mesh_id '<redacted>' # id shared between routers
option encryption 'sae' # wpa3, encrypts ONLY the mesh
option key '<redacted>' # password shared between routers
config wifi-iface 'mesh1'
option network 'wlan'
option device 'radio1'
option mode 'mesh'
option mesh_fwding '0'
option mesh_id '<redacted>'
option encryption 'sae' # wpa3, encrypts ONLY the mesh
option key '<redacted>'
Self compilation process:
*P* -> Pre install
*M* -> Manual install for later
*R* -> Remove if present
Base System::
* (P) block-mount -> mount filesystems
* (P/M) sqm-scripts -> enable SQM
Kernel Modules::
Filesystems;;
* (P) kmod-fs-f2fs -> support sdcard filesystem
* (M) kmod-fs-ext4 -> ext4 filesystem
* (M) kmod-fs-vfat -> fat/fat16/fat32 filesystem
* (M) kmod-fs-exfat -> exfat filesystem
USB Support;;
* (P) kmod-usb2 -> usb2 support (for usb expansion)
* (P) kmod-usb-storage -> usb storage support
* (P) kmod-usb-storage-uas -> some usb drives need this
* (R) kmod-usb3 -> usb3 interferes with 2.4Ghz
Network Support;;
* (M) kmod-batman-adv -> Batman Advanced for mesh with VLAN
Network::
* (M) batctl-default -> Batman debug/config tool
* (M) iftop -> network bandwidth monitor
* (M) wpad-mesh-openssl -> remove wpad-basic before doing so
Utilities::
* (M) irqbalance -> performance of multiple logical CPUs
Dependencies
------------
sqm-scripts::
* tc
* kmod-sched-core
* kmod-sched-cake
* kmod-ifb
* iptables-mod-ipopt
* iptables-mod-conntrack-extra
* kmod-ipt-raw
* kmod-ipt-ipopt
* libelf
* zlib
kmod-batman-adv::
* kmod-lib-crc16
* kmod-lib-crc32c
kmod-fs-ext4::
* kmod-lib-crc16
* kmod-crypto-crc32c
kmod-fs-vfat::
* kmod-nls-cp437
* kmod-nls-iso8859-1
* kmod-nls-utf8
kmod-usb-storage-uas::
* kmod-scsi-core
kmod-usb2::
* kmod-usb-ehci
wpad-mesh-openssl::
* libopenssl1.1
batctl-default::
* librt
iftop::
* libpcap1
* libncurses6
* terminfo
Post-compile
------------
Use scp to upload all the <M> packages to root@192.168.1.1:/tmp
opkg install /tmp/*.ipk
Enable & start services: **sqm** and **irqbalance**.
Commands used:
git clone https://git.openwrt.org/openwrt/openwrt.git # was done long ago
git fetch
git checkout v19.07.8
umask 022
./scripts/feeds update -a
./scripts/feeds install -a
make menuconfig # Here I choose all the packages as explained above + target device
make defconfig # Remove any optional dependenciesons
make -j5 download world

 I really appreciate your help, thank you.
I really appreciate your help, thank you. Update:
Update: