PetrP
June 21, 2024, 8:55pm
1
I just added new firewall zone, and it's empty in nft tables. Can't figure out how to block connections on newly created zone. No matter what I set in LUCI, nft is empty, and the actual connections do not get blocked. How do I block connections, drop or reject?
nft list tables:
chain input_iconnect {
}
chain output_iconnect {
}
chain forward_iconnect {
}
brada4
June 21, 2024, 8:59pm
2
luci firewall operates only on table inet fw4 (or in ancient version on iptables customary renderings)nft list ruleset ?ubus call system board (colour scheme does not look 100% openwrt)
PetrP
June 21, 2024, 9:03pm
3
nft list ruleset
chain input_iconnect {
counter packets 0 bytes 0 jump handle_reject comment "!fw4: Iconnect diable all"
jump drop_from_iconnect
}
chain output_iconnect {
jump drop_to_iconnect
}
chain forward_iconnect {
jump drop_to_iconnect
}
chain helper_iconnect {
}
chain accept_to_iconnect {
}
chain reject_from_iconnect {
}
chain reject_to_iconnect {
}
chain drop_from_iconnect {
iifname "br-lan" counter packets 0 bytes 0 drop comment "!fw4: drop iconnect IPv4/IPv6 traffic"
}
chain drop_to_iconnect {
oifname "br-lan" counter packets 0 bytes 0 drop comment "!fw4: drop iconnect IPv4/IPv6 traffic"
}
firewall
config zone
option name 'iconnect'
option input 'DROP'
option output 'DROP'
option forward 'DROP'
list network 'interconnect'
however, ping and ssh do work, and I want them to stop.
brada4
June 21, 2024, 9:04pm
4
You need to drop states with conntrack -D or wait 6h for all them to sever.
PetrP
June 21, 2024, 9:47pm
5
How do I? I just set it in Luci. Rebooting does not help
BTW, this is (both routers) an alias interface with a separate IP.
chain accept_from_iconnect {
iifname { "wan", "wgIC" } counter packets 0 bytes 0 accept comment "!fw4: accept iconnect IPv4/IPv6 traffic"
}
chain accept_to_iconnect {
oifname { "wan", "wgIC" } counter packets 0 bytes 0 accept comment "!fw4: accept iconnect IPv4/IPv6 traffic"
}
chain reject_to_iconnect {
oifname { "wan", "wgIC" } counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject iconnect IPv4/IPv6 traffic"
}
These rules are also listed
krazeh
June 21, 2024, 10:16pm
6
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/firewall
2 Likes
brada4
June 22, 2024, 12:16am
7
Which part of full ruleset and full config files is so hard to get?
PetrP
June 22, 2024, 3:45am
8
The goal I want to reach is to connect two networks behind routers together via two additional networks: first one insecure, 10.100.100.0/24, and the second one secure Wireguard network which is not created yet.
For the insecure network 10.100.100.0 I want to block all except ICMP and ssh.
ubus call system board
{
"kernel": "5.15.134",
"hostname": "host1",
"system": "MediaTek MT7621 ver:1 eco:4",
"model": "Xiaomi Redmi Router AC2100",
"board_name": "xiaomi,redmi-router-ac2100",/
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.0",
"revision": "r23497-6637af95aa",
"target": "ramips/mt7621",
"description": "OpenWrt 23.05.0 r23497-6637af95aa"
}
}
network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix '123::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.91.1'
option netmask '255.255.255.0'
config interface 'interconnect'
option device 'wan'
option proto 'static'
option ipaddr '10.100.100.2'
option netmask '255.255.255.0'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option delegate '0'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option auto '0'
option reqaddress 'try'
option reqprefix 'auto'
config interface 'Interconnect'
option proto 'wireguard'
option private_key '123'
config interface 'wgIC'
option proto 'wireguard'
option private_key '123'
list addresses '10.100.200.1'
firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option forward 'ACCEPT'
option mtu_fix '1'
option input 'ACCEPT'
option masq '1'
list network 'wan'
list network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'AllowRemoteLuci'
list proto 'tcp'
option src 'wan'
option dest_port '80'
option target 'ACCEPT'
option enabled '0'
config forwarding
option src 'wan'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'wan'
config zone
option name 'iconnect'
option input 'REJECT'
option output 'REJECT'
option forward 'REJECT'
list network 'interconnect'
list network 'wgIC'
config zone
option name 'iconnectInt'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
brada4
June 22, 2024, 7:19am
9
nft list ruleset
some zones do not seem to contain any interfaces to attach rules to?
PetrP
June 22, 2024, 7:59am
10
which zones? I can't see
and how do I set this up in Luci?
network
config interface 'interconnect'
option device 'wan'
option proto 'static'
option ipaddr '10.100.100.2'
option netmask '255.255.255.0'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option delegate '0'
ping 10.100.100.1 does work, but it shouldn't.
antonk
June 22, 2024, 8:07am
11
@PetrP if you want to get help, please read carefully which information is required.
1 Like
PetrP
June 22, 2024, 8:13am
12
Sorry
root@router2 ~# nft list ruleset
table inet fw4 {
flowtable ft {
hook ingress priority filter
devices = { lan1, lan2, lan3, wan }
flags offload
counter
}
chain input {
type filter hook input priority filter; policy accept;
iifname "lo" accept comment "!fw4: Accept traffic from loopback"
ct state established,related accept comment "!fw4: Allow inbound established and related flows"
tcp flags syn / fin,syn,rst,ack jump syn_flood comment "!fw4: Rate limit TCP syn packets"
iifname "br-lan" jump input_lan comment "!fw4: Handle lan IPv4/IPv6 input traffic"
iifname "wan" jump input_wan comment "!fw4: Handle wan IPv4/IPv6 input traffic"
iifname { "wan", "wgIC" } jump input_iconnect comment "!fw4: Handle iconnect IPv4/IPv6 input traffic"
}
chain forward {
type filter hook forward priority filter; policy drop;
meta l4proto { tcp, udp } flow add @ft
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
iifname "br-lan" jump forward_lan comment "!fw4: Handle lan IPv4/IPv6 forward traffic"
iifname "wan" jump forward_wan comment "!fw4: Handle wan IPv4/IPv6 forward traffic"
iifname { "wan", "wgIC" } jump forward_iconnect comment "!fw4: Handle iconnect IPv4/IPv6 forward traffic"
jump handle_reject
}
chain output {
type filter hook output priority filter; policy accept;
oifname "lo" accept comment "!fw4: Accept traffic towards loopback"
ct state established,related accept comment "!fw4: Allow outbound established and related flows"
oifname "br-lan" jump output_lan comment "!fw4: Handle lan IPv4/IPv6 output traffic"
oifname "wan" jump output_wan comment "!fw4: Handle wan IPv4/IPv6 output traffic"
oifname { "wan", "wgIC" } jump output_iconnect comment "!fw4: Handle iconnect IPv4/IPv6 output traffic"
}
chain prerouting {
type filter hook prerouting priority filter; policy accept;
iifname "br-lan" jump helper_lan comment "!fw4: Handle lan IPv4/IPv6 helper assignment"
iifname { "wan", "wgIC" } jump helper_iconnect comment "!fw4: Handle iconnect IPv4/IPv6 helper assignment"
}
chain handle_reject {
meta l4proto tcp reject with tcp reset comment "!fw4: Reject TCP traffic"
reject comment "!fw4: Reject any other traffic"
}
chain syn_flood {
limit rate 25/second burst 50 packets return comment "!fw4: Accept SYN packets below rate-limit"
drop comment "!fw4: Drop excess packets"
}
chain input_lan {
jump accept_from_lan
}
chain output_lan {
jump accept_to_lan
}
chain forward_lan {
jump accept_to_wan comment "!fw4: Accept lan to wan forwarding"
jump accept_to_lan
}
chain helper_lan {
}
chain accept_from_lan {
iifname "br-lan" counter packets 16350 bytes 2610153 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain accept_to_lan {
oifname "br-lan" counter packets 2140 bytes 165264 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain input_wan {
meta nfproto ipv4 udp dport 68 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCP-Renew"
icmp type echo-request counter packets 2 bytes 168 accept comment "!fw4: Allow-Ping"
meta nfproto ipv4 meta l4proto igmp counter packets 0 bytes 0 accept comment "!fw4: Allow-IGMP"
meta nfproto ipv6 udp dport 546 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCPv6"
ip6 saddr fe80::/10 icmpv6 type . icmpv6 code { mld-listener-query . no-route, mld-listener-report . no-route, mld-listener-done . no-route, mld2-listener-report . no-route } counter packets 0 bytes 0 accept comment "!fw4: Allow-MLD"
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply, nd-router-solicit, nd-router-advert } limit rate 1000/second counter packets 247 bytes 35232 accept comment "!fw4: Allow-ICMPv6-Input"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, nd-neighbor-solicit . no-route, nd-neighbor-advert . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 1316 bytes 94752 accept comment "!fw4: Allow-ICMPv6-Input"
jump accept_from_wan
}
chain output_wan {
jump accept_to_wan
}
chain forward_wan {
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
meta l4proto esp counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-IPSec-ESP"
udp dport 500 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-ISAKMP"
jump accept_to_lan comment "!fw4: Accept wan to lan forwarding"
jump accept_to_wan
}
chain accept_from_wan {
iifname "wan" counter packets 16123 bytes 2357723 accept comment "!fw4: accept wan IPv4/IPv6 traffic"
}
chain accept_to_wan {
meta nfproto ipv4 oifname "wan" ct state invalid counter packets 1032 bytes 56193 drop comment "!fw4: Prevent NAT leakage"
oifname "wan" counter packets 22885 bytes 5401099 accept comment "!fw4: accept wan IPv4/IPv6 traffic"
}
chain input_iconnect {
jump accept_from_iconnect
}
chain output_iconnect {
jump accept_to_iconnect
}
chain forward_iconnect {
jump reject_to_iconnect
}
chain helper_iconnect {
}
chain accept_from_iconnect {
iifname { "wan", "wgIC" } counter packets 0 bytes 0 accept comment "!fw4: accept iconnect IPv4/IPv6 traffic"
}
chain accept_to_iconnect {
oifname { "wan", "wgIC" } counter packets 0 bytes 0 accept comment "!fw4: accept iconnect IPv4/IPv6 traffic"
}
chain reject_to_iconnect {
oifname { "wan", "wgIC" } counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject iconnect IPv4/IPv6 traffic"
}
chain input_iconnectInt {
jump accept_from_iconnectInt
}
chain output_iconnectInt {
jump accept_to_iconnectInt
}
chain forward_iconnectInt {
jump reject_to_iconnectInt
}
chain helper_iconnectInt {
}
chain accept_from_iconnectInt {
}
chain accept_to_iconnectInt {
}
chain reject_to_iconnectInt {
}
chain dstnat {
type nat hook prerouting priority dstnat; policy accept;
}
chain srcnat {
type nat hook postrouting priority srcnat; policy accept;
oifname "wan" jump srcnat_wan comment "!fw4: Handle wan IPv4/IPv6 srcnat traffic"
}
chain srcnat_wan {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 wan traffic"
}
chain raw_prerouting {
type filter hook prerouting priority raw; policy accept;
}
chain raw_output {
type filter hook output priority raw; policy accept;
}
chain mangle_prerouting {
type filter hook prerouting priority mangle; policy accept;
}
chain mangle_postrouting {
type filter hook postrouting priority mangle; policy accept;
}
chain mangle_input {
type filter hook input priority mangle; policy accept;
}
chain mangle_output {
type route hook output priority mangle; policy accept;
}
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
iifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 ingress MTU fixing"
oifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 egress MTU fixing"
}
}
antonk
June 22, 2024, 8:45am
13
chain input_iconnect {
counter packets 0 bytes 0 jump handle_reject comment "!fw4: Iconnect diable all"
jump drop_from_iconnect
}
...
chain input_iconnect {
jump accept_from_iconnect
}
Clearly the ruleset has changed between the first time you posted it and the second time. Looks like the first version should have been working, although i can't say for sure because you didn't post the complete ruleset. The current version jumps to accept, so no blocking is to be expected.
1 Like
brada4
June 22, 2024, 8:49am
14
All the traffic is accepted from "wan" interface before drop/reject on wgic one.
antonk
June 22, 2024, 8:52am
15
@PetrP I'd suggest you to re-do the config, restart the router, test, and if you still have the issue, post all the requested config (including ruleset) again.
1 Like
PetrP
June 22, 2024, 9:17am
16
It seems than this is the correct answer. wgIC (wg interconnect) interface is an alias for WAN, that's why it works like that.
Is there a way to set this up? BTW, an alias is necessary only for testing.
brada4
June 22, 2024, 10:40am
17
remove wan from accepting interconnect interface.
PetrP
June 22, 2024, 10:58am
18
Where? I don't get
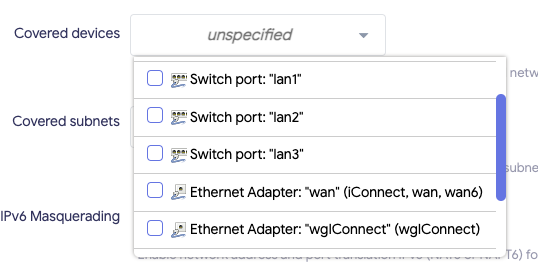
I see only this:
So no alias devices here.
Still not blocking
brada4
June 22, 2024, 11:05am
19
Chek the rules that pertain, and clear existing states with conntrack -D
antonk
June 22, 2024, 12:26pm
20
Post your updated nft ruleset
1 Like