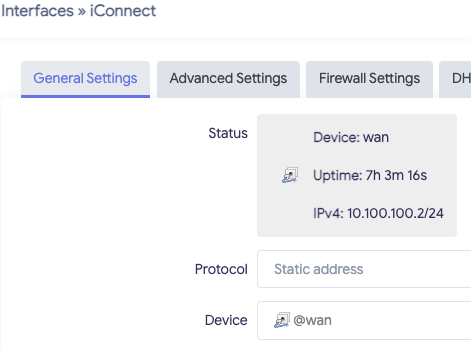
Could you please elaborate what should I check?
Updated ruleset:
table inet fw4 {
flowtable ft {
hook ingress priority filter
devices = { lan1, lan2, lan3, wan }
flags offload
counter
}
chain input {
type filter hook input priority filter; policy accept;
iifname "lo" accept comment "!fw4: Accept traffic from loopback"
ct state established,related accept comment "!fw4: Allow inbound established and related flows"
tcp flags syn / fin,syn,rst,ack jump syn_flood comment "!fw4: Rate limit TCP syn packets"
iifname "br-lan" jump input_lan comment "!fw4: Handle lan IPv4/IPv6 input traffic"
iifname "wan" jump input_wan comment "!fw4: Handle wan IPv4/IPv6 input traffic"
iifname "wan" jump input_icZone comment "!fw4: Handle icZone IPv4/IPv6 input traffic"
}
chain forward {
type filter hook forward priority filter; policy drop;
meta l4proto { tcp, udp } flow add @ft
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
iifname "br-lan" jump forward_lan comment "!fw4: Handle lan IPv4/IPv6 forward traffic"
iifname "wan" jump forward_wan comment "!fw4: Handle wan IPv4/IPv6 forward traffic"
iifname "wan" jump forward_icZone comment "!fw4: Handle icZone IPv4/IPv6 forward traffic"
jump handle_reject
}
chain output {
type filter hook output priority filter; policy accept;
oifname "lo" accept comment "!fw4: Accept traffic towards loopback"
ct state established,related accept comment "!fw4: Allow outbound established and related flows"
oifname "br-lan" jump output_lan comment "!fw4: Handle lan IPv4/IPv6 output traffic"
oifname "wan" jump output_wan comment "!fw4: Handle wan IPv4/IPv6 output traffic"
oifname "wan" jump output_icZone comment "!fw4: Handle icZone IPv4/IPv6 output traffic"
}
chain prerouting {
type filter hook prerouting priority filter; policy accept;
iifname "br-lan" jump helper_lan comment "!fw4: Handle lan IPv4/IPv6 helper assignment"
iifname "wan" jump helper_icZone comment "!fw4: Handle icZone IPv4/IPv6 helper assignment"
}
chain handle_reject {
meta l4proto tcp reject with tcp reset comment "!fw4: Reject TCP traffic"
reject comment "!fw4: Reject any other traffic"
}
chain syn_flood {
limit rate 25/second burst 50 packets return comment "!fw4: Accept SYN packets below rate-limit"
drop comment "!fw4: Drop excess packets"
}
chain input_lan {
jump accept_from_lan
}
chain output_lan {
jump accept_to_lan
}
chain forward_lan {
jump accept_to_wan comment "!fw4: Accept lan to wan forwarding"
jump accept_to_lan
}
chain helper_lan {
}
chain accept_from_lan {
iifname "br-lan" counter packets 8800 bytes 1503230 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain accept_to_lan {
oifname "br-lan" counter packets 1363 bytes 110531 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain input_wan {
meta nfproto ipv4 udp dport 68 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCP-Renew"
icmp type echo-request counter packets 3 bytes 252 accept comment "!fw4: Allow-Ping"
meta nfproto ipv4 meta l4proto igmp counter packets 0 bytes 0 accept comment "!fw4: Allow-IGMP"
meta nfproto ipv6 udp dport 546 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCPv6"
ip6 saddr fe80::/10 icmpv6 type . icmpv6 code { mld-listener-query . no-route, mld-listener-report . no-route, mld-listener-done . no-route, mld2-listener-report . no-route } counter packets 0 bytes 0 accept comment "!fw4: Allow-MLD"
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply, nd-router-solicit, nd-router-advert } limit rate 1000/second counter packets 147 bytes 21584 accept comment "!fw4: Allow-ICMPv6-Input"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, nd-neighbor-solicit . no-route, nd-neighbor-advert . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 818 bytes 58896 accept comment "!fw4: Allow-ICMPv6-Input"
jump accept_from_wan
}
chain output_wan {
jump accept_to_wan
}
chain forward_wan {
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
meta l4proto esp counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-IPSec-ESP"
udp dport 500 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-ISAKMP"
jump accept_to_lan comment "!fw4: Accept wan to lan forwarding"
jump accept_to_wan
}
chain accept_from_wan {
iifname "wan" counter packets 9711 bytes 1414364 accept comment "!fw4: accept wan IPv4/IPv6 traffic"
}
chain accept_to_wan {
meta nfproto ipv4 oifname "wan" ct state invalid counter packets 97 bytes 4840 drop comment "!fw4: Prevent NAT leakage"
oifname "wan" counter packets 8486 bytes 2161541 accept comment "!fw4: accept wan IPv4/IPv6 traffic"
}
chain input_iconnect {
}
chain output_iconnect {
}
chain forward_iconnect {
}
chain helper_iconnect {
}
chain accept_from_iconnect {
}
chain accept_to_iconnect {
}
chain reject_to_iconnect {
}
chain input_iconnectInt {
}
chain output_iconnectInt {
}
chain forward_iconnectInt {
}
chain helper_iconnectInt {
}
chain accept_from_iconnectInt {
}
chain accept_to_iconnectInt {
}
chain reject_to_iconnectInt {
}
chain dstnat {
type nat hook prerouting priority dstnat; policy accept;
}
chain srcnat {
type nat hook postrouting priority srcnat; policy accept;
oifname "wan" jump srcnat_wan comment "!fw4: Handle wan IPv4/IPv6 srcnat traffic"
}
chain srcnat_wan {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 wan traffic"
}
chain raw_prerouting {
type filter hook prerouting priority raw; policy accept;
}
chain raw_output {
type filter hook output priority raw; policy accept;
}
chain mangle_prerouting {
type filter hook prerouting priority mangle; policy accept;
}
chain mangle_postrouting {
type filter hook postrouting priority mangle; policy accept;
}
chain mangle_input {
type filter hook input priority mangle; policy accept;
}
chain mangle_output {
type route hook output priority mangle; policy accept;
}
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
iifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 ingress MTU fixing"
oifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 egress MTU fixing"
}
chain input_icZone {
jump reject_from_icZone
}
chain output_icZone {
jump reject_to_icZone
}
chain forward_icZone {
jump reject_to_icZone
}
chain helper_icZone {
}
chain reject_from_icZone {
iifname "wan" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject icZone IPv4/IPv6 traffic"
}
chain reject_to_icZone {
oifname "wan" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject icZone IPv4/IPv6 traffic"
}
chain input_wgZone {
jump accept_from_wgZone
}
chain output_wgZone {
jump accept_to_wgZone
}
chain forward_wgZone {
jump reject_to_wgZone
}
chain helper_wgZone {
}
chain accept_from_wgZone {
}
chain accept_to_wgZone {
}
chain reject_to_wgZone {
}
}
Also I put @wan instead of wan, does not help either