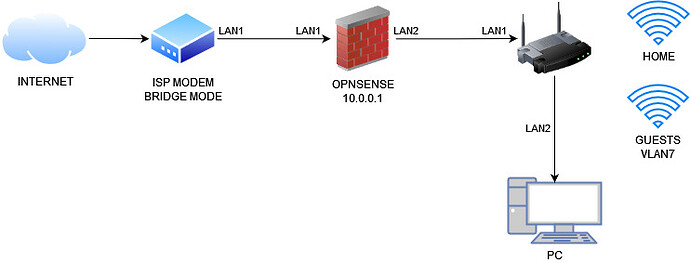
I've an OPNsense box for DNS, DHCP, etc. From this box, an ethernet cable out to a switch, and one port to a PC, another to an OpenWrt dumb AP with two SSIDs, one for home devices and one for guests devices. How can I achieve isolating the guests SSID from the LAN and also limiting the bandwidth, knowing that I can't create a firewall rule?
The best place to do this is using your OPNsense box -- the main router is typically the preferred place to setup multiple networks. Then, the main router can also handle the firewall and bandwidth limiting.
If you've already got that setup, look at how OPNsense can do bandwidth limiting.
If not, take a look at the guest wifi on a dumb AP tutorial:
And then also take a look at cake or other bandwidth limiting filters that are available on OpenWrt (simply search the OpenWrt forums and/or wiki).
Just to chime in on this and to clarify (a bit).
The central router/ boarder gateway is indeed the best place for doing this, once, for the whole network - the APs are merely executing the policies decided on the router. You can implement that with running OpenWrt as a router (e.g. on the same x86_64 hardware) or running OPNsense, the part of which firmware will do it is immaterial (either can), the distinguishing factor is what role the devices are playing in your network topology (and what kind of system resources they can put on the table).
Thanks for your answers! You say it's possible, but I need to search how exactly can I do it ![]() I don't know if the OPNsense box makes any "sense" in my case giving the fact that OpenWrt can also do what I need, and I already know how to!
I don't know if the OPNsense box makes any "sense" in my case giving the fact that OpenWrt can also do what I need, and I already know how to!
In the end, the functionality can be the same regardless of the choice of OPNsense or OpenWrt for the guest network. But usually the administration is easier when you run the guest network routing on the main router... this way, all your firewall rules and bandwidth controls are in one place and your other devices purely behave as switches or dumb APs.
I was reading that I can achieve my goal with VLANs. So, I created a VLAN in OPNsense with the LAN interface as the parent. Now, in OpenWrt 23.05.0, which is a dumb AP, I have the lan interface and the br-lan device. My LuCI doesn't have the "Switch" menu, so I think it's different now? I was following this video, but it's not a dumb AP.
If there is no switch menu, the AP is either a DSA device or uses individually routed ports (i.e. no internal switch chip).
Let's find out:
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.134",
"hostname": "OpenWrt",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "TP-Link Archer C6 v3",
"board_name": "tplink,archer-c6-v3",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.0",
"revision": "r23497-6637af95aa",
"target": "ramips/mt7621",
"description": "OpenWrt 23.05.0 r23497-6637af95aa"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc4:bae2:b84f::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '10.0.0.100'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '10.0.0.1'
list dns '10.0.0.1'
root@OpenWrt:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:00.0/0000:01:00.0'
option channel '1'
option band '2g'
option htmode 'HT20'
option disabled '1'
config wifi-device 'radio1'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
option channel '161'
option band '5g'
option htmode 'VHT40'
option txpower '18'
option cell_density '0'
option country 'EC'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'HOME'
option encryption 'sae'
option key '***'
config wifi-iface 'wifinet4'
option device 'radio1'
option mode 'ap'
option ssid 'GUESTS'
option encryption 'sae-mixed'
option isolate '1'
option key '***'
option network 'lan'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
Ok... so this is a DSA device... it will be pretty simple to get this to work.
We need to know 2 things:
- What physical port is used to connect to the OPNsense router?
- What is the VLAN ID you setup for the guest network on the OPNsense router?
This is how my network looks like right now.
- Port 1 of the OpenWrt AP goes to port 2 (LAN) of the OPNsense router.
- I assigned it to VLAN 7.
If it can be done by just using one cable that goes from the router I'll be happy ![]()
In the future, please post your image directly to the forum, rather than using a 3rd party image serving site.
The unmanaged switch may cause you problems here -- they are not designed to be used with tagged networks, only a single untagged one should ever be passed through an unmanaged switch. YMMV regarding issues -- you may not experience any problems, possibly minor or even major problems.
Is it possible for you to switch the position of the AP and the unmanaged switch? Specifically, if you can connect your AP directly to the router, and then the switch to the AP, that can solve the problem because then we can configure your OpenWrt AP to only send a single untagged network to the switch.
Yes, this is not a problem.
Add these sections:
config bridge-vlan
option name 'br-lan'
option vlan '1'
list ports 'lan1:u*'
list ports 'lan2:u*'
list ports 'lan3:u*'
list ports 'lan4:u*'
config bridge-vlan
option name 'br-lan'
option vlan '7'
list ports 'lan1:t'
config interface 'guest'
option device 'br-lan.7'
option proto 'none'
Then edit the lan interface to use br-lan.1 instead of br-lan like this:
config interface 'lan'
option device 'br-lan.1'
option proto 'static'
option ipaddr '10.0.0.100'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '10.0.0.1'
list dns '10.0.0.1'
And finally, edit your wireless config so that the GUESTS SSID uses the guest network, like this:
config wifi-iface 'wifinet4'
option device 'radio1'
option mode 'ap'
option ssid 'GUESTS'
option encryption 'sae-mixed'
option isolate '1'
option key '***'
option network 'guest'
As recommend above, if you can switch the physical order of the network topology, I'd recommend:
OPNsense router port LAN2 > OpenWrt AP port LAN1 | OpenWrt AP port LAN2 > unmanaged switch
Thank you! I'll change the topology and try the configuration, as you suggested.
I'll report back!
You did it again P! Thanks a lot for your help :')
I got rid of the switch and now my network looks like this:
Awesome! Glad I could help!
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.
Thanks! ![]()
Just one last question. Should I change to DSA the VLANs I created on another OpenWrt router using the "old" way?
I'm not really sure what you mean by this question. At this point, you've got a DSA based device and everything should be configured properly based on everything we've done.
In general, if a device has migrated to DSA, you cannot use the "old way" anymore, and if it is a swconfig device, you need to use swconfig ("old way") syntax.
So, no, don't make any changes. Unless I've misunderstood your question -- in which case, please elaborate.
You (and others) helped me set up the VLANs for my TP-Link Archer C60 with swconfig. But since then, I upgraded the firmware to 23.05.0. My question is: should I change the VLANs configuration to DSA, or just leave it alone?
The Archer C60 is part of the ath79 target. This means it is still using swconfig (it has not been through a DSA transition). So just leave it as it is.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.