Hi,
I have setup a portforwarding rule for my Jellyfin server so I can access it from outside of my network. However, Jellyfin is not accessible even though it seems traffic is hitting it
Internal IP of my server is 192.168.0.XXX It seems I have 2 public IPs?
13:49:09.095469 IP 10.112.XXX.XX.45202 > 185.190.XXX.XXX.8096: Flags [S], seq 2701356879, win 65535, options [mss 1460,sackOK,T S val 1599646342 ecr 0,nop,wscale 9], length 0
XXX stands for numbers which were deleted since it's a sensitive information
trendy
November 3, 2021, 1:48pm
2
Please run the following commands (copy-paste the whole block) and paste the output here, using the "Preformatted text </> " button:
ubus call system board; \
uci export network; uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
iptables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
As a sidenote addresses starting from 10. and 192.168. are private and not sensitive information.
Here it is
{
"kernel": "5.4.154",
"hostname": "RaspberryRouter",
"system": "ARMv8 Processor rev 3",
"model": "Raspberry Pi 4 Model B Rev 1.4",
"board_name": "raspberrypi,4-model-b",
"release": {
"distribution": "OpenWrt",
"version": "21.02.1",
"revision": "r16325-88151b8303",
"target": "bcm27xx/bcm2711",
"description": "OpenWrt 21.02.1 r16325-88151b8303"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd6b:7561:0c9a::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config interface 'lan'
option device 'eth0'
option proto 'static'
option ipaddr '192.168.0.2'
option netmask '255.255.255.0'
option type 'bridge'
option gateway '192.168.0.1'
list dns '192.168.0.172'
list dns '185.43.135.1'
list dns '193.17.47.1'
config interface 'wwan'
option proto 'dhcp'
config interface 'wan'
option proto 'dhcp'
option device 'eth1'
option peerdns '0'
list dns '192.168.0.172'
option hostname 'router'
config device
option name 'eth1'
option macaddr 'B8:69:F4:B0:69:DE'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option dnsforwardmax '2300'
option min_cache_ttl '270'
option cachesize '5000'
list address '/router/192.168.0.2'
option boguspriv '0'
option rebind_protection '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option ra 'hybrid'
option dhcpv6 'hybrid'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
list ra_flags 'none'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'eth0'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'eth0'
config host
option mac 'B8:27:EB:D8:00:58'
option ip '192.168.0.172'
option name 'AdGuard'
option dns '1'
config host
option mac 'E4:5F:01:5D:0B:75'
option ip '192.168.0.124'
option name 'NASty'
option dns '1'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option flow_offloading '1'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
option input 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
option reload '1'
config redirect
option target 'DNAT'
option name 'Jellyfin'
option src 'wan'
option src_dport '8096'
option dest 'lan'
option dest_ip '192.168.0.124'
option dest_port '8096'
config redirect
option target 'DNAT'
option name 'Plex'
option src 'wan'
option dest 'lan'
option dest_ip '192.168.0.124'
list proto 'all'
option reflection_src 'external'
config rule
option name 'PortForward'
option src 'wan'
option dest 'lan'
list dest_ip '192.168.0.124'
option target 'ACCEPT'
list proto 'all'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
if [ -f /etc/custom/firewall.custom ]; then
sh /etc/custom/firewall.custom
fi
# Generated by iptables-save v1.8.7 on Wed Nov 3 14:56:55 2021
*raw
:PREROUTING ACCEPT [476370:317055984]
:OUTPUT ACCEPT [10688:22866966]
:zone_lan_helper - [0:0]
[14477:1807135] -A PREROUTING -i eth0 -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
COMMIT
# Completed on Wed Nov 3 14:56:55 2021
# Generated by iptables-save v1.8.7 on Wed Nov 3 14:56:55 2021
*nat
:PREROUTING ACCEPT [3207:894657]
:INPUT ACCEPT [752:56702]
:OUTPUT ACCEPT [685:45268]
:POSTROUTING ACCEPT [180:16229]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[3409:928821] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[3207:894657] -A PREROUTING -i eth0 -m comment --comment "!fw3" -j zone_lan_prerouting
[202:34164] -A PREROUTING -i eth1 -m comment --comment "!fw3" -j zone_wan_prerouting
[3171:889343] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[140:13419] -A POSTROUTING -o eth0 -m comment --comment "!fw3" -j zone_lan_postrouting
[2991:873114] -A POSTROUTING -o eth1 -m comment --comment "!fw3" -j zone_wan_postrouting
[140:13419] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[0:0] -A zone_lan_postrouting -s 192.168.0.0/24 -d 192.168.0.124/32 -p tcp -m tcp --dport 8096 -m comment --comment "!fw3: Jellyfin (reflection)" -j SNAT --to-source 192.168.0.2
[0:0] -A zone_lan_postrouting -s 192.168.0.0/24 -d 192.168.0.124/32 -p udp -m udp --dport 8096 -m comment --comment "!fw3: Jellyfin (reflection)" -j SNAT --to-source 192.168.0.2
[0:0] -A zone_lan_postrouting -s 192.168.0.0/24 -d 192.168.0.124/32 -m comment --comment "!fw3: Plex (reflection)" -j SNAT --to-source 10.112.101.23
[3207:894657] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -s 192.168.0.0/24 -d 10.112.101.23/32 -p tcp -m tcp --dport 8096 -m comment --comment "!fw3: Jellyfin (reflection)" -j DNAT --to-destination 192.168.0.124:8096
[0:0] -A zone_lan_prerouting -s 192.168.0.0/24 -d 10.112.101.23/32 -p udp -m udp --dport 8096 -m comment --comment "!fw3: Jellyfin (reflection)" -j DNAT --to-destination 192.168.0.124:8096
[0:0] -A zone_lan_prerouting -s 192.168.0.0/24 -d 10.112.101.23/32 -m comment --comment "!fw3: Plex (reflection)" -j DNAT --to-destination 192.168.0.124
[2991:873114] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[2991:873114] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[202:34164] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 8096 -m comment --comment "!fw3: Jellyfin" -j DNAT --to-destination 192.168.0.124:8096
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 8096 -m comment --comment "!fw3: Jellyfin" -j DNAT --to-destination 192.168.0.124:8096
[202:34164] -A zone_wan_prerouting -m comment --comment "!fw3: Plex" -j DNAT --to-destination 192.168.0.124
COMMIT
# Completed on Wed Nov 3 14:56:55 2021
# Generated by iptables-save v1.8.7 on Wed Nov 3 14:56:55 2021
*mangle
:PREROUTING ACCEPT [476376:317056384]
:INPUT ACCEPT [9158:1607827]
:FORWARD ACCEPT [467047:315420513]
:OUTPUT ACCEPT [10701:22871710]
:POSTROUTING ACCEPT [477571:338284495]
[788:41804] -A FORWARD -o eth1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[753:39708] -A FORWARD -i eth1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Wed Nov 3 14:56:55 2021
# Generated by iptables-save v1.8.7 on Wed Nov 3 14:56:55 2021
*filter
:INPUT ACCEPT [84:4188]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_ACCEPT - [0:0]
[892:74270] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[8269:1533677] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[5932:1387733] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[158:8240] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[2253:141756] -A INPUT -i eth0 -m comment --comment "!fw3" -j zone_lan_input
[84:4188] -A INPUT -i eth1 -m comment --comment "!fw3" -j zone_wan_input
[467047:315420513] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[463499:314318193] -A FORWARD -m comment --comment "!fw3: Traffic offloading" -m conntrack --ctstate RELATED,ESTABLISHED -j FLOWOFFLOAD
[463499:314318193] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[3365:1084884] -A FORWARD -i eth0 -m comment --comment "!fw3" -j zone_lan_forward
[183:17436] -A FORWARD -i eth1 -m comment --comment "!fw3" -j zone_wan_forward
[892:74270] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[9813:22798272] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[8980:22745288] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[211:14112] -A OUTPUT -o eth0 -m comment --comment "!fw3" -j zone_lan_output
[622:38872] -A OUTPUT -o eth1 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[158:8240] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[394:31548] -A zone_lan_dest_ACCEPT -o eth0 -m comment --comment "!fw3" -j ACCEPT
[3365:1084884] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[3365:1084884] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[2253:141756] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[2253:141756] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[211:14112] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[211:14112] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[2253:141756] -A zone_lan_src_ACCEPT -i eth0 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[177:7728] -A zone_wan_dest_ACCEPT -o eth1 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[3810:1116028] -A zone_wan_dest_ACCEPT -o eth1 -m comment --comment "!fw3" -j ACCEPT
[183:17436] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[183:17436] -A zone_wan_forward -d 192.168.0.124/32 -m comment --comment "!fw3: PortForward" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[84:4188] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[84:4188] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_ACCEPT
[622:38872] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[622:38872] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_ACCEPT -i eth1 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
COMMIT
# Completed on Wed Nov 3 14:56:55 2021
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
inet 192.168.0.2/24 brd 192.168.0.255 scope global eth0
valid_lft forever preferred_lft forever
13: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc cake state UP group default qlen 1000
inet 10.112.101.23/25 brd 10.112.101.127 scope global eth1
valid_lft forever preferred_lft forever
default via 10.112.101.1 dev eth1 proto static src 10.112.101.23
10.112.101.0/25 dev eth1 proto kernel scope link src 10.112.101.23
192.168.0.0/24 dev eth0 proto kernel scope link src 192.168.0.2
broadcast 10.112.101.0 dev eth1 table local proto kernel scope link src 10.112.101.23
local 10.112.101.23 dev eth1 table local proto kernel scope host src 10.112.101.23
broadcast 10.112.101.127 dev eth1 table local proto kernel scope link src 10.112.101.23
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.0.0 dev eth0 table local proto kernel scope link src 192.168.0.2
local 192.168.0.2 dev eth0 table local proto kernel scope host src 192.168.0.2
broadcast 192.168.0.255 dev eth0 table local proto kernel scope link src 192.168.0.2
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
Is your device connected to the internet directly? Does it have a public IP address on the WAN interface? Your configuration is confusing in this aspect.
2 Likes
It's connected via OpenWRT Raspberry Pi router and yes, it can reach the internet
trendy
November 3, 2021, 2:50pm
6
The rules are there:
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 8096 -m comment --comment "!fw3: Jellyfin" -j DNAT --to-destination 192.168.0.124:8096
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 8096 -m comment --comment "!fw3: Jellyfin" -j DNAT --to-destination 192.168.0.124:8096
[202:34164] -A zone_wan_prerouting -m comment --comment "!fw3: Plex" -j DNAT --to-destination 192.168.0.124
however only the last rule has hits. As a sidenote, the last forwarding rule will match any packet coming to wan zone and send it to 192.168.0.124 server. You might not want that.
Another thing I noticed is that lan interface has gateway and nameservers configured. This is not correct if you are using the wan or wwan interfaces as uplink. Are you sure that the 0.124 server is using the OpenWrt as gateway?
I have removed [202:34164] -A zone_wan_prerouting -m comment --comment "!fw3: Plex" -j DNAT --to-destination 192.168.0.124
Gateway was a mistake
0.124 has definitely OpenWrt as a gateway, here is dhpcpcd.conf
interface eth0
static ip_address=192.168.0.121/24
static routers=192.168.0.2
static domain_name_servers=192.168.0.172
trendy
November 3, 2021, 3:35pm
8
I guess you can see the mistake.
trendy
November 3, 2021, 3:43pm
10
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.
Unfortunately no, it's still not working when I enter my public IP
trendy
November 3, 2021, 4:44pm
12
iptables-save -c -t nat | grep Jellyfin
Could it be that my WAN interface shows this `IPv4 Upstream
But my public IP is something completely different?`
stangri
November 3, 2021, 5:04pm
14
Why is your router at 192.168.0.2?
1 Like
This is an RFC1918 address and is not publicly routable. Is your OpenWrt router directly connected to your internet connection, or is there another NAT device upstream (such as a modem+router combo unit or an ISP supplied router, etc.)?
2 Likes
Because my original router, Archer C6, was 0.1 and Raspberry Pi was plugged into it. I then swapped them around
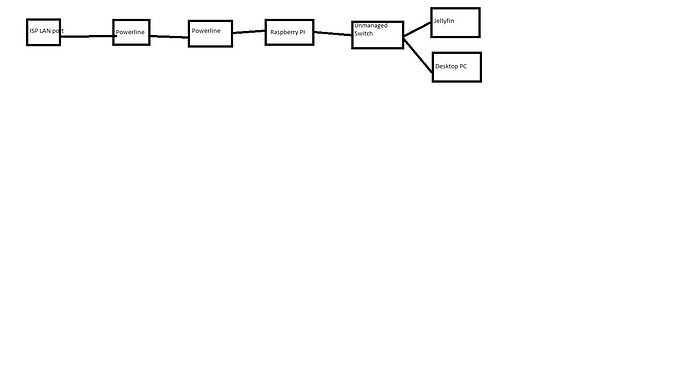
Yes it is, it''s connected to a power line in my study which in turn connects to powerline in our living room where our ISP has placed the lan port to connect routers/modems
What address do you get if you plug a device directly into the "ISP LAN port" ?
I will try that later on tonight after I stop working. I want to measure speed without powerlines anyway
trendy
November 3, 2021, 6:01pm
20
Don't forget to post the iptables command too.
iptables-save -c -t nat | grep Jellyfin
 Thanks
Thanks