RPi4 connected to Port1 of TP-Link managed switch.
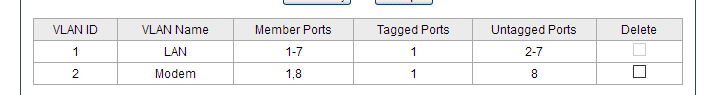
Switch is configured as: 802.1Q VLAN Enabled
VLAN1 Ports: 1-7; Tagged: 1; Untagged: 2-7;
VLAN2 Ports: 1,8; Tagged: 1; Untagged: 8; -> Port 8: PVID 2
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxxx:xxxx:xxxx::/48'
config interface 'lan'
option type 'bridge'
option netmask '255.255.255.0'
option ip6assign '60'
option ifname 'eth1.1'
option proto 'static'
option ipaddr '192.168.1.1'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
option macaddr 'xx:xx:xx:xx:xx:xx'
After rebooting the modem (CM1000) I'm able to get DHCP working for short period of time
CM1000 ip addr: 192.168.100.1 and WAN: 192.168.100.10
I'm able to ping it but no internet connection and short after (maybe 5-10 sec) Network becomes unreachable
Here is part of the log:
Sat Jun 13 06:37:54 2020 kern.notice kernel: [ 117.424952] r8152 2-1:1.0 eth1: Promiscuous mode enabled
Sat Jun 13 06:37:54 2020 kern.info kernel: [ 117.432680] br-lan: port 1(eth1.1) entered blocking state
Sat Jun 13 06:37:54 2020 kern.info kernel: [ 117.439645] br-lan: port 1(eth1.1) entered forwarding state
Sat Jun 13 06:37:54 2020 daemon.notice netifd: VLAN 'eth1.1' link is up
Sat Jun 13 06:37:54 2020 kern.info kernel: [ 117.446847] IPv6: ADDRCONF(NETDEV_CHANGE): eth1.2: link becomes ready
Sat Jun 13 06:37:54 2020 daemon.notice netifd: VLAN 'eth1.2' link is up
Sat Jun 13 06:37:54 2020 daemon.notice netifd: Interface 'WAN' has link connectivity
Sat Jun 13 06:37:54 2020 daemon.notice netifd: Interface 'WAN' is setting up now
Sat Jun 13 06:37:54 2020 kern.info kernel: [ 117.454941] IPv6: ADDRCONF(NETDEV_CHANGE): br-lan: link becomes ready
Sat Jun 13 06:37:54 2020 daemon.notice netifd: bridge 'br-lan' link is up
Sat Jun 13 06:37:54 2020 daemon.notice netifd: Interface 'lan' has link connectivity
Sat Jun 13 06:37:54 2020 kern.notice kernel: [ 117.463499] r8152 2-1:1.0 eth1: Promiscuous mode enabled
Sat Jun 13 06:37:54 2020 daemon.notice netifd: WAN (1068): udhcpc: started, v1.31.1
Sat Jun 13 06:37:54 2020 daemon.notice netifd: WAN (1068): udhcpc: sending discover
Sat Jun 13 06:37:55 2020 daemon.err odhcpd[613]: Failed to send to ff02::1%lan@br-lan (Address not available)
Sat Jun 13 06:37:56 2020 kern.notice kernel: [ 118.814156] r8152 2-1:1.0 eth1: Promiscuous mode enabled
Sat Jun 13 06:37:56 2020 kern.notice kernel: [ 119.133502] r8152 2-1:1.0 eth1: Promiscuous mode enabled
Sat Jun 13 06:37:57 2020 daemon.notice netifd: WAN (1068): udhcpc: sending discover
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[424]: exiting on receipt of SIGTERM
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: Connected to system UBus
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: started, version 2.81 cachesize 150
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: DNS service limited to local subnets
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-DNSSEC no-ID loop-detect inotify dumpfile
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: UBus support enabled: connected to system bus
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq-dhcp[1153]: DHCP, IP range 192.168.1.100 -- 192.168.1.249, lease time 12h
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: using only locally-known addresses for domain test
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: using only locally-known addresses for domain onion
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: using only locally-known addresses for domain localhost
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: using only locally-known addresses for domain local
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: using only locally-known addresses for domain invalid
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: using only locally-known addresses for domain bind
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: using only locally-known addresses for domain lan
Sat Jun 13 06:37:58 2020 daemon.warn dnsmasq[1153]: no servers found in /tmp/resolv.conf.d/resolv.conf.auto, will retry
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: read /etc/hosts - 4 addresses
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq[1153]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Sat Jun 13 06:37:58 2020 daemon.info dnsmasq-dhcp[1153]: read /etc/ethers - 0 addresses
Sat Jun 13 06:38:00 2020 daemon.notice netifd: WAN (1068): udhcpc: sending discover
Sat Jun 13 06:38:12 2020 daemon.err uhttpd[683]: luci: accepted login on /admin/status/syslog for root from 192.168.1.103
Sat Jun 13 06:39:37 2020 daemon.notice netifd: WAN (1068): udhcpc: sending select for 192.168.100.10
Sat Jun 13 06:39:38 2020 daemon.notice netifd: WAN (1068): udhcpc: lease of 192.168.100.10 obtained, lease time 122
Sat Jun 13 06:39:38 2020 daemon.notice netifd: Interface 'WAN' is now up
Sat Jun 13 06:39:38 2020 user.notice firewall: Reloading firewall due to ifup of WAN (eth1.2)
Sat Jun 13 06:40:39 2020 daemon.notice netifd: WAN (1068): udhcpc: sending renew to 192.168.100.1
Sat Jun 13 06:41:10 2020 daemon.notice netifd: WAN (1068): udhcpc: sending renew to 0.0.0.0
Sat Jun 13 06:41:25 2020 daemon.notice netifd: WAN (1068): udhcpc: sending renew to 0.0.0.0
Sat Jun 13 06:41:32 2020 daemon.notice netifd: WAN (1068): udhcpc: sending renew to 0.0.0.0
Sat Jun 13 06:41:35 2020 daemon.notice netifd: WAN (1068): udhcpc: sending renew to 0.0.0.0
Sat Jun 13 06:41:36 2020 daemon.notice netifd: WAN (1068): udhcpc: sending renew to 0.0.0.0
Sat Jun 13 06:41:36 2020 daemon.notice netifd: WAN (1068): udhcpc: lease lost, entering init state
Sat Jun 13 06:41:36 2020 daemon.notice netifd: Interface 'WAN' has lost the connection