Hi everyone,
I am using OpenWRT for a while now, and have never managed to solve the following problem:
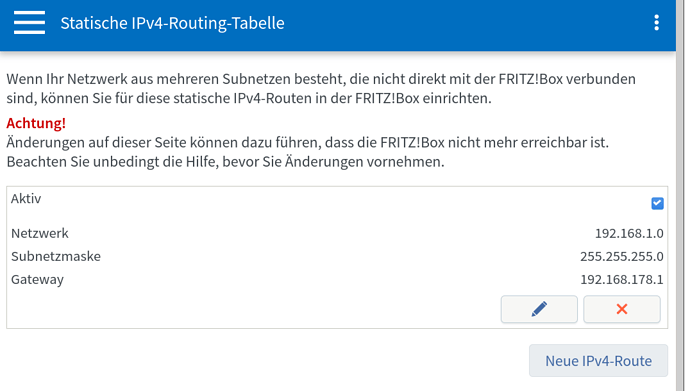
- I have an ISP that uses DS-Lite, meaning that I get a public ipv6 address and a /56 prefix on my DSL-modem
- My DSL-modem is a FritzBox 7560, which broadcasts a (guest) WLAN and has a single LAN connection to the WAN interface of my OpenWRT router.
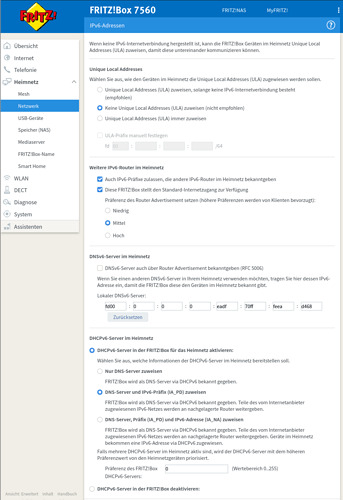
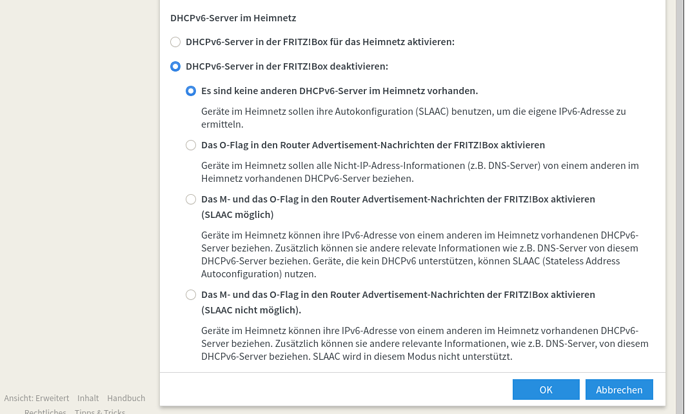
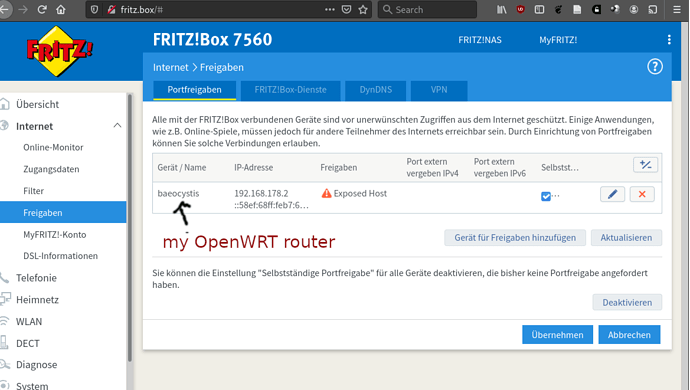
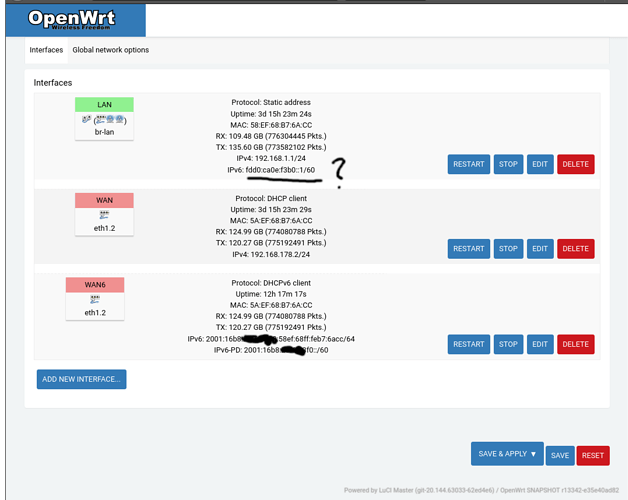
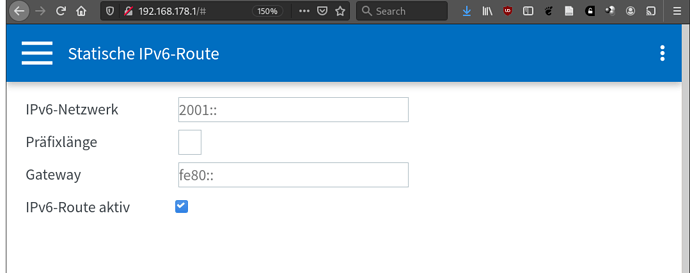
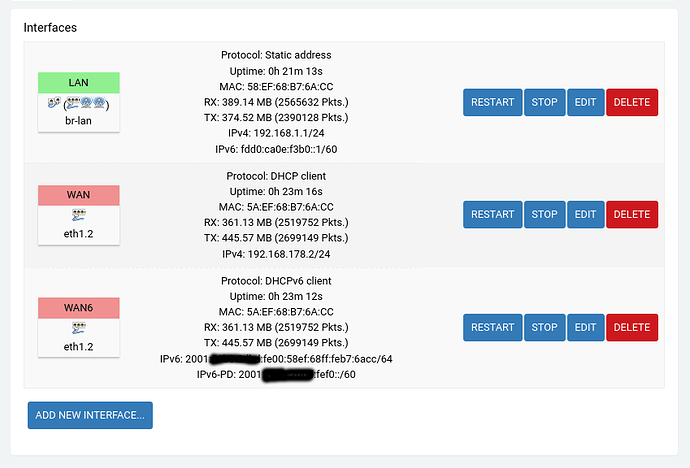
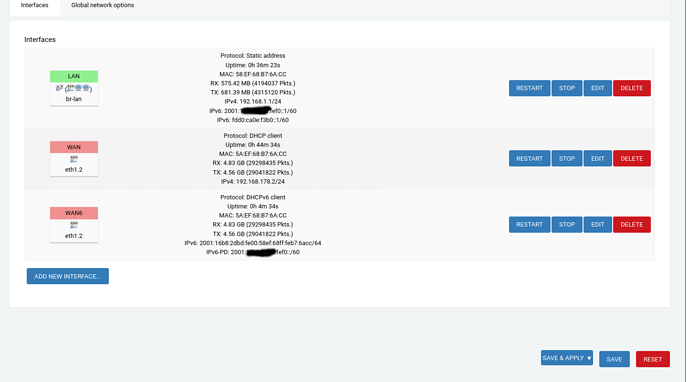
- I have configured the OpenWRT router as an exposed host on the FritzBox and have the DHCP6 server configured on the FritzBox to assign IP addresses and a prefix. The DHCP6 configuration for the LAN interface is set to relay, whereas it is DHCP client for WAN6.
- With this configuration, LAN interface get public global ipv6 addresses, which the FritzBox knows as well (2001:xxxxxx)
Allowing dropbear for WAN access on a custom port <sshport> and configuring the Firewall Traffic Rule as
option name 'WAN-SSH-ipv6'
option family 'ipv6'
list proto 'tcp'
option src 'wan'
option target 'ACCEPT'
option dest_port '2323'
gives me WAN access to by OpenWRT Router, which I test by trying to access it via the guest-WLAN configuration on my FB.
In short:
ssh -p <sshport> root@<router-public-ipv6-address>
does work.
Ultimately, I want to allows access to virtual machines on my FreeNAS device, which lives in LAN.
To make this access public, I will probably have to use dyndns and a port mapper.
However, for troubleshooting issues at the moment I am just trying to exposing an apache webserver running on my desktop at ipv6 2001:ab:cd:ef:12:34:55:67 on port <webport>
to the internet.
From within LAN, everything works well. I can access the webserver via ipv6, and the URL http://[2001:ab:cd:ef:12:34:55:67]:<webport> in Firefox displays the webserver.
So I tried to setup a traffic rule to make this available also via WAN.
I used the adapted example from https://openwrt.org/docs/guide-user/firewall/fw3_configurations/fw3_ipv6_examples to setup the corresponding rule:
config rule
option src 'wan'
option proto 'tcp'
option dest 'lan'
option family 'ipv6'
option target 'ACCEPT'
list dest_ip '2001:ab:cd:ef:12:34:55:67'
option dest_port '<webport>'
Now I can finally access the webserver from WAN.
The next step would be now to make this rule somehow, so that it persists when
- the ISP changes the IPv6 prefix
2001:ab:cd:efto something else - The local suffix of the IP changes to something else (e.g. when router or computer is restarted)
The first bullet point seems to be solved by adapting my config to
config rule
list dest_ip '::12:34:55:67/-64'
meaning that I mask the prefix.
So this all works.
The question is now, how can I make this rule also independent of the suffix, i.e. by setting a static suffix.
According to https://openwrt.org/docs/guide-user/base-system/dhcp_configuration#static_leases , I setup an IPv6 suffix '111' in my dhcp.
config host
option name 'desktop'
option dns '1'
option mac 'XX:XX:XX:XX:XX:XX'
option ip '192.168.1.111'
option duid '<some-duid-that-was-selected-by-LUCI>'
option hostid '111'
I am not really sure how to find the DUID of my desktop (arch linux, using networkmanager), but LUCI selected this DUID for me.
(You see, here I am starting to get confused)
I then hoped that using the adapted rule
config rule
list dest_ip '::111/-64'
would work, but it doesn't.
The problem seems to be that my desktop does not get assigned any form of "static" ipv6.
This might be a problem with the "relay" DHCPv6 configuration for the LAN interface on OpenWRT.
So I might need to generally reconfigure the IPv6 settings in the FritzBox and OpenWRT, and I have no problems to do so.
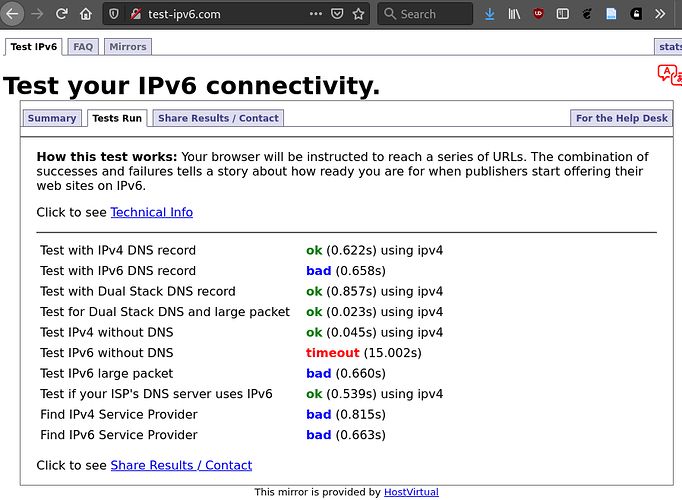
However, the current permutation of configurations for IPv6 DHCP in OpenWRT and the FritzBox was the only one where IPv6 would work in general (i.e. that e.g. http://test-ipv6.com/ completed all tests successfully).
Can anyone help me with my configuration?