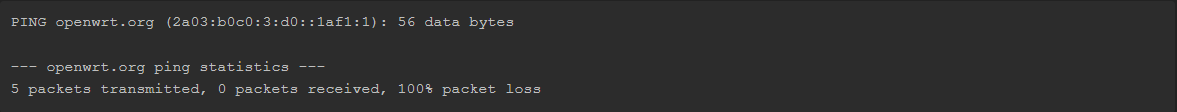
before i do that is this something useful?
root@OpenWrt:~# killall tcpdump; tcpdump -n -i pppoe-wan
killall: tcpdump: no process killed
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on pppoe-wan, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes
10:41:18.351804 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 412, length 64
10:41:19.062093 IP 172.217.169.170.443 > 100.96.116.98.36884: Flags [F.], seq 1258863522, ack 2347092321, win 537, options [nop,nop,TS val 2599298205 ecr 3243086220], length 0
10:41:19.285077 IP 172.217.169.170.443 > 100.96.116.98.36884: Flags [F.], seq 0, ack 1, win 537, options [nop,nop,TS val 2599298429 ecr 3243086220], length 0
10:41:19.352112 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 413, length 64
10:41:19.402960 IP 100.96.116.98.36884 > 172.217.169.170.443: Flags [.], ack 1, win 78, options [nop,nop,TS val 3243088235 ecr 2599298429,nop,nop,sack 1 {0:1}], length 0
10:41:20.352421 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 414, length 64
10:41:21.352728 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 415, length 64
10:41:22.200017 IP 100.96.116.98.52340 > 40.74.3.100.3544: UDP, length 61
10:41:22.245842 IP 40.74.3.100.3544 > 100.96.116.98.52340: UDP, length 109
10:41:22.353035 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 416, length 64
10:41:22.754096 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [P.], seq 1175896929:1175896974, ack 3808169200, win 6994, length 45
10:41:22.755871 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [P.], seq 45:83, ack 1, win 6994, length 38
10:41:22.757968 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [.], ack 83, win 513, length 0
10:41:22.758225 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [P.], seq 1:43, ack 83, win 513, length 42
10:41:22.851321 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [.], ack 43, win 6994, length 0
10:41:23.353372 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 417, length 64
10:41:24.353676 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 418, length 64
10:41:24.846602 IP 40.90.9.180.443 > 100.96.116.98.64949: Flags [P.], seq 965435014:965435045, ack 1471911259, win 2047, length 31
10:41:24.852300 IP 100.96.116.98.64949 > 40.90.9.180.443: Flags [.], ack 31, win 1020, length 0
10:41:25.196398 IP 184.104.202.142.443 > 100.96.116.98.64985: Flags [P.], seq 2337863534:2337864012, ack 3610135778, win 83, length 478
10:41:25.200745 IP 100.96.116.98.64985 > 184.104.202.142.443: Flags [P.], seq 1:36, ack 478, win 512, length 35
10:41:25.259591 IP 184.104.202.142.443 > 100.96.116.98.64985: Flags [.], ack 36, win 83, length 0
10:41:25.353978 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 419, length 64
10:41:26.354284 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 420, length 64
10:41:27.354591 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 421, length 64
10:41:27.922154 IP 100.96.116.98.50505 > 8.219.48.186.8053: UDP, length 32
10:41:28.226125 IP 8.219.48.186.8053 > 100.96.116.98.50505: UDP, length 32
10:41:28.354898 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 422, length 64
10:41:29.109487 IP 100.96.116.98.35882 > 194.27.156.207.123: NTPv4, Client, length 48
10:41:29.140171 IP 194.27.156.207.123 > 100.96.116.98.35882: NTPv4, Server, length 48
10:41:29.355204 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 423, length 64
10:41:29.596586 IP 104.22.8.20.443 > 100.96.116.98.54144: UDP, length 54
10:41:29.602238 IP 100.96.116.98.54144 > 104.22.8.20.443: UDP, length 45
10:41:30.355504 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 424, length 64
10:41:31.355859 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 425, length 64
10:41:32.356165 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 426, length 64
10:41:33.187731 IP 100.96.116.98.64950 > 13.89.223.27.443: Flags [P.], seq 3886643226:3886643261, ack 1145169548, win 1020, length 35
10:41:33.356477 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 427, length 64
10:41:33.392929 IP 13.89.223.27.443 > 100.96.116.98.64950: Flags [.], ack 35, win 2049, length 0
10:41:34.181685 IP 100.96.116.98.64941 > 146.75.0.193.443: Flags [.], seq 3675183607:3675183608, ack 3657447893, win 514, length 1
10:41:34.212901 IP 146.75.0.193.443 > 100.96.116.98.64941: Flags [.], ack 1, win 290, options [nop,nop,sack 1 {0:1}], length 0
10:41:34.356809 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 428, length 64
10:41:34.549290 IP 100.96.116.98.64937 > 151.101.193.69.443: Flags [.], seq 832526709:832526710, ack 1826738357, win 1026, length 1
10:41:34.564664 IP 151.101.193.69.443 > 100.96.116.98.64937: Flags [.], ack 1, win 325, options [nop,nop,sack 1 {0:1}], length 0
10:41:34.682852 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [P.], seq 43:146, ack 83, win 513, length 103
10:41:34.682967 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [P.], seq 146:192, ack 83, win 513, length 46
10:41:34.683035 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [P.], seq 192:781, ack 83, win 513, length 589
10:41:34.734412 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [.], ack 146, win 6994, length 0
10:41:34.734412 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [.], ack 192, win 6994, length 0
10:41:34.734745 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [P.], seq 83:142, ack 192, win 6994, length 59
10:41:34.747952 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [P.], seq 142:552, ack 781, win 7016, length 410
10:41:34.750581 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [.], ack 552, win 511, length 0
10:41:34.752901 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [P.], seq 781:823, ack 552, win 511, length 42
10:41:34.768945 IP 100.96.116.98.64492 > 104.244.42.129.443: Flags [.], seq 3898112539:3898112540, ack 4045404526, win 510, length 1
10:41:34.827160 IP 104.244.42.129.443 > 100.96.116.98.64492: Flags [.], ack 1, win 846, options [nop,nop,sack 1 {0:1}], length 0
10:41:34.847412 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [.], ack 823, win 7016, length 0
10:41:34.850410 IP 40.90.9.180.443 > 100.96.116.98.64949: Flags [P.], seq 31:62, ack 1, win 2047, length 31
10:41:34.852718 IP 100.96.116.98.64949 > 40.90.9.180.443: Flags [.], ack 62, win 1020, length 0
10:41:35.357114 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 429, length 64
10:41:36.357434 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 430, length 64
10:41:37.357739 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 431, length 64
10:41:38.358053 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 432, length 64
10:41:38.593421 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [P.], seq 823:906, ack 552, win 511, length 83
10:41:38.645185 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [.], ack 906, win 7016, length 0
10:41:38.660488 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [P.], seq 552:1077, ack 906, win 7016, length 525
10:41:38.711322 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [.], ack 1077, win 509, length 0
10:41:38.907766 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [P.], seq 906:1021, ack 1077, win 509, length 115
10:41:38.999442 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [.], ack 1021, win 7016, length 0
10:41:39.002336 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [.], seq 1077:2477, ack 1021, win 7016, length 1400
10:41:39.002336 IP 139.59.210.197.443 > 100.96.116.98.63283: Flags [P.], seq 2477:2545, ack 1021, win 7016, length 68
10:41:39.005161 IP 100.96.116.98.63283 > 139.59.210.197.443: Flags [.], ack 2545, win 514, length 0
10:41:39.250486 IP6 fe80::be4a:56ff:fe4f:5080 > ff02::1: ICMP6, router advertisement, length 96
10:41:39.358361 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 433, length 64
10:41:40.358810 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 434, length 64
10:41:40.361556 IP6 fe80::6c07:a1bc:7cc5:615e > ff02::16: HBH ICMP6, multicast listener report v2, 9 group record(s), length 188
10:41:40.745321 IP6 fe80::6c07:a1bc:7cc5:615e > ff02::16: HBH ICMP6, multicast listener report v2, 9 group record(s), length 188
10:41:41.359111 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 435, length 64
10:41:41.377746 IP 100.96.116.98.52340 > 40.74.3.100.3544: UDP, length 61
10:41:41.423479 IP 40.74.3.100.3544 > 100.96.116.98.52340: UDP, length 109
10:41:42.359412 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 436, length 64
10:41:43.295876 IP 100.96.116.98.63227 > 20.199.120.85.443: Flags [P.], seq 1784445491:1784445592, ack 144939445, win 511, length 101
10:41:43.346238 IP 20.199.120.85.443 > 100.96.116.98.63227: Flags [P.], seq 1:172, ack 101, win 7067, length 171
10:41:43.359722 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 437, length 64
10:41:43.402809 IP 100.96.116.98.63227 > 20.199.120.85.443: Flags [.], ack 172, win 510, length 0
10:41:44.360028 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 438, length 64
10:41:44.606608 IP 100.96.116.98.54144 > 104.22.8.20.443: UDP, length 45
10:41:44.612685 IP 104.22.8.20.443 > 100.96.116.98.54144: UDP, length 25
10:41:44.746016 IP 100.96.116.98.43425 > 173.194.79.188.5228: Flags [P.], seq 1356738376:1356738404, ack 153885290, win 216, options [nop,nop,TS val 237883862 ecr 2459935182], length 28
10:41:44.795023 IP 173.194.79.188.5228 > 100.96.116.98.43425: Flags [P.], seq 1:27, ack 28, win 267, options [nop,nop,TS val 2460225473 ecr 237883862], length 26
10:41:44.797774 IP 100.96.116.98.43425 > 173.194.79.188.5228: Flags [.], ack 27, win 216, options [nop,nop,TS val 237883880 ecr 2460225473], length 0
10:41:44.864980 IP 40.90.9.180.443 > 100.96.116.98.64949: Flags [P.], seq 62:93, ack 1, win 2047, length 31
10:41:44.868167 IP 100.96.116.98.64949 > 40.90.9.180.443: Flags [.], ack 93, win 1020, length 0
10:41:45.360345 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 439, length 64
10:41:45.509393 IP 100.96.116.98.63228 > 20.199.120.85.443: Flags [P.], seq 4149713163:4149713266, ack 253211225, win 514, length 103
10:41:45.559269 IP 20.199.120.85.443 > 100.96.116.98.63228: Flags [P.], seq 1:174, ack 103, win 6853, length 173
10:41:45.603829 IP 100.96.116.98.63228 > 20.199.120.85.443: Flags [.], ack 174, win 513, length 0
10:41:45.731356 IP 100.96.116.98.64940 > 198.252.206.25.443: Flags [.], seq 1337624305:1337624306, ack 3357517743, win 509, length 1
10:41:45.854737 IP 198.252.206.25.443 > 100.96.116.98.64940: Flags [.], ack 1, win 62, options [nop,nop,sack 1 {0:1}], length 0
10:41:46.360654 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 440, length 64
10:41:47.320045 IP 100.96.116.98.64942 > 198.252.206.25.443: Flags [.], seq 2931856837:2931856838, ack 3465307681, win 512, length 1
10:41:47.360961 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 441, length 64
10:41:47.443511 IP 198.252.206.25.443 > 100.96.116.98.64942: Flags [.], ack 1, win 62, options [nop,nop,sack 1 {0:1}], length 0
10:41:47.922195 IP 100.96.116.98.50505 > 8.219.48.186.8053: UDP, length 32
10:41:48.226267 IP 8.219.48.186.8053 > 100.96.116.98.50505: UDP, length 32
10:41:48.361315 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 442, length 64
10:41:49.029081 IP 93.184.220.70.443 > 100.96.116.98.48746: Flags [.], ack 2973865845, win 133, length 0
10:41:49.054322 IP 68.232.34.217.443 > 100.96.116.98.49254: Flags [.], ack 3878313341, win 133, length 0
10:41:49.273108 IP 100.96.116.98.49254 > 68.232.34.217.443: Flags [.], ack 1, win 172, length 0
10:41:49.273223 IP 100.96.116.98.48746 > 93.184.220.70.443: Flags [.], ack 1, win 161, length 0
10:41:49.300799 IP 100.96.116.98.42044 > 157.240.234.34.443: Flags [R.], seq 238021736, ack 2287131363, win 135, length 0
10:41:49.302752 IP 100.96.116.98.39348 > 157.240.234.18.443: Flags [R.], seq 360121523, ack 4069983463, win 133, length 0
10:41:49.302857 IP 100.96.116.98.43978 > 104.244.42.130.443: Flags [F.], seq 4166764896, ack 2499097327, win 135, length 0
10:41:49.302922 IP 100.96.116.98.48746 > 93.184.220.70.443: Flags [F.], seq 1, ack 1, win 161, length 0
10:41:49.303106 IP 100.96.116.98.49254 > 68.232.34.217.443: Flags [F.], seq 1, ack 1, win 172, length 0
10:41:49.303389 IP 100.96.116.98.43778 > 209.237.198.128.443: Flags [F.], seq 322965606, ack 1809135230, win 135, length 0
10:41:49.303484 IP 100.96.116.98.48676 > 157.240.9.54.443: Flags [F.], seq 2020435641, ack 3618206497, win 131, length 0
10:41:49.339921 IP 68.232.34.217.443 > 100.96.116.98.49254: Flags [F.], seq 1, ack 2, win 133, length 0
10:41:49.341446 IP 100.96.116.98.49254 > 68.232.34.217.443: Flags [.], ack 2, win 172, length 0
10:41:49.345900 IP 93.184.220.70.443 > 100.96.116.98.48746: Flags [F.], seq 1, ack 2, win 133, length 0
10:41:49.347446 IP 209.237.198.128.443 > 100.96.116.98.43778: Flags [P.], seq 1:25, ack 1, win 265, length 24
10:41:49.347655 IP 209.237.198.128.443 > 100.96.116.98.43778: Flags [F.], seq 25, ack 1, win 265, length 0
10:41:49.348573 IP 100.96.116.98.48746 > 93.184.220.70.443: Flags [.], ack 2, win 161, length 0
10:41:49.350515 IP 100.96.116.98.43778 > 209.237.198.128.443: Flags [R], seq 322965607, win 0, length 0
10:41:49.351789 IP 100.96.116.98.43778 > 209.237.198.128.443: Flags [R], seq 322965607, win 0, length 0
10:41:49.361544 IP 104.244.42.130.443 > 100.96.116.98.43978: Flags [P.], seq 1:25, ack 1, win 265, length 24
10:41:49.361765 IP 104.244.42.130.443 > 100.96.116.98.43978: Flags [F.], seq 25, ack 1, win 265, length 0
10:41:49.361983 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 443, length 64
10:41:49.364697 IP 100.96.116.98.43978 > 104.244.42.130.443: Flags [R], seq 4166764897, win 0, length 0
10:41:49.364966 IP 100.96.116.98.43978 > 104.244.42.130.443: Flags [R], seq 4166764897, win 0, length 0
10:41:49.389542 IP 157.240.9.54.443 > 100.96.116.98.48676: Flags [.], ack 1, win 261, length 0
10:41:49.472432 IP 157.240.9.54.443 > 100.96.116.98.48676: Flags [F.], seq 1, ack 1, win 261, length 0
10:41:49.612569 IP 157.240.9.54.443 > 100.96.116.98.48676: Flags [F.], seq 1, ack 1, win 261, length 0
10:41:49.756543 IP 157.240.9.54.443 > 100.96.116.98.48676: Flags [F.], seq 1, ack 1, win 261, length 0
10:41:50.037561 IP 157.240.9.54.443 > 100.96.116.98.48676: Flags [F.], seq 1, ack 1, win 261, length 0
10:41:50.362314 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 444, length 64
10:41:50.644814 IP 157.240.9.54.443 > 100.96.116.98.48676: Flags [F.], seq 1, ack 1, win 261, length 0
10:41:51.362627 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 445, length 64
10:41:51.797571 IP 157.240.9.54.443 > 100.96.116.98.48676: Flags [F.], seq 1, ack 1, win 261, length 0
10:41:52.362932 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 446, length 64
10:41:53.363241 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 447, length 64
10:41:54.036840 IP 157.240.9.54.443 > 100.96.116.98.48676: Flags [F.], seq 1, ack 1, win 261, length 0
10:41:54.363548 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 448, length 64
10:41:54.866061 IP 40.90.9.180.443 > 100.96.116.98.64949: Flags [P.], seq 93:124, ack 1, win 2047, length 31
10:41:54.869281 IP 100.96.116.98.64949 > 40.90.9.180.443: Flags [.], ack 124, win 1020, length 0
10:41:55.363853 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 449, length 64
10:41:56.063689 IP 100.96.116.98.64966 > 142.250.187.132.443: Flags [.], seq 2406714257:2406714258, ack 2714818815, win 1027, length 1
10:41:56.078563 IP 142.250.187.132.443 > 100.96.116.98.64966: Flags [.], ack 1, win 504, options [nop,nop,sack 1 {0:1}], length 0
10:41:56.364162 IP6 2a02:ff0:2fc:dc9a::1 > 2606:4700:4700::1111: ICMP6, echo request, seq 450, length 64
^C
148 packets captured
148 packets received by filter
0 packets dropped by kernel