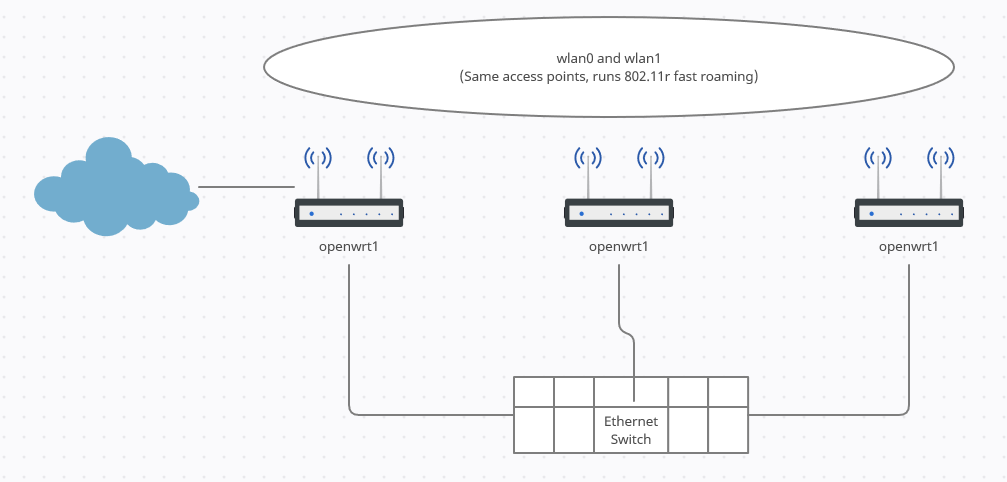
I've been using openwrt for years on a single router setup. Recently i moved into a much larger place, with lots of wifi-unfriendly materials. So got some new little gl.inet b1300 routers, and have them set up nicely like this:
This is working great... the main router talks to the ISP and handles DHCP for the whole network. The router and APs all connect to an ethernet switch, and have static IPs all on the same network. They all have both 2.4Ghz and 5GHz radios advertising the same SSID, but different channels for each. 802.11r fast roaming is turned on and everything is working great. This is my "trusted" network.
Now I am trying to figure out how to layer an untrusted IOT network on top of it. I have in particular a machine that manages video cameras. It has ethernet interfaces which need to talk to cameras hooked to IOT wifi in a different part of the house.
I've read many other forum posts, and I understand adding another SSID, a subnet for it, and how firewall rules would work between them.
What I cannot get my head around is how to handle this in the backhaul layer. On my existing backhaul, this is untagged ethernet. What I had thought to do was create a "lowtrust" interface in each openwrt, and bridge that to the wireless sub-AP that has the new IOT SSID. This seems to work if i use DHCP at each individual AP.
Then i thought I would be able to tie these separate IOT wlans together by bridging them to a tagged vlan. Therein lies my troubles. It works only between openwrt2 and openwrt3. As soon as I configure the switch in openwrt1 (the "main router"), then it recycles the wan port and from there on is unable to DHCP on wan to get address from my ISP. its weird!
I think that the only problem is on the "main" router, so have attached its configs here:
/etc/config/wireless (same in working or broken state)
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11g'
option path 'platform/soc/a000000.wifi'
option htmode 'HT40'
option channel '1'
config wifi-iface 'wifi2ghz'
option device 'radio0'
option network 'lan'
option mode 'ap'
option key '*****'
option ssid 'trusted'
option ft_over_ds '1'
option mobility_domain 'beef'
option ft_psk_generate_local '1'
option ieee80211r '1'
option disabled '0'
option ieee80211w '1'
option encryption 'psk2'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11a'
option path 'platform/soc/a800000.wifi'
option disabled '0'
option htmode 'VHT40'
option channel '149'
config wifi-iface 'wifi5ghz'
option device 'radio1'
option network 'lan'
option mode 'ap'
option key '*****'
option ssid 'trusted'
option ft_over_ds '1'
option mobility_domain 'beef'
option ft_psk_generate_local '1'
option ieee80211r '1'
option disabled '0'
option ieee80211w '1'
option encryption 'psk2'
config wifi-iface 'wifilow2'
option ssid 'lowtrust'
option encryption 'psk2'
option device 'radio0'
option ieee80211r '1'
option ft_over_ds '1'
option key '********'
option mode 'ap'
option ft_psk_generate_local '1'
option mobility_domain 'dead'
option isolate '1'
option network 'lowtrust'
/etc/config/network in "working" state:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.9.1'
option ifname 'eth0'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
option broadcast '1'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config interface 'lowtrust'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.13.1'
option type 'bridge'
option igmp_snooping '1'
option ifname 'eth0.13'
I change it just a little bridge lowtrust to the switch, then the whole thing goes to shit and wan will not dhcp anymore. It does however work in that two untrusted clients can now ping each other (firewall lock down coming a bit later) across two different access points.
/etc/config/network which breaks wan:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.9.1'
option ifname 'eth0.1'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
option broadcast '1'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 3 4'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '13'
option ports '0t 3t 4t'
config interface 'lowtrust'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.13.1'
option type 'bridge'
option igmp_snooping '1'
option ifname 'eth0.13'
Have i got this all wrong? Can someone explain a better way to handle an isolated IOT or guest network across many access points that are set up this way?