I have seen other similar questions but not with my network configuration ( IOT isolation with vlans in multi-AP environment - Installing and Using OpenWrt / Network and Wireless Configuration - OpenWrt Forum).
I have some IOT devices, which I would like to isolate in a network in order to have 2 separate networks (with the same base hardware infraestructure).
- One home network where the PCs, tablets, phones... of the family members would connect (wirelessly 2.4G or 5G, depending on their capabilities, or through ethernet).
- One IOT network where the thermostat, controllers, ip cameras or other IOT devices would be connected wirelesly. For now I don't have any iot device that has an ethernet interface.
The idea is to not let iot devices connect to internet, just among them and with the router.
They should not connect to the home lan either. So they can't send any info to cloud services or internet inadvertidly (with all that devices coming from china or other uncertain sources I don't want anybody to take control of my home).
But to simplify things (configuration or testint of devices, which usually exhibit an http interface) I would let alll devices from home lan connect to the iot lan.
A don't know if this approach can have security risks.
Any opinion about what would be the best approach and more secure would be wellcome (taking into acount simplicity, my home is not the NASA or the central bank either).
One problem I can think of is updating firmware to the devices. Many can be updated via OTA (that won't be directly posible from internet, as they won't be connected to internet) but you can allways use http connection to uplodad a file. OTA from the device won't work either from a file in the home lan as devices cannot access the lan network (there is always the posibility of configuring exceptions).
The second part of the problem is how to achieve that planning.
I would describe my current config with the home lan network.
I would like to change it (in the hardware part) as few as possible, and maintain the number of needed devices to the minimum (no new routers, gateways etc, if possible).
There are two parts in the home that are enough far away to don't be able to reach wifi network from one part to the other: backside and frontside.
So I have:
-
One gateway at the backside of the home.It is the one provided by the ISP.
It acts mainly as the gateway to direct traffic to ISP WAN. No other services are installed in it (that is the task of the main router), but it is configured as a WIFI access point for devices in the backside of the home (with the same SSID and password as the main router, to provide itinerancy), and ethernet access to a couple of computers. IP addresses are served by the main router.
This device is to configure more SSID to give access to the iot devices, but it is limited in functions and configuration possibilities (as the firmware is from the ISP). -
One main router at the front of the home. It is a fritzBox 440 with openWRT installed (last version, 21.02.1). It is the DHCP server to provide IPs. It acts as the local DNS server for the home devices too. It has configured mDNS with a .home domain for easy accessing the NAS server or other devices that need to be accesses with a known IP and which have assigned static IPs in the DHCP config.
It has installed mosquito MQTT server too in order to act as the MQTT borker of the home (this service of course should be accessible from IOT network).
It has connected a QNAP NAS to its ethernet port and provides a WIFI access point to the devices at the front of the home, with the same SSID and password aste AP in the gatewate at the back side.
In order to achive the goals of isolating iot devices without adding more devices to the network as routers or gateways, I have:
- Created another wifi lan at the main openWRT router, lets call it IOT Wifi, with its own different SSID and password.
- Configured a new interface named IOT that is only linked to that wifi in the network field during creation.
- configured the iot interface with protocol "static adress" with an IP address in a private Class B network different from the private IP network of the home lan.
- Configured DHCP to serve IPs to devices connected to that iot interface.
- I have not created VLANs for now at the switch level to assign ports to the iot lan, as there is not yet any ethernet iot device, and I would like to keep things as simple as possible.
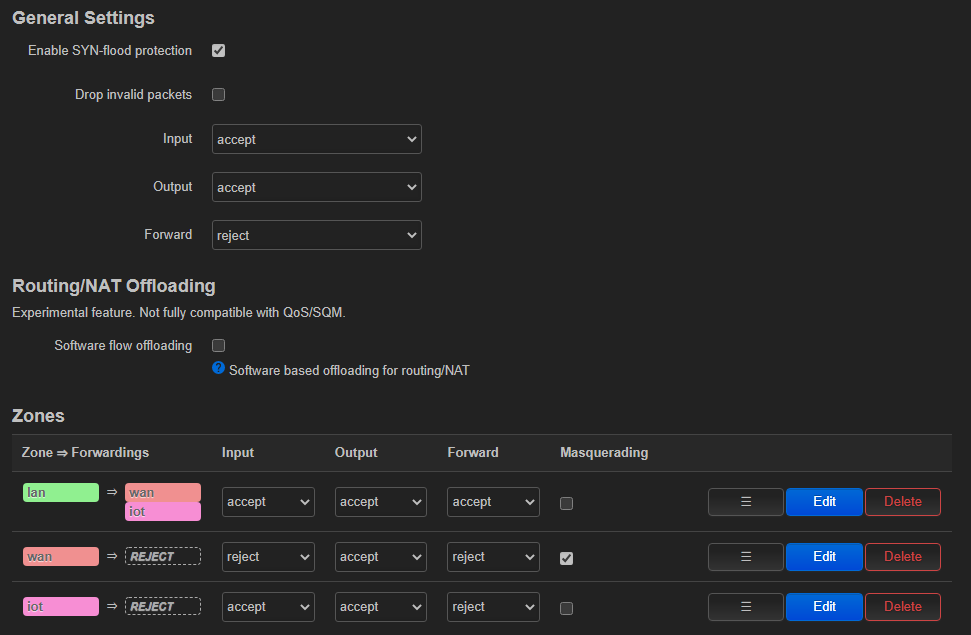
- I have configured a firewall rule to reject all traffic coming from iot zone to other zones, and to accept redirected traffic from lan to iot, as it can be seen in the image (the wan zone is not really used, as the wan port of the router is disable, as it is not directly connected to the internet, internet traffic is redirected to the ISP gateway configuring it as the gateway of the home lan interface in the main router).
At the ISP gateway in the backside, I have created another IOT wifi access point with the same SSID and password as the one at the frontside, in order to provide wifi connection to the IOT network to the devices at the backside.
It seems to work now to some extend.
I can connect to the IOT wifi in the main router and I get a new IP in the iot network, and I get an adviertizement that I don't have internet connection.
But I could not solve some things yet:
- I am not sure if the firewall rules are OK and devices from home lan can connect to the iot devices, but not viceversa.
- I don't know how to provide IOT address to the devices connected to IOT wifi at the BACKSIDE of the home, to the ISP gateway. Devices connected there get addresses from the home lan, I think.
- I don't know how to config mDNS in order to create a separate .iot domain, different from the .home local domain, to give iot devices easy access names instead of having to remember IPs.
Any help and ideas would be wellcome.