As I have comented in other thead, I want to create an IOT network in my home isolated from main home lan and internet.
In the other thread, I was given ideas of how to configure firewall, vlans and other things and was adviced about the need of installing another openwrt router, and use isp router only as bridge, and that is I would like to do.
But I need advice about the phisical and logical topology of the network.
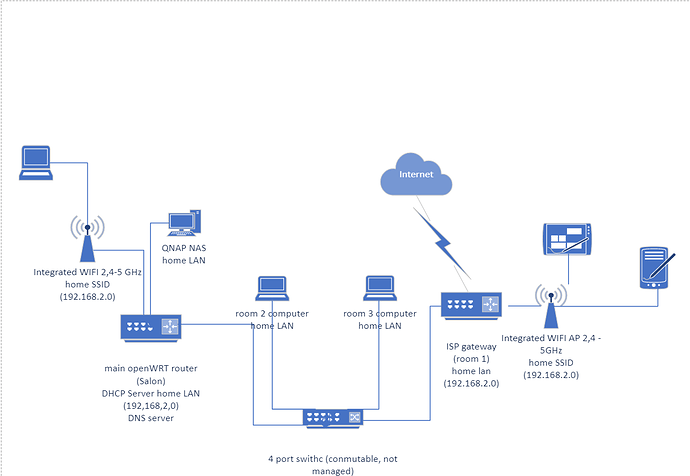
I am going to explain how it is now (I put here the network diagram):
In my house there is a comunications cabinet (very small, just an electric cabinet indeed) were arrive TV cable from the outside and fiber.
All ethernet cat 6 wires from the 5 rooms are connected directly to that cabinet.
So there is a 1 Gb switch (conmutable and non managed) installed there.
As it is quite small, the fiber optical wire was extended from there to a room (room 1 in the backside of the home) were reside a couple of computers connected to the ISP gateway and the home lan, and it provides WIFI access to the home SSID (connected to the home lan).
In the front side of the home, as the wifi does not reach there, I have installed a better (fritzbox 4040) router with openWRT, which is the DHCP server the home LAN (the gateway is the ISP router) and DNS server usind dnsmasq to integrate dns with dhcp leases, forming a .home domain and being the DNS primary server for the entire home LAN. DNS queries for other domains are redirected to well known DNS servers in internet.
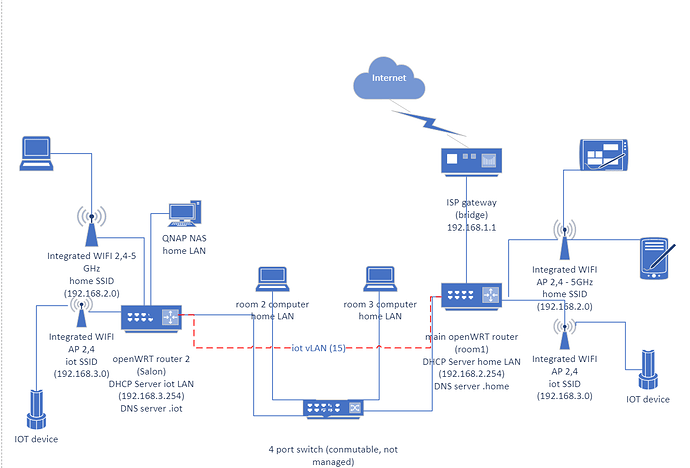
As I said, now I want to add a second separate lan for iot (let us call it iot) accesible from wifi with its own ssid and isolated. So I will use vlan 15 for iot net traffic, where for now will be connected the wifi iot in the main router and the router in the other room (to substitute the ISP router).
I can think of two possible configuration: just adding a new vlan with other IP net (192.168.3.0) and a DHCP server and DNS server in the other router.
One of the routers would be the DNS and DHCP server for home network (the new main router) and the other for the iot network, with separate IP networks and connected between them through a VLAN (15) for iot traffic. New SSID WIFIs would be created in both routers in order to provide access to iot wifi device. If there were some ethernet device in the future, the corresponding switch port would be assigned to the VLAN 5.
I seems quite simple and similar to what I have now, with all home devices in the same IP network and iot devices in another network.
Thus the switches would not have to send packets to the routers when two devices in the same IP network interconnect among them, it can be solved at the layer 2 using MACs (once the MAC have been discovered).
More or less like this:
An alternative would be to let each router assign DHCP adresses to the devices that connect to it in separate IP networks (one for iot and one for the home lan) so there would be 2 IP networks for iot and 2 for home lan that would, with static routes to send traffic from home IP net to home IP net and IOT IP net and iot IP net.
The advantage would be knowing by IP to which router a devices is connected.
But it would be more comples and ... less efficient?
If a device connected to one router has to send packets to a device connected to the other router it will have to send the packet to the other router and be dispateched at level 3, the switch won't be able to distribute that traffic.
Devices connected to the switch is not known, which router would be connected to?
I think the previous aproach can be easier and better, but am not sure if there can be problems.