Well I have been testing the configuration.
And it seems to work EVEN with the unmanaged and not VLAN aware switch in between.
I have configured to test routers connected by a wire with a lan and vlan IOT in it through the switch. And I can ping between two devices connected to the IOT wifi of each router, so it seems to work OK.
Anyway I will upgrade the switch to a managed switch (and maybe POe to be able to provide some access point to one room without having to add an electrical cable, as there are some wall APs with POe that seem just an ethernet plug).
But I am not sure of having configured all things OK.
And there remain some problems with DHCP and DNS that I could not solve yet.
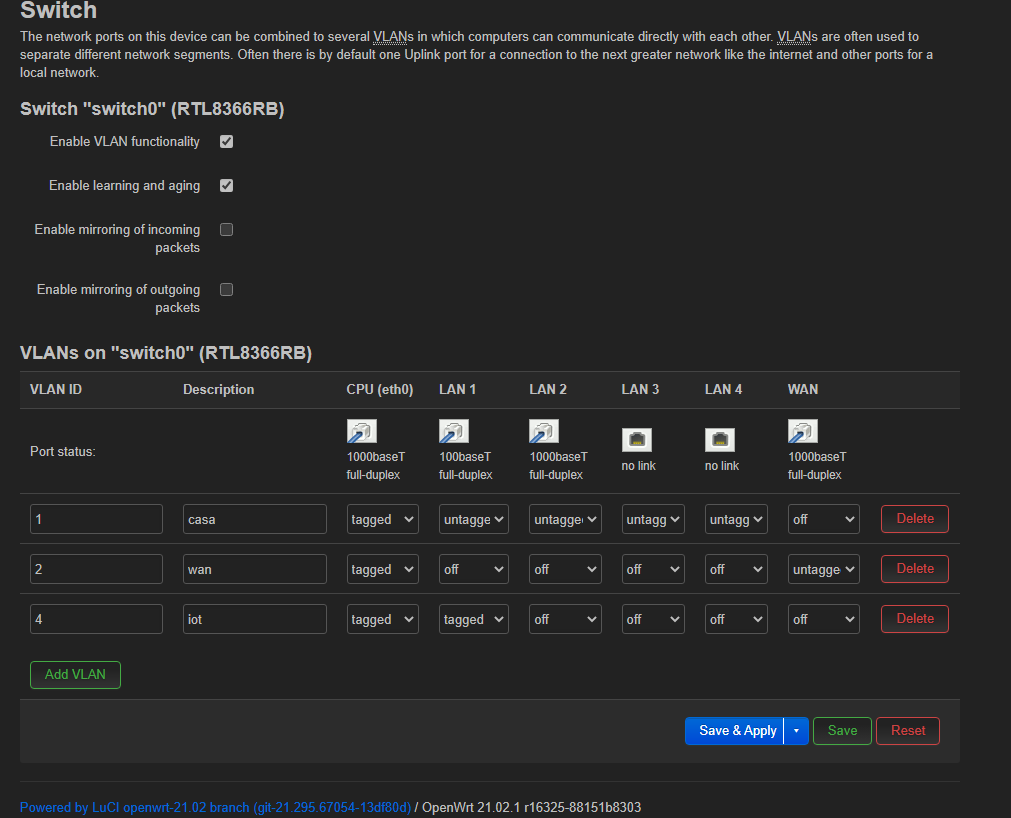
This is the switch configuration of the main router:
the 1 vlan is the one that transport the main traffic, the lan with no internet connection restrictions.
the vlan 2 is for the wan port to route traffic to the isp provider, as this router has the wan port integrated in the switch.
the 4 vlan is the one I created to the iot network for iot device interconnection with no internet connection.
The port one is the one that connects to the other router via ethernet cable (with the unmaged switch in the middle).
The other router has the same config with no wan vlan or interfaces.
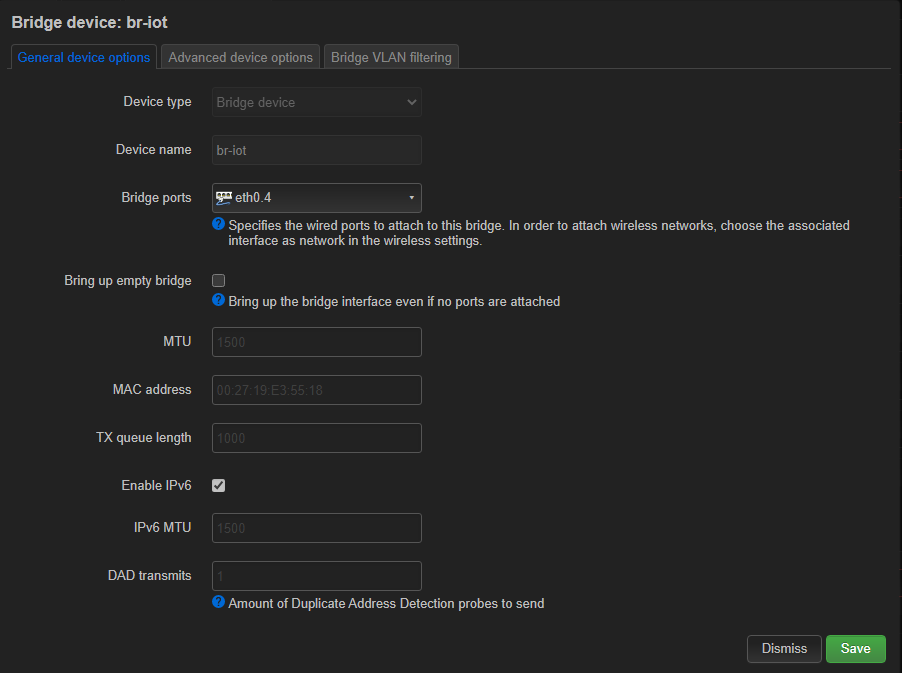
Then I created a bridge device for interconnection of the iot WIFI and the vlan # 4 (iot) in both routers:
The other tabs are left as they are by default.
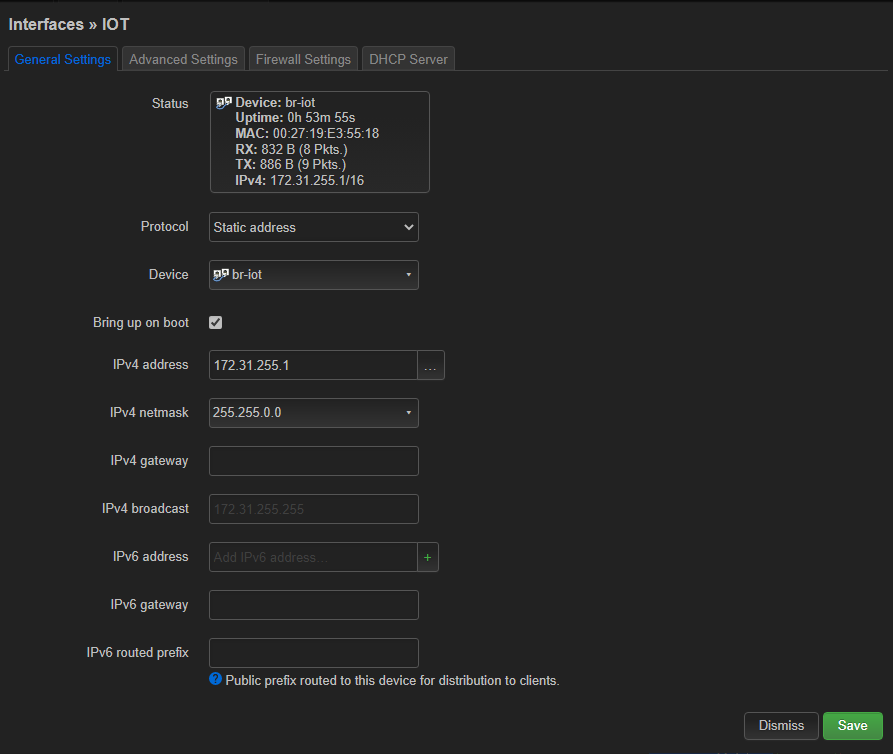
Then I created the IOT interface, with the iot bridge as base device.
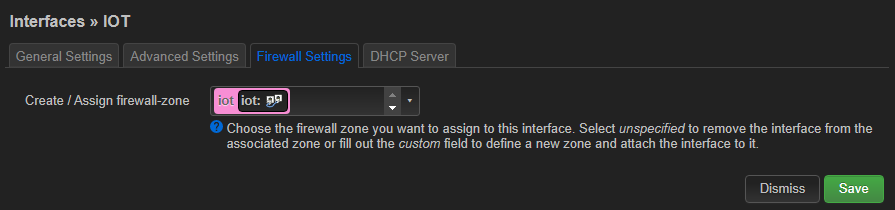
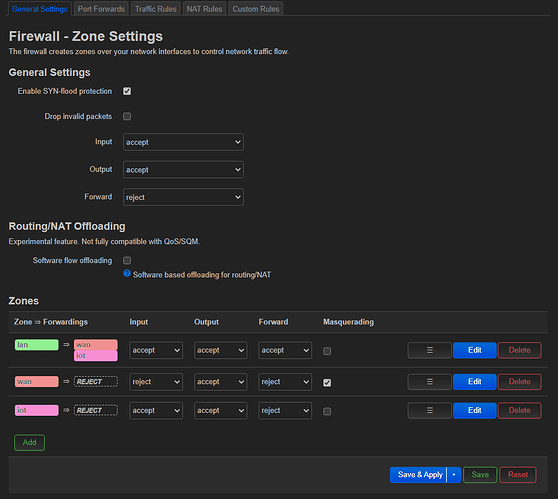
An I created a firewall zone:
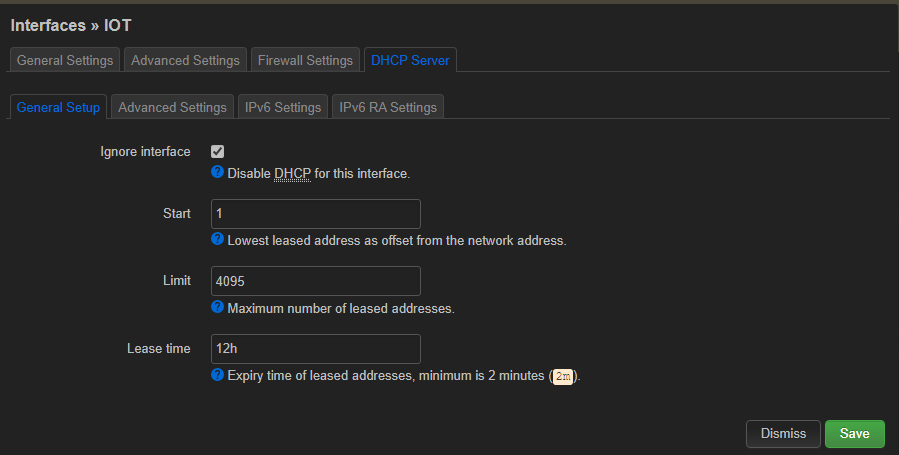
And configured dhcp server in the main router (in the other router it is disabled for both, lan and iot networks):
The other router the same, but with differente static address (of course) and dhcp disable.
And lastly, I created the wifi SSID and assigned it the IOT interface:
The other router has identical wirless config.
And to end with, the firewall rules, just dropping all outbound traffic from the iot zone, and accpting only traffic from lan zone (same fro both):
Is this correct?
You told me that in iot zone input should be "reject". But won't that drop incoming connection from lan network?
Or the reject option is just the default for all other zones not explicitly listed as source for iot zone?
It seem to be working (I have to test it more and see if the isolations is working correctly).
But I have some problems.
As it is now the main router provides DHCP to both networks and DNS.
But it cannot provide DNS registering for the IOT network, as there is only one domain you can configure in dnsmasq LUCI interface.
You have provided an advance mode to install two dnsmasq instances in the main router, but then it seems that you cannot configure dns through LUCI interface, something I would like to avoid.
The dns for IOT domain could be assigned to the other router, but in order to get proper registration of devices that are given a lease, the DHCP should be running in that router.
I could activate it and assign IPs to the iot devices just in the IOT interface of the secondary router, and to the lan interface in the main router.
But even if only one of the router is assignen IPs to one net, when you activate both, there is a conflict and one of them stops assigning IPs.
I have tried to use the "listen interface option" in the DNS config panel, but it does not seem to work as I had expected.
Is it possible for a dhcp instance to register the devices that have been otrogued a lease in a DNS instance that is running in other openWRT router?
 now they count full duplex as 2Gb... There are 10 Gb cards, probably not giving that speed, I thought they were being honest and saying the real speed the switch can achive.
now they count full duplex as 2Gb... There are 10 Gb cards, probably not giving that speed, I thought they were being honest and saying the real speed the switch can achive.