Documenting my adventures with EdgeRouter X (ERX), which was originally used as the main router on my home network, but ended up being a managed switch for a "router-on-a-stick" Mini-PC. Both the Mini-PC router and the ERX run under OpenWrt.
The original problem I had with my ERX is that it was often freezing while running under OpenWrt 19.07.0x, which seems to be a common issue with ERX. I did try troubleshooting it but to no avail.
I then repurposed a spare x86 Mini PC as a "router-on-a-stick", and tried using the ERX as a managed switch for it, like this:
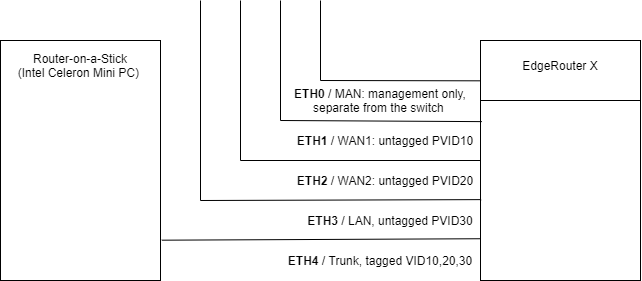
That worked, but the ERX was still hanging. I then asked Redditors for recommendations of a decent managed SOHO switch, other than ERX, with an option to isolate the management port. Apparently, the today's choice of those are rather limited. Presumably, TRENDnet TEG-S80ES is capable of isolating its management UI (emulator).
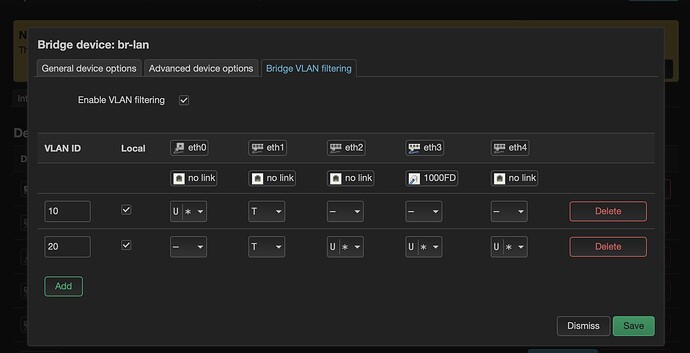
I've also tried reverting the ERX back to the latest sock Ubiquiti EdgeOS and configuring it as a managed Layer-2 switch. I couldn't get it working for the VLAN setup as on the picture above, I gave up after an hour of fiddling.
Then I stumbled upon this Q/A. Apparently, the freezing stops being an issue with the newer MT7621 SoC driver for the DSA mode, which is used by the Linux kernel v5+ in current OpenWrt snapshot builds.
So, I've decided to give my ERX a final try, now under the latest OpenWrt snapshot build. And so far, so good! It's been stable for over a week now.
The snapshot builds of OpenWrt currently don't have the Switch menu for configuring DSA switches in the Luci UI. A manual configuration is required, and it took me quite a while to figure out how to apply it to EdgeRouter X. Here's what I've come up with, for the future reference:
-
Updated, install
ip-bridgeandip-fullpackages (for proper functioning ofbridgeandip link set dev $SW type bridge vlan_filtering 1commands):opkg update && opkg install ip-full ip-bridge
/etc/config/network
I use eth0 for emergency management, it isn't a part of the switch. Normally, the switch can also be managed via a DHCP address it obtains from the Mini-PC router's LAN segment:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
config interface 'man'
option ifname 'eth0'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option delegate '0'
config interface 'switch'
option ifname 'sw0'
option proto 'dhcp'
option delegate '0'
/etc/hotplug.d/iface/21-switch
This script does the actual job on manually creating the new sw0 bridge interface and configuring its VLANs. I couldn't think of a better place for running this logic, other than upon the ifup hotplug hook for localhost interface.
#!/bin/sh
[ "$INTERFACE" = loopback ] && [ "$ACTION" = ifup ] || exit 0
# name of the bridge
SW="sw0"
logger "Configuring VLANs on $SW..."
# create the SW bridge
if [ ! -d "/sys/class/net/$SW" ]
then
ip link add name $SW type bridge
else
ip link set $SW down
fi
# enable VLAN filtering
ip link set dev $SW type bridge vlan_filtering 1
ip link set dev $SW type bridge vlan_default_pvid 1
logger "VLAN filtering enabled: $(cat /sys/class/net/$SW/bridge/vlan_filtering)"
ip link set dev eth1 master $SW
ip link set dev eth2 master $SW
ip link set dev eth3 master $SW
ip link set dev eth4 master $SW
# clear out the default vlan id 1 on SW
bridge vlan del dev eth1 vid 1
bridge vlan del dev eth2 vid 1
bridge vlan del dev eth3 vid 1
bridge vlan del dev eth4 vid 1
bridge vlan del dev $SW self vid 1
# set vlan for eth1 (WAN1)
bridge vlan add dev eth1 vid 10 pvid untagged
# set vlan for eth2 (WAN2)
bridge vlan add dev eth2 vid 20 pvid untagged
# set vlan for eth3 (LAN)
bridge vlan add dev eth3 vid 30 pvid untagged
# set vlans for eth4 (trunk)
bridge vlan add dev eth4 vid 10
bridge vlan add dev eth4 vid 20
bridge vlan add dev eth4 vid 30
# set vlans of the CPU port (LAN)
bridge vlan add dev $SW self vid 30 pvid untagged
# bring up interfaces
ip link set eth1 up
ip link set eth2 up
ip link set eth3 up
ip link set eth4 up
/etc/sysupgrade.conf
We need to add 21-switch to the list of persistent scripts:
## This file contains files and directories that should
## be preserved during an upgrade.
# /etc/example.conf
# /etc/openvpn/
/etc/hotplug.d/iface/21-switch
For completeness, here is /etc/config/network from my Mini-PC router, which has only one Ethernet port and uses driver-level tagged VLANs for WAN1, WAN2 and LAN:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config device
option type '8021q'
option ifname 'eth0'
option vid '10'
option name 'vlan10'
config device
option type '8021q'
option ifname 'eth0'
option vid '20'
option name 'vlan20'
config device
option type '8021q'
option ifname 'eth0'
option vid '30'
option name 'vlan30'
config interface 'lan'
option ifname 'vlan30'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.3.1'
option delegate '0'
config interface 'wan'
option ifname 'vlan10'
option proto 'dhcp'
option delegate '0'
option hostname 'router'
Hope this may help others and my future self. Alternatively, a Raspberry Pi could be used in place of the x86/x64 Mini PC.