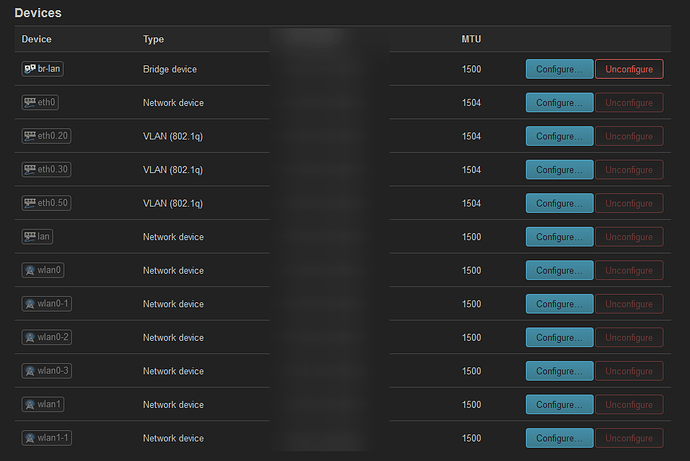
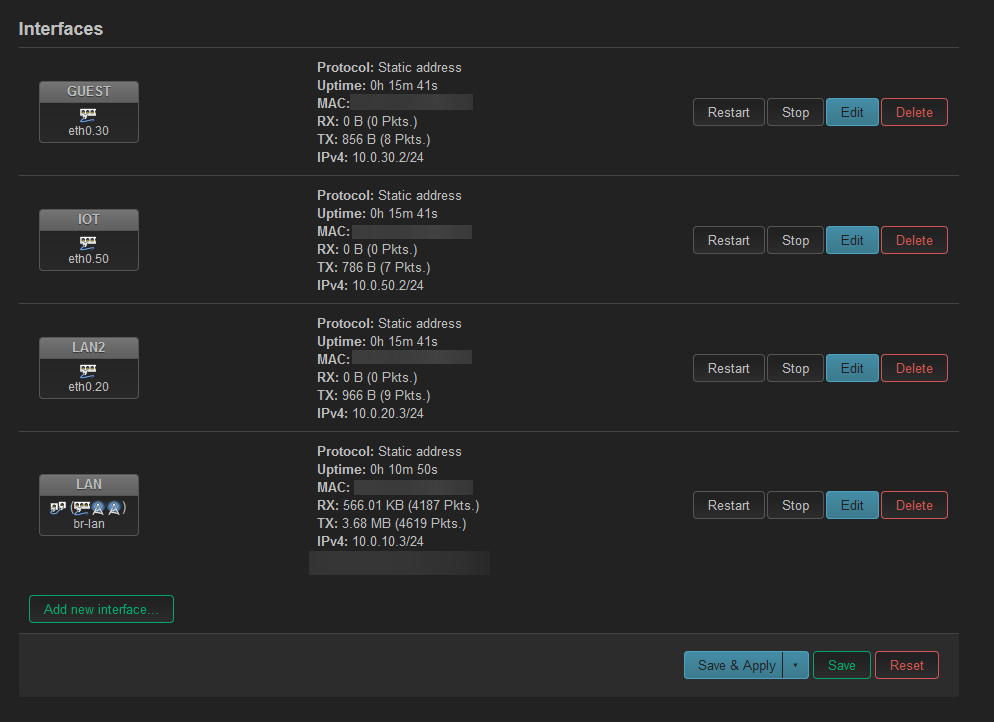
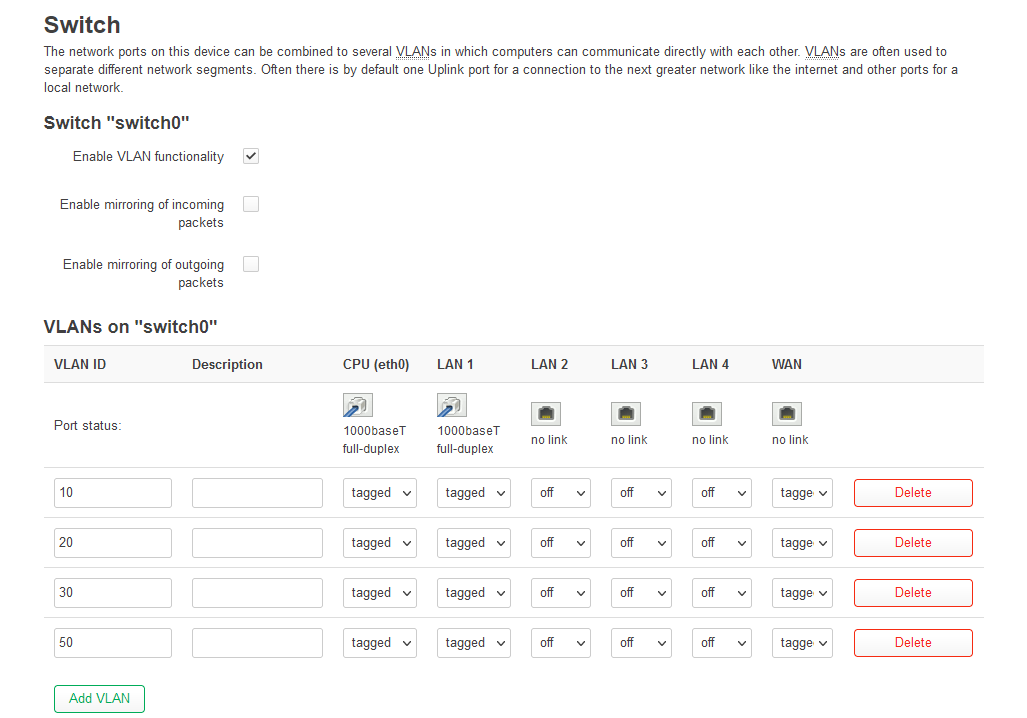
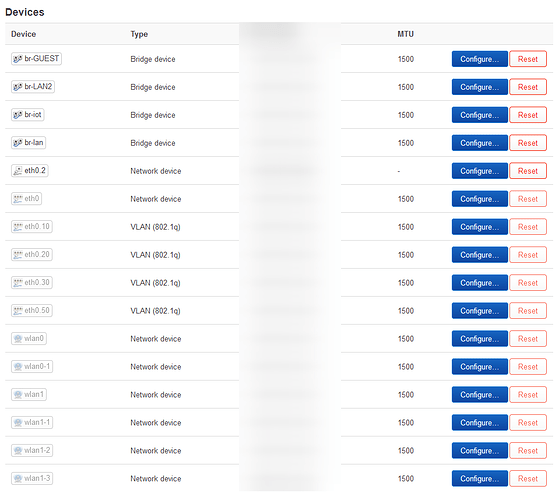
I can't say I'm extremely familiar with vlan concepts, this is my first time doing this really.
I figured this would all be pretty cookie cutter seeing literally nothing is changing. The only thing that is changing is there is no switch built into the Unifi. However I only had one cable going to my old AP anyways, and there's one cable going to this AP.. so I don't see why it would have issues.
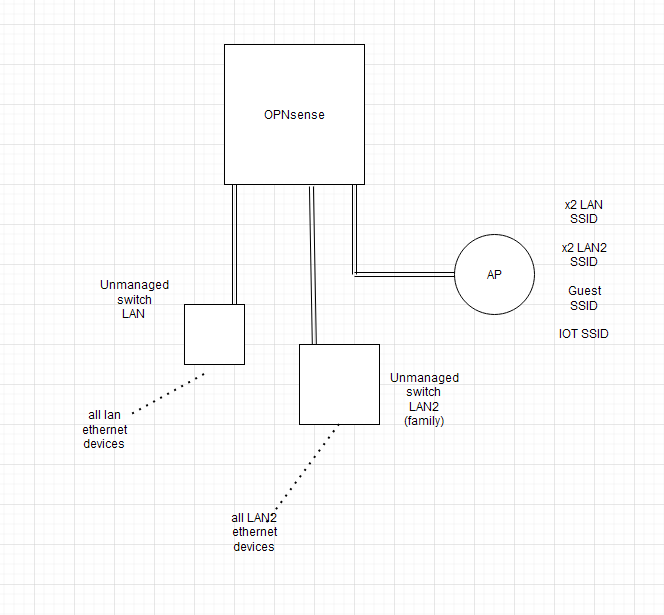
However I believe an issue is I am not currently incorporating a managed switch into my setup, although there is some separation.
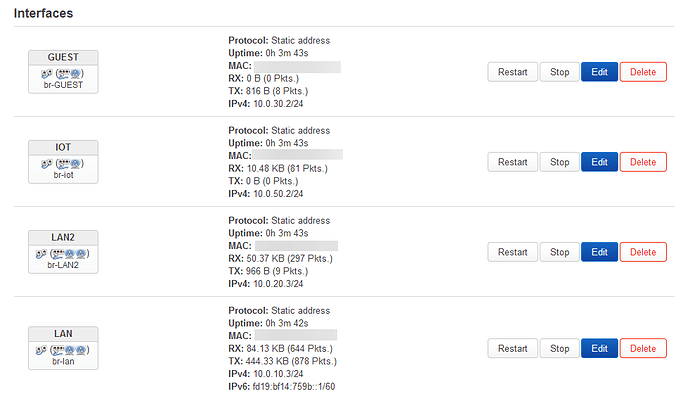
What is basically is is, I have a few ports on the back of my firewall. I have one for wan, one for my lan which runs to an unmanaged switch with all my devices, one for lan2 which runs to an unmanaged switch for all my family devices, and one for the access point.
So LAN and LAN2 each have their own ethernet port, and 2 wireless ssids each. Guest and IoT have no ethernet, and one wireless SSID each. LAN and LAN2 isolated from one another, Guest and IoT also isolated from everyone else. Some stuff crosses over manually via specific port rules.
It hasn't been an issue like this because all my families devices are on one unmanaged switch as previously stated. And all my devices are on another so that is the separation right there to substitute for a managed switch. I have one but I do not have the time to figure out setup on it, I plan to work on it in the future but I wanted to get this AP setup hopefully soon.
Basically lan is bridged on opnsense between my lan port, and the vlan tag so lan has wireless and ethernet. Same for lan2. Then for guest it only has a vlan so it only has wireless, and then same for IoT.
I will start by providing the information for my old access point seeing that is the one currently in use:
# cat /etc/config/network
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config globals 'globals'
option ula_prefix ''
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '10.0.10.1'
option ipaddr '10.0.10.3'
option gateway '10.0.10.2'
option device 'br-lan'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr ''
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '10'
option ports '0t 2t 1t'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '20'
option ports '0t 2t 1t'
config interface 'LAN2'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.0.20.3'
option gateway '10.0.20.2'
list dns '10.0.10.1'
option device 'br-LAN2'
config interface 'GUEST'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.0.30.2'
option gateway '10.0.30.1'
list dns '10.0.10.1'
option device 'br-GUEST'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '30'
option ports '0t 2t 1t'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.10'
config device
option name 'br-LAN2'
option type 'bridge'
list ports 'eth0.20'
config device
option name 'br-GUEST'
option type 'bridge'
list ports 'eth0.30'
config interface 'IoT'
option proto 'static'
option ipaddr '10.0.50.2'
option netmask '255.255.255.0'
option gateway '10.0.50.1'
option device 'br-iot'
config switch_vlan
option device 'switch0'
option vlan '5'
option vid '50'
option ports '0t 2t 1t'
config device
option type 'bridge'
option name 'br-iot'
list ports 'eth0.50'
option ipv6 '0'
# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option country 'US'
option cell_density '0'
option htmode 'VHT40'
option channel 'auto'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'LAN5ghz'
option key ''
option ieee80211w '2'
option encryption 'psk2+ccmp'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option cell_density '0'
option htmode 'HT20'
option channel '3'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'LAN24ghz'
option key ''
option encryption 'psk2+ccmp'
config wifi-iface 'wifinet2'
option device 'radio1'
option mode 'ap'
option ssid 'LAN25ghz'
option network 'LAN2'
option key ''
option encryption 'psk2+ccmp'
config wifi-iface 'wifinet3'
option device 'radio0'
option mode 'ap'
option ssid 'LAN2-2ghz'
option network 'LAN2'
option key ''
option encryption 'psk2+ccmp'
config wifi-iface 'wifinet4'
option ssid 'GuestWireless'
option device 'radio1'
option mode 'ap'
option isolate '1'
option network 'GUEST'
option macfilter 'deny'
option key ''
option encryption 'psk2'
config wifi-iface 'wifinet5'
option device 'radio1'
option mode 'ap'
option key '
option network 'IoT'
option encryption 'psk2+ccmp'
option ssid 'IoTWireless'
option wmm '0'
option ieee80211w '1'
I will report back soon with the Unifi configs.
I can't grab my OPNsense configs atm, but if you can tell me the exact files and ideally paths if you don't mind, you want to see on it I can grab it when I get home. Hopefully this gives you something to work with for now though.
Edit:
Here are the Unifi configs:
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix ''
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '10.0.10.1'
option ipaddr '10.0.10.3'
option gateway '10.0.10.2'
config interface 'LAN2'
option proto 'static'
option device 'eth0.20'
option ipaddr '10.0.20.3'
option netmask '255.255.255.0'
option gateway '10.0.20.2'
option type 'bridge'
config interface 'IOT'
option proto 'static'
option device 'eth0.50'
option ipaddr '10.0.50.2'
option netmask '255.255.255.0'
option gateway '10.0.50.1'
option type 'bridge'
config interface 'GUEST'
option proto 'static'
option device 'eth0.30'
option ipaddr '10.0.30.2'
option netmask '255.255.255.0'
option gateway '10.0.30.1'
option type 'bridge'
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fded:26c9:2d14::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '10.0.10.1'
root@:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:00.0/0000:01:00.0'
option band '2g'
option htmode 'HT20'
option channel 'auto'
option cell_density '0'
config wifi-device 'radio1'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
option band '5g'
option htmode 'HE80'
option channel 'auto'
option cell_density '0'
config wifi-iface 'wifinet3'
option device 'radio1'
option mode 'ap'
option key ''
option network 'lan'
option ssid 'LAN5ghz'
option encryption 'sae-mixed'
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'ap'
option encryption 'sae-mixed'
option key ''
option network 'lan'
option ssid 'LAN24ghz'
config wifi-iface 'wifinet2'
option device 'radio0'
option mode 'ap'
option encryption 'sae-mixed'
option key ''
option network 'LAN2'
option ssid 'LAN25ghz'
config wifi-iface 'wifinet4'
option device 'radio0'
option mode 'ap'
option ssid 'Wayne Manor Guest2'
option encryption 'sae-mixed'
option key ''
option network 'GUEST'
option isolate '1'
config wifi-iface 'wifinet5'
option device 'radio0'
option mode 'ap'
option encryption 'sae-mixed'
option key ''
option network 'IOT'
option ssid 'IoT
config wifi-iface 'wifinet6'
option device 'radio1'
option mode 'ap'
option encryption 'sae-mixed'
option key ''
option network 'LAN2'
option ssid 'LAN22.4