Hi,
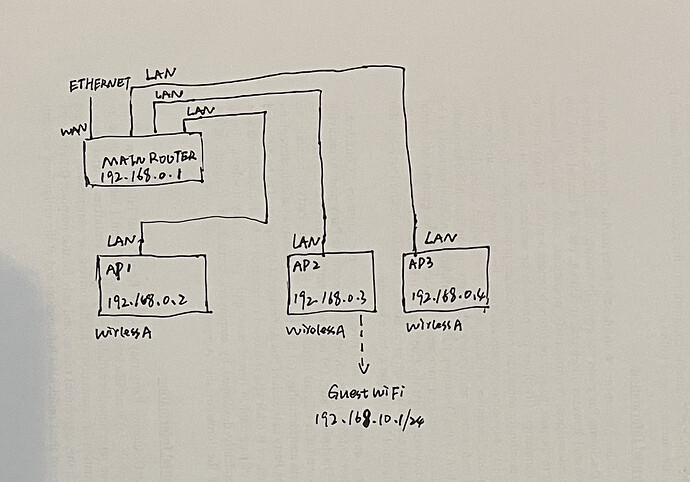
I'm using 4 routers to setup my network, all are running 21.02.1. One main router and three APs.
.
The main router provides DHCP, Firewall and DNS services, and DHCP are disabled for all APs LAN interfaces, and gateway points to main router (192.168.0.1)
All APs have been enabled 802.11r and run same SSID as WirelessA, as you can see from the diagram, all APs connect to main router via LAN, the WANs of APs aren't in use, and all APs work well.
Now, I wish to setup a separated guest network using a subnet (192.168.10.1/24) for all my IoT devices on the 2nd AP (AP2) to prevent the local resources access like NAS etc. (which are connected to the main router). I created a new interface in AP2 which enabled DHCP and firewall.
I followed this link to set the Guest Wi-Fi, the major commands are as followings, but I did a little modifiction, changed uci set firewall.guest_wan.dest="wan" to uci set firewall.guest_wan.dest="lan"
# Configure network
uci -q delete network.guest_dev
uci set network.guest_dev="device"
uci set network.guest_dev.type="bridge"
uci set network.guest_dev.name="br-guest"
uci -q delete network.guest
uci set network.guest="interface"
uci set network.guest.proto="static"
uci set network.guest.device="br-guest"
uci set network.guest.ipaddr="192.168.3.1"
uci set network.guest.netmask="255.255.255.0"
uci commit network
/etc/init.d/network restart
# Configure wireless
WIFI_DEV="$(uci get wireless.@wifi-iface[0].device)"
uci -q delete wireless.guest
uci set wireless.guest="wifi-iface"
uci set wireless.guest.device="${WIFI_DEV}"
uci set wireless.guest.mode="ap"
uci set wireless.guest.network="guest"
uci set wireless.guest.ssid="guest"
uci set wireless.guest.encryption="none"
uci commit wireless
wifi reload
# Configure DHCP
uci -q delete dhcp.guest
uci set dhcp.guest="dhcp"
uci set dhcp.guest.interface="guest"
uci set dhcp.guest.start="100"
uci set dhcp.guest.limit="150"
uci set dhcp.guest.leasetime="1h"
uci commit dhcp
/etc/init.d/dnsmasq restart
# Configure firewall
uci -q delete firewall.guest
uci set firewall.guest="zone"
uci set firewall.guest.name="guest"
uci set firewall.guest.network="guest"
uci set firewall.guest.input="REJECT"
uci set firewall.guest.output="ACCEPT"
uci set firewall.guest.forward="REJECT"
uci -q delete firewall.guest_wan
uci set firewall.guest_wan="forwarding"
uci set firewall.guest_wan.src="guest"
# A little change here, since no wan is in use, change wan to lan
# uci set firewall.guest_wan.dest="wan"
uci set firewall.guest_wan.dest="lan"
uci -q delete firewall.guest_dns
uci set firewall.guest_dns="rule"
uci set firewall.guest_dns.name="Allow-DNS-Guest"
uci set firewall.guest_dns.src="guest"
uci set firewall.guest_dns.dest_port="53"
uci set firewall.guest_dns.proto="tcp udp"
uci set firewall.guest_dns.target="ACCEPT"
uci -q delete firewall.guest_dhcp
uci set firewall.guest_dhcp="rule"
uci set firewall.guest_dhcp.name="Allow-DHCP-Guest"
uci set firewall.guest_dhcp.src="guest"
uci set firewall.guest_dhcp.dest_port="67"
uci set firewall.guest_dhcp.proto="udp"
uci set firewall.guest_dhcp.family="ipv4"
uci set firewall.guest_dhcp.target="ACCEPT"
uci commit firewall
/etc/init.d/firewall restart
The problem is that the connection to guest wifi has no issue, but no internet access. Did I miss anything? Don't very understand this part, any help would be appreciated. Thanks.