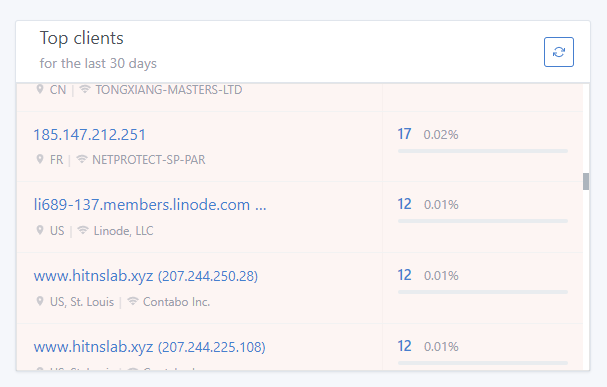
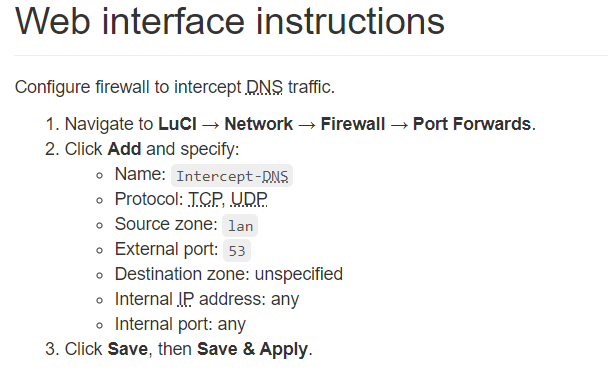
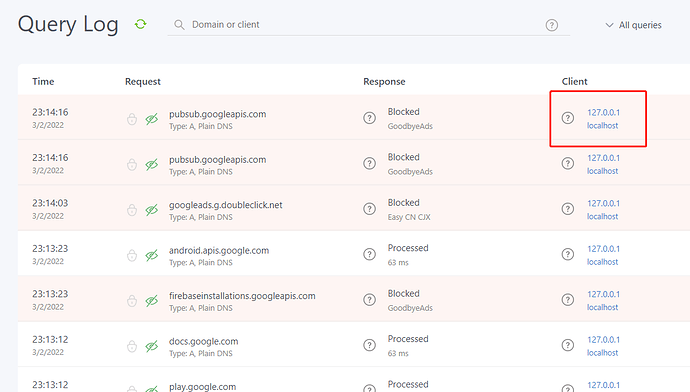
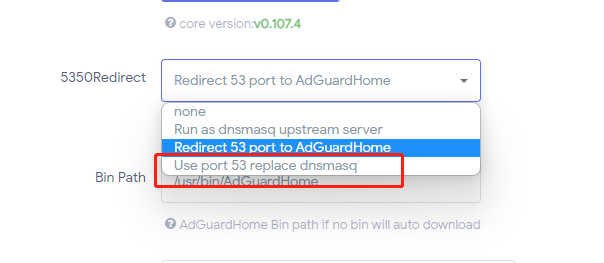
Thanks for the quick respond.
trendy:
That sounds worrying.
Well, because I am using Adguard Home, so I guess that's why port 53 is open. I didn't open it by myself.
$ ubus call system board; \
uci export network; uci export dhcp; uci export firewall; \
head -n -0
/etc/firewall.user; \
iptables-save -c; ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
ls -l /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/* ; head -n -0 /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/*
{
"kernel": "5.4.162",
"hostname": "",
"system": "ARMv8 Processor rev 4",
"model": "FriendlyElec NanoPi R2S",
"board_name": "friendlyarm,nanopi-r2s",
"release": {
"distribution": "ImmortalWrt",
"version": "18.06-5.4-SNAPSHOT",
"revision": "r11598-55a2113503",
"target": "rockchip/armv8",
"description": "ImmortalWrt 18.06-5.4-SNAPSHOT r11598-55a2113503 (2022-02-04)"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
config interface 'lan'
option type 'bridge'
option ifname 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.'
option dns '192.168.'
config device 'lan_eth1_dev'
option name 'eth1'
option macaddr ''
config interface 'wan'
option ifname 'eth0'
option _orig_ifname 'eth0'
option _orig_bridge 'false'
option proto 'pppoe'
option username ''
option password ''
option ipv6 'auto'
option keepalive '0'
config device 'wan_eth0_dev'
option name 'eth0'
option macaddr ''
config interface 'wan6'
option ifname 'eth0'
option _orig_ifname 'eth0'
option _orig_bridge 'false'
option proto 'pppoe'
option username ''
option password ''
option ipv6 'auto'
option keepalive '0'
config wireguard_vpn0
option public_key ''
list allowed_ips '192.168.1.2/32'
option route_allowed_ips '1'
option preshared_key ''
option persistent_keepalive '25'
config interface 'wg0'
option proto 'wireguard'
option listen_port ''
list addresses ''
option private_key ''
config wireguard_wg0
list allowed_ips ''
option route_allowed_ips '1'
option public_key ''
option preshared_key ''
option persistent_keepalive '25'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option nonwildcard '1'
option localservice '1'
option dns_redirect '1'
option ednspacket_max '1232'
option localuse '1'
option port '53'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
list server '127.0.0.1#5350'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config host
option name 'ServerPC'
option dns '1'
option mac ''
option ip ''
option leasetime 'infinite'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option fullcone '1'
option flow_offloading '1'
option flow_offloading_hw '1'
option drop_invalid '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config include 'zerotier'
option type 'script'
option path '/etc/zerotier.start'
option reload '1'
config include 'gowebdav'
option type 'script'
option path '/var/etc/gowebdav.include'
option reload '1'
config include 'openclash'
option type 'script'
option path '/var/etc/openclash.include'
option reload '1'
config include 'passwall'
option type 'script'
option path '/var/etc/passwall.include'
option reload '1'
config include 'passwall_server'
option type 'script'
option path '/var/etc/passwall_server.include'
option reload '1'
config include 'softethervpn'
option type 'script'
option path '/usr/share/softethervpn/firewall.include'
option reload '1'
config include 'wrtbwmon'
option type 'script'
option path '/etc/wrtbwmon.include'
option reload '1'
config zone 'vpn'
option name 'vpn'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option network 'vpn0 wg0'
config forwarding 'vpntowan'
option src 'vpn'
option dest 'wan'
config forwarding 'vpntolan'
option src 'vpn'
option dest 'lan'
config forwarding 'lantovpn'
option src 'lan'
option dest 'vpn'
config include 'v2ray_server'
option type 'script'
option path '/usr/share/v2ray_server/firewall.include'
option reload '1'
config include 'trojan_server'
option type 'script'
option path '/usr/share/trojan_server/firewall.include'
option reload '1'
config include 'ss_rules'
option path '/etc/firewall.ss-rules'
option reload '1'
config rule
option target 'ACCEPT'
option src 'wan'
option proto 'udp'
option dest_port ''
option name 'Wireguard'
config include 'shadowsocksr'
option type 'script'
option path '/var/etc/shadowsocksr.include'
option reload '1'
config rule
option src 'wan'
option proto 'tcp udp'
option name 'UDP'
option dest '*'
option target 'DROP'
option extra '-m geoip ! --src-cc BD -j DROP'
config include 'AdGuardHome'
option type 'script'
option path '/usr/share/AdGuardHome/firewall.start'
option reload '1'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
iptables -t nat -A PREROUTING -p udp --dport 53 -j REDIRECT --to-ports 9550
iptables -t nat -A PREROUTING -p tcp --dport 53 -j REDIRECT --to-ports 9550
[ -n "$(command -v ip6tables)" ] && ip6tables -t nat -A PREROUTING -p udp --dport 53 -j REDIRECT --to-ports 9550
[ -n "$(command -v ip6tables)" ] && ip6tables -t nat -A PREROUTING -p tcp --dport 53 -j REDIRECT --to-ports 9550
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o br-lan -j MASQUERADE
iptables -A INPUT -m geoip ! --src-cc BD -j DROP
iptables -A INPUT -m geoip -p tcp –dport 25 ! –src-cc BD -j DROP
iptables -A FORWARD -m geoip --src-cc BD -j DROP
iptables -I INPUT -m geoip --src-cc BD -j DROP# Generated by iptables-save v1.8.7 on Wed Mar 2 22:17:03 2022
*nat
:PREROUTING ACCEPT [50892:21377065]
:INPUT ACCEPT [30095:2152861]
:OUTPUT ACCEPT [34681:2155810]
:POSTROUTING ACCEPT [22878:1394428]
:SS_SPEC_WAN_AC - [0:0]
:SS_SPEC_WAN_FW - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_vpn_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_vpn_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_vpn_postrouting - [0:0]
:zone_vpn_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[10945:717831] -A PREROUTING -i br-lan -p tcp -m comment --comment _SS_SPEC_RULE_ -j SS_SPEC_WAN_AC
[16080:1119267] -A PREROUTING -p udp -m udp --dport 53 -j REDIRECT --to-ports 5350
[28:1460] -A PREROUTING -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 5350
[0:0] -A PREROUTING -p udp -m comment --comment DNSMASQ -m udp --dport 53 -j REDIRECT --to-ports 53
[53116:23025773] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[24227:18005014] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[9957:2063569] -A PREROUTING -i pppoe-wan6 -m comment --comment "!fw3" -j zone_wan_prerouting
[17968:2797166] -A PREROUTING -i wg0 -m comment --comment "!fw3" -j zone_vpn_prerouting
[0:0] -A PREROUTING -d 192.168.31.1/32 -p udp -m udp --dport 53 -j REDIRECT --to-ports 5350
[12804:769680] -A OUTPUT -p tcp -m comment --comment _SS_SPEC_RULE_ -j SS_SPEC_WAN_AC
[529:29173] -A POSTROUTING -s 192.168.10.0/24 -o br-lan -j MASQUERADE
[51759:6324540] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[2332:1677532] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[26549:3252580] -A POSTROUTING -o pppoe-wan6 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o wg0 -m comment --comment "!fw3" -j zone_vpn_postrouting
[0:0] -A SS_SPEC_WAN_AC -m set --match-set whitelist dst -j RETURN
[44:2640] -A SS_SPEC_WAN_AC -m set --match-set blacklist dst -j SS_SPEC_WAN_FW
[0:0] -A SS_SPEC_WAN_AC -m set --match-set bplan src -j RETURN
[0:0] -A SS_SPEC_WAN_AC -m set --match-set fplan src -j SS_SPEC_WAN_FW
[11073:664380] -A SS_SPEC_WAN_AC -d -p tcp -m tcp ! --dport 53 -j RETURN
[12632:820491] -A SS_SPEC_WAN_AC -j SS_SPEC_WAN_FW
[0:0] -A SS_SPEC_WAN_FW -d 0.0.0.0/8 -j RETURN
[13:780] -A SS_SPEC_WAN_FW -d 10.0.0.0/8 -j RETURN
[34:2040] -A SS_SPEC_WAN_FW -d 127.0.0.0/8 -j RETURN
[0:0] -A SS_SPEC_WAN_FW -d 169.254.0.0/16 -j RETURN
[0:0] -A SS_SPEC_WAN_FW -d 172.16.0.0/12 -j RETURN
[772:47712] -A SS_SPEC_WAN_FW -d 192.168.0.0/16 -j RETURN
[0:0] -A SS_SPEC_WAN_FW -d 224.0.0.0/4 -j RETURN
[0:0] -A SS_SPEC_WAN_FW -d 240.0.0.0/4 -j RETURN
[11857:772599] -A SS_SPEC_WAN_FW -p tcp -j REDIRECT --to-ports 1234
[2332:1677532] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[2332:1677532] -A zone_lan_postrouting -m comment --comment "!fw3" -j FULLCONENAT
[24227:18005014] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[24227:18005014] -A zone_lan_prerouting -m comment --comment "!fw3" -j FULLCONENAT
[0:0] -A zone_vpn_postrouting -m comment --comment "!fw3: Custom vpn postrouting rule chain" -j postrouting_vpn_rule
[0:0] -A zone_vpn_postrouting -m comment --comment "!fw3" -j FULLCONENAT
[17968:2797166] -A zone_vpn_prerouting -m comment --comment "!fw3: Custom vpn prerouting rule chain" -j prerouting_vpn_rule
[17968:2797166] -A zone_vpn_prerouting -m comment --comment "!fw3" -j FULLCONENAT
[26549:3252580] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[26549:3252580] -A zone_wan_postrouting -m comment --comment "!fw3" -j FULLCONENAT
[9957:2063569] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[9957:2063569] -A zone_wan_prerouting -m comment --comment "!fw3" -j FULLCONENAT
COMMIT
# Completed on Wed Mar 2 22:17:03 2022
# Generated by iptables-save v1.8.7 on Wed Mar 2 22:17:03 2022
*raw
:PREROUTING ACCEPT [10380307:8162894582]
:OUTPUT ACCEPT [7007189:8480714967]
COMMIT
# Completed on Wed Mar 2 22:17:03 2022
# Generated by iptables-save v1.8.7 on Wed Mar 2 22:17:03 2022
*mangle
:PREROUTING ACCEPT [10258251:8081959707]
:INPUT ACCEPT [10124903:8051176856]
:FORWARD ACCEPT [116997:29228332]
:OUTPUT ACCEPT [7007189:8480715782]
:POSTROUTING ACCEPT [7118821:8509673164]
:RRDIPT_FORWARD - [0:0]
:RRDIPT_INPUT - [0:0]
:RRDIPT_OUTPUT - [0:0]
:SS_SPEC_TPROXY - [0:0]
[168260:97308718] -A PREROUTING -i br-lan -p udp -m comment --comment _SS_SPEC_RULE_ -j SS_SPEC_TPROXY
[10124905:8051177060] -A INPUT -j RRDIPT_INPUT
[116998:29228372] -A FORWARD -j RRDIPT_FORWARD
[0:0] -A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[6807:354380] -A FORWARD -o pppoe-wan6 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[6583:342148] -A FORWARD -i pppoe-wan6 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[7007192:8480715994] -A OUTPUT -j RRDIPT_OUTPUT
[136:9594] -A RRDIPT_FORWARD -s 192.168.31.102/32 -j RETURN
[104:4864] -A RRDIPT_FORWARD -d 192.168.31.102/32 -j RETURN
[1997:105340] -A RRDIPT_FORWARD -s 192.168.31.111/32 -j RETURN
[41:2366] -A RRDIPT_FORWARD -d 192.168.31.111/32 -j RETURN
[0:0] -A RRDIPT_FORWARD -s 192.168.31.240/32 -j RETURN
[0:0] -A RRDIPT_FORWARD -d 192.168.31.240/32 -j RETURN
[7:364] -A RRDIPT_FORWARD -s 192.168.31.170/32 -j RETURN
[0:0] -A RRDIPT_FORWARD -d 192.168.31.170/32 -j RETURN
[321:99495] -A RRDIPT_FORWARD -s 192.168.31.171/32 -j RETURN
[25:34200] -A RRDIPT_FORWARD -d 192.168.31.171/32 -j RETURN
[1108:72639] -A RRDIPT_FORWARD -s 192.168.31.244/32 -j RETURN
[731:35253] -A RRDIPT_FORWARD -d 192.168.31.244/32 -j RETURN
[937:75461] -A RRDIPT_FORWARD -s 192.168.31.180/32 -j RETURN
[71:5920] -A RRDIPT_FORWARD -d 192.168.31.180/32 -j RETURN
[29613:14623756] -A RRDIPT_FORWARD -s 192.168.31.238/32 -j RETURN
[16381:6519814] -A RRDIPT_FORWARD -d 192.168.31.238/32 -j RETURN
[1523:80709] -A RRDIPT_FORWARD -s 192.168.31.239/32 -j RETURN
[628:25156] -A RRDIPT_FORWARD -d 192.168.31.239/32 -j RETURN
[1158:192228] -A RRDIPT_INPUT -i eth0 -j RETURN
[0:0] -A RRDIPT_INPUT -i pppoe-wan -j RETURN
[0:0] -A RRDIPT_OUTPUT -o eth0 -j RETURN
[0:0] -A RRDIPT_OUTPUT -o pppoe-wan -j RETURN
[10275:699859] -A SS_SPEC_TPROXY -p udp -m udp --dport 53 -j RETURN
[0:0] -A SS_SPEC_TPROXY -d 0.0.0.0/8 -p udp -j RETURN
[24:3168] -A SS_SPEC_TPROXY -d 10.0.0.0/8 -p udp -j RETURN
[0:0] -A SS_SPEC_TPROXY -d 127.0.0.0/8 -p udp -j RETURN
[0:0] -A SS_SPEC_TPROXY -d 169.254.0.0/16 -p udp -j RETURN
[0:0] -A SS_SPEC_TPROXY -d 172.16.0.0/12 -p udp -j RETURN
[28961:14644084] -A SS_SPEC_TPROXY -d 192.168.0.0/16 -p udp -j RETURN
[6916:1013378] -A SS_SPEC_TPROXY -d 224.0.0.0/4 -p udp -j RETURN
[33:13690] -A SS_SPEC_TPROXY -d 240.0.0.0/4 -p udp -j RETURN
[0:0] -A SS_SPEC_TPROXY -d -p udp -m udp ! --dport 53 -j RETURN
[0:0] -A SS_SPEC_TPROXY -p udp -m set --match-set bplan src -j RETURN
[0:0] -A SS_SPEC_TPROXY -p udp -m set --match-set fplan src -j TPROXY --on-port 1234 --on-ip 0.0.0.0 --tproxy-mark 0x1/0x1
[122051:80934539] -A SS_SPEC_TPROXY -p udp -j TPROXY --on-port 1234 --on-ip 0.0.0.0 --tproxy-mark 0x1/0x1
COMMIT
# Completed on Wed Mar 2 22:17:03 2022
# Generated by iptables-save v1.8.7 on Wed Mar 2 22:17:03 2022
*filter
:INPUT ACCEPT [1158:192228]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_vpn_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_vpn_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_vpn_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_vpn_dest_ACCEPT - [0:0]
:zone_vpn_forward - [0:0]
:zone_vpn_input - [0:0]
:zone_vpn_output - [0:0]
:zone_vpn_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[257767:73453004] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[9867139:7977724108] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[9826957:7975020970] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[2244:91909] -A INPUT -m conntrack --ctstate INVALID -m comment --comment "!fw3" -j DROP
[15665:858206] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[22001:1505282] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[0:0] -A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
[8773:478834] -A INPUT -i pppoe-wan6 -m comment --comment "!fw3" -j zone_wan_input
[6006:434885] -A INPUT -i wg0 -m comment --comment "!fw3" -j zone_vpn_input
[116999:29228412] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[98829:24730046] -A FORWARD -m comment --comment "!fw3: Traffic offloading" -m conntrack --ctstate RELATED,ESTABLISHED -j FLOWOFFLOAD --hw
[98829:24730046] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[5496:311465] -A FORWARD -m conntrack --ctstate INVALID -m comment --comment "!fw3" -j DROP
[269:32548] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
[2215:1647614] -A FORWARD -i pppoe-wan6 -m comment --comment "!fw3" -j zone_wan_forward
[10190:2506739] -A FORWARD -i wg0 -m comment --comment "!fw3" -j zone_vpn_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[163871:43948591] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[6843335:8436775268] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[6821014:8434402077] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[63:5453] -A OUTPUT -m conntrack --ctstate INVALID -m comment --comment "!fw3" -j DROP
[228:58666] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
[22030:2309072] -A OUTPUT -o pppoe-wan6 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o wg0 -m comment --comment "!fw3" -j zone_vpn_output
[5426:248450] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[263:31315] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[15665:858206] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[0:0] -A zone_lan_dest_ACCEPT -o br-lan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[789:89503] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[269:32548] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[269:32548] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to vpn forwarding policy" -j zone_vpn_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[22001:1505282] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[21127:1411537] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[874:93745] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[228:58666] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[228:58666] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[874:93745] -A zone_lan_src_ACCEPT -i br-lan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_vpn_dest_ACCEPT -o wg0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_vpn_dest_ACCEPT -o wg0 -m comment --comment "!fw3" -j ACCEPT
[10190:2506739] -A zone_vpn_forward -m comment --comment "!fw3: Custom vpn forwarding rule chain" -j forwarding_vpn_rule
[10190:2506739] -A zone_vpn_forward -m comment --comment "!fw3: Zone vpn to wan forwarding policy" -j zone_wan_dest_ACCEPT
[561:30837] -A zone_vpn_forward -m comment --comment "!fw3: Zone vpn to lan forwarding policy" -j zone_lan_dest_ACCEPT
[0:0] -A zone_vpn_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_vpn_forward -m comment --comment "!fw3" -j zone_vpn_dest_ACCEPT
[6006:434885] -A zone_vpn_input -m comment --comment "!fw3: Custom vpn input rule chain" -j input_vpn_rule
[5999:434521] -A zone_vpn_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[7:364] -A zone_vpn_input -m comment --comment "!fw3" -j zone_vpn_src_ACCEPT
[0:0] -A zone_vpn_output -m comment --comment "!fw3: Custom vpn output rule chain" -j output_vpn_rule
[0:0] -A zone_vpn_output -m comment --comment "!fw3" -j zone_vpn_dest_ACCEPT
[7:364] -A zone_vpn_src_ACCEPT -i wg0 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o pppoe-wan6 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[31928:4817522] -A zone_wan_dest_ACCEPT -o pppoe-wan6 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan6 -m comment --comment "!fw3" -j reject
[2215:1647614] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[2215:1647614] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[8773:478834] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[2017:134130] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[4:704] -A zone_wan_input -p udp -m udp --dport 23367 -m comment --comment "!fw3: Wireguard" -j ACCEPT
[31:1312] -A zone_wan_input -p tcp -m tcp --dport 3389 -m comment --comment "!fw3: BLOCK" -j DROP
[1:44] -A zone_wan_input -p udp -m udp --dport 3389 -m comment --comment "!fw3: BLOCK" -j DROP
[1031:62879] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[5689:279765] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[22030:2309072] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[22030:2309072] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
[5689:279765] -A zone_wan_src_REJECT -i pppoe-wan6 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Wed Mar 2 22:17:03 2022
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
8: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.31.1/24 brd 192.168.31.255 scope global br-lan
valid_lft forever preferred_lft forever
10: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
inet 192.168.10.0/24 brd 192.168.10.255 scope global wg0
valid_lft forever preferred_lft forever
15: pppoe-wan: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1480 qdisc fq_codel state UNKNOWN group default qlen 3
inet peer scope global pppoe-wan
valid_lft forever preferred_lft forever
16: pppoe-wan6: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1480 qdisc fq_codel state UNKNOWN group default qlen 3
inet peer scope global pppoe-wan6
valid_lft forever preferred_lft forever
default via 59.153. dev pppoe-wan6 proto static
59.153. dev pppoe-wan proto kernel scope link src
59.153. dev pppoe-wan6 proto kernel scope link src
192.168.10.0/24 dev wg0 proto kernel scope link src
192.168.10.2 dev wg0 proto static scope link
192.168.10.4 dev wg0 proto static scope link
192.168.10.5 dev wg0 proto static scope link
192.168.10.6 dev wg0 proto static scope link
192.168.10.7 dev wg0 proto static scope link
192.168.31.0/24 dev br-lan proto kernel scope link src 192.168.31.1
local dev pppoe-wan table local proto kernel scope host src
local dev pppoe-wan6 table local proto kernel scope host src
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
local 192.168.10.0 dev wg0 table local proto kernel scope host src 192.168.10.0
broadcast 192.168.10.0 dev wg0 table local proto kernel scope link src 192.168.10.0
broadcast 192.168.10.255 dev wg0 table local proto kernel scope link src 192.168.10.0
broadcast 192.168.31.0 dev br-lan table local proto kernel scope link src 192.168.31.1
local 192.168.31.1 dev br-lan table local proto kernel scope host src 192.168.31.1
broadcast 192.168.31.255 dev br-lan table local proto kernel scope link src 192.168.31.1
0: from all lookup local
32765: from all fwmark 0x1/0x1 lookup 100
32766: from all lookup main
32767: from all lookup default
lrwxrwxrwx 1 root root 16 Jan 30 12:59 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 32 Mar 2 02:39 /tmp/resolv.conf
lrwxrwxrwx 1 root root 35 Mar 1 20:00 /tmp/resolv.conf.auto -> /tmp/resolv.conf.d/resolv.conf.auto
-rw-r--r-- 1 root root 173 Mar 1 20:01 /tmp/resolv.conf.d/resolv.conf.auto
-rw-r--r-- 1 root root 50 Mar 1 20:01 /tmp/resolv.conf.ppp
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 173 Mar 1 20:01 resolv.conf.auto
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.auto <==
# Interface lan
nameserver 192.168.31.1
# Interface wan
nameserver
nameserver
# Interface wan6
nameserver
nameserver
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error
==> /tmp/resolv.conf.ppp <==
nameserver
nameserver
==> /tmp/resolv.conf.d/resolv.conf.auto <==
# Interface lan
nameserver 192.168.31.1
# Interface wan
nameserver
nameserver
# Interface wan6
nameserver
nameserver