Set-up:
- 1x ISP Modem (bridged; 192.168.1.0/24)
- 2x WRT1900ACS with 18.06.4 (One router/AP, and one AP; 192.168.2.0/24)
- 1x RPi 4b (192.168.2.3; Primary Pi-Hole, with Unbound - recursive w/ DNSSEC)
- 1x RPi 3b+ (192.168.2.4; Secondary Pi-Hole, with Unbound - recursive w/ DNSSEC)
Issue:
At the very least, I want to block DNS queries from br-lan on both IPv4 and IPv6. IPv6 is currently running SLAAC with DHCPv6 providing DNS (RA = Server; DHCPv6 = Server/Stateless). Ideally, I'd like to be able to run a redirecting ruleset similar to what I used to run prior to my ISP offering IPv6:
# Let the RPi's be able to access DNS (UDP)
iptables -t nat -A PREROUTING -s 192.168.2.3 -i br-lan -p udp --dport 53 -j ACCEPT
iptables -t nat -A PREROUTING -s 192.168.2.4 -i br-lan -p udp --dport 53 -j ACCEPT
# If the packet is DNS and the destination is not in LAN, redirect to Primary RPi (UDP)
iptables -t nat -A PREROUTING -s 192.168.2.0/24 ! -d 192.168.2.0/24 -i br-lan -p udp --dport 53 -j DNAT --to 192.168.2.3:53
# Let the RPi's be able to access DNS (TCP)
iptables -t nat -A PREROUTING -s 192.168.2.3 -i br-lan -p tcp --dport 53 -j ACCEPT
iptables -t nat -A PREROUTING -s 192.168.2.4 -i br-lan -p tcp --dport 53 -j ACCEPT
# If the packet is DNS and the destination is not in LAN, redirect to Primary RPi (TCP)
iptables -t nat -A PREROUTING -s 192.168.2.0/24 ! -d 192.168.2.0/24 -i br-lan -p tcp --dport 53 -j DNAT --to 192.168.2.3:53
# Prevent client issue
iptables -t nat -A POSTROUTING -j MASQUERADE
What I have tried:
- Copying the ruleset above for IPv6 aided by
kmod-ipt-nat6 - https://openwrt.org/docs/guide-user/services/dns/intercept - stops Unbound on both Pi's from being able to resolve queries
- Redirect All Outbound DNS Traffic to Internal IP - IPv4 only
- https://www.reddit.com/r/openwrt/comments/8lgcrr/captive_dns_with_openwrt_ipv6_and_netfilter/
- https://www.reddit.com/r/openwrt/comments/8updbe/two_questions_block_all_dns_except_my_service/
-
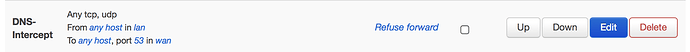
(Referring to the image): Unbound can't resolve anything anymore. Tried to remediate with
iptables -t nat -A PREROUTING -s 192.168.2.3 -i br-lan -p udp --dport 53 -j ACCEPTandip6tables -t nat -A PREROUTING -s fd0f:3fd1:8002::3 -i br-lan -p udp --dport 53 -j ACCEPT
Addendum:
At this point I'd be happy even if anyone could assist me in a ruleset to set up a port 53 block to anything heading to WAN (while punching a hole for the 2x RPi's).