Should he rule for my guest VLAN and DNS be under Port Forwards or Traffic Rules?
Right now, both are under the Traffic Rules and it seems to work but not sure if they need to under Port Forwards.
You do not need the rules under forward if it for the router itself.
Post the contents of your /etc/config/firewall file (paste it into a < \ > code block)
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option network 'VLAN20'
option forward 'REJECT'
option name 'VLAN20'
option output 'ACCEPT'
option input 'REJECT'
config forwarding
option dest 'wan'
option src 'VLAN20'
config forwarding
option dest 'VLAN20'
option src 'lan'
config redirect
option dest_port '51820'
option src 'wan'
option name 'Wireguard-VPN'
option src_dport '51820'
option target 'DNAT'
option dest_ip '192.168.4.8'
option dest 'lan'
list proto 'udp'
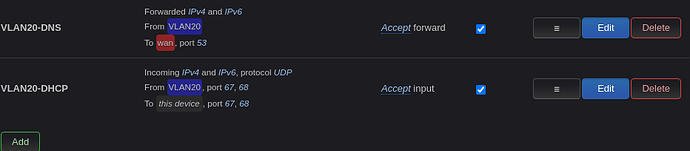
config rule
option dest_port '53'
option src 'VLAN20'
option name 'VLAN20-DNS'
option dest 'wan'
option target 'ACCEPT'
config rule
option src_port '67 68'
option src 'VLAN20'
option name 'VLAN20-DHCP'
option target 'ACCEPT'
option dest_port '67 68'
list proto 'udp'
If the DNS is the router, there is no forwarding involved...
A rule can allow (or deny) traffic, which might be ingress to the router, egress from the router, or traversing the router.
A redirect (or port forward) is basically a DNAT, so it rewrites the destination address (and optionally the port).
The rule for port 53 is not necessary, you have already a forwarding from VLAN20 -> wan.
If you want to use the OpenWrt as nameserver, then you should remove the option dest 'wan' from that rule. It also depends on the dhcp settings you have for the VLAN20 interface. By default the OpenWrt is advertised as nameserver and with this configuration your guests will be blocked.
The other rule is almost correct, src_port is only 68 and dest_port only 67
Made changes based on your suggestion.
So far, all is good.
onfig rule
option dest_port '53'
option src 'VLAN20'
option name 'VLAN20-DNS'
option target 'ACCEPT'
config rule
option src 'VLAN20'
option name 'VLAN20-DHCP'
option target 'ACCEPT'
list proto 'udp'
option src_port '68'
option dest_port '67'
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.