4lexO
April 17, 2019, 12:16pm
1
Hello,different thread .
Here is the setup of the project :
Context :
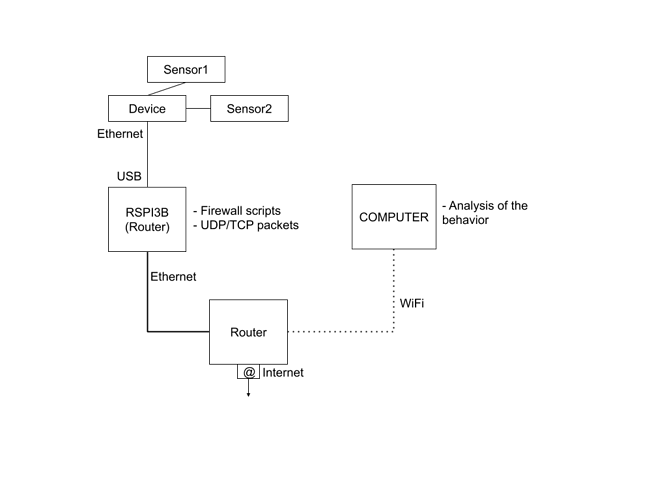
The device is used to relay the data of different sensors. The data are unidirectionally transmitted to the device. No data are going from the device to the sensors. To do this, the device communicates with different domains through different ports (443 TCP(HTTPS), 123 UDP(NTP), 53 UDP(DNS). Sometimes in a different network, the configuration of this network doesn't allow a communication and it's difficult to determine it.
Objectif :
Problem :Firewall - Custom rules tab to see if the device can still communicate. I tried different combinations and flushed before each try the different rules.
A
iptables -I FORWARD -s 192.168.179.194 -p udp --dport 123 -j DROP
No effect, still working.
B
iptables -I FORWARD -s 192.168.179.194 -p udp --dport 53 -j DROP
No effect, still working.
C
iptables -I FORWARD -s 192.168.179.194 -p tcp --dport 443 -j DROP
The device stop working.
Questions
1 - Why only the C rule make it not working ?tool to analyze the port's status inside the device, it tells the ports are enabled even I blocked them with IPTABLES, why ?
Thank you,
mikma
April 17, 2019, 12:35pm
2
1). The FORWARD chain isn't traversed in case the packet is addressed to the firewall itself. In that case you need to use the INPUT chain.
4). You could use the ipset option supported by dnsmasq-full . That could insert the IP addresses resolved by dnsmasq in an ipset which you can use in iptables rules.
1 Like
4lexO
April 17, 2019, 1:38pm
3
I used the following commands :
iptables -I INPUT -s 192.168.179.194 -p udp --dport 123 -j DROP
iptables -I INPUT -s 192.168.179.194 -p udp --dport 53 -j DROP
I shut down the device then apply the firewall and reconnect the device still working
jeff
April 17, 2019, 1:49pm
4
To understand which rules do what, you'll need to look at the entire set of rules. If, for example, a rule "early" in the set of rules accepts a packet (such as "allow LAN hosts to access the Internet"), a "later" rule to block things never gets checked.
You also should understand that TCP traffic is always two-way. While UDP can "throw a packet" at another server, TCP always involves ACKnowledge packets flowing back. This is typically handled by connection tracking ("state established" or similar) in the firewall for home users.
Firewalls like iptables work on IP addresses (and potentially Ethernet addresses), but not domain names. You can block a set/range of IP addresses, but the concept of *.example.com doesn't exist at the packet level. Even blocking IP addresses, you're not blocking *.example.com as, especially today in commercial operations and cloud-based servers, more than one host name is served by a single IP address.
3 Likes
trendy
April 17, 2019, 2:10pm
5
Please post here the output of the following commands, you can paste in multiple lines if you keep the backslash at the end of each line.
cat /etc/config/network; cat /etc/config/firewall; cat /etc/config/dhcp;\
echo "### ADDRv4 ###";ip -4 addr; echo "### ROUTEv4 ###"; ip -4 ro; echo "### RULEv4 ###";ip -4 ru;\
echo "### FILTERv4 ###"; iptables -L -vn; echo "### NATv4 ###"; iptables -t nat -L -vn; echo "### MANGLEv4 ###"; iptables -t mangle -L -vn
4lexO
April 17, 2019, 2:15pm
6
@jeff Thank you for the precision, it helped me understanding it better
root@OpenWrt:~# cat /etc/config/network; cat /etc/config/firewall; cat
/etc/config/dhcp;\
> echo "### ADDRv4 ###";ip -4 addr; echo "### ROUTEv4 ###"; ip -4 ro; e
cho "### RULEv4 ###";ip -4 ru;\
> echo "### FILTERv4 ###"; iptables -L -vn; echo "### NATv4 ###"; iptab
les -t nat -L -vn; echo "### MANGLEv4 ###"; iptables -t mangle -L -vn
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd4d:0405:966a::/48'
config interface 'lan'
option ifname 'eth1'
option proto 'static'
option ipaddr '192.168.179.108'
option netmask '255.255.255.0'
option broadcast '192.168.179.255'
config interface 'WAN'
option proto 'dhcp'
option ifname 'eth0'
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'ACCEPT'
option name 'WAN'
option network 'WAN'
config rule
option name 'Allow-DHCP-Renew'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
option src 'WAN'
config rule
option name 'Allow-Ping'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-IGMP'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-DHCPv6'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-MLD'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-ICMPv6-Input'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-ICMPv6-Forward'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-IPSec-ESP'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-ISAKMP'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option src 'WAN'
config include
option path '/etc/firewall.user'
config forwarding
option dest 'lan'
option src 'WAN'
config forwarding
option dest 'WAN'
option src 'lan'
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
### ADDRv4 ###
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP qlen 1000
inet 192.168.178.108/24 brd 192.168.178.255 scope global eth0
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP qlen 1000
inet 192.168.179.108/24 brd 192.168.179.255 scope global eth1
valid_lft forever preferred_lft forever
### ROUTEv4 ###
default via 192.168.178.1 dev eth0 src 192.168.178.108
192.168.178.0/24 dev eth0 scope link src 192.168.178.108
192.168.179.0/24 dev eth1 scope link src 192.168.179.108
### RULEv4 ###
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
### FILTERv4 ###
Chain INPUT (policy ACCEPT 5261 packets, 328K bytes)
pkts bytes target prot opt in out source destination
53 3875 DROP udp -- * * 192.168.179.194 0.0.0.0/0 udp dpt:53
0 0 DROP udp -- * * 192.168.179.194 0.0.0.0/0 udp dpt:123
Chain FORWARD (policy ACCEPT 19764 packets, 4777K bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 6063 packets, 6058K bytes)
pkts bytes target prot opt in out source destination
Chain forwarding_WAN_rule (0 references)
pkts bytes target prot opt in out source destination
Chain forwarding_lan_rule (0 references)
pkts bytes target prot opt in out source destination
Chain forwarding_rule (0 references)
pkts bytes target prot opt in out source destination
Chain input_WAN_rule (0 references)
pkts bytes target prot opt in out source destination
Chain input_lan_rule (0 references)
pkts bytes target prot opt in out source destination
Chain input_rule (0 references)
pkts bytes target prot opt in out source destination
Chain output_WAN_rule (0 references)
pkts bytes target prot opt in out source destination
Chain output_lan_rule (0 references)
pkts bytes target prot opt in out source destination
Chain output_rule (0 references)
pkts bytes target prot opt in out source destination
Chain reject (0 references)
pkts bytes target prot opt in out source destination
Chain syn_flood (0 references)
pkts bytes target prot opt in out source destination
Chain zone_WAN_dest_ACCEPT (0 references)
pkts bytes target prot opt in out source destination
Chain zone_WAN_forward (0 references)
pkts bytes target prot opt in out source destination
Chain zone_WAN_input (0 references)
pkts bytes target prot opt in out source destination
Chain zone_WAN_output (0 references)
pkts bytes target prot opt in out source destination
Chain zone_WAN_src_ACCEPT (0 references)
pkts bytes target prot opt in out source destination
Chain zone_lan_dest_ACCEPT (0 references)
pkts bytes target prot opt in out source destination
Chain zone_lan_forward (0 references)
pkts bytes target prot opt in out source destination
Chain zone_lan_input (0 references)
pkts bytes target prot opt in out source destination
Chain zone_lan_output (0 references)
pkts bytes target prot opt in out source destination
Chain zone_lan_src_ACCEPT (0 references)
pkts bytes target prot opt in out source destination
### NATv4 ###
Chain PREROUTING (policy ACCEPT 315 packets, 25835 bytes)
pkts bytes target prot opt in out source destination
315 25835 prerouting_rule all -- * * 0.0.0.0/0 0.0.0.0/0 /* !fw3: Custom prerouting rule chain */
278 20172 zone_lan_prerouting all -- eth1 * 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
37 5663 zone_WAN_prerouting all -- eth0 * 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
Chain INPUT (policy ACCEPT 38 packets, 5991 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 109 packets, 8456 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 3 packets, 482 bytes)
pkts bytes target prot opt in out source destination
316 21755 postrouting_rule all -- * * 0.0.0.0/0 0.0.0.0/0 /* !fw3: Custom postrouting rule chain */
1 334 zone_lan_postrouting all -- * eth1 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
313 21273 zone_WAN_postrouting all -- * eth0 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
Chain postrouting_WAN_rule (1 references)
pkts bytes target prot opt in out source destination
Chain postrouting_lan_rule (1 references)
pkts bytes target prot opt in out source destination
Chain postrouting_rule (1 references)
pkts bytes target prot opt in out source destination
Chain prerouting_WAN_rule (1 references)
pkts bytes target prot opt in out source destination
Chain prerouting_lan_rule (1 references)
pkts bytes target prot opt in out source destination
Chain prerouting_rule (1 references)
pkts bytes target prot opt in out source destination
Chain zone_WAN_postrouting (1 references)
pkts bytes target prot opt in out source destination
313 21273 postrouting_WAN_rule all -- * * 0.0.0.0/0 0.0.0.0/0 /* !fw3: Custom WAN postrouting rule chain */
313 21273 MASQUERADE all -- * * 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
Chain zone_WAN_prerouting (1 references)
pkts bytes target prot opt in out source destination
37 5663 prerouting_WAN_rule all -- * * 0.0.0.0/0 0.0.0.0/0 /* !fw3: Custom WAN prerouting rule chain */
Chain zone_lan_postrouting (1 references)
pkts bytes target prot opt in out source destination
1 334 postrouting_lan_rule all -- * * 0.0.0.0/0 0.0.0.0/0 /* !fw3: Custom lan postrouting rule chain */
Chain zone_lan_prerouting (1 references)
pkts bytes target prot opt in out source destination
278 20172 prerouting_lan_rule all -- * * 0.0.0.0/0 0.0.0.0/0 /* !fw3: Custom lan prerouting rule chain */
### MANGLEv4 ###
Chain PREROUTING (policy ACCEPT 25115 packets, 5113K bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 5334 packets, 333K bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 19764 packets, 4777K bytes)
pkts bytes target prot opt in out source destination
106 6296 TCPMSS tcp -- * eth0 0.0.0.0/0 0.0.0.0/0 tcp flags:0x06/0x02 /* !fw3: Zone WAN MTU fixing */ TCPMSS clamp to PMTU
Chain OUTPUT (policy ACCEPT 6090 packets, 6071K bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 25854 packets, 11M bytes)
pkts bytes target prot opt in out source destination
trendy
April 17, 2019, 2:44pm
7
Communication from the device to the Raspberry for DNS and NTP is blocked.
53 3875 DROP udp -- * * 192.168.179.194 0.0.0.0/0 udp dpt:53
0 0 DROP udp -- * * 192.168.179.194 0.0.0.0/0 udp dpt:123
There are some dropped packets for DNS, for NTP there was nothing captured.
Other than that there is no other rule in INPUT or FORWARD and since the policy is ACCEPT to everything, it will pass.
4lexO
April 17, 2019, 2:50pm
8
But why should I also block OUTPUT and FORWARD ?
trendy
April 17, 2019, 2:58pm
9
It all depends from which are the flows.
4lexO
April 17, 2019, 2:59pm
10
Looks like I should only block INPUT and OUTPUT using the device's IP ?
trendy
April 17, 2019, 3:00pm
11
In this case device = openwrt running the firewall.
jeff
April 17, 2019, 3:32pm
12
Here's a link to a diagram of how the Linux firewall filters packets that I've found useful. It covers input, output, forward, pre-routing, post-routing, and the like:
https://wiki.nftables.org/wiki-nftables/index.php/Netfilter_hooks
2 Likes
4lexO
April 18, 2019, 10:24am
13
I think I also have another issue about the order of the rules.
root@OpenWrt:~# iptables --list-rules
-P INPUT ACCEPT
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
-N forwarding_WAN_rule
-N forwarding_lan_rule
-N forwarding_rule
-N input_WAN_rule
-N input_lan_rule
-N input_rule
-N output_WAN_rule
-N output_lan_rule
-N output_rule
-N reject
-N syn_flood
-N zone_WAN_dest_ACCEPT
-N zone_WAN_forward
-N zone_WAN_input
-N zone_WAN_output
-N zone_WAN_src_ACCEPT
-N zone_lan_dest_ACCEPT
-N zone_lan_forward
-N zone_lan_input
-N zone_lan_output
-N zone_lan_src_ACCEPT
-A INPUT -s 192.168.179.194/32 -p udp -m udp --dport 123 -j DROP
The last rule won't be crossed right ?
Local
process
^ | .-----------.
.-----------. | | | Routing |
| |-----> input / \---> | Decision |----> output \
--> prerouting --->| Routing | .-----------. \
| Decision | --> postrouting
| | /
| |---------------> forward ---------------------------
.-----------.
The LOCAL PROCESS is the device 192.168.178.194 ?
Test it.
Use log instead of DROP and you can answer any question you can think of.... with the appropriate test.
Your policy is ACCEPT and all other chains are empty / unused.
Nothing to do with order. It's the CHAIN/TARGET... the USE of INPUT over FORWARD if on the LOCAL DEVICE. So you can MATCH.
Is your local process sending packets to itself?
-s = SOURCE
Did you mean -d = DESTINATION
1 Like
trendy
April 18, 2019, 11:22am
15
What does crossed mean? It's the only rule you have there. If a packet comes from device .194 destined to the Raspberry ntp port, it will be dropped. Other than that everything else will be accepted, as the policy is to ACCEPT.And what does -m udp mean there?
Local Process is the Raspberry.
4lexO
April 18, 2019, 12:09pm
16
Using this command :
iptables -A INPUT -s 0/0 -i eth0 -d 192.168.178.194 -p udp --sport 123 -j logdrop
What means the commands to me :
INPUT means a packet come from the outside of the network and destined to the network. -A means it adds this rule at the end of the rules list. The source -s of this packet is any 0/0 and it comes in -i on eth0 (WAN interface). The destination -d of this packet is the 192.168.178.194. The port -p type udp is from the source --sport and the port is123. The target -j is to drop it with a log logdrop.
Is this interpretation correct ?
1 Like
iptables -A INPUT
-i eth0
-p udp
-s 0/0
-d 192.168.178.194
--dport 123
-j logdrop
Note: The -i and -d options are generally not used together unless paranoid.
i.e.
iptables -A INPUT
-p udp
-d 192.168.178.194
--dport 123
-j logdrop
Is good.... -s 0/0 is implied. Maybe it is -s 123 .... my brain is a bit mushy now.... low ports usually are on dest ( service ) side tho'
1 Like
trendy
April 18, 2019, 12:21pm
18
With -d option for the INPUT you need to use 192.168.179.108 as destination.
2 Likes
4lexO
April 18, 2019, 12:21pm
19
root@OpenWrt:~# iptables -A INPUT -p udp -d 192.168.178.194 --dport 123
-j logdrop
iptables v1.6.2: Couldn't load target `logdrop':No such file or directory
Try `iptables -h' or 'iptables --help' for more information.
logdrop apparently not implemented ?
iptables -N logdrop
( use all -N is the "CHAIN"
Or you could just do this
iptables -A INPUT -p udp -d 192.168.178.194 --dport 123 -j LOG
iptables -A INPUT -p udp -d 192.168.178.194 --dport 123 -j DROP
and a confession..... I actually can't understand the openwrt firewall most of the time.....
doing what you are.... and breaking it down.... reading the stuff jeff showed you..... is the best... and for me the ONLY way i can understand.