Hey there!
I was finally able to set up NAT6 on my network, and all the devices that are local to the router are able to connect to the internet successfully using either IPv4 or IPv6, though I'm still getting stuck on how to successfully give a ULA address to each of the configured peers so that I'm able to do the same with a road warrior configuration.
So far, even if I give both the interface and the peer an address from the br-lan group, I am only able to get a ping through to the peer if I'm using an IPv6 address that's exclusive to the Wireguard interface, using the LAN's address ends in a destination unreachable: no route message when trying to ping from the console. As of now, this means that the peer is unable to connect through IPv6 to anywhere.
I have seen this article on the wiki, and I believe it speaks exactly of the issue I'm trying to figure out, though, if possible, I'd like not to have to recreate all of my current configuration to be able to use the features described there.
Given my current situation, what would be the best way to try and troubleshoot this problem?
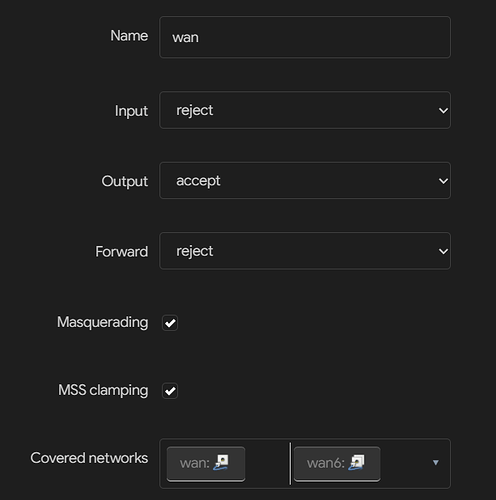
Thanks in advance! I'll make sure to attach my network and firewall configurations below.
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'ddf8:f929:5f71::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
list ports 'ztrta4adry'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '64'
option ip6class 'local'
config interface 'wan'
option proto 'pppoe'
option device 'eth0'
option username 'REDACTED'
option password 'REDACTED'
option ipv6 '1'
list ip6class 'local'
option delegate '0'
config interface 'wan6'
option proto 'dhcpv6'
option device '@wan'
option reqprefix '64'
option reqaddress 'try'
option sourcefilter '0'
option ip6assign '64'
list ip6class 'wan6'
config interface 'docker'
option device 'docker0'
option proto 'none'
option auto '0'
option peerdns '0'
option ip6assign '64'
list ip6class 'local'
list ip6class 'wan_6'
config device
option type 'bridge'
option name 'docker0'
config interface 'wg0'
option proto 'wireguard'
option private_key 'REDACTED'
option listen_port '51820'
list ip6class 'local'
option ip6assign '64'
list addresses '10.0.5.1/24'
list addresses 'fe80::e097:46ff:fef0:2d8e/64'
list addresses 'fd2d:a278:3852::1/64'
config wireguard_wg0
option public_key 'REDACTED'
option description 'ToastyPen10+'
option endpoint_port '51820'
option persistent_keepalive '25'
option preshared_key 'REDACTED'
list allowed_ips '10.0.5.2/32'
list allowed_ips 'fd2d:a278:3852::2/64'
config wireguard_wg0
option description 'ToastyUFO'
option preshared_key 'REDACTED'
option endpoint_port '51820'
option persistent_keepalive '25'
option public_key 'REDACTED'
list allowed_ips '10.0.5.3/32'
list allowed_ips 'fd2d:a278:3852::3/64'
config wireguard_wg0
option description 'Moto One Action de Liz'
option preshared_key 'REDACTED'
option endpoint_port '51820'
option persistent_keepalive '25'
option public_key 'REDACTED'
list allowed_ips '10.0.5.4/32'
list allowed_ips 'fd2d:a278:3852::4/64'
config wireguard_wg0
option description 'Liz-PC'
option public_key 'REDACTED'
option preshared_key 'REDACTED'
option endpoint_port '51820'
option persistent_keepalive '25'
list allowed_ips '10.0.5.5/32'
list allowed_ips 'fd2d:a278:3852::5/64'
config wireguard_wg0
option description 'Moto One Action de Celia'
option preshared_key 'REDACTED'
option endpoint_port '51820'
option persistent_keepalive '25'
option public_key 'REDACTED'
list allowed_ips '10.0.5.6/32'
list allowed_ips 'fd2d:a278:3852::6/64'
config device
option name 'eth1'
option mtu '1492'
option mtu6 '1492'
config device
option name 'br-iot'
option type 'bridge'
list ports 'br-lan.2'
config device
option name 'br-guest'
option type 'bridge'
list ports 'br-lan.3'
config interface 'ZeroTier'
option proto 'none'
option ip6assign '64'
list ip6class 'local'
list ip6class 'wan_6'
option device 'ztrta4adry'
config device
option name 'pppoe-wan'
option type 'tunnel'
config device
option name 'wg0'
config interface 'wg_usa'
option proto 'wireguard'
option private_key 'REDACTED'
list addresses '10.2.0.2/32'
option peerdns '0'
list dns '10.2.0.1'
config wireguard_wg_usa
option description 'SE-US#1'
option public_key 'REDACTED'
list allowed_ips '0.0.0.0/0'
option endpoint_host 'REDACTED'
option endpoint_port '51820'
config interface 'wg_uk'
option proto 'wireguard'
option private_key 'REDACTED'
list addresses '10.2.0.2/32'
option peerdns '0'
list dns '10.2.0.1'
config wireguard_wg_uk
option description 'IS-ES#1'
option public_key 'REDACTED'
list allowed_ips '0.0.0.0/0'
option endpoint_host 'REDACTED'
option endpoint_port '51820'
config interface 'wg_spa'
option proto 'wireguard'
option private_key 'REDACTED'
list addresses '10.2.0.2/32'
option peerdns '0'
list dns '10.2.0.1'
config wireguard_wg_spa
option description 'CH-UK#1'
option public_key 'REDACTED'
list allowed_ips '0.0.0.0/0'
option endpoint_host 'REDACTED'
option endpoint_port '51820'
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg0'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option masq6 '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config zone
option name 'vpnzone'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
option masq '1'
option masq6 '1'
option masq6_privacy '1'
option mtu_fix '1'
list network 'wg_usa'
list network 'wg_uk'
list network 'wg_spa'
config forwarding
option src 'lan'
option dest 'vpnzone'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6 replies'
option src 'wan'
option proto 'udp'
option src_port '547'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config rule
option target 'ACCEPT'
option src 'wan'
option proto 'udp'
option dest_port '547'
option name 'Allow DHCPv6 (546-to-547)'
option family 'ipv6'
option src_port '546'
config rule
option target 'ACCEPT'
option src 'wan'
option proto 'udp'
option dest_port '546'
option name 'Allow DHCPv6 (547-to-546)'
option family 'ipv6'
option src_port '547'
config include
option path '/etc/firewall.user'
option reload '1'
config zone 'docker'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option name 'docker'
list device 'br-5adff94956ab'
list network 'docker'
config rule
option name 'AllowNGINXPMAdmin'
option src_port '81'
option dest 'lan'
option dest_port '81'
option target 'ACCEPT'
option src 'lan'
list dest_ip '172.18.0.2'
config redirect
option target 'DNAT'
option name 'RProxy-Admin'
option src 'lan'
option src_dport '81'
option dest 'lan'
option dest_port '81'
option dest_ip '172.18.0.2'
option enabled '0'
config redirect
option target 'DNAT'
option name 'RProxy'
option src 'wan'
option dest 'lan'
option dest_ip '172.18.0.2'
option src_dport '80'
option dest_port '80'
config redirect
option target 'DNAT'
option name 'RProxy-SSL'
option src 'wan'
option dest 'lan'
option dest_ip '172.18.0.2'
option dest_port '443'
option src_dport '443'
config redirect 'adblock_wan853'
option src 'wan'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
option name 'AGH DNS over TLS'
option dest 'lan'
option dest_ip '192.168.1.1'
config redirect
option target 'DNAT'
option name 'AGH DNS over QUIC'
option src 'wan'
option src_dport '784'
option dest 'lan'
option dest_ip '192.168.1.1'
option dest_port '784'
config rule
option name 'RClone-GUI'
option src 'lan'
option src_port '5572'
option dest 'lan'
option dest_port '5572'
option target 'ACCEPT'
list dest_ip '192.168.1.1'
list dest_ip 'fd04:52a5:a38a::1'
config rule
option name 'HomeAssistant'
option src 'lan'
option src_port '8123'
option dest 'lan'
option dest_port '8123'
option target 'ACCEPT'
list dest_ip '192.168.1.1'
list dest_ip 'fd04:52a5:a38a::1'
config rule
option name 'Allow-NFS-RPC'
option src 'lan'
option proto 'tcp udp'
option dest_port '111'
option target 'ACCEPT'
config rule
option name 'Allow-NFS'
option src 'lan'
option proto 'tcp udp'
option dest_port '2049'
option target 'ACCEPT'
config rule
option name 'Allow-NFS-Lock'
option src 'lan'
option proto 'tcp udp'
option dest_port '32777:32780'
option target 'ACCEPT'
config rule
option name 'Tautulli'
option src 'lan'
option src_port '8181'
option dest 'lan'
list dest_ip '172.18.0.5'
option dest_port '8181'
option target 'ACCEPT'
config rule
option name 'PiHole-Admin'
option src_port '82'
option dest 'lan'
option dest_port '82'
option target 'ACCEPT'
option src 'lan'
list dest_ip '192.168.1.1'
list dest_ip 'fd04:52a5:a38a::1'
config rule
option name 'Transmission-GUI'
option src 'lan'
option dest 'lan'
option target 'ACCEPT'
list dest_ip '192.168.1.1'
list dest_ip 'fd04:52a5:a38a::1'
option src_port '9091'
option dest_port '9091'
config rule
option name 'NGINXPM-DB'
option src 'lan'
list src_ip '172.18.0.2'
option src_port '3306'
option dest 'lan'
list dest_ip '172.18.0.3'
option dest_port '3306'
option target 'ACCEPT'
config rule
option name 'Adguard-Admin'
option src 'wan'
option src_port '82'
option dest 'lan'
option dest_port '82'
option target 'ACCEPT'
list dest_ip '172.18.0.6'
list dest_ip '2001:3984:3989::6'
config rule 'wg'
option dest_port '51820'
option target 'ACCEPT'
option name 'Allow-WireGuard-lan'
list proto 'tcp'
list proto 'udp'
option src 'wan'
config defaults
option input 'REJECT'
option output 'REJECT'
option forward 'REJECT'
option synflood_protect '1'
option drop_invalid '1'
config rule
option name 'Allow-ZeroTier-Inbound'
list proto 'udp'
option src 'wan'
option dest_port '9993'
option target 'ACCEPT'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option name 'ZeroTier'
list network 'ZeroTier'
config forwarding
option dest 'lan'
option src 'ZeroTier'
config forwarding
option dest 'wan'
option src 'ZeroTier'
config forwarding
option src 'lan'
option dest 'ZeroTier'
config forwarding
option src 'wan'
option dest 'ZeroTier'
config redirect 'adblock_docker53'
option name 'Adblock DNS (docker, 53)'
option src 'docker'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_docker853'
option name 'Adblock DNS (docker, 853)'
option src 'docker'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
config redirect 'adblock_docker5353'
option name 'Adblock DNS (docker, 5353)'
option src 'docker'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config redirect 'adblock_lan53'
option name 'Adblock DNS (lan, 53)'
option src 'lan'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_lan853'
option name 'Adblock DNS (lan, 853)'
option src 'lan'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
config redirect 'adblock_lan5353'
option name 'Adblock DNS (lan, 5353)'
option src 'lan'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config redirect 'adblock_vpnzone53'
option name 'Adblock DNS (vpnzone, 53)'
option src 'vpnzone'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_vpnzone853'
option name 'Adblock DNS (vpnzone, 853)'
option src 'vpnzone'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
config redirect 'adblock_vpnzone5353'
option name 'Adblock DNS (vpnzone, 5353)'
option src 'vpnzone'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config redirect 'adblock_wan53'
option name 'Adblock DNS (wan, 53)'
option src 'wan'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_wan5353'
option name 'Adblock DNS (wan, 5353)'
option src 'wan'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Allow-P2P-USA'
option src 'vpnzone'
option src_dport '58861'
config include 'opennds'
option type 'script'
option path '/usr/lib/opennds/restart.sh'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Mosquitto-Outside'
option src 'wan'
option src_dport '8883-8884'
option dest_ip '192.168.1.1'
option dest_port '8883-8884'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Mosquitto-WebSockets'
option src 'wan'
option src_dport '8083'
option dest_ip '192.168.1.1'
option dest_port '8083'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Allow-ZeroTier-Inbound'
list proto 'udp'
option src 'wan'
option src_dport '9993'
option dest_ip '192.168.1.1'
option dest_port '9993'
config forwarding
option src 'docker'
option dest 'wan'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
config redirect 'dns_int'
option src 'lan'
option src_dport '53'
option proto 'tcp udp'
option target 'DNAT'
option family 'any'
list src_mac '!2C:16:DB:A0:E6:92'
option name 'Redirect-DNS'
option dest_ip '192.168.1.1'
option src_ip '!192.168.1.1'
option enabled '0'
config nat 'dns_masq'
option name 'Masquerade-DNS'
option src 'lan'
option dest_ip '192.168.1.1'
option dest_port '53'
option proto 'tcp udp'
option target 'MASQUERADE'
config rule 'samba_nsds_nt'
option name 'NoTrack-Samba/NS/DS'
option src 'lan'
option dest 'lan'
option dest_port '137-138'
option proto 'udp'
option target 'NOTRACK'
config rule 'samba_ss_nt'
option name 'NoTrack-Samba/SS'
option src 'lan'
option dest 'lan'
option dest_port '139'
option proto 'tcp'
option target 'NOTRACK'
config rule 'samba_smb_nt'
option name 'NoTrack-Samba/SMB'
option src 'lan'
option dest 'lan'
option dest_port '445'
option proto 'tcp'
option target 'NOTRACK'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Allow-WireGuard-Inbound'
option src 'wan'
option src_dport '51820'
option dest_port '51820'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'