Being a little more specific: by 04/26 build I meant r13059. Now I reverted back to r12833, and the wifi speed is usable, but something is not quite right: it's still heavily bogged down. I stopped now smbd (this is a pure wifi router, no shares) and also ddns (also don't use it). I also discovered that adblock was errorring, and I force reinstalled it, that wiped the config file and now it's OK. Now a little more detail about this "bog down situation".
- If I hook straight to a LAN port of the router the Ookla speedtest shows 110Mbps, which is actually little more than the 100Mbps my plan supposed to provide. Last night with r13059 the speedtest through wifi was only 2-5 Mbps, which means basically unusable. Now with r12833 it's up to 50 Mbps, but then where does the extra 50-60 Mbps go?
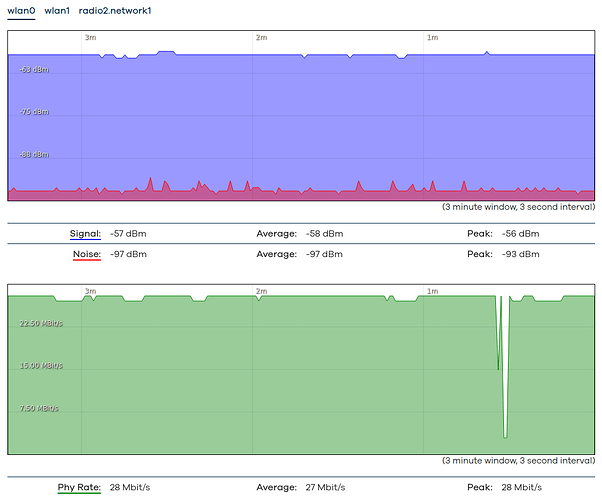
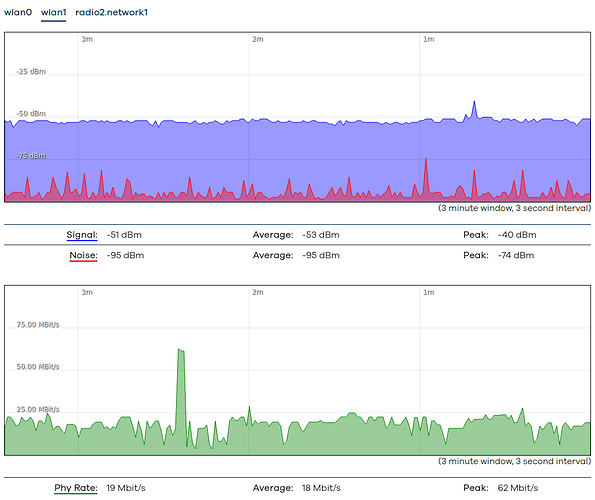
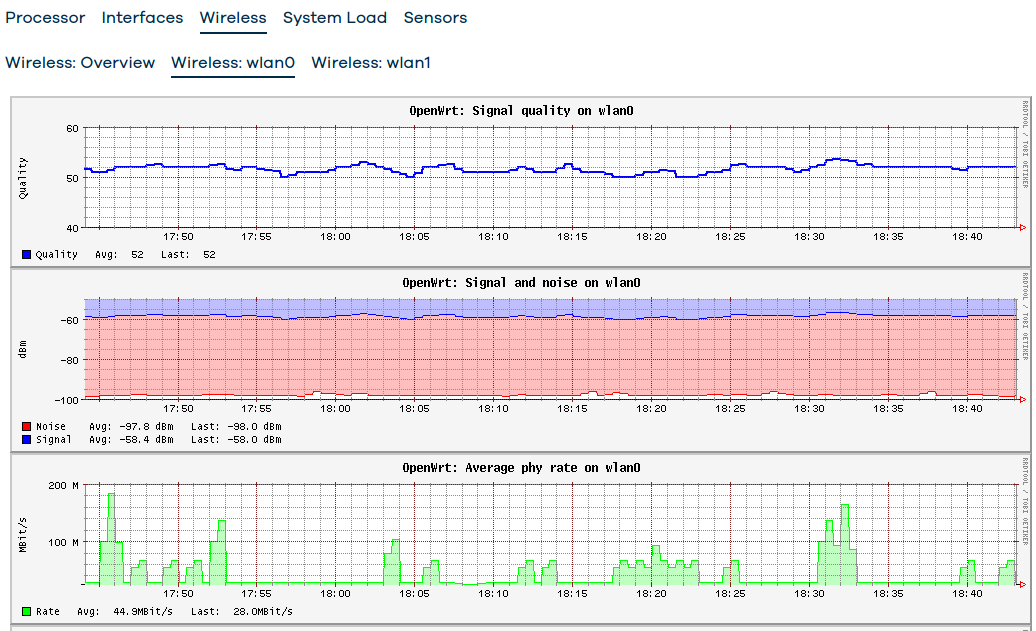
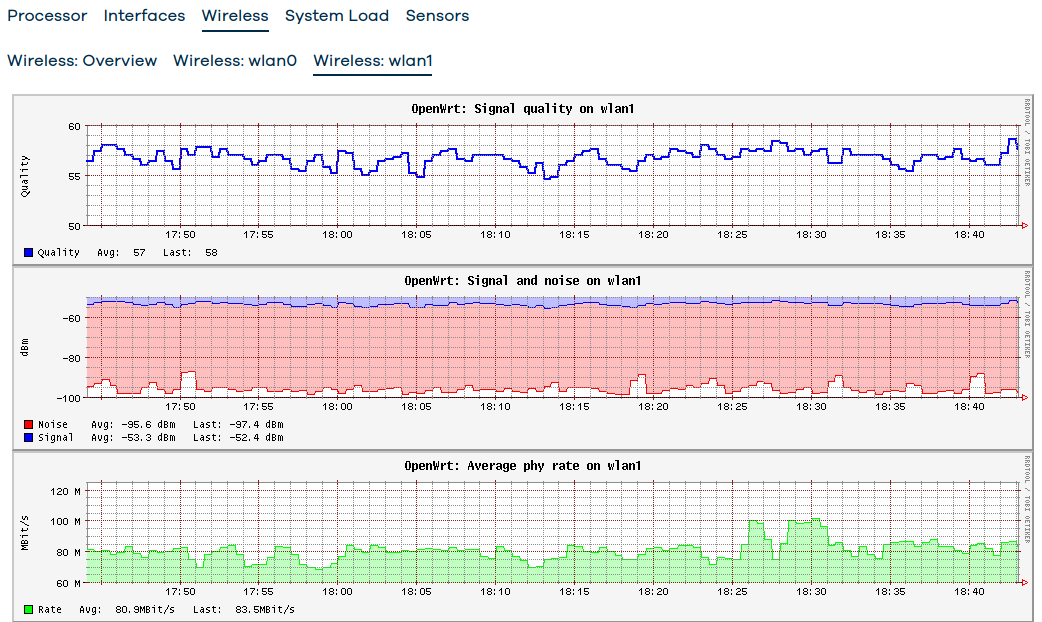
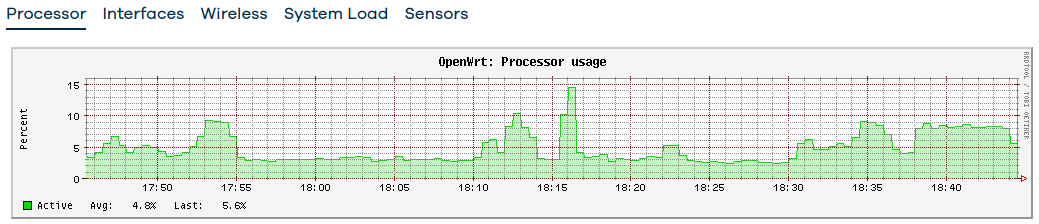
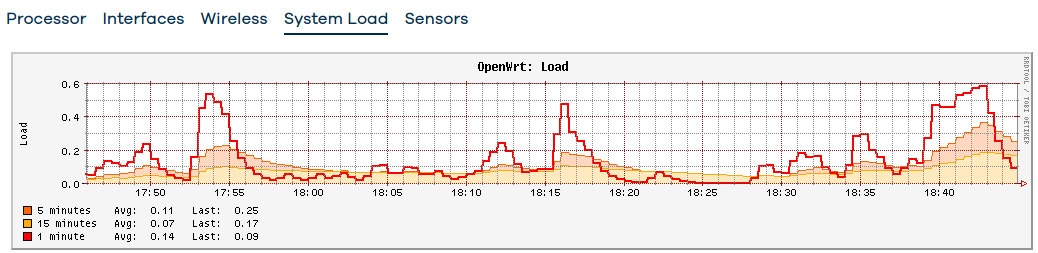
- Well, I'll show real-time graph and statistics graphs of wlan0 and wlan1. These graphs show constant ~25Mbps traffic. Not consistent completely between the aggregated statistics graphs vs the real-time graphs, but they show massive (25 Mbps constant traffic is I'd call massive, especially when I don't have any device which would account for that). The CPU utilization is not high, the system load is low, and although you can see some spikes but those are me mucking around.
- I know what you think: why don't we actually peek into that traffic and see what is that? I couldn't resist to do that.
tcpdump -i wlan0 -l -U -s0 -n -q -c 500ortcpdump -i wlan1 -l -U -s0 -n -q -c 500should have filled the dump file in a blink of an eye if there's 25Mbps traffic. However, the dump lasted several seconds, and it showed completely boring stuff, nothing what I expected that 1.5K packets hauled around. So I'm absolutely dumbfounded. WTF is going on?
Real-time graphs:
Statistic graphs:
Other: