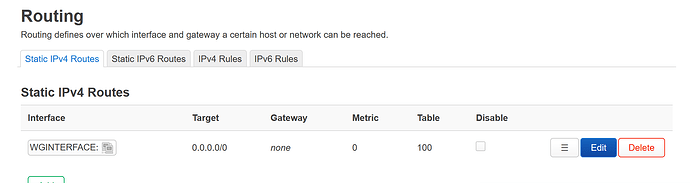
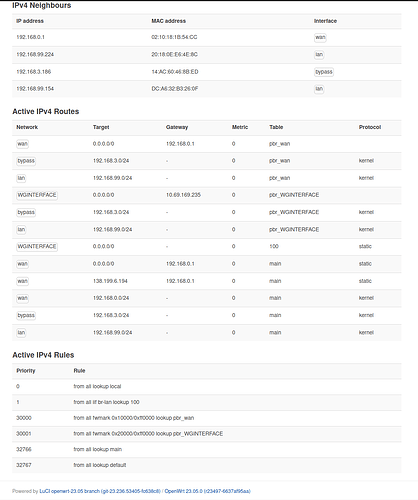
So I want all devices connected to my router via VPNWIFI or lan ports to access internet via Mullvad VPN. Devices connected via BypassWifi should connect to internet straight, without vpn, via WAN. At the same time I want devices connected both ways to treat each other as if they are on the same networks, i.e. when I am on BypassWifi I want to access/ping devices connected on VPNWIFI or lan ports, and vice versa.
P.S. I know there is PBR, but I haven't found an explanation on how to filter sources based on wifi AP they come to network, and I'm keeping that option for later. I want to try to make my current config do what I want.
ubus call system board
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.134",
"hostname": "OpenWrt",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "Xiaomi Redmi Router AC2100",
"board_name": "xiaomi,redmi-router-ac2100",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.0",
"revision": "r23497-6637af95aa",
"target": "ramips/mt7621",
"description": "OpenWrt 23.05.0 r23497-6637af95aa"
}
}
Network
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'CENCORED'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.99.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config device 'bypass_dev'
option type 'bridge'
option name 'br-bypass'
config interface 'bypass'
option proto 'static'
option device 'br-bypass'
list ipaddr '192.168.3.1/24'
option defaultroute '0'
config interface 'WGINTERFACE'
option proto 'wireguard'
option private_key 'CENCORED'
list addresses 'CENCORED'
option force_link '1'
option mtu '1280'
config wireguard_WGINTERFACE
option public_key 'CENCORED'
option endpoint_host 'ONE OF MULLVAD IP SERVERS'
option endpoint_port '51820'
list allowed_ips '0.0.0.0/0'
config route 'vpn_route'
option interface 'WGINTERFACE'
option target '0.0.0.0/0'
option table '100'
config rule 'vpn_rule'
option in 'lan'
option lookup '100'
Wireless
root@OpenWrt:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
option channel '1'
option band '2g'
option htmode 'HT20'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'VPNWIFI'
option encryption 'sae-mixed'
option key 'CENCORED'
config wifi-device 'radio1'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:00.0/0000:01:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'VPNWIFI5G'
option encryption 'sae-mixed'
option key 'CENCORED'
config wifi-iface 'bypass'
option device 'radio0'
option mode 'ap'
option network 'bypass'
option ssid 'BypassWifi'
option encryption 'sae-mixed'
option key 'CENCORED'
config wifi-iface 'bypass5G'
option device 'radio1'
option mode 'ap'
option network 'bypass'
option ssid 'BypassWifi5g'
option encryption 'sae-mixed'
option key 'CENCORED'
DHCP
cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '10.64.0.1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
list dhcp_option '6,10.64.0.1'
option dns_service '0'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'bypass'
option interface 'bypass'
option start '100'
option limit '150'
option leasetime '24h'
list dhcp_option '6,8.8.8.8,8.8.4.4'
Firewall
cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone 'bypass'
option name 'bypass'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'bypass'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule 'bypass_dns'
option name 'Allow-DNS-Guest'
option src 'bypass'
option dest_port '53'
option proto 'tcp udp'
option target 'ACCEPT'
config rule 'bypass_dhcp'
option name 'Allow-DHCP-Guest'
option src 'bypass'
option dest_port '67'
option proto 'udp'
option family 'ipv4'
option target 'ACCEPT'
config zone
option name 'WGZONE'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'WGINTERFACE'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config rule
option name 'Allow-mDNS'
list proto 'udp'
option src '*'
option src_port '5353'
option dest_port '5353'
option target 'ACCEPT'
list dest_ip '224.0.0.221'
config forwarding
option src 'lan'
option dest 'bypass'
config forwarding
option src 'bypass'
option dest 'lan'
config rule
option name 'Allow-All-1'
option src 'bypass'
option dest 'lan'
option target 'ACCEPT'
list proto 'all'
config rule
option name 'Allow-All-2'
option src 'lan'
option dest 'bypass'
option target 'ACCEPT'
list proto 'all'
config forwarding
option src 'lan'
option dest 'WGZONE'
config forwarding
option src 'bypass'
option dest 'wan'