@passwd -
There may be a few different ways to do this, but I would do it in a certain way. First, if you can simply run the VPN client on your PC, it might be the easiest option (assuming the PC is the only device that needs to go through the VPN). But, if you want to use a hardware solution like the RPi, that is absolutely possible.
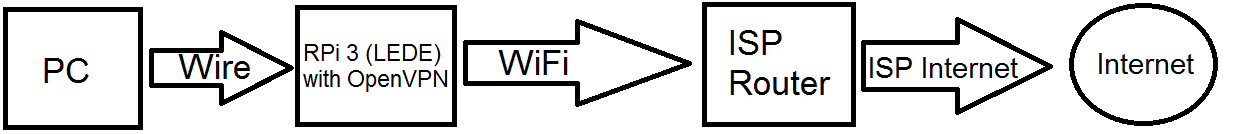
For the RPi to work, I would recommend using it like a router. This means your PC will likely be double-NAT'd which can be an issue from time to time, but is typically not a big deal. By default, your PC will not be reachable by other devices on your network since it will be behind the NAT/firewall, and your PC will probably not be able to access any local network resources when you have the VPN tunnel running and you are blocking traffic from escaping through any means other than the VPN.
That said, I think you probably want to go back to defaults on the RPi config and then set it up to function as a router. Set the wifi interface as the WAN and the ethernet port as LAN. Make sure that you are using a different network address space than the main ISP router -- that is to say that the LAN IP and subnet mask on the RPi must not overlap the main LAN.
Next, make sure your PC is only using ethernet for connectivity to the internet -- it is much easier to manage the traffic if you can guarantee everything is going through a single network interface. Test the internet connectivity (in general) -- it should be working normally. Run a traceroute so you can see where the traffic goes (should be PC > RPi > main router > ISP > ... > target address).
Next, install and configure your VPN client. Make sure you setup a network interface for the VPN as well as an associated firewall zone and that you allow forwarding from LAN > VPN. Also, make sure that all traffic is set to be directed through the VPN -- if you're using OpenVPN, you'll want a 'redirect gateway def1' directive in your client side config file.
Start the VPN and ensure that it is working. You can test with a traceroute again -- you should see it skip your main router and ISP (and a bunch of other stuff) and emerge from the VPN provider's IP.
Stop the VPN. Run traceroute and observe that you should see stuff flowing through your ISP again.
To prevent traffic from flowing out when the VPN is down, you'll remove the forwarding rule from LAN > WAN. (you can remove this or set it to reject or drop). Now, you should not be able to access anything outside the RPi's LAN (which is in theory just your PC and the RPi itself). Start the VPN and you should have internet access again.
If you want to be able to access LAN resources that are not part of the RPi's network, you may need to set some special firewall rules and/or routing tables to get that to work. But if you're really just looking for VPN protected internet access, this should be all you need.

 .
.

 maybe because input rule
maybe because input rule
