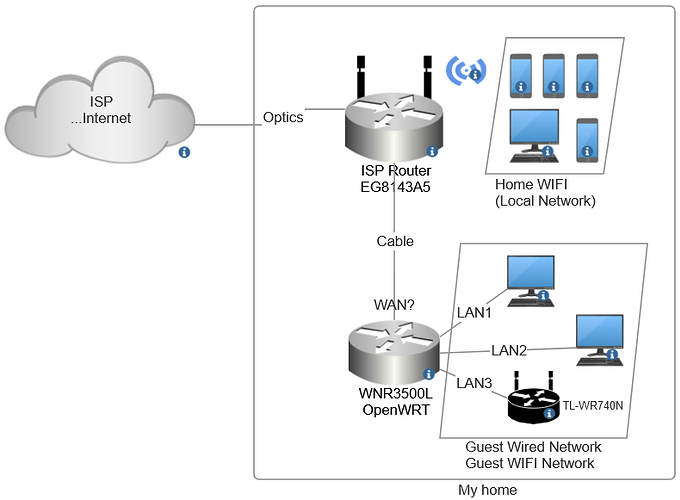
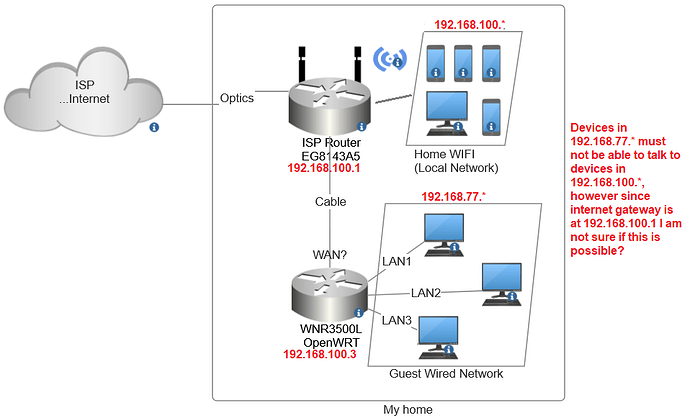
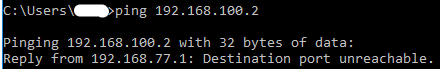
Hello, here is the current config:
root@OpenWrt:~# ubus call system board
{
"kernel": "5.10.176",
"hostname": "OpenWrt",
"system": "Broadcom BCM4716",
"model": "Netgear WNR3500L",
"board_name": "0x04CF:3500",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.5",
"revision": "r20134-5f15225c1e",
"target": "bcm47xx/mips74k",
"description": "OpenWrt 22.03.5 r20134-5f15225c1e"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd2c:6c65:a831::/48'
config interface 'wan'
option device 'eth0.1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.1'
option proto 'dhcpv6'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 8t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 8t'
config interface 'guest_interface'
option device 'eth0.10'
option proto 'static'
option ipaddr '192.168.77.1'
option netmask '255.255.255.0'
option gateway '192.168.100.1'
config switch_vlan
option device 'switch0'
option ports '1 2 3 8t'
option vlan '10'
option description 'guest_vlan'
root@OpenWrt:~# cat /etc/config/wireless
>>> Please note that I will have radio disabled at all times. No radio required for this excercise...
config wifi-device 'radio0'
option type 'mac80211'
option path 'bcm47xx_soc/bcma0:1'
option channel '1'
option band '2g'
option htmode 'NOHT'
option disabled '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest_interface'
option interface 'guest_interface'
option ignore '1'
option start '100'
option limit '150'
option leasetime '1h'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'guest_zone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest_interface'
config forwarding
option src 'guest_zone'
option dest 'wan'
config rule
option name 'Guest DNS'
option src 'guest_zone'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Guest DHCP'
list proto 'udp'
option src 'guest_zone'
option dest_port '67 68'
option target 'ACCEPT'
There is also one more rule which is currently disabled:
config rule
option name 'block_guest'
list proto 'all'
option src 'guest_zone'
list dest_ip '192.168.100.0/24'
option target 'REJECT'
option enabled '0'
Enabling or disabling this rule "block_guest" also blocks the Internet foe guests, probably because gateway is at 192.168.100.1?
![]()