Hello all. I setup a dedicated server at my home for my gaming group. In order to isolate it from the rest of the LAN I thought to create a separate VLAN for it that only uses Ethernet port 1, while all the other ports are for the main LAN. I also created two additional zones in the firewall (dcs for such server, and guest for the guest WiFi network).
The server can successfully connect to the WAN and other people can access it, but I cannot from my PC in the lan zone. I tried connecting my PC with a mobile hotspot through my cell phone, and in that case I can successfully connect, so I guess it's something in the firewall. Also, if I change the port forwarding rules from dest 'dcs' to dest 'lan' I can connect, but I honestly cannot understand why, and it seems wrong, isn't it?
here are my configs for network and firewall:
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd0b:f52a:7a73::/48'
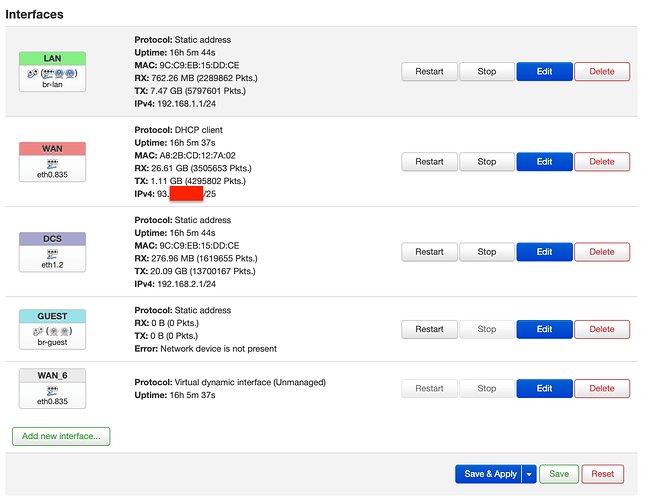
config interface 'lan'
option type 'bridge'
option ifname 'eth1.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
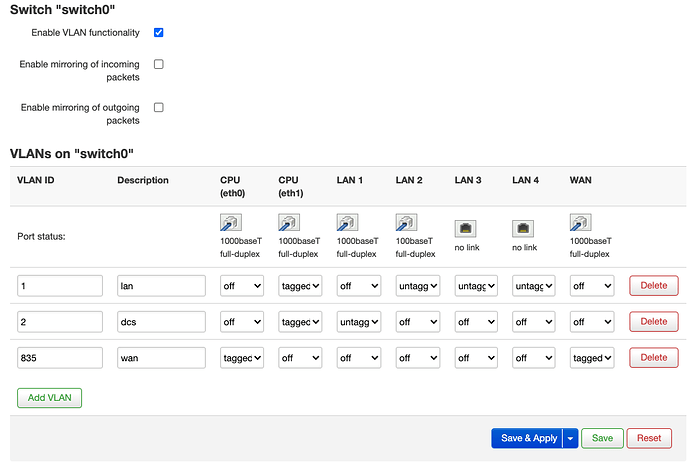
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option description 'lan'
option ports '6t 3 2 1'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '835'
option description 'wan'
option ports '0t 5t'
config interface 'wan'
option ifname 'eth0.835'
option proto 'dhcp'
option macaddr 'A8:2B:CD:xx:xx:xx'
option vendorid 'huawei_HW_E1A.A_SW_1.0.1b/dslforum.org'
option peerdns '0'
list dns '8.8.8.8'
list dns '1.1.1.1'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '2'
option description 'dcs'
option ports '6t 4'
config interface 'dcs'
option ifname 'eth1.2'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.2.1'
config interface 'guest'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.3.1'
config defaults
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option input 'REJECT'
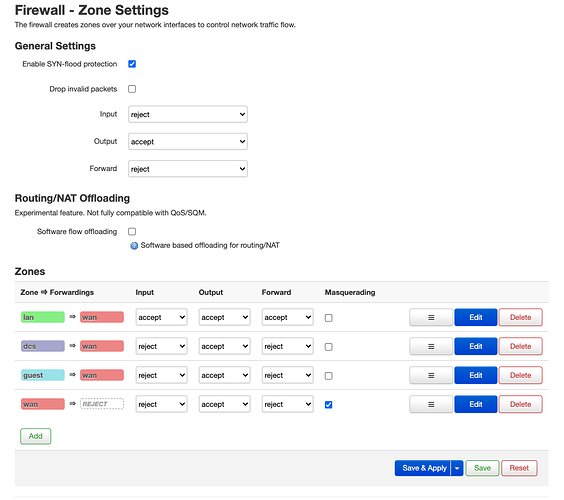
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config forwarding
option src 'lan'
option dest 'wan'
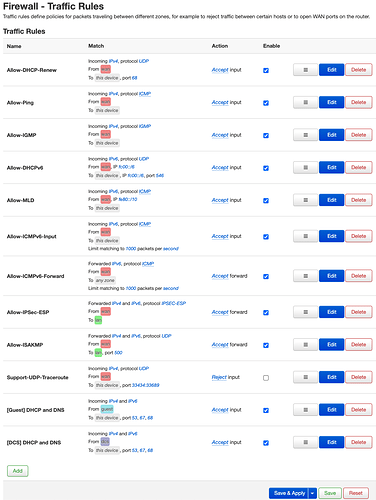
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config zone
option name 'dcs'
option output 'ACCEPT'
list network 'dcs'
option input 'REJECT'
option forward 'REJECT'
config zone
option name 'guest'
list network 'guest'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'wan'
option forward 'REJECT'
config rule
option src 'guest'
option dest_port '53 67 68'
option target 'ACCEPT'
option name '[Guest] DHCP and DNS'
config forwarding
option src 'guest'
option dest 'wan'
config forwarding
option src 'dcs'
option dest 'wan'
config rule
option name '[DCS] DHCP and DNS'
option src 'dcs'
option dest_port '53 67 68'
option target 'ACCEPT'
config redirect
option target 'DNAT'
option src 'wan'
option dest_ip '192.168.2.203'
option name 'DCS Server 10307'
option src_dport '10307'
option dest_port '10307'
option dest 'dcs'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'dcs'
option dest_ip '192.168.2.203'
option name 'DCS Server 10308'
option src_dport '10308'
option dest_port '10308'
config redirect
option target 'DNAT'
option name 'DCS Server 10310'
option src 'wan'
option src_dport '10310'
option dest_ip '192.168.2.203'
option dest_port '10310'
option dest 'dcs'
config redirect
option target 'DNAT'
option name 'SimpleRadio 5002'
option src 'wan'
option src_dport '5002'
option dest_ip '192.168.2.203'
option dest_port '5002'
option dest 'dcs'
config redirect
option target 'DNAT'
option name 'Tacview 42674'
list proto 'tcp'
option src 'wan'
option src_dport '42674'
option dest_ip '192.168.2.203'
option dest_port '42674'
option dest 'dcs'
config redirect
option target 'DNAT'
option name 'TeamSpeak 9987'
option src 'wan'
option src_dport '9987'
option dest_ip '192.168.2.203'
option dest_port '9987'
list proto 'udp'
option dest 'dcs'
config redirect
option target 'DNAT'
option name 'TeamSpeak 10011'
list proto 'tcp'
option src 'wan'
option src_dport '10011'
option dest_ip '192.168.2.203'
option dest_port '10011'
option dest 'dcs'
config redirect
option target 'DNAT'
option name 'TeamSpeak 30033'
list proto 'tcp'
option src 'wan'
option src_dport '30033'
option dest_ip '192.168.2.203'
option dest_port '30033'
option dest 'dcs'
Any hint would be greatly appreciated!
ASFP
May 21, 2021, 11:14am
2
2 possible solutions:
config forwarding
option src 'lan'
option dest 'dcs'
The other solution would be to duplicate the firewall rules you already have that allow wan->dcs. change those that they allow lan->dcs on the specified ports. The options option dest_ip and option dest_port will not be needed. (You have to use the IP of your server when connecting from you lan)
Also you're current firewall rules wan->dcs do not need the option dest_port. You only need that if you want to change the port of the traffic, which isn't the case.
1 Like
This was one of the things I already tried, but apparently it doesn't seem to work, just tried again. I'll try the other solution later.
ASFP
May 21, 2021, 11:31am
4
Can you send me some LuCI Screenshots, would give me a better overview.
ASFP
May 21, 2021, 12:55pm
6
Don't know why this isn't solving the issue. It should do the trick.
Yeah... I cannot understand either. Moreover, I cannot understand why changing option dest 'dcs' to option dest 'lan' works. This really bugs me.
EDIT: since I'm at a loss here... could it be that the router doesn't route the packets outside of the wan interface and back to the dcs zone because it resolves my WAN IP to one of its interfaces? I really cannot shake this from my head...
If you are trying to access the server in dcs from a host in lan by the wan IP or some ddns hostname, it won't work.create a hostname with the server hostname pointing to the private IP and use that name.
2 Likes
Ok, I'll keep the lan->dcs rule, it makes sense after all.
But still... it's not working I'm afraid. There must be something else...
Isn't the fact that the game server is on a different VLAN and a different subnet an issue here?
When you use DNAT, fw3 automatically creates the corresponding additional iptables NAT reflection rules based on the destination zone.
trendy
May 21, 2021, 1:28pm
11
It's not connected.iptables-save -c . I suppose the server is .2.203
trendy:
You need the lan->dcs forwarding in the firewall, so keep it there.create a hostname with the server hostname pointing to the private IP and use that name.
Ok, added lan->dcs and trying to reach the server via the local IP (192.168.2.x) and I can see it.lan zone. But again, for me, it wouldn't work. It's not critical (although a bit annoying), but if there was a chance for me to connect to the WAN IP, that would be awesome.
root@OpenWrt:~# iptables-save -c
# Generated by iptables-save v1.8.7 on Fri May 21 15:29:30 2021
*nat
:PREROUTING ACCEPT [2228:389491]
:INPUT ACCEPT [424:29797]
:OUTPUT ACCEPT [267:18598]
:POSTROUTING ACCEPT [797:47084]
:postrouting_dcs_rule - [0:0]
:postrouting_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_dcs_rule - [0:0]
:prerouting_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_dcs_postrouting - [0:0]
:zone_dcs_prerouting - [0:0]
:zone_guest_postrouting - [0:0]
:zone_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[3011:435687] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[1873:346949] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[91:18559] -A PREROUTING -i eth1.2 -m comment --comment "!fw3" -j zone_dcs_prerouting
[0:0] -A PREROUTING -i br-guest -m comment --comment "!fw3" -j zone_guest_prerouting
[1047:70179] -A PREROUTING -i eth0.835 -m comment --comment "!fw3" -j zone_wan_prerouting
[1678:257033] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[787:46390] -A POSTROUTING -o eth1.2 -m comment --comment "!fw3" -j zone_dcs_postrouting
[0:0] -A POSTROUTING -o br-guest -m comment --comment "!fw3" -j zone_guest_postrouting
[881:209949] -A POSTROUTING -o eth0.835 -m comment --comment "!fw3" -j zone_wan_postrouting
[787:46390] -A zone_dcs_postrouting -m comment --comment "!fw3: Custom dcs postrouting rule chain" -j postrouting_dcs_rule
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p tcp -m tcp --dport 10307 -m comment --comment "!fw3: DCS Server 10307 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p udp -m udp --dport 10307 -m comment --comment "!fw3: DCS Server 10307 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p tcp -m tcp --dport 10308 -m comment --comment "!fw3: DCS Server 10308 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p udp -m udp --dport 10308 -m comment --comment "!fw3: DCS Server 10308 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p tcp -m tcp --dport 10310 -m comment --comment "!fw3: DCS Server 10310 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p udp -m udp --dport 10310 -m comment --comment "!fw3: DCS Server 10310 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p tcp -m tcp --dport 5002 -m comment --comment "!fw3: SimpleRadio 5002 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p udp -m udp --dport 5002 -m comment --comment "!fw3: SimpleRadio 5002 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p tcp -m tcp --dport 42674 -m comment --comment "!fw3: Tacview 42674 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p udp -m udp --dport 9987 -m comment --comment "!fw3: TeamSpeak 9987 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p tcp -m tcp --dport 10011 -m comment --comment "!fw3: TeamSpeak 10011 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_dcs_postrouting -s 192.168.2.0/24 -d 192.168.2.203/32 -p tcp -m tcp --dport 30033 -m comment --comment "!fw3: TeamSpeak 30033 (reflection)" -j SNAT --to-source 192.168.2.1
[91:18559] -A zone_dcs_prerouting -m comment --comment "!fw3: Custom dcs prerouting rule chain" -j prerouting_dcs_rule
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p tcp -m tcp --dport 10307 -m comment --comment "!fw3: DCS Server 10307 (reflection)" -j DNAT --to-destination 192.168.2.203:10307
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p udp -m udp --dport 10307 -m comment --comment "!fw3: DCS Server 10307 (reflection)" -j DNAT --to-destination 192.168.2.203:10307
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p tcp -m tcp --dport 10308 -m comment --comment "!fw3: DCS Server 10308 (reflection)" -j DNAT --to-destination 192.168.2.203:10308
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p udp -m udp --dport 10308 -m comment --comment "!fw3: DCS Server 10308 (reflection)" -j DNAT --to-destination 192.168.2.203:10308
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p tcp -m tcp --dport 10310 -m comment --comment "!fw3: DCS Server 10310 (reflection)" -j DNAT --to-destination 192.168.2.203:10310
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p udp -m udp --dport 10310 -m comment --comment "!fw3: DCS Server 10310 (reflection)" -j DNAT --to-destination 192.168.2.203:10310
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p tcp -m tcp --dport 5002 -m comment --comment "!fw3: SimpleRadio 5002 (reflection)" -j DNAT --to-destination 192.168.2.203:5002
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p udp -m udp --dport 5002 -m comment --comment "!fw3: SimpleRadio 5002 (reflection)" -j DNAT --to-destination 192.168.2.203:5002
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p tcp -m tcp --dport 42674 -m comment --comment "!fw3: Tacview 42674 (reflection)" -j DNAT --to-destination 192.168.2.203:42674
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p udp -m udp --dport 9987 -m comment --comment "!fw3: TeamSpeak 9987 (reflection)" -j DNAT --to-destination 192.168.2.203:9987
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p tcp -m tcp --dport 10011 -m comment --comment "!fw3: TeamSpeak 10011 (reflection)" -j DNAT --to-destination 192.168.2.203:10011
[0:0] -A zone_dcs_prerouting -s 192.168.2.0/24 -d 93.xxx.xxx.xxx/32 -p tcp -m tcp --dport 30033 -m comment --comment "!fw3: TeamSpeak 30033 (reflection)" -j DNAT --to-destination 192.168.2.203:30033
[0:0] -A zone_guest_postrouting -m comment --comment "!fw3: Custom guest postrouting rule chain" -j postrouting_guest_rule
[0:0] -A zone_guest_prerouting -m comment --comment "!fw3: Custom guest prerouting rule chain" -j prerouting_guest_rule
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[1873:346949] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[881:209949] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[881:209949] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[1047:70179] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 10307 -m comment --comment "!fw3: DCS Server 10307" -j DNAT --to-destination 192.168.2.203:10307
[256:15104] -A zone_wan_prerouting -p udp -m udp --dport 10307 -m comment --comment "!fw3: DCS Server 10307" -j DNAT --to-destination 192.168.2.203:10307
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 10308 -m comment --comment "!fw3: DCS Server 10308" -j DNAT --to-destination 192.168.2.203:10308
[257:15163] -A zone_wan_prerouting -p udp -m udp --dport 10308 -m comment --comment "!fw3: DCS Server 10308" -j DNAT --to-destination 192.168.2.203:10308
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 10310 -m comment --comment "!fw3: DCS Server 10310" -j DNAT --to-destination 192.168.2.203:10310
[258:15209] -A zone_wan_prerouting -p udp -m udp --dport 10310 -m comment --comment "!fw3: DCS Server 10310" -j DNAT --to-destination 192.168.2.203:10310
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 5002 -m comment --comment "!fw3: SimpleRadio 5002" -j DNAT --to-destination 192.168.2.203:5002
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 5002 -m comment --comment "!fw3: SimpleRadio 5002" -j DNAT --to-destination 192.168.2.203:5002
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 42674 -m comment --comment "!fw3: Tacview 42674" -j DNAT --to-destination 192.168.2.203:42674
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 9987 -m comment --comment "!fw3: TeamSpeak 9987" -j DNAT --to-destination 192.168.2.203:9987
[12:720] -A zone_wan_prerouting -p tcp -m tcp --dport 10011 -m comment --comment "!fw3: TeamSpeak 10011" -j DNAT --to-destination 192.168.2.203:10011
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 30033 -m comment --comment "!fw3: TeamSpeak 30033" -j DNAT --to-destination 192.168.2.203:30033
COMMIT
# Completed on Fri May 21 15:29:30 2021
# Generated by iptables-save v1.8.7 on Fri May 21 15:29:30 2021
*mangle
:PREROUTING ACCEPT [64218:42998257]
:INPUT ACCEPT [1809:176964]
:FORWARD ACCEPT [61377:42673059]
:OUTPUT ACCEPT [1717:329027]
:POSTROUTING ACCEPT [63055:43000459]
[291:16600] -A FORWARD -o eth0.835 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[237:13476] -A FORWARD -i eth0.835 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Fri May 21 15:29:30 2021
# Generated by iptables-save v1.8.7 on Fri May 21 15:29:30 2021
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_dcs_rule - [0:0]
:forwarding_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_dcs_rule - [0:0]
:input_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_dcs_rule - [0:0]
:output_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_dcs_dest_ACCEPT - [0:0]
:zone_dcs_dest_REJECT - [0:0]
:zone_dcs_forward - [0:0]
:zone_dcs_input - [0:0]
:zone_dcs_output - [0:0]
:zone_dcs_src_REJECT - [0:0]
:zone_guest_dest_ACCEPT - [0:0]
:zone_guest_dest_REJECT - [0:0]
:zone_guest_forward - [0:0]
:zone_guest_input - [0:0]
:zone_guest_output - [0:0]
:zone_guest_src_REJECT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[296:25562] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[1514:151454] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[706:91311] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[124:5540] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[436:30696] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[35:2540] -A INPUT -i eth1.2 -m comment --comment "!fw3" -j zone_dcs_input
[0:0] -A INPUT -i br-guest -m comment --comment "!fw3" -j zone_guest_input
[337:26907] -A INPUT -i eth0.835 -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -m comment --comment "!fw3" -j reject
[61377:42673059] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[59958:42431891] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[569:191832] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[67:3140] -A FORWARD -i eth1.2 -m comment --comment "!fw3" -j zone_dcs_forward
[0:0] -A FORWARD -i br-guest -m comment --comment "!fw3" -j zone_guest_forward
[783:46196] -A FORWARD -i eth0.835 -m comment --comment "!fw3" -j zone_wan_forward
[1:52] -A FORWARD -m comment --comment "!fw3" -j reject
[296:25562] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[1423:304805] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[1158:286308] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o eth1.2 -m comment --comment "!fw3" -j zone_dcs_output
[0:0] -A OUTPUT -o br-guest -m comment --comment "!fw3" -j zone_guest_output
[265:18497] -A OUTPUT -o eth0.835 -m comment --comment "!fw3" -j zone_wan_output
[195:8324] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[144:18701] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[124:5540] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[4:204] -A zone_dcs_dest_ACCEPT -o eth1.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_dcs_dest_REJECT -o eth1.2 -m comment --comment "!fw3" -j reject
[67:3140] -A zone_dcs_forward -m comment --comment "!fw3: Custom dcs forwarding rule chain" -j forwarding_dcs_rule
[67:3140] -A zone_dcs_forward -m comment --comment "!fw3: Zone dcs to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_dcs_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[1:52] -A zone_dcs_forward -m comment --comment "!fw3" -j zone_dcs_dest_REJECT
[35:2540] -A zone_dcs_input -m comment --comment "!fw3: Custom dcs input rule chain" -j input_dcs_rule
[0:0] -A zone_dcs_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: [DCS] DHCP and DNS" -j ACCEPT
[0:0] -A zone_dcs_input -p tcp -m tcp --dport 67 -m comment --comment "!fw3: [DCS] DHCP and DNS" -j ACCEPT
[0:0] -A zone_dcs_input -p tcp -m tcp --dport 68 -m comment --comment "!fw3: [DCS] DHCP and DNS" -j ACCEPT
[32:2306] -A zone_dcs_input -p udp -m udp --dport 53 -m comment --comment "!fw3: [DCS] DHCP and DNS" -j ACCEPT
[0:0] -A zone_dcs_input -p udp -m udp --dport 67 -m comment --comment "!fw3: [DCS] DHCP and DNS" -j ACCEPT
[0:0] -A zone_dcs_input -p udp -m udp --dport 68 -m comment --comment "!fw3: [DCS] DHCP and DNS" -j ACCEPT
[0:0] -A zone_dcs_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[3:234] -A zone_dcs_input -m comment --comment "!fw3" -j zone_dcs_src_REJECT
[0:0] -A zone_dcs_output -m comment --comment "!fw3: Custom dcs output rule chain" -j output_dcs_rule
[0:0] -A zone_dcs_output -m comment --comment "!fw3" -j zone_dcs_dest_ACCEPT
[3:234] -A zone_dcs_src_REJECT -i eth1.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_guest_dest_ACCEPT -o br-guest -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_guest_dest_REJECT -o br-guest -m comment --comment "!fw3" -j reject
[0:0] -A zone_guest_forward -m comment --comment "!fw3: Custom guest forwarding rule chain" -j forwarding_guest_rule
[0:0] -A zone_guest_forward -m comment --comment "!fw3: Zone guest to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_guest_forward -m comment --comment "!fw3" -j zone_guest_dest_REJECT
[0:0] -A zone_guest_input -m comment --comment "!fw3: Custom guest input rule chain" -j input_guest_rule
[0:0] -A zone_guest_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: [Guest] DHCP and DNS" -j ACCEPT
[0:0] -A zone_guest_input -p tcp -m tcp --dport 67 -m comment --comment "!fw3: [Guest] DHCP and DNS" -j ACCEPT
[0:0] -A zone_guest_input -p tcp -m tcp --dport 68 -m comment --comment "!fw3: [Guest] DHCP and DNS" -j ACCEPT
[0:0] -A zone_guest_input -p udp -m udp --dport 53 -m comment --comment "!fw3: [Guest] DHCP and DNS" -j ACCEPT
[0:0] -A zone_guest_input -p udp -m udp --dport 67 -m comment --comment "!fw3: [Guest] DHCP and DNS" -j ACCEPT
[0:0] -A zone_guest_input -p udp -m udp --dport 68 -m comment --comment "!fw3: [Guest] DHCP and DNS" -j ACCEPT
[0:0] -A zone_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_guest_input -m comment --comment "!fw3" -j zone_guest_src_REJECT
[0:0] -A zone_guest_output -m comment --comment "!fw3: Custom guest output rule chain" -j output_guest_rule
[0:0] -A zone_guest_output -m comment --comment "!fw3" -j zone_guest_dest_ACCEPT
[0:0] -A zone_guest_src_REJECT -i br-guest -m comment --comment "!fw3" -j reject
[0:0] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[569:191832] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[569:191832] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[4:204] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to dcs forwarding policy" -j zone_dcs_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[436:30696] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[436:30696] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[0:0] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[0:0] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[436:30696] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[38:1575] -A zone_wan_dest_ACCEPT -o eth0.835 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[858:211638] -A zone_wan_dest_ACCEPT -o eth0.835 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth0.835 -m comment --comment "!fw3" -j reject
[783:46196] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[783:46196] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[337:26907] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[2:168] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[335:26739] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[265:18497] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[265:18497] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[335:26739] -A zone_wan_src_REJECT -i eth0.835 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Fri May 21 15:29:30 2021
trendy
May 21, 2021, 1:31pm
14
There is, but you should take in consideration that it will use extra cycles on the cpu, since it will do some DNAT, which should be avoided for the inter-vlan traffic.
trendy:
There is, but you should take in consideration that it will use extra cycles on the cpu, since it will do some DNAT, which should be avoided for the inter-vlan traffic.
Well, I would like to try, unless there are security concerns. And of course, I'm open to any alternative solution in general. I thought that having a separate VLAN was a good idea to isolate the server from the rest of the network, but if it's not I will gladly explore other ways.
mk24
May 21, 2021, 1:35pm
16
The script should advertise your public DNS name not the WAN IP. Then the LAN user will use the same local host DNS to resolve that name into a local IP, while remote users will resolve it to the public IP.
Also you don't need an option dest in the port forward rules at all, since the destination IP defines which network and firewall zone is the destination.
1 Like
trendy
May 21, 2021, 1:42pm
17
It is, but what you are trying to achieve (that is accessing an internal server from an external IP) is not best practice.
iptables -A zone_lan_prerouting -s 192.168.1.0/24 -d 93.xxx.xxx.xxx/32 -p tcp -m tcp --dport 10307 -m comment --comment "!fw3: DCS Server 10307 (reflection)" -j DNAT --to-destination 192.168.2.203:10307
iptables -A zone_dcs_postrouting -s 192.168.1.0/24 -d 192.168.2.203/32 -p tcp -m tcp --dport 10307 -m comment --comment "!fw3: DCS Server 10307 (reflection)" -j SNAT --to-source 192.168.2.1
Try these rules to test, use the right ports and protocols.@mk24 mentioned, verify that the script indeed advertises an IP and not the hostname.
1 Like
I'm trying to understand why, but
root@OpenWrt:~# iptables -A zone_lan_prerouting -s 192.168.1.0/24 -d 93.xxx.xxx.xxx/32 -p tcp -m tcp --dport 10307 -m comment --comment "!fw3: DCS Server 10307 (reflection)" -j DNAT --to-destination 192.168.2.203:10307
iptables: No chain/target/match by that name.
for both rules (yes, I'm using the correct IP in the real rule
I did a quick search, perhaps I'm missing some iptables module? but testing them independently, they all return proper error messages... What else could it be?
EDIT: it seems that adding -t nat fixes the error. is that the case?
EDIT2: adding -t nat actually works! I'm getting there, thank you!
1 Like
trendy
May 21, 2021, 3:04pm
19
Yes, sorry I forgot the -t nat.
Well... apparently I spoke too fast. I mean, the rules seem to be working because all the "side utilities" I installed on the same server (a TeamSpeak server, and a couple of other apps -- a total of ~10 rules) are working, but apparently DCS itself is not: i mean, I can nc 93.xxx.xxx.xxx 10307 correctly (the connection drops after 1 second, but I guess it could be the way DCS is written, to drop a connection if no traffic comes in?), but from inside the game I cannot find my server. I double checked multiple times, and the rules are all correct. Moreover, I tried to switch my local PC from the WLAN of the router to my mobile hotspot, so not going through the router, and this time I can find the server. Funny thing is, switching back to the local WLAN... and it still works! Until I reboot my PC; after that, I am back to square one, not finding the server.
Now, I know I may be off topic, so tell me if I should open another thread, but... assuming the rules are correct, is there something I can do to "debug" what's going on?