I fked up...
Changed firewall zone lan>wan , input,output,forward everything to reject and can't access router anymore xd ( I wanted to temp disable internet on lan while I'm testing something... )
Anyways I eventually managed to get back into router - reboot into failsafe mode and then I issued these commands :
root@(none):/rom/root# uci set firewall.@zone[0].input='ACCEPT'
root@(none):/rom/root# uci set firewall.@zone[0].output='ACCEPT'
root@(none):/rom/root# uci set firewall.@zone[0].forward='ACCEPT'
I am not sure though if anything else needs to be changed ? I am very new to openwrt as you can see xd This is my first time using uci and I don't really understand how zones,rules work...
Could you check if firewall looks ok now? I am afraid I might have fked something up.... thanks
This is what it looked like while I was locked out:
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@defaults[0].synflood_protect='1'
firewall.@defaults[0].flow_offloading='1'
firewall.@defaults[0].flow_offloading_hw='1'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='REJECT'
firewall.@zone[0].output='REJECT'
firewall.@zone[0].forward='REJECT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan' 'wan6'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@zone[2]=zone
firewall.@zone[2].name='guestlanfw'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].forward='REJECT'
firewall.@zone[2].network='guest_lan'
firewall.@zone[2].input='REJECT'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='guestlanfw'
firewall.@forwarding[1].dest='wan'
firewall.@rule[9]=rule
firewall.@rule[9].name='Guest-lan-dhcp'
firewall.@rule[9].proto='udp'
firewall.@rule[9].src='guestlanfw'
firewall.@rule[9].dest_port='67'
firewall.@rule[9].target='ACCEPT'
firewall.@rule[10]=rule
firewall.@rule[10].name='Guest-lan-dns'
firewall.@rule[10].src='guestlanfw'
firewall.@rule[10].dest_port='53'
firewall.@rule[10].target='ACCEPT'
firewall.@rule[11]=rule
firewall.@rule[11].name='Guest-block-all'
firewall.@rule[11].src='guestlanfw'
firewall.@rule[11].target='DROP'
This is after I changed firewall in failsafe with commands above:
root@(none):/rom/root# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@defaults[0].synflood_protect='1'
firewall.@defaults[0].flow_offloading='1'
firewall.@defaults[0].flow_offloading_hw='1'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan' 'wan6'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@zone[2]=zone
firewall.@zone[2].name='guestlanfw'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].forward='REJECT'
firewall.@zone[2].network='guest_lan'
firewall.@zone[2].input='REJECT'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='guestlanfw'
firewall.@forwarding[1].dest='wan'
firewall.@rule[9]=rule
firewall.@rule[9].name='Guest-lan-dhcp'
firewall.@rule[9].proto='udp'
firewall.@rule[9].src='guestlanfw'
firewall.@rule[9].dest_port='67'
firewall.@rule[9].target='ACCEPT'
firewall.@rule[10]=rule
firewall.@rule[10].name='Guest-lan-dns'
firewall.@rule[10].src='guestlanfw'
firewall.@rule[10].dest_port='53'
firewall.@rule[10].target='ACCEPT'
firewall.@rule[11]=rule
firewall.@rule[11].name='Guest-block-all'
firewall.@rule[11].src='guestlanfw'
firewall.@rule[11].target='DROP'
In case you wanna see /etc/config/firewall, I backed them up
Locked out:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone
option name 'lan'
list network 'lan'
option input 'REJECT'
option output 'REJECT'
option forward 'REJECT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'guestlanfw'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest_lan'
option input 'REJECT'
config forwarding
option src 'guestlanfw'
option dest 'wan'
config rule
option name 'Guest-lan-dhcp'
list proto 'udp'
option src 'guestlanfw'
option dest_port '67'
option target 'ACCEPT'
config rule
option name 'Guest-lan-dns'
option src 'guestlanfw'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Guest-block-all'
option src 'guestlanfw'
option target 'DROP'
root@(none):/rom/root#
After using uci to set lan>wan back to ACCEPT:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'guestlanfw'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest_lan'
option input 'REJECT'
config forwarding
option src 'guestlanfw'
option dest 'wan'
config rule
option name 'Guest-lan-dhcp'
list proto 'udp'
option src 'guestlanfw'
option dest_port '67'
option target 'ACCEPT'
config rule
option name 'Guest-lan-dns'
option src 'guestlanfw'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Guest-block-all'
option src 'guestlanfw'
option target 'DROP'
You can always reset to default
We don't know your intentions
StepSis:
Changed firewall zone lan>wan , input,output,forward everything to reject and can't access router anymore xd ( I wanted to temp disable internet on lan while I'm testing something... )
This is because you disabled INPUT from LAN. Hence you couldn't input traffic to access your web GUI.
Do you mean /rom/etc/config/firewall?
I checked it but it has entries which I don't have in my current firewall
Maybe it's because firewall got updated in 22.02/22.03 version of openwrt? I've kept my settings for 3/4 versions already, maybe it's time to factory reset and start from scratch
Anyways... could setting all input/output/forward to REJECT have changed any of the rules? ( config rule from /etc/config/firewall )
Not sure what you think I meant; but I mean simply resting the whole device:
Failsafe mode, factory reset, and recovery mode OpenWrt offers several ways to “start over” with your router: * Failsafe mode is useful if you have lost control of your device, and it has become inaccessible, perhaps through a configuration...
I think this is the default file; but what you described/noted about it makes little sense.
Yes (that's exactly what altering settings should do).
Okay. Just keep a copy, you can backup your config from the web GUI before the reset.
Ty, I'll keep this in mind
But I'm still bit confused ...
uci set firewall.@zone[0].input='ACCEPT'
uci set firewall.@zone[0].output='ACCEPT'
uci set firewall.@zone[0].forward='ACCEPT'
did you mount the filesystem is r/w? If not, you're likely working on the ROM partition (which obviously can't be updated). You also need to commit your changes in UCI.
1 Like
I did xd ( I didn't know what mount_root does until you commented but I figured if it's in failsafe guide then it's probably good to use )
Anyways... I followed the advice and tried firewalling again - I've set forward to REJECT and output to REJECT but internet still remains o.o ( lan>wan zone )
Are you running normally (i.e. not in failsafe; booted with your normal config)? Even if it is not doing what you want, are you at least able to use the router normally?
StepSis
January 24, 2023, 5:00pm
10
Are you running normally (i.e. not in failsafe; booted with your normal config)? Even if it is not doing what you want, are you at least able to use the router normally?
Yes , back in the luci web interface
I already isued those 3 commands from above ,then uci commit firewall and reboot
I followed the advice and tried firewalling again - I've set forward to REJECT and output to REJECT but internet still remains o.o ( lan>wan zone )
Maybe I should reboot firewall for changes to take effect? I only pressed save and apply ( But then again back when I was locked out that was enough... And now I can't really take down the internet to test )
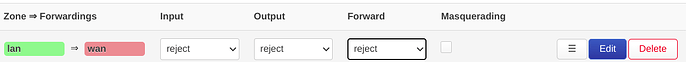
If you want to cut off internet acess from the LAN, simply remove the lan > wan forwarding
config forwarding
option src 'lan'
option dest 'wan'
1 Like
To stop Internet on LAN:
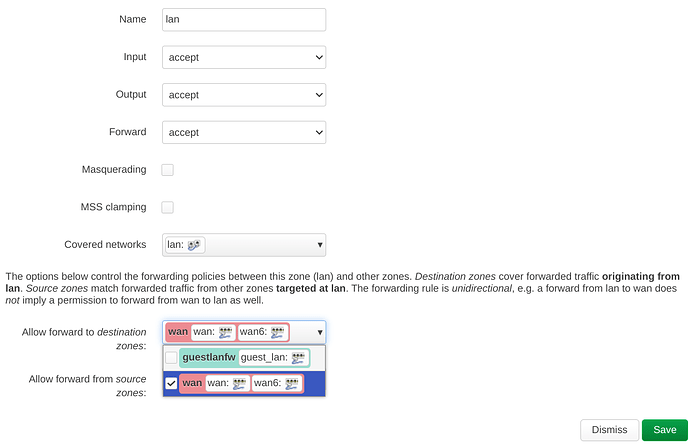
You click "Edit" on the LAN row (i.e. to edit the LAN zone)
Browse to "Allow forward to destination zones "; and
Uncheck WAN
(It seems like you were accidentally editing the FORWARD parameters between interfaces on LAN and not LAN-to-WAN forwarding.)
1 Like
StepSis
January 24, 2023, 5:12pm
13
Yeah this one
Ty I found what you're talking about
I don't know how to apply this without taking down firewall for a reset ( which would kill internet for evryone ? )
I showed you: Bad firewall got me locked out - #12 by lleachii
Excellent!
(Then just use the web GUI.)
Leave the lan zone as:
Then edit the lan zone and remove the "wan" zone from the "allow forward to" section.
1 Like
StepSis
January 24, 2023, 5:16pm
16
Thanks , I meant this one :
config forwarding
It's supposed to be changed in /etc/config/firewall ?
Anyways let me try via luci, thanks for all the help guys !
LuCI is just a front-end for the UCI commands that ultimately edit the text configuration files... it's all the same.
2 Likes
As @psherman noted, you can:
use the LuCI web GUI; or
the command line to edit the firewall file
In any case, you editing the same thing.
1 Like
StepSis
January 24, 2023, 5:20pm
19
Oh , so just changing the /etc/config/firewall would have it update firewall rules instantly?
I already managed to set it up via luci btw
1 Like
No, on command line, you must:
Save the file
Exit the file editor
Run /etc/init.d/firewall reload
(i.e. Save and Apply)
2 Likes
![]()