Hi,
I have Linksys WRT3200ACM running LEDE firmware released 05-18-2018.
My concern for this is all regarding the fact I'm using vpn, with provider who doesn't support IPv6.
I followed guides on NordVPN for setting it up, works great even for Netflix. And on all devices.
However, services like Netflix take longer to load because of it and some minor issues here and there such as Netflix eventually blocking it then I need to switch servers and all that gets annoying eventually.
I decided that my Amazon fire TV doesn't need to be connected through VPN as it's only an entertainment device and nothing 'sensitive'. I was trying to use vpn-policy-routing to allow my fire TV's IP address to bypass VPN and it worked. Since I had disabled IPv6 to prevent leak on all devices (did this by unticking 'bring up on boot' for wan6 interface). Netflix just results in no network connection error, acts as if it doesn't know I'm online. Other things work on the fire TV, and ipleak.net gets my real ip, but once I enable IPv6 then Netflix works and is bypassing VPN where all other devices are still going through VPN. (This way, all devices even ones on the VPN detect my real IPv6 address. This is the leak I'm talking about)
Mainly what I need to do is keep the VPN bypass enabled for fire TV, and allow IPv6 traffic on that device and only that device. As for some reason Netflix works if I send it through VPN with IPV6 disabled, or I bypass VPN with IPv6 enabled. I do not want VPN on fire TV anymore but do what Netflix working.
It's hard trying to explain this, as it's confusing me why it doesn't work like it should.
Any way to only allow IPv6 traffic for fire TV? (Making sure ALL current and future devices can't connect via IPv6 in order to prevent leak.)
Thank you 
Easiest would probably be make a separate vlan, and connect fire to that. see wiki for guest Network setup.
Hi,
I am not sure what a vlan is or how to configure it. I've done research on google, and cannot seem to find much even relating to my issue. I've already set up a guest Network, but not sure what use it would be in this case. I've already looked at lede-project.org main page under security section as to where I got the directions for setting it up.
So far extra I've tried creating new firewall rules, as well as wireless and linking them to the wan6 interface and new firewall rule, but sometimes resorted in disabling IPv6, other times remote device would get stuck 'obtaining up address's. So I've reverted those changes now, so I don't screw up further.
This sounds like it would be a very simple fix, as it's not uncommon for people to want only certain features for certain devices. I'm only wanting it for security, and been on this for over 2 months.
a "guest network" need not be just a network for your guests, add another "guest network" and make it a network for certain special devices, then connect those special devices to this new network, and treat them all uniformly.
a VLAN is just a way to differentiate between two sets of traffic traveling over the same medium. For example on a wire you can tag your traffic with a VLAN ID and then at the other end of the wire the device knows everything tagged with say VLAN 1 is associated to network 1 and everything tagged VLAN 2 is associated to network 2...
if you've already set up a guest network, most of those HOWTOs involve creating a different VLAN for the guest network, so you've probably done it already.
Just create a network, give it an ESSID like "myIoTDevices" and connect your Fire and a few other devices you want similar treatment for, to that. Then, don't route this network over your VPN... route it over WAN... that's basically it.
So if I got this right, if I created a new network routed over wan, then I would have to to enable Bring up on boot for wan6 then devices connected to this new network would be outside VPN, using both IPv4 and IPv6 where all other devices connected to my current network would only route through VPN with IPv6 disabled? Just doesn't sound like its sepcifically telling it not to use IPv6 on other devices.
And by doing it this way, would I skip using vpn-policy-routing?
I'll give it a test run and experiment since I seem to be understanding more of what I should do, rather than what I was doing (I'll back up first).
if you don't want ipv6 on one network, don't enable it on that network. So for your LAN just tell LEDE to turn off IPv6 (ipv6 assignment length = disabled in LUCI for the interface), but if you want IPv6 on your IoT/Guest network, do turn it on there.
Policy routing probably still needed, and don't disable WAN6.
Ok, I may have gone the wrong direction. When I originally wanted to just disable IPv6 to prevent VPN leak, I unticking bring up on boot for wan6 interface. Was this even the correct way to properly disable it? If I check it, and reboot then IPv6 is automatically enabled for all devices. I guess I will leave all that at default then, and try as you suggested.
I have just tried this, I went into LAN and disabled IPv6 assignment length then hit save and apply.
I added new network, selected guest as the interface, added encryption (WPA2-PSK) then hit save and apply.
I also enabled VPN policy routing with default settings except I added the name and up of the device (what it currently is). Then I rebooted router. Once back up, I went to connect fire TV to it and it connected to router, but informs me it can't reach the internet. Followed exact steps of the how to for guest Network creation. I see in the firewall that guestzone is out accepted only, input and forward are rejected. This is sent to wan. I assume that since it forwards to wan, guest would be the correct interface to have this network attached to. (I've tried selecting wan after this failed attempt of selecting guest, didn't change the result)
On a side note, I modified the file located in /etc/firewall.user to add code which rejects all internet traffic if VPN connection drops. I renamed the file temporarily and restarted firewall just to be sure this wasn't the cause, didn't seem to be so I renamed it back to what it was. (I thought it might be, if IP of fire TV changed when connecting it to new network. As if it did, the VPN policy routing would be set up with an invalid ip where it might be trying to connect to VPN that is not setup to do so on this guest network)
Am I just really missing something here?
I'm not sure of half the 'meanings' of some of these things as my skills in computers are far different than networking. I am glad I backed up though, saves me alot of trouble.
Thanks for your continued help, eventually I'll get it 
You're making progress.
disabling wan6 disables ipv6 for everything. You just want to disable for one specific sub-network, as you did:
Now, I'm not sure what this means:
Is this part of the LUCI gui? You want policy routing that does the following:
- If something comes in via LAN, policy route it to the VPN
- If something comes in via the Fire/IoT network, route it to WAN
- If something comes in via your other guest network.... Do whatever you want
I doubt you got that by "default settings" so you will need to improve the settings to set up that above policy.
Also:
Forward rejected is probably a major part of your issue. "output" is for packets generated by your router... forward is packets coming from your fire trying to get somewhere. You need that accepted.
Wouldn't it be easier to make 2 rules:
- One Allow Forwarding rule for the MAC or static IPv6 device in question
- Block forwarding by default; or an IPv6 Block rule for all other IPs in the Firewall Zone?
Most devices prefer ipv6 if they have it. If you're broadcasting router advertisements, your devices will get ipv6 addresses, and try to use them, if you're blocking their ipv6 they'll basically be disconnected from the internet for any site that uses ipv6, because they're going to try to use that, and be firewalled off..
If you want most of a network to not use IPV6 then you shouldn't advertise ipv6 on that network. If you want some devices to use IPv6 then you should put them on a separate VLAN where you do advertise... that's my thought at least.
I've been replying to you on this forum through email, forgot to mention something extra and can't find my reply here so I'll add.
The VPN policy routing I'm using allows me to specify an IP in lan that is allowed to bypass my VPN and allow internet via ISP directly. As I don't need it for services such as Netflix. When I said default settings, I went a head and left all settings of that software I installed default and only added name (Amazon Fire TV) and it's IP address and saved and enabled it.
With the part of the firewall guestzone I told you, I didn't manually create this. From lede-project told me the code to enter via ssh. I did so, and it created all that for me. I don't know much about the firewall, but I know what's its used for and it sounded like an issue which I why I mentioned it.
As for the VLAN you keep mentioning, only thing I see that relates to it is Switch tab in network section. I now know what it is, but not sure settings to change or add.
Can you upload network and wifi config, make sure to obscure wifi passwords.
Most guest Network tutorials will create a separate vlan, they look like eth0.4 for the vlan tagged 4 on eth0 interface.
Ok, I understand what your talking about now. That makes sense, but as for any additional WiFi access point I add, 2.4GHz or 5GHz no devices can connect successfully. Sometimes stuck at obtaining IP address, sometimes it connects to router but not internet. I've switched the settings plenty of times trying to figure it out, read other forums, FAQ, and wiki nothing is working. Even if I set up another network with EXACT settings of current one, the new one still gives me same issues. Makes me think something is very wrong. But even after factory reset, same issues. So I doubt is hardware related, or software. Probably my mistake, I just have to figure out what I'm missing. I entered an essid, used wan network, gave a password. That's all I modified as the wiki told me, but I just get issues with it.
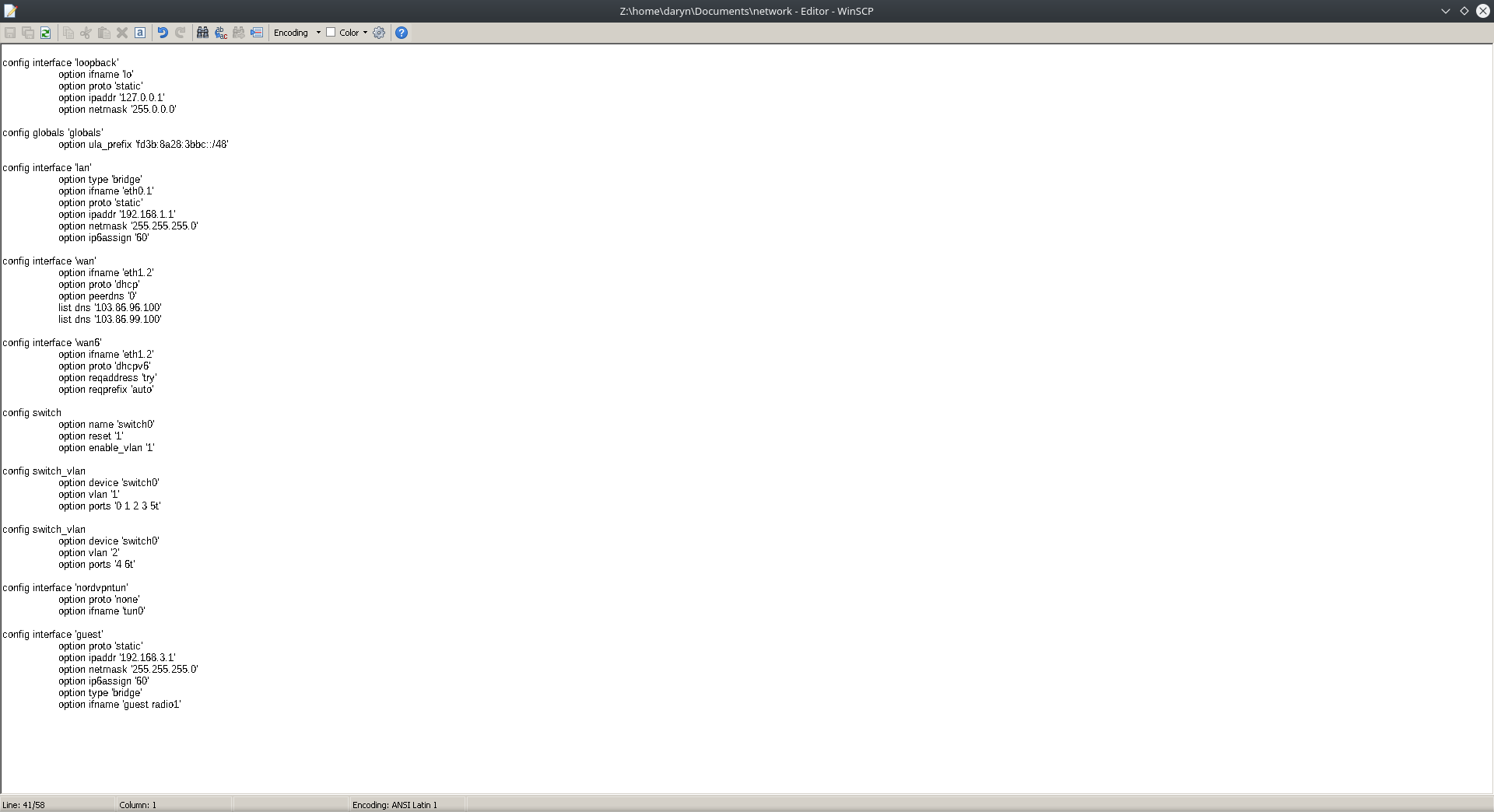
It seems I can only upload photo's, not the file it's self. I just opened it up after copying to desktop to remove the passwords for my 3 wireless networks, the wrest is all left alone as it is currently set up. I won't change anything until I hear back from you.
So far, progress is farther. I connected fire tv to new network and fire tv does not route through VPN, and IPv6 is accessible. My current issue is that IPv6 connectivity is not working for my original wireless network routed on the lan, now yes this is what I wanted so lan doesn't have IPv6, but I still want it working though just not enabled now. My VPN provider is in process of getting support for this protocol, and when they do I would like to revert these changes and have IPv6 on for every device. Wan6 is enabled, so is IPv6 assignment set to 60 in lan interface. I've only changed a few things from default vaules in firewall, under general settings I changed Forward from rejected to accept. I've also changed the guestzone Input/Forward both to accept. Those were needed to be without issues. The commands I got use via ssh:
NETWORKID=guest;FIREWALLZONE=guestzone;
uci batch <<EOF
set network.${NETWORKID}=interface
set network.${NETWORKID}.ifname=${NETWORKID}
set network.${NETWORKID}.proto=static
set network.${NETWORKID}.ipaddr=192.168.3.1
set network.${NETWORKID}.netmask=255.255.255.0
set network.${NETWORKID}.ip6assign='60'
set dhcp.${NETWORKID}=dhcp
set dhcp.${NETWORKID}.interface=${NETWORKID}
set dhcp.${NETWORKID}.start=100
set dhcp.${NETWORKID}.leasetime=12h
set dhcp.${NETWORKID}.limit=150
set dhcp.${NETWORKID}.dhcpv6=server
set dhcp.${NETWORKID}.ra=server
set firewall.${FIREWALLZONE}=zone
set firewall.${FIREWALLZONE}.name=${FIREWALLZONE}
set firewall.${FIREWALLZONE}.network=${NETWORKID}
set firewall.${FIREWALLZONE}.forward=REJECT
set firewall.${FIREWALLZONE}.output=ACCEPT
set firewall.${FIREWALLZONE}.input=REJECT
set firewall.${FIREWALLZONE}_fwd=forwarding
set firewall.${FIREWALLZONE}_fwd.src=${FIREWALLZONE}
set firewall.${FIREWALLZONE}_fwd.dest=wan
set firewall.${FIREWALLZONE}_dhcp=rule
set firewall.${FIREWALLZONE}_dhcp.name=${FIREWALLZONE}_DHCP
set firewall.${FIREWALLZONE}_dhcp.src=${FIREWALLZONE}
set firewall.${FIREWALLZONE}_dhcp.target=ACCEPT
set firewall.${FIREWALLZONE}_dhcp.proto=udp
set firewall.${FIREWALLZONE}_dhcp.dest_port=67-68
set firewall.${FIREWALLZONE}_dns=rule
set firewall.${FIREWALLZONE}_dns.name=${FIREWALLZONE}_DNS
set firewall.${FIREWALLZONE}_dns.src=${FIREWALLZONE}
set firewall.${FIREWALLZONE}_dns.target=ACCEPT
set firewall.${FIREWALLZONE}_dns.proto='tcp udp'
set firewall.${FIREWALLZONE}_dns.dest_port=53
EOF
uci commit
One more thing, checking ipleak.net on fire tv (firefox browser) has custom DNS i setup in WAN interface which points to my VPN. I used my VPN dns's only, to prevent DNS leak. So far, so good on the fire tv but this just makes me curious whether that would be a problem or not since i heard netflx and some servces can still block you from access because they assume you are on VPN. All I would lke to do is get IPv6 'WORKING', after I can do that, I will just disable it on lan and carry on my day...finally. I had a backup created before I started all of this, which i've restored plenty of times when I messed up. Wan6 enabled, when I switched lan interface settings for IPv6 assignment length to disabled, that also worked to disable it but when I went to switch it back to default vaule of 60, there was only 64 and disabled options. I set 64, and IPv6 wouldn't work anymore according to ipv6-test.com. When back to disabled, no difference. I opened the network config and changed it to 60 manually, saved and restarted network (/etc/init.d/network restart) there was still no IPv6 connectivity but the options were back for IPv6 assignment length (60 64 custom disable). I'm not sure what's up with that, like the only way to get IPv6 back on lan after disabling it was restoring my backup from before I messed with that option.
Sorry for long response, trying to give as much detail as possible, but i keep confusing myself 
Hi, it looks like you're making a lot of progress. I can't look at this carefully right now but let me mention some things that might be helpful:
-
IPv6 assignment should be 64 for each of your networks where you want to use ipv6, UNLESS you plan to have routers attached to this network and routing for sub-networks. Since I don't think that's the case, you want 64... If however you set 60 or something else like that, you may have "used up" your available prefixes, which is why you couldn't select 60. Set everything to 64 and reboot.
-
IPv6 on your LAN that you want routed over VPN won't be something you can test until you actually have a working ipv6 VPN. Even then you probably need your LAN to use an ipv6 prefix assigned BY YOUR VPN, I doubt you can route your ISP's prefix down your VPN tunnel.
-
You can turn off the VPN and the policy routing, and test your ipv6 on your LAN, if that works, then turn off prefixes, and turn on your VPN+policy route and just wait until later.
-
If your VPN provider provides an IPv6 prefix, you'll potentially want to advertise that on your LAN, at that point in time come back and have someone help you specifically with that problem. What you'll want there is to advertise the prefix only from the VPN not from the WAN6. I honestly don't know how to set that up in OpenWRT off the top of my head, it usually advertises all available prefixes.
At the moment, if you turn off VPN and policy routing, and have 64 set for IPv6 on LAN and the Fire network, do you get working ipv6 everywhere? if not, what happens?
IPv6 has always worked while I had vpn active, the problem was it was causing me an IPv6 leak. E.g would be that IPv4 would display random ISP, IP & location but IPv6 displayed my ISP, My real IP, & My real location. SO anyone can still track me, or read data coming from IPv6. That is why i disabled it in the first place. Now for testing this, i did disable vpn & policy routing as well as my modified firewall.user file. I sitll get IPv4 connectivity but not IPv6 on the lan. The fire tv device bypasses my vpn, and it does have IPv6. Can't get it to work on the lan as it should, I dont want it enabled I just want to know its working for when the support does come out for it.
As for DNS, I dont understand that. I unchecked Use advertised dns servers by peers in wan interface and added the 2 from my VPN a while back. I know that wan is shared between all wireless networks, so i understand why my firetv picks them up. I see similar option under LAN for custom DNS, tried adding them their and removing from wan but still get dns leak. As long as IPv6 is disabled on lan, and DNS are added to wan then their is no leak. Know why this might be?
I assume policy routing was not sending your packets to your VPN, but instead out your WAN6. If it DID go to your VPN, then they'd probably drop them on the floor.
Were you advertising a /64 on the LAN? did your test machine have an ipv6 address? If so, then this means something is blocking your packets, if not... well one question is how big is the prefix set your ISP allows you? Some ISPs just give you one /64 prefix and then you can only have one subnet with ipv6.
ATT gives me a /60 so I can have 4 bits of prefix: 16 subnets, unfortunately their ISP device only gives it out in terms of one /64 at a time, so I just request 2 (one for LAN and one for guest).
Lots of companies are handing out /56 prefixes, and then you can have 256 subnets.
So you need to figure out what's going on in terms of whether you have more than 1 prefix available.
Yes, i selected 64 for assignment length as you said (did this for both guest & lan interface) and its working for guest but not lan. I still have time though to figure this out.
I am not sure what my ISP offers as for prefix (ComCast).
I was just about to edit my previous reply, as I sad somethng wasn't quite true. I thought it was, but found out I did something wrong. For the Dns, once i enabled wan6 and just disabled IPv6 assignment on the lan as you said I immediately started gettings dns leaks. If I switch off wan6, and no leaks. So i just re-connected wan6, disabled IPv6 assignment length in lan then add custom dns server to both wan and wan6. Now, no leaks. The only issue is that fire tv picks them up on new network. I figured this would happen as wan & wan6 are linked to guest interface which is lined to the wireless network. Would this be a problem at all? This is really my only last concern, then I could consider this solved. If possible to use custom dns with lan only but preventing any leaks that would be preferred.



