I personally wouldn't go through the trouble of setting static IPs on each device - static DHCP is much better approach I find (whether to give only in a specific range, or specific IP)... That's a significant lift, and I'm not a fan of hardcoding things like that on edge devices. For example, last year I changed my IP address range and subnet. This was more or less effortless as the changes took place only on routing devices.
Here's my setup which may help. I would give it a try... I can't imagine this adding much load on your router to be honest.
As I run miniupnpd (UPNP), I also drop the UPNP open requests. This shouldn't be needed given that the traffic is dropped, but I have included it:
/etc/config/firewall - also configurable in Luci's firewall page under "traffic rules" tab
config rule
option src 'lan'
option dest 'wan'
option target 'REJECT'
list src_ip '192.168.40.0/25'
option name 'IoT No Internet (192.168.40.0 to 127)'
config redirect
option target 'DNAT'
option src 'lan'
option src_dport '53'
option name 'DNS Intercept Requests'
option reflection '0'
option dest 'wan'
/etc/config/upnpd - also configurable in Luci's upnp app.
config perm_rule
option ext_ports '0-65535'
option int_ports '0-65535'
option action 'deny'
option comment 'Deny IoT (192.168.40.0 to 127)'
option int_addr '192.168.40.0/25'
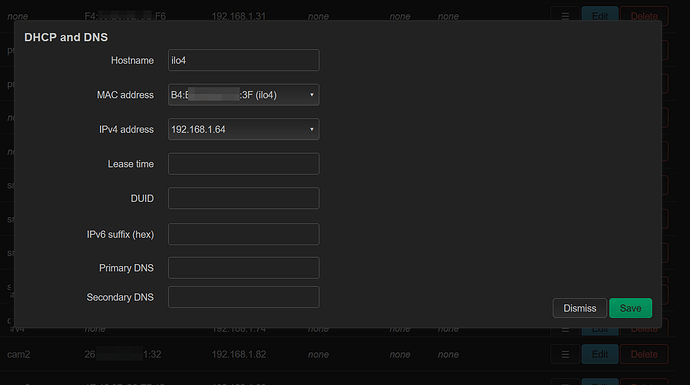
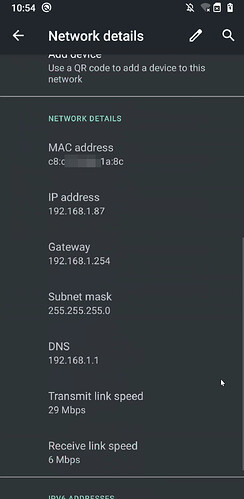
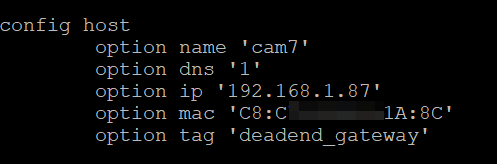
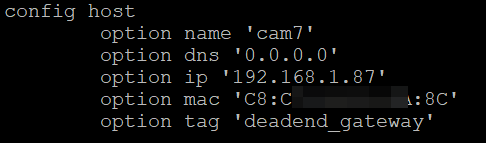
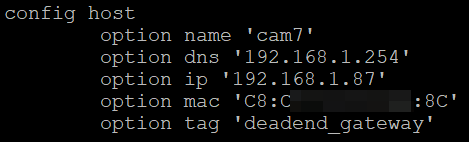
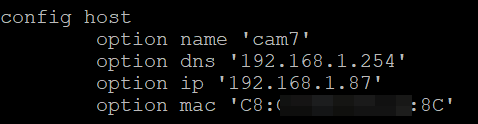
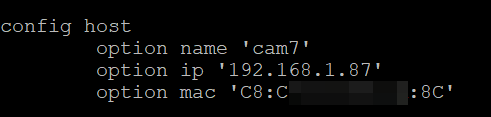
Below are two examples. In first, I let an IP be provided to the device within the "allowed/reserved/known" range based on the tagging. In the second, I have provided a specific IP address in this no internet range, but outside the DHCP IPs in the range.
The reason for the static DHCP is that after a reboot some devices don't renew their IPs fast enough, and so can be unreachable (depends on the device).
/etc/config/dhcp
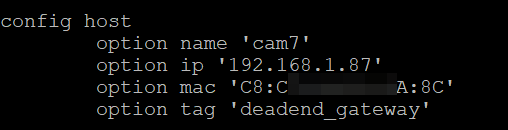
config host
option name 'Device 1'
option dns '1'
option mac '34:EA:XX:XX:XX:XX'
option tag 'iot-no-internet'
config host
option name 'cam-garage'
option dns '1'
option mac 'E0:B9:XX:XX:XX:XX'
option tag 'iot-no-internet'
option ip '192.168.40.10'
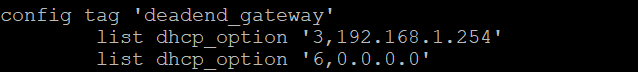
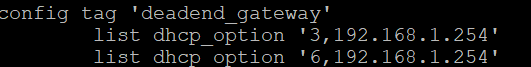
Also within dhcp config file (in Luci, it's under the interface's DHCP Server tab, except for the dhcp_option, which has to be hand typed in the config file). Note that the dhcp_option is actually not needed for this example. But I left it in because I use the "kids" tag to send the kids to a pihole DNS instead of the openwrt DNS:
config dhcp 'lan'
option interface 'lan'
option dhcpv4 'server'
option start '522'
option limit '191'
option leasetime '3h'
list dhcp_option 'tag:kids,option:dns-server,192.168.41.11,192.168.41.1'
Last thing for the /etc/config/dhcp configuration file, the below option must be added,
config dnsmasq
option confdir '/etc/dnsmasq.d'
Now moving over to /etc/dnsmasq.d directory, I have created a text file called additional.conf which simply contains this line; You could add additional line for each tag). This tells dnsmasq to serve only this range for the given tag:
dhcp-range=tag:iot-no-internet,192.168.40.20,192.168.40.127,3h
I think that's it... Nothing to do on the devices.