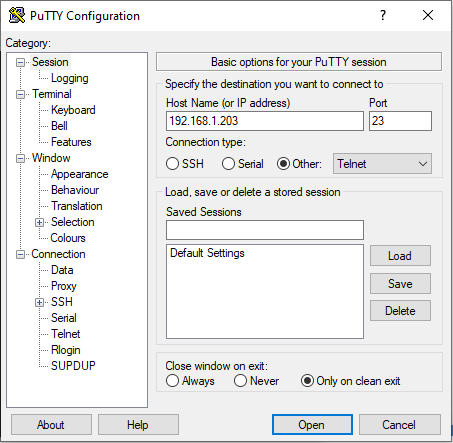
Thanks
Interesting! Im not sure I fully understand, but I have now backed up the config-file. and It looks like this:
{
"X_ZYXEL_LoginCfg":{
"LoginGroupConfigurable":true,
"LogGp":[
{
"emptyIns":true
},
{
"GP_Privilege":"_encryp1_qmmb5+mF+SO8zu7NkkJcFQSxAqYcK6zDnkf0NVLl5uQ=",
"Account":[
{
"Enabled":true,
"Username":"admin",
"Password":"_encryp1_IyDCb0j5PofD2p9VkZJvcg==",
"PasswordHash":"",
"Privilege":"_encryp1_e8nx0GtPTMxfyyEz4qvZWg==",
"DotChangeDefPwd":true,
"ThemeColor":"green",
"RemoteAccessPrivilege":"LAN",
"DefaultPassword":"_encryp1_1wJBVNirK9OUdgWa4pKP0g==",
"OldDefaultPassword":"_encryp1_ZaV\/Xl0K58TAU51F0BT9pA==",
"EnableQuickStart":false,
"DefaultGuiPassword":"",
"ResetDefaultPassword":false,
"shadow":"admin:$6$5QB0c\/sFjL9G4kLJ$3f\/cO00LmF74zj5Cn0bRovMgd\/C\/buFtyjgbLSoizJBPeno1uIcKmnRz6eYOEioiLG.G0a0FDm0uq.pnpdrh61:18932::::::\n",
"smbpasswd":"",
"ConfigAccountFromWAN":false,
"DefPwLength":8,
"AccountRetryTime":3,
"AccountIdleTime":300,
"AccountLockTime":300,
"ShowSkipBtnInChgDefPwdPage":true,
"AutoGenPwdBySn":false,
"AutoShowQuickStart":false,
"Stored":"",
"Salt":"",
"RoleList":"",
"CardOrder":"",
"CardHide":"",
"HiddenPage":"",
"SshKeyBaseAuthPublicKey":"",
"Modified":false
},
{
"Enabled":true,
"EnableQuickStart":true,
"Username":"support",
"Password":"_encryp1_IyDCb0j5PofD2p9VkZJvcg==",
"PasswordHash":"",
"Privilege":"_encryp1_e8nx0GtPTMxfyyEz4qvZWg==",
"DotChangeDefPwd":true,
"ThemeColor":"green",
"RemoteAccessPrivilege":"LAN",
"DefaultPassword":"_encryp1_IyDCb0j5PofD2p9VkZJvcg==",
"DefaultGuiPassword":"",
"ResetDefaultPassword":false,
"shadow":"support:$6$qeFJGj8yPX1Suubw$ios12\/\/tva2\/wGFQ8MABXdnYIEfBCff1Evkq4snM77mIm0gU5RiZjsaGEMselYPBgnvVRf46louoIjJYfzUQU\/:18932::::::\n",
"smbpasswd":"",
"ConfigAccountFromWAN":false,
"DefPwLength":8,
"AccountRetryTime":3,
"AccountIdleTime":300,
"AccountLockTime":300,
"ShowSkipBtnInChgDefPwdPage":false,
"AutoGenPwdBySn":false,
"AutoShowQuickStart":false,
"Stored":"",
"Salt":"",
"RoleList":"",
"OldDefaultPassword":"",
"CardOrder":"",
"CardHide":"",
"HiddenPage":"",
"SshKeyBaseAuthPublicKey":"",
"Modified":false
}
]
},
{
"GP_Privilege":"_encryp1_Gv\/qT4N4GHVNjRHXjXu6QQ==",
"Account":[
]
}
],
"MaxiumLoginAccountNumber":20
},
"X_ZYXEL_Change_Icon_Name":[
]
}
--
Where/what should be changed in it to get root-access?
Thanks.
![]()