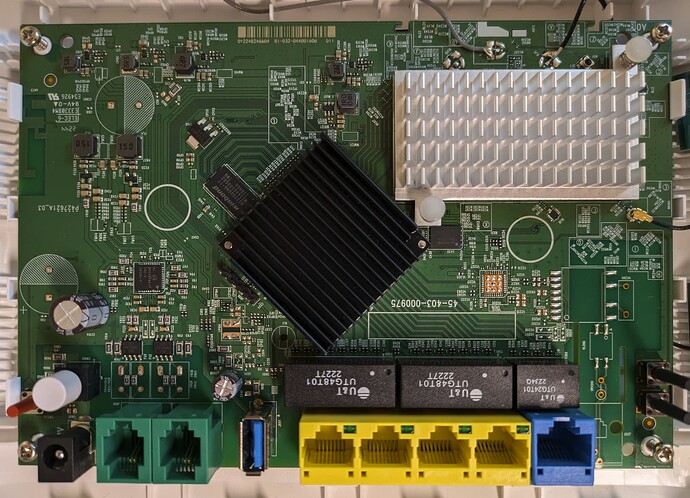
These are turktelekom's rebranded devices with Wifi6. They are capable of 1000mbits of internet easily. They look exactly similiar to those of VMG3625, although no DSL ports. Only WAN. I assume these are Econet maybe. But I wish not. Should I open it to see what CPU does it use? I can dump serials here.
I have similar one from o2.
Ex330x.
I do not use it, because its trimmed fw with ztr-86 or so and no openwrt on it.
Its ax1800 with 4gbe lan and 1 gbe wan. It has usb port too.
It actually works great tho. 1gbps speed on wifi is quite possible. It doesnt run openwrt? Interesting.
How you upgraded it to openwrt? I have it at stock fw.
It's currently not a supported device.
Thats why asking ![]()
Simillar devices are supported
Is it possible some day will be openwrt supported?
I didn't. I meant the stock firmware is actually good.
Sure, if you put in the time...
Dont say it. Its econet, its impossible to openwrt it...
OP says "maybe", no way of knowing for sure, until you open one up, or get console access.
Some more info..
It's possible to get root password and gain terminal access using this method described here to extract the root password to a USB-stick. Worked with firmware V5.50(ABVY.3.4)C0. Seems like it is patched in 5.50(ABVY.4)C0.
https://bandaancha.eu/foros/zyxel-ex3301-t0-obtencion-contrasena-1749511 (translate from Spanish->English)
# cat /proc/cpuinfo
system type : EcoNet EN751627 SOC
# cat /proc/meminfo
MemTotal: 227344 kB
# uname -a
Linux EX3301-T0 3.18.21 #1 SMP Wed Nov 23 11:38:34 CST 2022 mips GNU/Linux
# cat /proc/mtd
dev: size erasesize name
mtd0: 00040000 00020000 "bootloader"
mtd1: 00040000 00020000 "romfile"
mtd2: 003bf1d3 00020000 "kernel"
mtd3: 015c0004 00020000 "rootfs"
mtd4: 02800000 00020000 "tclinux"
mtd5: 003beeb0 00020000 "kernel_slave"
mtd6: 015c0004 00020000 "rootfs_slave"
mtd7: 02620000 00020000 "tclinux_slave"
mtd8: 00100000 00020000 "wwan"
mtd9: 00400000 00020000 "data"
mtd10: 00100000 00020000 "rom-d"
mtd11: 02000000 00020000 "misc"
mtd12: 00080000 00020000 "Factory"
mtd13: 000c0000 00020000 "reservearea"
# cat /proc/partitions
major minor #blocks name
31 0 256 mtdblock0
31 1 256 mtdblock1
31 2 3836 mtdblock2
31 3 22272 mtdblock3
31 4 40960 mtdblock4
31 5 3835 mtdblock5
31 6 22272 mtdblock6
31 7 39040 mtdblock7
31 8 1024 mtdblock8
31 9 4096 mtdblock9
31 10 1024 mtdblock10
31 11 32768 mtdblock11
31 12 512 mtdblock12
31 13 768 mtdblock13
It's also possible to change from ISP specific firmware to Zyxel generic/global firmware by disabling model check and firmware ID check as described here: https://community.zyxel.com/en/discussion/11497/xmg3927-b50a-firmware-version
It's also possible to go from a newer firmware to an older vulnerable firmware using this method. Was able to go from 5.50(ABVY.4)C0 back to V5.50(ABVY.3.4)C0.
1. gain ssh admin access
2. run commands in ssh
zycli
zycli modelcheck
zycli modelcheck show (Result : "ret:0")
zycli modelcheck off
zycli modelcheck show (Result : "ret:-17")
zycli fwidcheck show (Result : "ret:0")
zycli fwidcheck off
zycli fwidcheck show (Result : "ret:-17")
exit
3. update FW from web UI
Even though I am on firmware 3.1 (downgraded from ISP 5.4 to 4.2 stock and then to 3.1 stock), the method to obtain the root pass with the USB stick and the script didn't work. Also tried 3 different methods too but had no luck either (python script based on s/n, python script based on Session and AESKey to descrypt config file, Hack GPON method). Any other possible method to obtain the root pass without knowing the supervisor password either?
P.S. VMG8623-T50B is pretty much the same platform (same SoC, RAM, flash chip, etc.) other than the wireless. I have root access there (via the python script based on s/n) and obtained copies of the 12 mtd blocks.