Since there is very little up to date information about connecting to Yggdrasil network I decided to share my experience on OpenWrt 23.05.5.
Installation: opkg update; opkg install luci-proto-yggdrasil yggdrasil-jumper ( yggdrasil-jumper is optional).
It should be noted that I had to reboot my router to see new type of network interface.
Configuration: Network → Interfaces → Add new interface..., choose Yggdrasil Network as new interface's protocol and give it some name (ygg in my case).
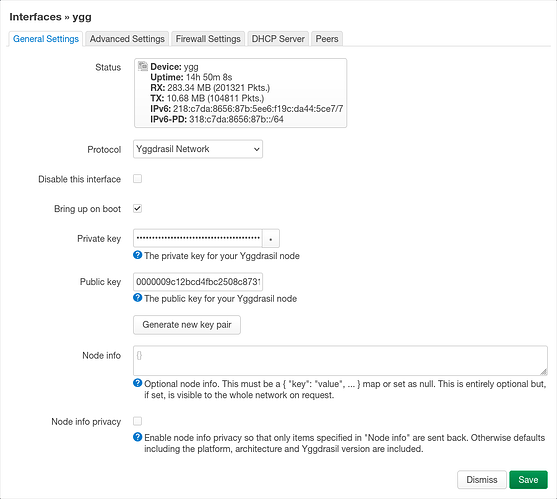
Now is the time to setup new interface. Press Generate new key pair in General Settings tab:
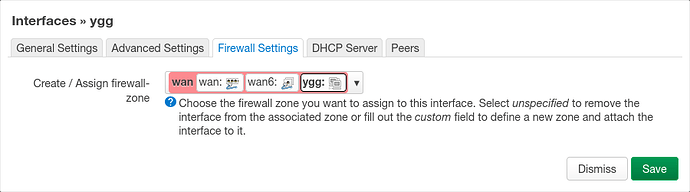
Assign firewall zone in Firewall Settings:
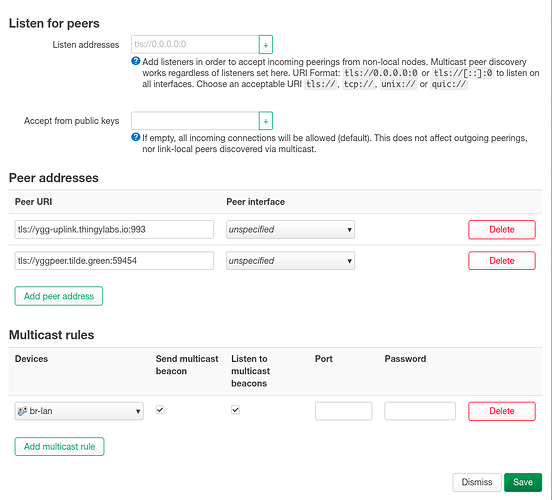
And add several peers (sure, if you want to connect to public playground) from https://github.com/yggdrasil-network/public-peers (choose geographically closest to you). Enabling multicast on br-lan may be a useful option too if you want other nodes in your LAN to autoconnect without setting up peers manually:
Now press Save and restart ygg interface (I don't know why but new settings were not applied immediately after saving).
After that all your local network devices should receive new IPv6 address from the prefix delegated to Yggdrasil without any additional configuration. That's it.
Curious one can configure Alfis DNS, lazy one can leave it as it is and use ygg.at domain instead of ygg. For example domain rutracker.ygg also can be accessed as rutracker.ygg.at.
Map of Yggdrasil: http://[21e:e795:8e82:a9e2:ff48:952d:55f2:f0bb]/.
Torrent tracker I tried: http://[316:c51a:62a3:8b9::5]/announce.
Out proxy (just for testing purposes): 324:71e:281a:9ed3::fa11 port 1080 (SOCKS5) and port 3128 (HTTP/HTTPS).
EDIT (early 2025): Added yggdrasil-jumper to installation packages.