I'm resurrecting this because I feel I'm almost there but not sure I'm doing this correctly as I still can't get it working. After discovering my device does not use DSA, I proceeded to create VLANS using swconfig. I completely started over, fresh install with:
- wpad-basic-wolfssl removed and hostapd-wolfssl installed
- firewall disabled & rules deleted & in/out/fwd=accept, dnsmasq disabled and odhcpd disabled
- /etc/resolv.conf is a physical file instead of symlink containing nameserver 192.168.1.254 (FW)
- patch from beginning of thread to get OpenWrt to send MAC address for authentication to RADIUS
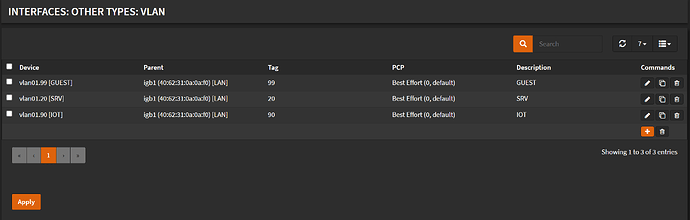
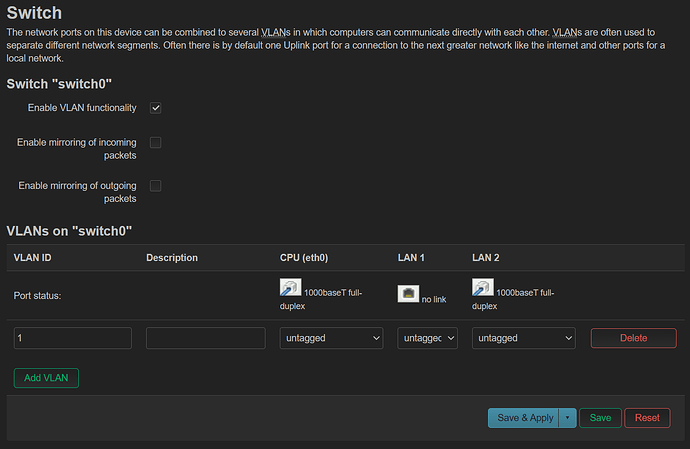
- aruba switch config remains the same. dhcp snooping enabled on all vlans, port1+5 marked trusted and port 5 enabled for MAC authentication (PAP)
- MAC address configured in FreeREADIUS on FW, successfully authenticates and VLAN99 (configured) is passed back to OpenWrt
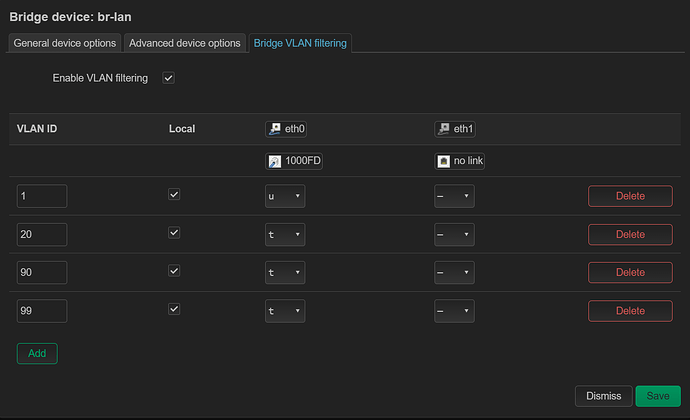
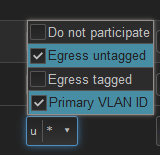
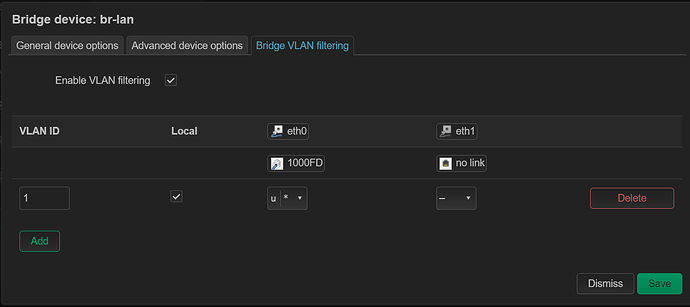
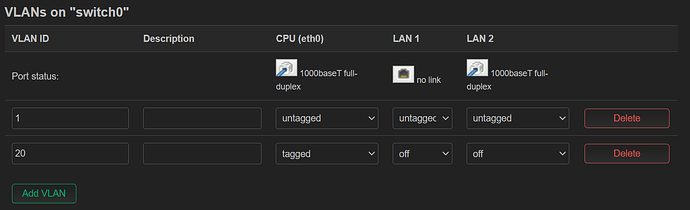
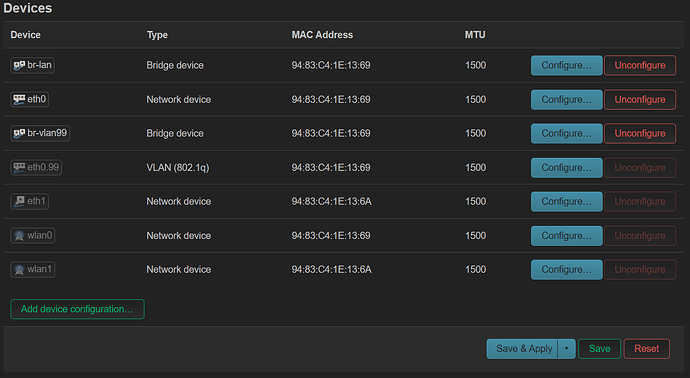
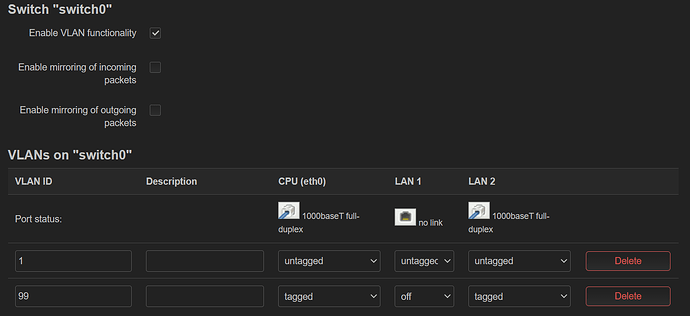
I created a VLAN bridge device called br-vlan backed by eth0 (cpu) and then added a VLAN device with tag 99 and then an unmanaged interface called VLAN99 backed by br-vlan.99 and then in Switch config, added VLAN 99 being tagged on eth0 (cpu) and untagged on all other ports. In Wireless, I set the network on 2.4/5GHz to be VLAN99
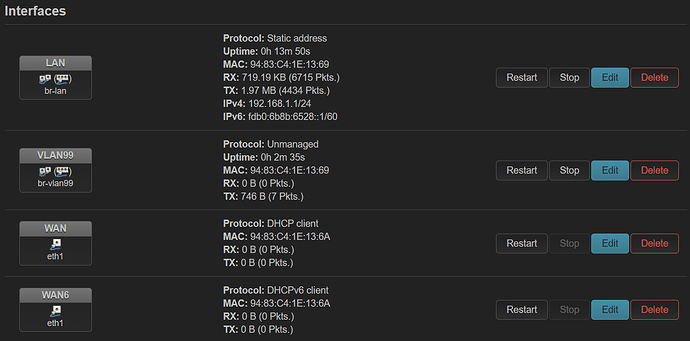
This nets me network devices br-vlan, br-vlan.99 and eth0.99 -- when connecting with my phone to the SSID, I authenticate successfully, OpenWrt recognizes the client is supposed to be on VLAN 99 (via hostapd) spins up wlan1.99 and the phone sits there waiting for DHCP which never happens and disconnects from SSID. On the OPNSense router I have VLAN 99 configured and a DHCP scope targeting the VLAN for 192.168.99.100-200
EDIT: If I configure my phone MAC to VLAN 1 in FreeRADIUS, I can connect successfully to VLAN 1 over wireless
Using logread, I can see the transaction happen:
Sun Mar 5 20:42:12 2023 daemon.info hostapd: wlan1: STA 11:22:33:44:55:66 RADIUS: VLAN ID 99
Sun Mar 5 20:42:12 2023 daemon.err hostapd: VLAN: vlan_add: ADD_VLAN_CMD failed for br-vlan: File exists
Sun Mar 5 20:42:12 2023 kern.info kernel: [ 1653.106987] br-vlan99: port 1(br-vlan.99) entered blocking state
Sun Mar 5 20:42:12 2023 kern.info kernel: [ 1653.107045] br-vlan99: port 1(br-vlan.99) entered disabled state
Sun Mar 5 20:42:12 2023 kern.info kernel: [ 1653.112864] device br-vlan.99 entered promiscuous mode
Sun Mar 5 20:42:12 2023 kern.info kernel: [ 1653.118089] device br-vlan entered promiscuous mode
Sun Mar 5 20:42:12 2023 kern.info kernel: [ 1653.124829] br-vlan99: port 2(wlan1.99) entered blocking state
Sun Mar 5 20:42:12 2023 kern.info kernel: [ 1653.127811] br-vlan99: port 2(wlan1.99) entered disabled state
Sun Mar 5 20:42:12 2023 kern.info kernel: [ 1653.134425] device wlan1.99 entered promiscuous mode
Sun Mar 5 20:42:12 2023 kern.info kernel: [ 1653.139974] br-vlan99: port 2(wlan1.99) entered blocking state
Sun Mar 5 20:42:12 2023 kern.info kernel: [ 1653.144813] br-vlan99: port 2(wlan1.99) entered forwarding state
Sun Mar 5 20:42:12 2023 daemon.info hostapd: wlan1: STA 11:22:33:44:55:66 IEEE 802.11: authenticated
Sun Mar 5 20:42:12 2023 daemon.info hostapd: wlan1: STA 11:22:33:44:55:66 IEEE 802.11: associated (aid 1)
Sun Mar 5 20:42:12 2023 daemon.notice hostapd: wlan1: AP-STA-CONNECTED 11:22:33:44:55:66
Sun Mar 5 20:42:12 2023 daemon.info hostapd: wlan1: STA 11:22:33:44:55:66 RADIUS: starting accounting session 8407B7890598D480
Sun Mar 5 20:42:12 2023 daemon.info hostapd: wlan1: STA 11:22:33:44:55:66 WPA: pairwise key handshake completed (RSN)
Sun Mar 5 20:42:12 2023 daemon.notice hostapd: wlan1: EAPOL-4WAY-HS-COMPLETED 11:22:33:44:55:66
Sun Mar 5 20:42:30 2023 daemon.notice hostapd: wlan1: AP-STA-DISCONNECTED 11:22:33:44:55:66
Sun Mar 5 20:42:30 2023 daemon.info hostapd: wlan1: STA 11:22:33:44:55:66 IEEE 802.11: disassociated
Sun Mar 5 20:42:31 2023 daemon.info hostapd: wlan1: STA 11:22:33:44:55:66 IEEE 802.11: deauthenticated due to inactivity (timer DEAUTH/REMOVE)
Sun Mar 5 20:42:31 2023 kern.info kernel: [ 1672.612508] br-vlan99: port 2(wlan1.99) entered disabled state
Sun Mar 5 20:42:31 2023 kern.info kernel: [ 1672.674655] device wlan1.99 left promiscuous mode
Sun Mar 5 20:42:31 2023 kern.info kernel: [ 1672.674995] br-vlan99: port 2(wlan1.99) entered disabled state
Sun Mar 5 20:42:31 2023 daemon.err hostapd: VLAN: br_delif: Failure determining interface index for 'wlan1.99'
Sun Mar 5 20:42:31 2023 kern.info kernel: [ 1672.858341] device br-vlan.99 left promiscuous mode
Sun Mar 5 20:42:31 2023 kern.info kernel: [ 1672.858395] device br-vlan left promiscuous mode
Sun Mar 5 20:42:31 2023 kern.info kernel: [ 1672.862583] br-vlan99: port 1(br-vlan.99) entered disabled state
Here is my /etc/config/firewall:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option synflood_protect '1'
Here is my /etc/config/network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb0:6b8b:6528::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.1.254'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 3 4'
option vid '1'
config device
option name 'eth0'
config device
option type 'bridge'
option name 'br-vlan'
list ports 'eth0'
option bridge_empty '1'
config device
option type '8021q'
option ifname 'br-vlan'
option vid '99'
option name 'br-vlan.99'
config interface 'VLAN99'
option proto 'none'
option device 'br-vlan.99'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t'
option vid '99'
Here is my /etc/config/wireless:
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/soc/a000000.wifi'
option channel '1'
option band '2g'
option htmode 'HT20'
option country 'CA'
option cell_density '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt'
option key 'EDCBA7568'
option encryption 'psk2+ccmp'
option macfilter 'radius'
option auth_server '192.168.1.254'
option auth_secret '<redacted>'
option auth_port '1812'
option dynamic_vlan '2'
option vlan_tagged_interface 'br-vlan'
option vlan_naming '1'
option vlan_bridge 'br-vlan'
option rsn_preauth '1'
option network 'VLAN99'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/soc/a800000.wifi'
option channel '36'
option band '5g'
option htmode 'VHT80'
option country 'CA'
option cell_density '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'psk2+ccmp'
option key 'EDCBA7568'
option macfilter 'radius'
option auth_server '192.168.1.254'
option auth_secret '<redacted>'
option auth_port '1812'
option dynamic_vlan '2'
option vlan_tagged_interface 'br-vlan'
option vlan_naming '1'
option vlan_bridge 'br-vlan'
option rsn_preauth '1'
option network 'VLAN99'
On the FreeRADIUS server:
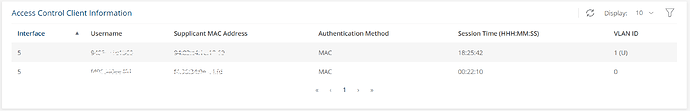
Sun Mar 5 19:31:01 2023 : Auth: (34) Login OK: [112233445566/112233445566] (from client OpenWRT port 0 cli 11-22-33-44-55-66)
Sun Mar 5 20:06:57 2023 : Auth: (36) Login OK: [778899001122/778899001122] (from client SWITCH port 5 cli 77-88-99-00-11-22)
The only thing I notice here other than successful authentication is that OpenWrt is passing port 0 (it's in port 5 physically on the switch) and the 2nd MAC address is OpenWrt LAN (untagged 1) and I can see in the switch interface it's successfully authenticated to VLAN 1 (which is what I have this MAC configured to in FreeRADIUS where I want it.)
Now I'm totally stuck as I've run out of ideas on how to troubleshoot this.
![]()