My port mappings don't work properly, I can't understand what I'm doing wrong with OpenWrt.
All services work correctly when access to the server is without having to go through the router, that is, connection to a network interface (10.10.10.1) of the server.
I have apache listening on ports 80 443 444 and I have an ftp server listening on ports 21 22 990.
I think something is not right, but I have no idea what it can be, I believe that the firewall does not handle the opening of ports, but I am not an expert in the networks.
The symptoms are as follows:
Access to the web server via http: 80, sometimes the page loads completely, in other cases no, I disable the cache in the browser, so it loads everything every time.
I do this tests from another ip of the same ISP, but I have also made http and https access from the onion network with similar results.
The certificate is 14 days to expire and is from Let's Encrypt.
Access to the web server via http: 443 generates errors, in Chrome I get the error ERR_SSL_BAD_RECORD_MAC_ALERT, in Firefox I get the errorSSL_ERROR_BAD_MAC_ALERT, in Brave I get the error ERR_SSL_VERSION_OR_CIPHER_MISMATCH
Access to the webdav with WinSCP also fails, it is possible to login, but when you wait for a list of files and directories the connection is interrupted.
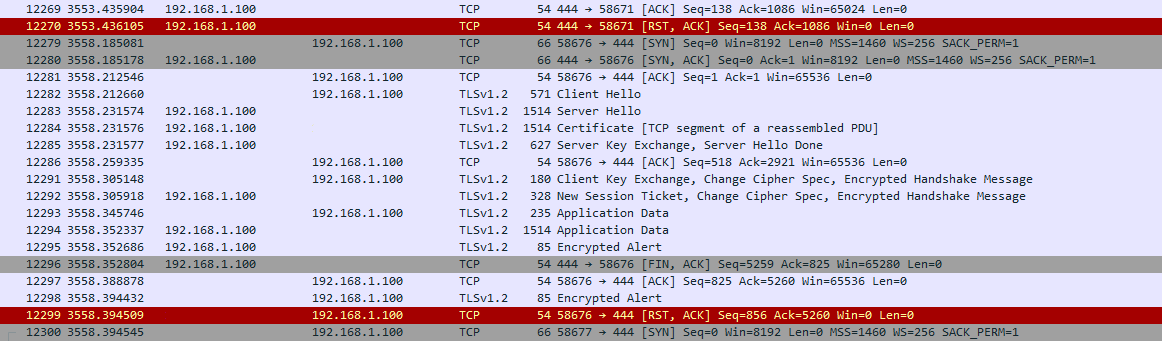
I have Wireshark on the server, checking the layout, you can see the following in the image:
There were moments that seemed to work, via webdav. I managed to transfer about 500 MiB.
I believed that the problem was generated, because after creating the rules, I did not run service firewall reload, service firewall restart, however this morning the connectivity problem reappeared and the connections are interrupted.
My Port Forwards configuration active in OpenWrt, generated with LuCI
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option src_dport '20-22'
option dest_ip '192.168.1.100'
option dest_port '20-22'
option name 'Forward-20:22'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option src_dport '80'
option dest_ip '192.168.1.100'
option dest_port '80'
option reflection '0'
option name 'Forward-80'
config redirect
option target 'DNAT'
option src 'wan'
option proto 'tcp'
option dest_ip '192.168.1.100'
option name 'Forward-443'
option dest 'lan'
option src_dport '443'
option dest_port '443'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option src_dport '444'
option dest_ip '192.168.1.100'
option dest_port '444'
option name 'Forward-444'
config redirect
option target 'DNAT'
option src 'wan'
option proto 'tcp'
option dest_ip '192.168.1.100'
option dest_port '990'
option name 'Forward-990'
option src_dport '990'
option dest 'lan'
Greeting
Sorry, English is not my native language.