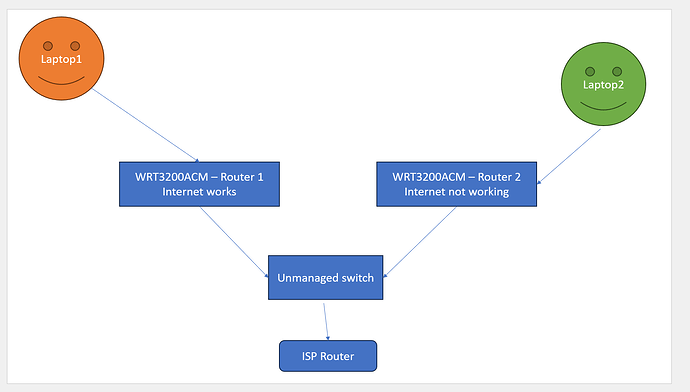
Trying to install openwrt on WRT3200acm (router2), i am using a backup of config from another openwrt wrt3200acm (router 1) which is identical in hardware. For unknown reason i cant connect to internet even when i disable openvpn and wireguard config adn reboot. Both routers are on the same network, is that an issue?
Please can someone help me
My config is as below
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.162",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 1 (v7l)",
"model": "Linksys WRT3200ACM",
"board_name": "linksys,wrt3200acm",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.4",
"revision": "r24012-d8dd03c46f",
"target": "mvebu/cortexa9",
"description": "OpenWrt 23.05.4 r24012-d8dd03c46f"
}
}
root@OpenWrt:~#
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb6:f6e7:56f8::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'wan'
option macaddr '62:38:e0:b7:c9:10'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option peerdns '0'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'nordvpntun'
option proto 'none'
option device 'tun0'
option disabled '1'
option auto '0'
config interface 'wg2'
option proto 'wireguard'
option private_key '********'
list addresses '10.5.0.2'
option mtu '1499'
list dns '103.86.96.100'
list dns '103.86.99.100'
option disabled '1'
option auto '0'
config wireguard_wg2
option description 'us8103.nordvpn.com'
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '185.247.70.67'
option endpoint_port '51820'
option persistent_keepalive '25'
option public_key '**********'
config wireguard_wg2
option description '185.255.130.149'
list allowed_ips '0.0.0.0/0'
option endpoint_host '185.255.130.149'
option endpoint_port '51820'
option persistent_keepalive '25'
option public_key '*********'
option disabled '1'
config wireguard_wg2
option description 'us9157'
option public_key '*******************'
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '2.56.190.73'
option endpoint_port '51820'
option persistent_keepalive '25'
option disabled '1'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpnfirewall'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'nordvpntun'
config forwarding
option src 'lan'
option dest 'vpnfirewall'
config zone
option name 'wgfirewall'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wg2'
config forwarding
option src 'lan'
option dest 'wgfirewall'
root@OpenWrt:~# ip ro
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
root@OpenWrt:~#