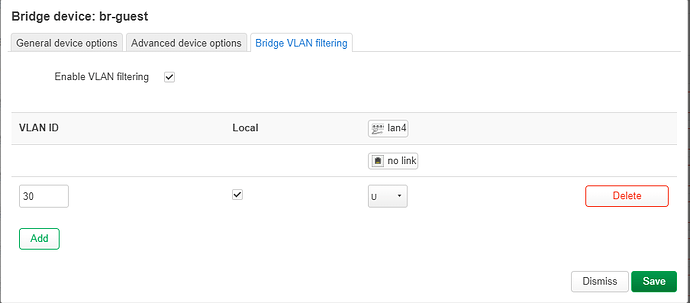
Hi everybody,
I have a question similar to the one described here: Access point, multiple SSIDs, firewall
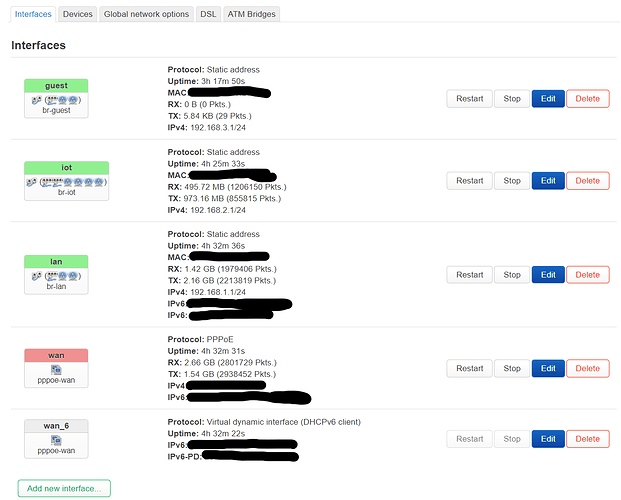
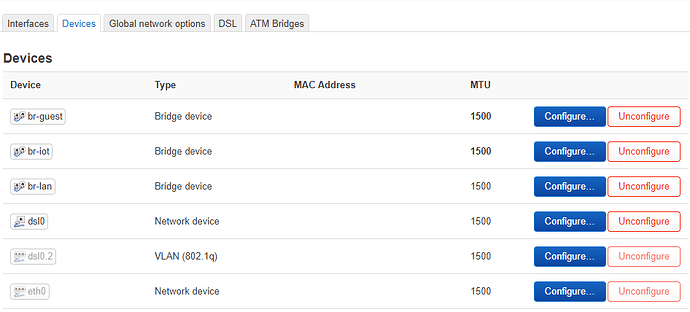
I have a router (Fritz!Box 7530) running OpenWrt connection via modem to the internet. I have configured several interfaces (lan, iot, guest) via bridges (don't know whether this is the correct way/needed, but seems to work somehow). Each of these interfaces provides a different subnet (192.168.1.1, 192.168.2.1, 192.168.3.1).
Here's an excerpt of my /etc/config/network of the router:
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option type 'bridge'
option name 'br-iot'
list ports 'lan2'
list ports 'lan3'
option mtu '1500'
option macaddr 'xxx'
option txqueuelen '1000'
config interface 'iot'
option proto 'static'
option device 'br-iot'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
config device
option type 'bridge'
option name 'br-guest'
list ports 'lan4'
option mtu '1500'
option macaddr 'xxx'
option txqueuelen '1000'
option mtu6 '1500'
config interface 'guest'
option proto 'static'
option device 'br-guest'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
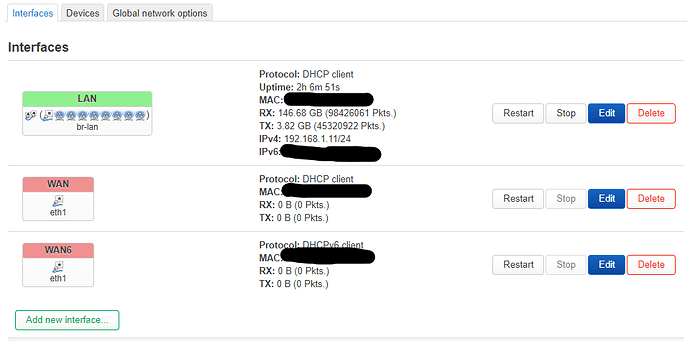
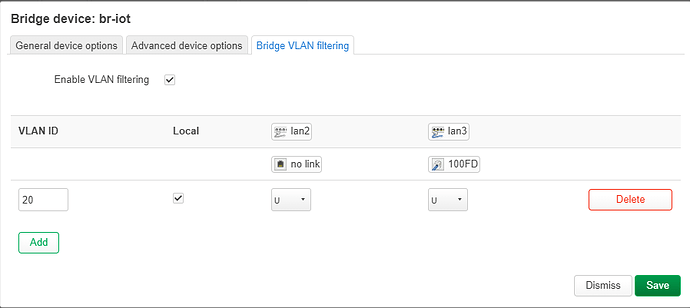
The main router has three SSIDs defined (currently 4, one will be deleted as soon as the setup is working). One linked to 'lan', one linked to 'guest', and one linked to 'iot'. Hope this makes sense until here :-). In theory this seems to work. However, I have an access point (GL.iNet GL-B1300) hard wired via an unmanaged switch to lan1 of the main router and wanted that AP to repeat the same three SSIDs but failed. I (think I) got it working with just one SSID linked to lan of the AP, but not all three of them, supposedly because I need some kind of VLAN magic or so?
/etc/config/network of the AP is as follows:
root@GL-B1300:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxx::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'dhcp'
option ip6assign '60'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '3 4 0'
config device
option name 'eth0'
Using snapshot version of OpenWrt on the router and 22.03 on the AP. Can somebody enlighten me pls and guide me through this? Read what I found so far but could not get it working (or didn't understand it :-)) :-(. If something else is needed, please let me know.
Thanks in advance and have a nice day.
KR
Update:
Okay, doesn't work as intended. Tried to connect to the iot WLAN (linked to the iot interface which should be in the 192.168.2.1/24 subnet) but got an 192.168.1.x IP :-(. Any suggestions for that? Thanks!