Hi trendy,
I have recompile Openwrt and now travelmate appear in the menu, it displays the correct message and appear to have no error, just like before.
here is the info. Thank you for your time:
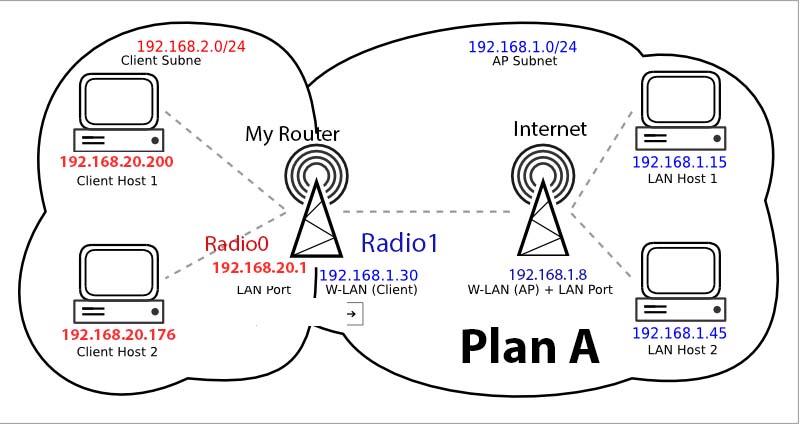
I have corrected the IP with according to the picture.
192.168.2.1 is the statistic IP of wlan with DHCP enabled.
192.168.1.30 is the DHCP assigned IP by "Internet router" to "My Router"
root@OpenWrt:~# uci show network;uci show wireless; \
> uci show firewall; uci show dhcp; \
> uci show travelmate ;
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='xxx:xxxb:xxx5::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0'
network.lan.proto='static'
network.lan.ip6assign='60'
network.lan.netmask='255.255.255.0'
network.lan.dns='1.1.1.1'
network.lan.gateway='192.168.1.8'
network.lan.ipaddr='192.168.20.1'
network.vpn0=interface
network.vpn0.ifname='tun0'
network.vpn0.proto='none'
network.wwan=interface
network.wwan.proto='dhcp'
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.hwmode='11g'
wireless.radio0.path='platform/soc/1c1d000.usb/usb5/5-1/5-1:1.0'
wireless.radio0.htmode='HT20'
wireless.radio0.channel='1'
wireless.radio0.country='00'
wireless.radio0.legacy_rates='1'
wireless.radio0.mu_beamformer='0'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.channel='11'
wireless.radio1.hwmode='11g'
wireless.radio1.path='platform/soc/1c10000.mmc/mmc_host/mmc2/mmc2:0001/mmc2:0001:1'
wireless.radio1.htmode='HT20'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.network='lan'
wireless.default_radio1.mode='ap'
wireless.default_radio1.ssid='OpenWrt'
wireless.default_radio1.encryption='none'
wireless.@wifi-iface[1]=wifi-iface
wireless.@wifi-iface[1].network='wwan'
wireless.@wifi-iface[1].ssid='F3'
wireless.@wifi-iface[1].encryption='psk2'
wireless.@wifi-iface[1].device='radio0'
wireless.@wifi-iface[1].mode='sta'
wireless.@wifi-iface[1].bssid='A0:AB:xx:xx:xx:xx'
wireless.@wifi-iface[1].key='xxx'
wireless.@wifi-iface[1].disabled='0'
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='ACCEPT'
firewall.@defaults[0].fullcone='1'
firewall.@defaults[0].flow_offloading='1'
firewall.@defaults[0].flow_offloading_hw='0'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='ACCEPT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='ACCEPT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan wan6 wwan stabridge'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.zerotier=include
firewall.zerotier.type='script'
firewall.zerotier.path='/etc/zerotier.start'
firewall.zerotier.reload='1'
firewall.miniupnpd=include
firewall.miniupnpd.type='script'
firewall.miniupnpd.path='/usr/share/miniupnpd/firewall.include'
firewall.miniupnpd.family='any'
firewall.miniupnpd.reload='1'
firewall.adbyby=include
firewall.adbyby.type='script'
firewall.adbyby.path='/usr/share/adbyby/firewall.include'
firewall.adbyby.reload='1'
firewall.adblock=rule
firewall.adblock.name='adblock'
firewall.adblock.target='DROP'
firewall.adblock.src='wan'
firewall.adblock.proto='tcp'
firewall.adblock.dest_port='8118'
firewall.kms=rule
firewall.kms.name='kms'
firewall.kms.target='ACCEPT'
firewall.kms.src='wan'
firewall.kms.proto='tcp'
firewall.kms.dest_port='1688'
firewall.mia=include
firewall.mia.type='script'
firewall.mia.path='/etc/mia.include'
firewall.mia.reload='1'
firewall.openvpn=rule
firewall.openvpn.name='openvpn'
firewall.openvpn.target='ACCEPT'
firewall.openvpn.src='wan'
firewall.openvpn.proto='tcp udp'
firewall.openvpn.dest_port='1194'
firewall.vpn=zone
firewall.vpn.name='vpn'
firewall.vpn.input='ACCEPT'
firewall.vpn.forward='ACCEPT'
firewall.vpn.output='ACCEPT'
firewall.vpn.masq='1'
firewall.vpn.network='vpn0'
firewall.vpnwan=forwarding
firewall.vpnwan.src='vpn'
firewall.vpnwan.dest='wan'
firewall.vpnlan=forwarding
firewall.vpnlan.src='vpn'
firewall.vpnlan.dest='lan'
firewall.pptpd=include
firewall.pptpd.type='script'
firewall.pptpd.path='/etc/pptpd.include'
firewall.pptpd.reload='1'
firewall.pptp=rule
firewall.pptp.name='pptp'
firewall.pptp.target='ACCEPT'
firewall.pptp.src='wan'
firewall.pptp.proto='tcp'
firewall.pptp.dest_port='1723'
firewall.gre=rule
firewall.gre.name='gre'
firewall.gre.target='ACCEPT'
firewall.gre.src='wan'
firewall.gre.proto='47'
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].boguspriv='1'
dhcp.@dnsmasq[0].filterwin2k='0'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].local='/lan/'
dhcp.@dnsmasq[0].domain='lan'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].nonegcache='0'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].resolvfile='/tmp/resolv.conf.auto'
dhcp.@dnsmasq[0].nonwildcard='1'
dhcp.@dnsmasq[0].localservice='1'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.limit='150'
dhcp.lan.leasetime='12h'
dhcp.lan.ra='server'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra_management='1'
dhcp.lan.ra_default='1'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.@srvhost[0]=srvhost
dhcp.@srvhost[0].srv='_vlmcs._tcp'
dhcp.@srvhost[0].target='OpenWrt'
dhcp.@srvhost[0].port='1688'
dhcp.@srvhost[0].class='0'
dhcp.@srvhost[0].weight='100'
travelmate.global=travelmate
travelmate.global.trm_captive='1'
travelmate.global.trm_triggerdelay='2'
travelmate.global.trm_debug='1'
travelmate.global.trm_maxretry='3'
travelmate.global.trm_minquality='35'
travelmate.global.trm_maxwait='30'
travelmate.global.trm_timeout='60'
travelmate.global.trm_rtfile='/tmp/trm_runtime.json'
travelmate.global.trm_iface='wwan'
travelmate.global.trm_enabled='1'
travelmate.global.trm_radio='radio0'
root@OpenWrt:~# ip -4 addr ; ip -4 ro ; ip -4 ru; \
> iptables-save; \
> head -n -0 /etc/firewall.user; \
> ls -l /etc/resolv.* /tmp/resolv.*; head -n -0 /etc/resolv.* /tmp/resolv.*