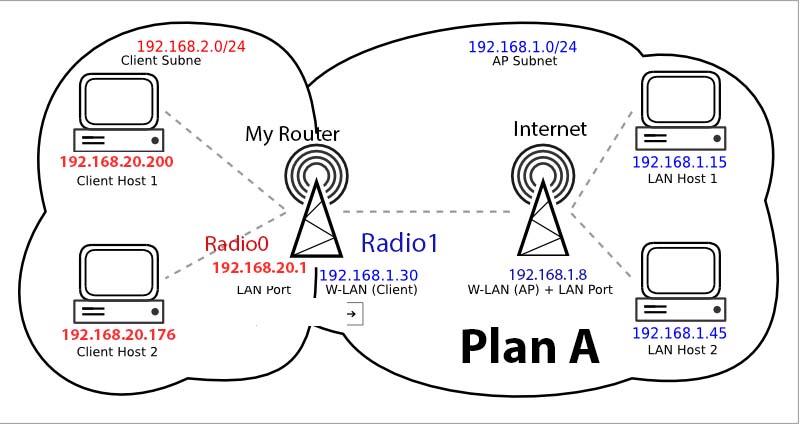
Hi Trendy,
Thank for your response.
root@OpenWrt:/etc/config# /etc/init.d/travelmate status
::: travelmate runtime information
+ travelmate_status : connected (net ok/81)
+ travelmate_version : 1.2.2
+ station_id : radio0/Trendy/A0:AB
+ station_interface : wwan
+ faulty_stations :
+ last_rundate : 30.09.2019 22:07:45
+ system : Air, OpenWrt
root@OpenWrt:/etc/config# uci show network ; uci show wireless ; uci show firewa
ll ; uci show travelmate
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fd3e:5344:159c::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0'
network.lan.proto='static'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.ipaddr='192.168.10.1'
network.wwan=interface
network.wwan.proto='dhcp'
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.hwmode='11g'
wireless.radio0.path='platform/soc/1c1d000.usb/usb5/5-1/5-1:1.0'
wireless.radio0.htmode='HT20'
wireless.radio0.channel='1'
wireless.radio0.country='00'
wireless.radio0.legacy_rates='1'
wireless.radio0.mu_beamformer='0'
wireless.radio0.disabled='0'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.channel='11'
wireless.radio1.hwmode='11g'
wireless.radio1.path='platform/soc/1c10000.mmc/mmc_host/mmc2/mmc2:0001/mmc2:0001:1'
wireless.radio1.htmode='HT20'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.network='lan'
wireless.default_radio1.mode='ap'
wireless.default_radio1.ssid='OpenWrt'
wireless.default_radio1.encryption='none'
wireless.@wifi-iface[1]=wifi-iface
wireless.@wifi-iface[1].network='wwan'
wireless.@wifi-iface[1].ssid='Trendy'
wireless.@wifi-iface[1].encryption='psk2'
wireless.@wifi-iface[1].device='radio0'
wireless.@wifi-iface[1].mode='sta'
wireless.@wifi-iface[1].bssid='A0:'
wireless.@wifi-iface[1].key='Ilovetravelmate'
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='ACCEPT'
firewall.@defaults[0].fullcone='1'
firewall.@defaults[0].flow_offloading='1'
firewall.@defaults[0].flow_offloading_hw='0'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='ACCEPT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='ACCEPT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan wan6 wwan'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.zerotier=include
firewall.zerotier.type='script'
firewall.zerotier.path='/etc/zerotier.start'
firewall.zerotier.reload='1'
firewall.miniupnpd=include
firewall.miniupnpd.type='script'
firewall.miniupnpd.path='/usr/share/miniupnpd/firewall.include'
firewall.miniupnpd.family='any'
firewall.miniupnpd.reload='1'
firewall.adbyby=include
firewall.adbyby.type='script'
firewall.adbyby.path='/usr/share/adbyby/firewall.include'
firewall.adbyby.reload='1'
firewall.adblock=rule
firewall.adblock.name='adblock'
firewall.adblock.target='DROP'
firewall.adblock.src='wan'
firewall.adblock.proto='tcp'
firewall.adblock.dest_port='8118'
firewall.v2ray_server=include
firewall.v2ray_server.type='script'
firewall.v2ray_server.path='/usr/share/v2ray_server/firewall.include'
firewall.v2ray_server.reload='1'
firewall.kms=rule
firewall.kms.name='kms'
firewall.kms.target='ACCEPT'
firewall.kms.src='wan'
firewall.kms.proto='tcp'
firewall.kms.dest_port='1688'
firewall.mia=include
firewall.mia.type='script'
firewall.mia.path='/etc/mia.include'
firewall.mia.reload='1'
firewall.pptpd=include
firewall.pptpd.type='script'
firewall.pptpd.path='/etc/pptpd.include'
firewall.pptpd.reload='1'
firewall.pptp=rule
firewall.pptp.name='pptp'
firewall.pptp.target='ACCEPT'
firewall.pptp.src='wan'
firewall.pptp.proto='tcp'
firewall.pptp.dest_port='1723'
firewall.gre=rule
firewall.gre.name='gre'
firewall.gre.target='ACCEPT'
firewall.gre.src='wan'
firewall.gre.proto='47'
travelmate.global=travelmate
travelmate.global.trm_enabled='1'
travelmate.global.trm_captive='1'
travelmate.global.trm_iface='trm_wwan'
travelmate.global.trm_triggerdelay='2'
travelmate.global.trm_debug='0'
travelmate.global.trm_maxretry='3'
travelmate.global.trm_minquality='35'
travelmate.global.trm_maxwait='30'
travelmate.global.trm_timeout='60'
travelmate.global.trm_rtfile='/tmp/trm_runtime.json'
Mon Sep 30 22:19:31 2019 user.info travelmate-1.2.2[3011]: travelmate instance started ::: action: start, pid: 3011
Mon Sep 30 22:19:32 2019 user.debug travelmate-1.2.2[3011]: f_jsnup::: config: @wifi-iface[1], status: connected (net ok/87), sta_iface: wwan, sta_radio: radio0, sta_essid: F3, sta_bssid: A0:AB:1B:50:C3:DE, faulty_list: -
Mon Sep 30 22:19:32 2019 user.debug travelmate-1.2.2[3011]: f_check::: mode: initial, name: wlan0, status: true, quality: 87, connection: net ok/87, wait: 1, max_wait: 30, min_quality: 35, captive: 1
Mon Sep 30 22:20:34 2019 user.debug travelmate-1.2.2[3011]: f_check::: mode: initial, name: wlan0, status: true, quality: 81, connection: net ok/87, wait: 1, max_wait: 30, min_quality: 35, captive: 1
Mon Sep 30 22:21:37 2019 user.debug travelmate-1.2.2[3011]: f_check::: mode: initial, name: wlan0, status: true, quality: 81, connection: net ok/87, wait: 1, max_wait: 30, min_quality: 35, captive: 1
Mon Sep 30 22:22:41 2019 user.debug travelmate-1.2.2[3011]: f_check::: mode: initial, name: wlan0, status: true, quality: 84, connection: net ok/87, wait: 1, max_wait: 30, min_quality: 35, captive: 1
Mon Sep 30 22:23:42 2019 user.debug travelmate-1.2.2[3011]: f_check::: mode: initial, name: wlan0, status: true, quality: 87, connection: net ok/87, wait: 1, max_wait: 30, min_quality: 35, captive: 1
strangely, I don't see Travelmate in the Service menu.