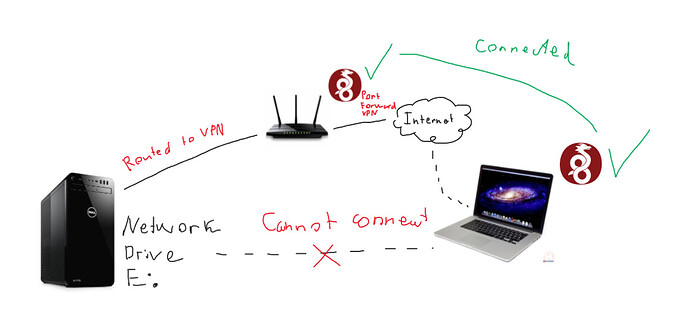
Here's my situation:
I attempt to write every possible IP address I have assigned during the setup on my Macbook connect to input bar. None of them work. I am not sure why.
The network drive sharing totally works since I previously have attempted run Wireguard on my Desktop PC and connect to the network drive on Macbook which was successful.
Configs:
[Interface]
PrivateKey = prKey
Address = 10.0.0.2/24
DNS = 10.0.0.1
[Peer]
PublicKey = puKey
AllowedIPs = 10.0.0.4/24
Endpoint = pAddress:51820
Routers config:
config interface 'wg0'
option proto 'wireguard'
option listen_port '51820'
list addresses '10.0.0.1/24'
option private_key 'prKey'
config wireguard_wg0
option description 'MacBook'
option public_key 'puKey'
list allowed_ips '10.0.0.2/32'
PBR Config
config policy
option name 'DesktopPC'
option chain 'output'
option interface 'wg0'
option src_addr '192.168.0.139'
option dest_addr '10.0.0.4'
Router Port Forward
config redirect
option dest 'lan'
option target 'DNAT'
option src 'wan'
option src_dport '51820'
option dest_port '51820'
option name 'VPN'
option dest_ip '192.168.0.1'
list proto 'tcp'
list proto 'udp'
I am looking forward for any help, thanks.
krazeh
December 6, 2023, 10:11am
2
There's a number of issues. The AllowedIPs in your macbook config looks wrong, you don't need PBR for what you want to do, and the port forward also appears wrong.
Let's get the full configs from your router and start there. Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/dhcp
cat /etc/config/firewall
Also, what IP address is assigned to your desktop PC?
1 Like
I may have to mention I did some tweaking in hopes it will work and to no avail nothing works.
{
"kernel": "5.10.176",
"hostname": "Farida-Wireless-Switch",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "TP-Link Archer C59 v1",
"board_name": "tplink,archer-c59-v1",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.5",
"revision": "r20134-5f15225c1e",
"target": "ath79/generic",
"description": "OpenWrt 22.03.5 r20134-5f15225c1e"
}
}
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd9d:bc6c:3303::/48'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.0.1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0t'
config device
option name 'eth0.1'
option type '8021q'
option ifname 'eth0'
option vid '1'
option ipv6 '0'
config device
option name 'eth1'
option macaddr 'mcAdress'
config interface 'wg0'
option proto 'wireguard'
option listen_port '51820'
list addresses '10.0.0.1/24'
option private_key 'prKey'
config wireguard_wg0
option description 'MacBook'
option public_key 'puKey'
list allowed_ips '10.0.0.2/32'
list allowed_ips '192.168.0.0/24'
cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option ednspacket_max '1232'
list server '/mask.icloud.com/'
list server '/mask-h2.icloud.com/'
list server '/use-application-dns.net/'
list server '127.0.0.1#5053'
list server '127.0.0.1#5054'
option doh_backup_noresolv '-1'
option noresolv '1'
list doh_backup_server '/mask.icloud.com/'
list doh_backup_server '/mask-h2.icloud.com/'
list doh_backup_server '/use-application-dns.net/'
list doh_backup_server '127.0.0.1#5053'
list doh_backup_server '127.0.0.1#5054'
list doh_server '127.0.0.1#5053'
list doh_server '127.0.0.1#5054'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'OMEN'
option dns '1'
option mac 'mcAddress'
option ip '192.168.0.139'
cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg0'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'DVRHTTP'
option family 'ipv4'
option src 'wan'
option src_dport '8080'
option dest_ip '192.168.0.174'
option dest_port '8080'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'DVRRTSP'
option family 'ipv4'
option src 'wan'
option src_dport '554'
option dest_ip '192.168.0.174'
option dest_port '554'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'DVRHTTPS'
option family 'ipv4'
option src 'wan'
option src_dport '443'
option dest_ip '192.168.0.174'
option dest_port '443'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'DVRServer'
option family 'ipv4'
option src 'wan'
option src_dport '8000'
option dest_ip '192.168.0.174'
option dest_port '8000'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'PrinterEPSONL150'
option family 'ipv4'
option src 'wan'
option src_dport '9100'
option dest_ip '192.168.0.160'
option dest_port '9100'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'OmenPCRDp'
option src 'wan'
option src_dport '3389'
option dest_ip '192.168.0.139'
option dest_port '3389'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'RPIPLEX'
option src 'wan'
option src_dport '32400'
option dest_port '32400'
option dest_ip '192.168.0.126'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'RPIRADARR'
option src 'wan'
option src_dport '7878'
option dest_port '7878'
option dest_ip '192.168.0.126'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'RPIPROWLARR'
option src 'wan'
option src_dport '9696'
option dest_port '9696'
option dest_ip '192.168.0.126'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'RPISONARR'
option src 'wan'
option src_dport '8989'
option dest_port '8989'
option dest_ip '192.168.0.126'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'RPIQBITT'
option src 'wan'
option src_dport '5080'
option dest_port '5080'
option dest_ip '192.168.0.126'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'RPIOVERSEERR'
option src 'wan'
option src_dport '5055'
option dest_port '5055'
option dest_ip '192.168.0.126'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'RPISYNCLOUNGE'
option src 'wan'
option src_dport '12222'
option dest_port '8088'
option dest_ip '192.168.0.126'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'JellyFin'
option src 'wan'
option src_dport '8096'
option dest_port '8096'
option dest_ip '192.168.0.126'
config redirect
option dest 'lan'
option target 'DNAT'
option src 'wan'
option src_dport '51820'
option dest_port '51820'
option name 'VPN'
option dest_ip '192.168.0.1'
list proto 'tcp'
list proto 'udp'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
IP address of my desktop PC is 192.168.0.139
krazeh
December 6, 2023, 10:30am
4
Remove that from the wireguard config on the router. Replace the current AllowedIPs on the macbook with 192.168.0.0/24
Remove the PBR config you added (as described in your first post).
Change this to:
config rule
option target 'ACCEPT'
option src 'wan'
option dest_port '51820'
option name 'VPN'
option proto 'udp'
If you're making changes through the cli rather than LuCi then when you've finished run/etc/init.d/firewall reload/etc/init.d/network reload
That should implement the changes. However, in some cases, changes to WG can necessitate a router restart before they're picked up properly.
2 Likes
I am finally back on the Internet.
krazeh
December 6, 2023, 11:37am
6
Nothing I suggested should've had any impact on the router's basic WAN/LAN functionality. Have you restarted the router? Do you have any connectivity to it on the LAN?
1 Like
I restarted it, did everything. I am trying to enter failsafe mode but fail to do so. I am going to attempt to reset everything and redo all configs.
1 Like
Replace the AllowedIPs in the Wireguard OpenWRT peer section or the Wireguard Config file of actual Macbook device?
krazeh
December 6, 2023, 1:43pm
9
Take it out of the peer section in the OpenWRT (i.e. on the router) wireguard config. Then on the macbook in the peer config replace the AllowedIPs of 10.0.0.4/24 with 192.168.0.0/24
I applied all changes, replaced the port forward with Rule, removed the IP from peer and replaces the AllowedIPs on Macbook. I have tried to test the activate, but no handshake happens
krazeh
December 6, 2023, 1:53pm
11
Let's see your updated configs. So /etc/config/network and /etc/config/firewall from the router, and the wireguard config from the macbook.
egc
December 6, 2023, 1:53pm
12
Maybe for Allowed IPs on the MacBook use 10.0.0.4/24 and 192.168.0.0/24?
krazeh
December 6, 2023, 1:55pm
13
If they were going to do that then they should use either 10.0.0.0/24 or 10.0.0.1/32, but neither should be necessary. 10.0.0.4/24 is wrong in all cases.
2 Likes
network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc3:f397:b8ec::/48'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.0.1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0t'
config device
option name 'eth1'
option macaddr 'mcaddress'
config interface 'wg0'
option proto 'wireguard'
option listen_port '51820'
list addresses '10.0.0.1/24'
option private_key 'privKey'
config wireguard_wg0
option description 'MacBook'
option public_key 'pubKey'
list allowed_ips '10.0.0.2/32'
Firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'VPN'
list proto 'udp'
option src 'wan'
option dest_port '51820'
option target 'ACCEPT'
krazeh
December 6, 2023, 2:00pm
15
Double check you've got the keys correctly on both ends of the tunnel. Re-add wg0 to the lan firewall zone.
On macbook, I have Endpoint address still set, should it be changed since we replaced Port Forward with Traffic rule.
krazeh
December 6, 2023, 2:10pm
17
I assume the router is connected directly to the internet? Is the endpoint address on your macbook set to your public IP address (which should be what is on your router)?
Yes, that is correct. The Endpoint address is the one of my Public IP Address that is accessible outside of home internet.
krazeh
December 6, 2023, 2:18pm
19
In that case the wireguard endpoint address shouldn't need changing.
What's the output of nft list ruleset | grep VPN on the router?
trendy
December 6, 2023, 2:18pm
20
wg0 is not in any firewall zone, add it in lan.