ubus call system board; \
> uci export network; \
> uci export dhcp; uci export firewall; \
> head -n -0 /etc/firewall.user; \
> ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
> ls -l /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/* ; head -n -0 /etc/resolv.*
/tmp/resolv.* /tmp/resolv.*/*
{
"kernel": "5.10.176",
"hostname": "ArmOpen16",
"system": "Intel(R) N100",
"model": "Default string Default string",
"board_name": "default-string-default-string",
"rootfs_type": "ext4",
"release": {
"distribution": "OpenWrt",
"version": "22.03.5",
"revision": "r20134-5f15225c1e",
"target": "x86/64",
"description": "OpenWrt 22.03.5 r20134-5f15225c1e"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdf5:78dd:d6d8::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option delegate '0'
config interface 'lan2'
option proto 'static'
option device 'eth2'
option ipaddr '192.168.2.254'
option netmask '255.255.255.0'
config interface 'lan3'
option proto 'static'
option device 'eth3'
option ipaddr '192.168.3.254'
option netmask '255.255.255.0'
config interface 'wan'
option proto 'dhcp'
option device 'eth0.10'
config interface 'wan6'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option device 'eth0.10'
config device
option name 'eth0.10'
option type '8021q'
option ifname 'eth0'
option vid '10'
config interface 'wg0'
option proto 'wireguard'
option private_key '2KXknd4sin5AkDAFSgY+2UtyW9acQw4uTwimr8VVGUE='
list addresses '10.14.0.2/16'
list dns '162.252.172.57'
list dns '149.154.159.92'
config wireguard_wg0
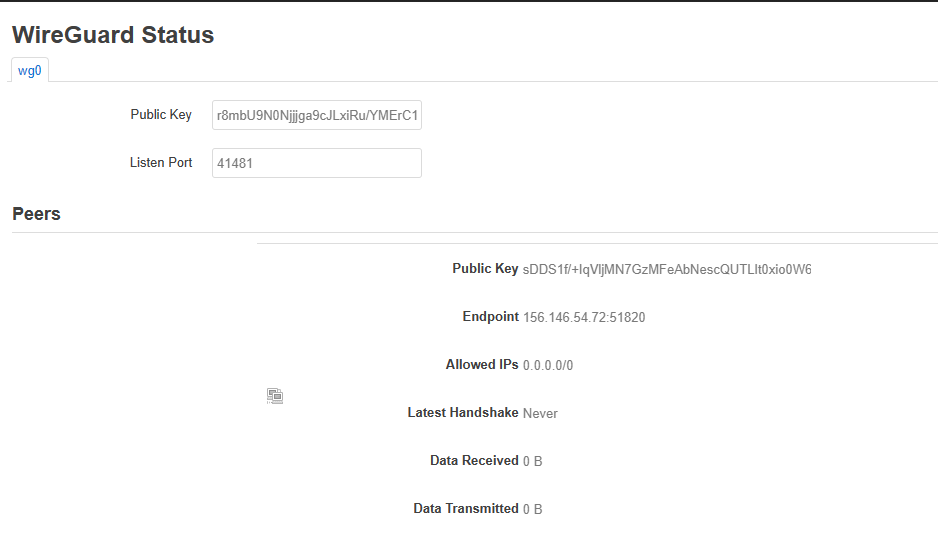
option public_key 'sDDS1f/+IqVljMN7GzMFeAbNescQUTLIt0xio0W61Q0='
list allowed_ips '0.0.0.0/0'
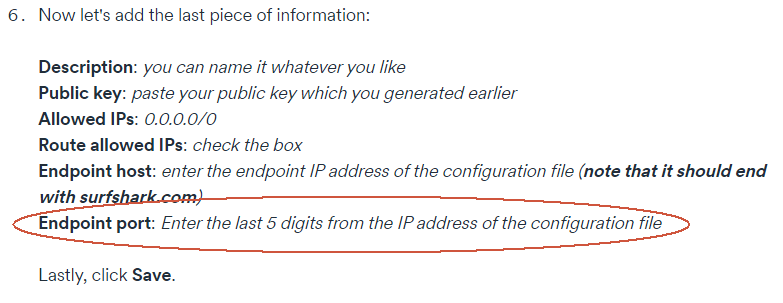
option endpoint_host 'us-sjc.prod.surfshark.com'
option endpoint_port '51820'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option dhcpv4 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option dns_service '0'
option start '105'
option limit '234'
option leasetime '40h'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'homeassistant'
option ip '192.168.1.229'
option mac '7C:D3:0A:31:D2:BE'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'lan2'
list network 'lan3'
option mtu_fix '1'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config zone
option name 'vpn'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
option masq '1'
list network 'wg0'
config forwarding
option src 'lan'
option dest 'vpn'
head: /etc/firewall.user: No such file or directory
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group defaul t qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
4: eth2: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state DOWN group default qlen 1000
inet 192.168.2.254/24 brd 192.168.2.255 scope global eth2
valid_lft forever preferred_lft forever
5: eth3: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state DOWN group default qlen 1000
inet 192.168.3.254/24 brd 192.168.3.255 scope global eth3
valid_lft forever preferred_lft forever
6: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP gro up default qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
7: eth0.10@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 121.74.232.127/22 brd 121.74.235.255 scope global eth0.10
valid_lft forever preferred_lft forever
8: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN gro up default qlen 1000
inet 10.14.0.2/16 brd 10.14.255.255 scope global wg0
valid_lft forever preferred_lft forever
default via 121.74.235.254 dev eth0.10 table pbr_wan
192.168.1.0/24 dev br-lan table pbr_wan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev eth2 table pbr_wan proto kernel scope link src 192.168.2.254 linkdown
192.168.3.0/24 dev eth3 table pbr_wan proto kernel scope link src 192.168.3.254 linkdown
default via 10.14.0.2 dev wg0 table pbr_wg0
192.168.1.0/24 dev br-lan table pbr_wg0 proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev eth2 table pbr_wg0 proto kernel scope link src 192.168.2.254 linkdown
192.168.3.0/24 dev eth3 table pbr_wg0 proto kernel scope link src 192.168.3.254 linkdown
default via 121.74.235.254 dev eth0.10 proto static src 121.74.232.127
10.14.0.0/16 dev wg0 proto kernel scope link src 10.14.0.2
121.74.232.0/22 dev eth0.10 proto kernel scope link src 121.74.232.127
156.146.54.72 via 121.74.235.254 dev eth0.10 proto static
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev eth2 proto kernel scope link src 192.168.2.254 linkdown
192.168.3.0/24 dev eth3 proto kernel scope link src 192.168.3.254 linkdown
broadcast 10.14.0.0 dev wg0 table local proto kernel scope link src 10.14.0.2
local 10.14.0.2 dev wg0 table local proto kernel scope host src 10.14.0.2
broadcast 10.14.255.255 dev wg0 table local proto kernel scope link src 10.14.0. 2
broadcast 121.74.232.0 dev eth0.10 table local proto kernel scope link src 121.7 4.232.127
local 121.74.232.127 dev eth0.10 table local proto kernel scope host src 121.74. 232.127
broadcast 121.74.235.255 dev eth0.10 table local proto kernel scope link src 121 .74.232.127
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0 .1
broadcast 192.168.1.0 dev br-lan table local proto kernel scope link src 192.168 .1.1
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.1 68.1.1
broadcast 192.168.2.0 dev eth2 table local proto kernel scope link src 192.168.2 .254 linkdown
local 192.168.2.254 dev eth2 table local proto kernel scope host src 192.168.2.2 54
broadcast 192.168.2.255 dev eth2 table local proto kernel scope link src 192.168 .2.254 linkdown
broadcast 192.168.3.0 dev eth3 table local proto kernel scope link src 192.168.3 .254 linkdown
local 192.168.3.254 dev eth3 table local proto kernel scope host src 192.168.3.2 54
broadcast 192.168.3.255 dev eth3 table local proto kernel scope link src 192.168 .3.254 linkdown
0: from all lookup local
30000: from all fwmark 0x10000/0xff0000 lookup pbr_wan
30001: from all fwmark 0x20000/0xff0000 lookup pbr_wg0
32766: from all lookup main
32767: from all lookup default
lrwxrwxrwx 1 root root 16 Apr 28 08:28 /etc/resolv.conf -> /tm p/resolv.conf
-rw-r--r-- 1 root root 47 Jul 21 12:57 /tmp/resolv.conf
-rw-r--r-- 1 root root 219 Jul 21 12:53 /tmp/resolv.conf.d/reso lv.conf.auto
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 219 Jul 21 12:53 resolv.conf.auto
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error
==> /tmp/resolv.conf.d/resolv.conf.auto <==
# Interface wan
nameserver 203.109.191.1
nameserver 203.118.191.1
# Interface wan6
nameserver 2407:7000:2100:5300::1
nameserver 2407:7000:ff00:5300::1
# Interface wg0
nameserver 162.252.172.57
nameserver 149.154.159.92
root@ArmOpen16:~# ^C
root@ArmOpen16:~# cls
-ash: cls: not found
root@ArmOpen16:~# clear
root@ArmOpen16:~# ubus call system board; \
> uci export network; \
> uci export dhcp; uci export firewall; \
> head -n -0 /etc/firewall.user; \
> ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
> ls -l /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/* ; head -n -0 /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/*
{
"kernel": "5.10.176",
"hostname": "ArmOpen16",
"system": "Intel(R) N100",
"model": "Default string Default string",
"board_name": "default-string-default-string",
"rootfs_type": "ext4",
"release": {
"distribution": "OpenWrt",
"version": "22.03.5",
"revision": "r20134-5f15225c1e",
"target": "x86/64",
"description": "OpenWrt 22.03.5 r20134-5f15225c1e"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdf5:78dd:d6d8::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option delegate '0'
config interface 'lan2'
option proto 'static'
option device 'eth2'
option ipaddr '192.168.2.254'
option netmask '255.255.255.0'
config interface 'lan3'
option proto 'static'
option device 'eth3'
option ipaddr '192.168.3.254'
option netmask '255.255.255.0'
config interface 'wan'
option proto 'dhcp'
option device 'eth0.10'
config interface 'wan6'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option device 'eth0.10'
config device
option name 'eth0.10'
option type '8021q'
option ifname 'eth0'
option vid '10'
config interface 'wg0'
option proto 'wireguard'
option private_key '2KXknd4sin5AkDAFSgY+2UtyW9acQw4uTwimr8VVGUE='
list addresses '10.14.0.2/16'
list dns '162.252.172.57'
list dns '149.154.159.92'
config wireguard_wg0
option public_key 'sDDS1f/+IqVljMN7GzMFeAbNescQUTLIt0xio0W61Q0='
list allowed_ips '0.0.0.0/0'
option endpoint_host 'us-sjc.prod.surfshark.com'
option endpoint_port '51820'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option dhcpv4 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option dns_service '0'
option start '105'
option limit '234'
option leasetime '40h'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'homeassistant'
option ip '192.168.1.229'
option mac '7C:D3:0A:31:D2:BE'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'lan2'
list network 'lan3'
option mtu_fix '1'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config zone
option name 'vpn'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
option masq '1'
list network 'wg0'
config forwarding
option src 'lan'
option dest 'vpn'
head: /etc/firewall.user: No such file or directory
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
qlen 1000 inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft forever
4: eth2: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state DOWN group
default qlen 1000 inet 192.168.2.254/24 brd 192.168.2.255 scope global eth2
valid_lft forever preferred_lft forever
5: eth3: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state DOWN group default
qlen 1000 inet 192.168.3.254/24 brd 192.168.3.255 scope global eth3 valid_lft forever
preferred_lft forever
6: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
qlen 1000 inet 192.168.1.1/24 brd 192.168.1.255 scope global br-la valid_lft forever
preferred_lft forever
7: eth0.10@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group
default qlen 1000 inet 121.74.232.127/22 brd 121.74.235.255 scope global eth0.10
valid_lft forever preferred_lft forever
8: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default
qlen 1000 inet 10.14.0.2/16 brd 10.14.255.255 scope global wg0 valid_lft forever
preferred_lft forever
default via 121.74.235.254 dev eth0.10 table pbr_wan
192.168.1.0/24 dev br-lan table pbr_wan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev eth2 table pbr_wan proto kernel scope link src 192.168.2.254 linkdown
192.168.3.0/24 dev eth3 table pbr_wan proto kernel scope link src 192.168.3.254 linkdown
default via 10.14.0.2 dev wg0 table pbr_wg0
192.168.1.0/24 dev br-lan table pbr_wg0 proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev eth2 table pbr_wg0 proto kernel scope link src 192.168.2.254 linkdown
192.168.3.0/24 dev eth3 table pbr_wg0 proto kernel scope link src 192.168.3.254 linkdown
default via 121.74.235.254 dev eth0.10 proto static src 121.74.232.127
10.14.0.0/16 dev wg0 proto kernel scope link src 10.14.0.2
121.74.232.0/22 dev eth0.10 proto kernel scope link src 121.74.232.127
156.146.54.72 via 121.74.235.254 dev eth0.10 proto static
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev eth2 proto kernel scope link src 192.168.2.254 linkdown
192.168.3.0/24 dev eth3 proto kernel scope link src 192.168.3.254 linkdown
broadcast 10.14.0.0 dev wg0 table local proto kernel scope link src 10.14.0.2
local 10.14.0.2 dev wg0 table local proto kernel scope host src 10.14.0.2
broadcast 10.14.255.255 dev wg0 table local proto kernel scope link src 10.14.0.2
broadcast 121.74.232.0 dev eth0.10 table local proto kernel scope link src 121.74.232.127
local 121.74.232.127 dev eth0.10 table local proto kernel scope host src 121.74.232.127
broadcast 121.74.235.255 dev eth0.10 table local proto kernel scope link src 121.74.232.127
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local proto kernel scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.168.1.1
broadcast 192.168.2.0 dev eth2 table local proto kernel scope link src 192.168.2.254 linkdown
local 192.168.2.254 dev eth2 table local proto kernel scope host src 192.168.2.254
broadcast 192.168.2.255 dev eth2 table local proto kernel scope link src 192.168.2.254 linkdown
broadcast 192.168.3.0 dev eth3 table local proto kernel scope link src 192.168.3.254 linkdown
local 192.168.3.254 dev eth3 table local proto kernel scope host src 192.168.3.254
broadcast 192.168.3.255 dev eth3 table local proto kernel scope link src 192.168.3.254 linkdown
0: from all lookup local
30000: from all fwmark 0x10000/0xff0000 lookup pbr_wan
30001: from all fwmark 0x20000/0xff0000 lookup pbr_wg0
32766: from all lookup main
32767: from all lookup default
lrwxrwxrwx 1 root root 16 Apr 28 08:28 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 47 Jul 21 12:57 /tmp/resolv.conf
-rw-r--r-- 1 root root 219 Jul 21 12:53 /tmp/resolv.conf.d/resolv.conf.auto
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 219 Jul 21 12:53 resolv.conf.auto
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error
==> /tmp/resolv.conf.d/resolv.conf.auto <==
# Interface wan
nameserver 203.109.191.1
nameserver 203.118.191.1
# Interface wan6
nameserver 2407:7000:2100:5300::1
nameserver 2407:7000:ff00:5300::1
# Interface wg0
nameserver 162.252.172.57
nameserver 149.154.159.92
root@ArmOpen16:~#