Hi, I'm new here, I'm coming from ddwrt, I have just set up my r7800 with OpenWrt, a long work since I have a lot of custom features from DDWRT (I've still not converted all).
Now I'm having an issue with Wireguard because I set up all the things and it works, or, the interface send and receive data but I can't browse internet nor ping devices from my iphone. I'm trying to understand what could be the issue but I'm not able, so I'm asking for a little help, here's the info:
wg0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.4.0.1 P-t-P:10.4.0.1 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP MTU:1420 Metric:1
RX packets:461 errors:0 dropped:0 overruns:0 frame:0
TX packets:54 errors:0 dropped:3 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:52540 (51.3 KiB) TX bytes:2736 (2.6 KiB)
root@R7800:~# wg show
interface: wg0
public key: pkey
private key: (hidden)
listening port: 51820
peer: pkey
endpoint: ip:51820
allowed ips: 10.4.0.1/32
latest handshake: 2 minutes, 6 seconds ago
transfer: 83.02 KiB received, 3.73 KiB sent
persistent keepalive: every 25 seconds
I've also created the rule to open the port 51820 from my wan to the router (wg0 is under LAN fw zone)
Incoming IPv4, protocol UDP From wan To this device port 51820
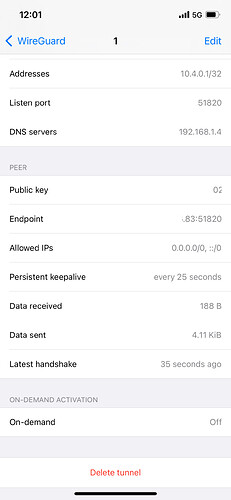
And on my iphone:
I'm using no-ip.com and DDNS on openwrt to auto-update the router's IP when it change, 192.168.1.4 is my pihole with Unbound that works as DNS (but doesn't work also with any other DNS).
What could be the trouble? On ddwrt same setup was working fine, surely I'm doing something wrong.
The only difference here is that I still don't have created the masquerade rules to view my modem (192.168.2.1) from my LAN/router (192.168.1.2), because I'm not able to do at the moment (something is different, help also here should be very usefuel)
Thanks for the help