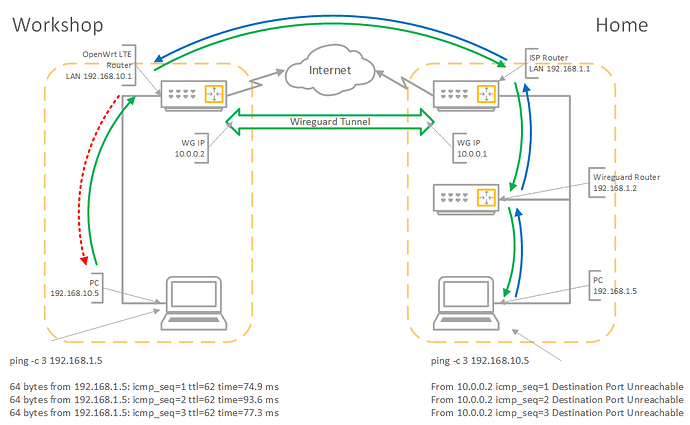
Hi,
I have spent so many hours reading this forum, Googling, but to no avail.
I have a site-to-site Wireguard tunnel working.
One site can successfully ping the local router, the near end of the tunnel, the far end of the tunnel, the far router LAN address, and clients on the far LAN.
The other site can successfully ping the same sequence in reverse, including the remote router LAN address, but not any clients on the LAN.
I have tried every permutation of masquerading, but I can't get over that last hurdle.
I would welcome any suggestions - thank you!
Site: Home cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxxx:xxxx:9b96::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.1.1'
option ipaddr '192.168.1.2'
list dns '192.168.1.5'
config interface 'wg_s2s_a'
option proto 'wireguard'
option private_key 'kGkGkGkGkGkGkGkGkGkGkGkGkGkGkGkG'
option listen_port '51820'
list addresses '10.0.0.1/32'
config wireguard_wg_s2s_a 's2s_vpn_site_workshop'
option public_key 'yNyNyNyNyNyNyNyNyNyNyNyNyNyNyNyNyNyNyNyN'
option preshared_key 'A5xA5xA5xA5xA5xA5xA5xA5xA5xA5xA5xA5xA5xA5x'
option description 'Site Workshop, yyy.yyydns.net'
option route_allowed_ips '1'
option persistent_keepalive '25'
option endpoint_host 'xxx.dns.net'
option endpoint_port '51820'
list allowed_ips '192.168.10.0/24'
list allowed_ips 'eeee:ffff:1541::/48'
list allowed_ips '10.0.0.2/32'
Site: Home cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
option masq '1'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
option masq '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule 'wg_s2s_51820'
option name 'Allow-WireGuard-51820'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'wg_s2s_a'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'lan'
Site: Workshop cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'ffff:eeee:1541::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '8.8.8.8'
option ipaddr '192.168.10.1'
config interface 'SmartyLTE'
option proto 'modemmanager'
option device '/sys/devices/platform/soc/3f980000.usb/usb1/1-1/1-1.2'
option auth 'none'
option iptype 'ipv4'
config interface 'wwan'
option proto 'dhcp'
option device 'wwan0'
config interface 'wg_s2s_b'
option proto 'wireguard'
option private_key 'cCcCcCcCcCcCcCcCcCcCcCcCcCcCcCcCcCcCcC'
option listen_port '51820'
list addresses '10.0.0.2/32'
config wireguard_wg_s2s_b 's2s_vpn_site_home'
option public_key 'sSsSsSsSsSsSsSsSsSsSsSsSsSsSsSsSsSsS'
option preshared_key 'tTtTtTtTtTtTtTtTtTtTtTtTtTtTtTtTtTtT'
option description 'Site Home, xxx.xxxdns.net'
option route_allowed_ips '1'
option persistent_keepalive '25'
option endpoint_host 'xxx.xxxdns.net'
option endpoint_port '51820'
list allowed_ips '192.168.1.0/24'
list allowed_ips 'ffff:ffff:9b96::/48'
list allowed_ips '10.0.0.1/32'
Site: Workshop cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
option masq '1'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'SmartyLTE'
list network 'wwan'
option masq '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule 'wg_s2s_51820'
option name 'Allow-WireGuard-51820'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'wg_s2s_b'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'wan'
Thanks again