with such an easy setup idk how Im getting this wrong (setup i followed )
so i installed the packages and luci app
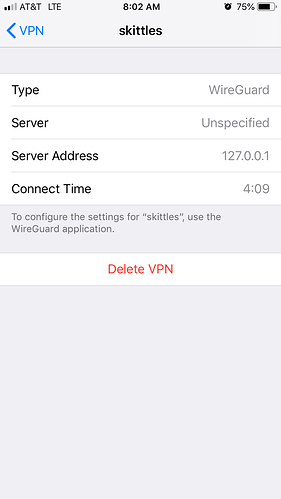
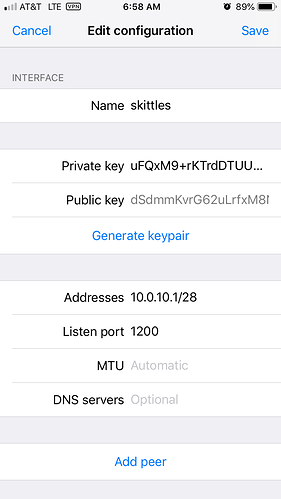
now on ios
however with it in a connected state
1 Like
Server address 127.0.0.1 doesn't look right. My guess is that this is where you enter the wan IP of the router.uci show network; uci show firewall
1 Like
I agree
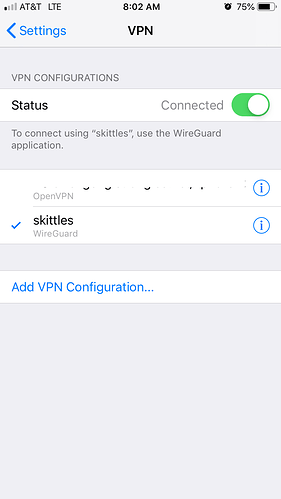
settings > vpn
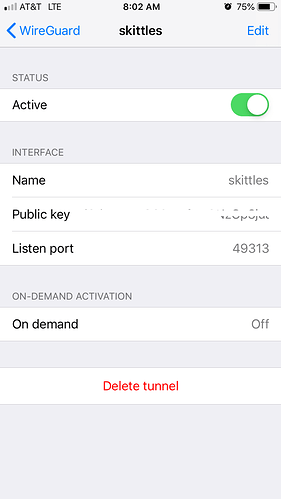
in wireguard application > edit configurationxyz.strangled.net
root@OpenWrt:/scripts# uci show network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fd22:c70b:d405::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0.1'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.wan=interface
network.wan.ifname='eth1.2'
network.wan.proto='dhcp'
network.wan6=interface
network.wan6.ifname='eth1.2'
network.wan6.proto='dhcpv6'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].ports='0 1 2 3 5t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='4 6t'
network.vpn=interface
network.vpn.ifname='tun0'
network.vpn.proto='none'
network.vpn.auto='0'
network.wireguardVPN=interface
network.wireguardVPN.proto='wireguard'
network.wireguardVPN.private_key='uFLEsHI='
root@OpenWrt:/scripts# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan' 'vpn'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].device='tun0'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@rule[9]=rule
firewall.@rule[9].name='Allow-OpenVPN'
firewall.@rule[9].src='wan'
firewall.@rule[9].dest_port='1194'
firewall.@rule[9].proto='udp'
firewall.@rule[9].target='ACCEPT'
firewall.vpn=rule
firewall.vpn.name='Allow-OpenVPN'
firewall.vpn.src='wan'
firewall.vpn.dest_port='1194'
firewall.vpn.proto='udp'
firewall.vpn.target='ACCEPT'
firewall.@rule[11]=rule
firewall.@rule[11].src='lan'
firewall.@rule[11].target='REJECT'
firewall.@rule[11].name='block traffic'
firewall.@rule[11].dest='wan'
firewall.@rule[11].enabled='0'
firewall.miniupnpd=include
firewall.miniupnpd.type='script'
firewall.miniupnpd.path='/usr/share/miniupnpd/firewall.include'
firewall.miniupnpd.family='any'
firewall.miniupnpd.reload='1'
firewall.bcp38=include
firewall.bcp38.type='script'
firewall.bcp38.path='/usr/lib/bcp38/run.sh'
firewall.bcp38.family='IPv4'
firewall.bcp38.reload='1'
What happens when you hit edit when in the Wireguard application?
What happens if you go directly to your installed Wireguard app.
For the phone you need:
Name the Interface
Make private key
Address and port of server (IP or hostname)
DNS servers you wish to use
Use 0.0.0.0/0 for allolwed IPs if this is a VPN to the Interent
On the far end (OpenWrt), you need:
The public key generated on phone
Open firewall for listening port of Wireguard
Use the /32 CIDR on peer for allowed IPs
2 Likes
Your config in OpenWrt is incomplete.
network.roadwarrior=interface
network.roadwarrior.proto='wireguard'
network.roadwarrior.private_key='mplamplampla='
network.roadwarrior.listen_port='1200'
network.roadwarrior.addresses='10.0.10.1/28'
network.@wireguard_roadwarrior[0]=wireguard_roadwarrior
network.@wireguard_roadwarrior[0].persistent_keepalive='25'
network.@wireguard_roadwarrior[0].public_key='/mplamplampla='
network.@wireguard_roadwarrior[0].description='Redmi Note4 trendy'
network.@wireguard_roadwarrior[0].allowed_ips='10.0.10.2/32'
Also you need to open on the firewall in wan zone the port that wireguard will use. I see that you have opened 1194 for openvpn.
Other than that follow also @lleachii 's suggestions.
2 Likes
Thanks guys, getting closer
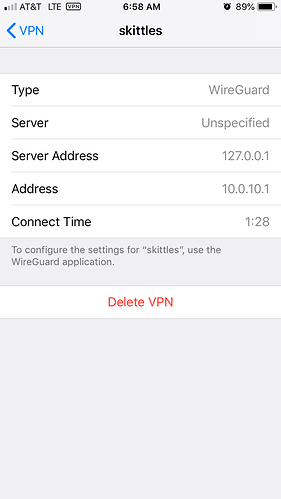
@lleachii I still do not see a place for Address and port of server (IP or hostname) after i updated wireguard interface then reimported the tunnel via the qr code it now shows 10.0.10.1/28 for addresses. However it still reads 127.0.0.1 as the server address when looking in ios>settings>vpn
ios > settings > vpn
wireguard app > edit
Here is my network and firewall again (for verification i guess)
root@OpenWrt:/etc/wireguard# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].device='tun0'
firewall.@zone[0].network='lan wireguardVPN'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan wan6'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@rule[9]=rule
firewall.@rule[9].src='wan'
firewall.@rule[9].proto='udp'
firewall.@rule[9].target='ACCEPT'
firewall.@rule[9].name='Allow-wireguard'
firewall.@rule[9].dest_port='1200'
firewall.@rule[10]=rule
firewall.@rule[10].src='lan'
firewall.@rule[10].target='REJECT'
firewall.@rule[10].name='block traffic'
firewall.@rule[10].dest='wan'
firewall.@rule[10].enabled='0'
firewall.miniupnpd=include
firewall.miniupnpd.type='script'
firewall.miniupnpd.path='/usr/share/miniupnpd/firewall.include'
firewall.miniupnpd.family='any'
firewall.miniupnpd.reload='1'
firewall.bcp38=include
firewall.bcp38.type='script'
firewall.bcp38.path='/usr/lib/bcp38/run.sh'
firewall.bcp38.family='IPv4'
firewall.bcp38.reload='1'
root@OpenWrt:/etc/wireguard# uci show network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fd22:c70b:d405::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0.1'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.wan=interface
network.wan.ifname='eth1.2'
network.wan.proto='dhcp'
network.wan6=interface
network.wan6.ifname='eth1.2'
network.wan6.proto='dhcpv6'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].ports='0 1 2 3 5t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='4 6t'
network.wireguardVPN=interface
network.wireguardVPN.proto='wireguard'
network.wireguardVPN.private_key='U......I='
network.wireguardVPN.listen_port='1200'
network.wireguardVPN.addresses='10.0.10.1/28'
network.@wireguard_wireguardVPN[0]=wireguard_wireguardVPN
network.@wireguard_wireguardVPN[0].public_key='d......4='
network.@wireguard_wireguardVPN[0].allowed_ips='10.0.10.2/32'
network.@wireguard_wireguardVPN[0].persistent_keepalive='25'
network.@wireguard_wireguardVPN[1]=wireguard_wireguardVPN
In OpenWrt config looks correct.
2 Likes
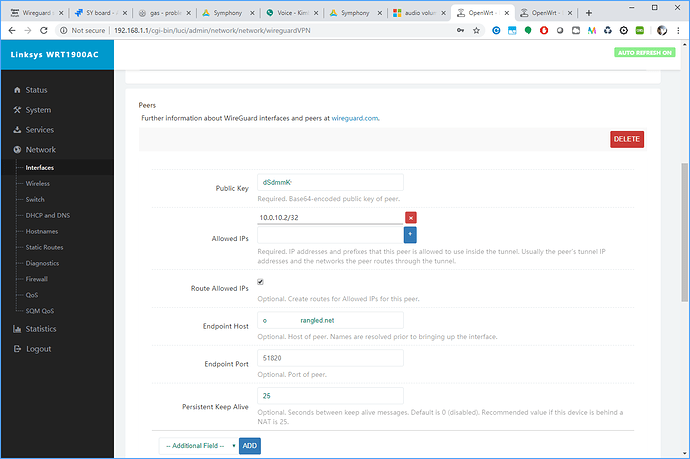
Im a little confused on where the "peer" should be created
I created one in the interface for wireguard on openwrt
then i also created it in the wireguard app
however looking at what ios settings report as the server it still shows the loopback address
do i need the peer configuration on openwrt?
@trendy I recreated manually but outcome was the same
FYI
trendy
May 30, 2019, 4:03pm
11
On Openwrt for the peer why did you specify endpoint IP and port? Also there is no need to route allowed IPs.
1 Like
OK...this is getting wayyyyy to complex.
On OpenWrt:
Create a Private Key
Add Private Key to OpenWrt interface
Assign IP 10.0.10.1/28
Make Peers
iPhone peer - add its Public Key and allowed IP 10.0.10.x /32
Android peer - add its Public Key and allowed IP 10.0.10.y /32
On Phones:
Make Private Key
IP 10.0.10.xxx/28
Copy down PUBLIC key to add in OpenWrt Make Peer with OpenWrt
add Public Key of OpenWrt here
add IP or hostname of OpenWrt
add port of OpenWrt
Allowed IP: 0.0.0.0/0
Add DNS servers accessible over tunnel
Why do you have an /etc/wireguard directory?
1 Like
its just where i placed my private and public key files that i generated
havnt tried the above yet, but i will
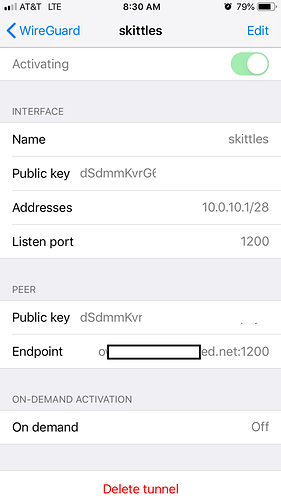
openwrt > interfaces > wireguardvpn
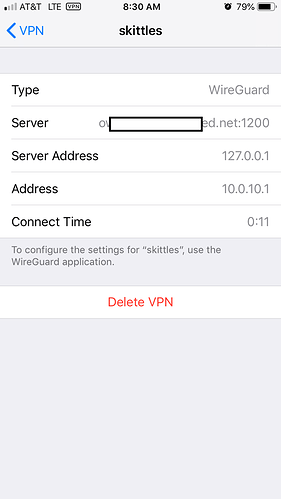
i tried your latest steps but no matter what 127.0.0.1 is the Server Address in ios > vpn (see earlier screenshots). Even though Server field does show my ddns name it seems that only Server Address matters.
it makes no sense to me that there is no where to manually set Server Address.
looking at the interface on openwrt it shows 0 for RX and TX
I've just tested on a borrowed iPhone, I'm able to successfully setup Wireguard and connect.
I simply edited the server section and entered foo.example.com :xxxxx
1 Like
there is server & server address
but its the server that holds the loopback address
if you look at the screenshot above it shows my ddns address in the server field
OK...please ignore the 127.0.0.1, as that's your iPhone!
Address - IP assigned /28 (you have this)
Listen port - Blank
MTU - Blank
DNS Servers - pick one that can be reached on tunnel
Public Key - add Public Key of OpenWrt
Allowed - IPs 0.0.0.0/0
Endpoint - foo.example.com :xxxx
Please share your results.
1 Like
sorry for all this trouble, and thank you for the help
same results
few specific questions here:
what firewall zone should it point to (lan wan or unspecified)?
should there be a peer configuration on openwrt side of things? it seems to me only the wireguard app on the phone should configure a peer.
i dont really have a dns server other the what is included in openwrt, so i just use the router address for the dns, does that seem correct?
but looking at the wireguard app (ios) log it almost seems correct. I was thinking maybe its a routing issue but with rx tx being 0 idk what to think
toooo long, omitted all lines previous to this
2019-05-30 14:53:40.469202: [NET] Stopping tunnel
2019-05-30 14:53:40.469749: [NET] Device closing
2019-05-30 14:53:40.473941: [NET] Routine: event worker - stopped
2019-05-30 14:53:40.476386: [NET] Routine: TUN reader - stopped
2019-05-30 14:53:40.479157: [NET] Routine: receive incoming IPv4 - stopped
2019-05-30 14:53:40.481882: [NET] Routine: receive incoming IPv6 - stopped
2019-05-30 14:53:40.490047: [NET] Routine: decryption worker - stopped
2019-05-30 14:53:40.490226: [NET] Routine: handshake worker - stopped
2019-05-30 14:53:40.492883: [NET] Routine: handshake worker - stopped
2019-05-30 14:53:40.493355: [NET] Routine: decryption worker - stopped
2019-05-30 14:53:40.496960: [NET] Routine: encryption worker - stopped
2019-05-30 14:53:40.501805: [NET] Routine: encryption worker - stopped
2019-05-30 14:53:40.506044: [NET] Interface closed
2019-05-30 14:53:40.520051: [APP] Tunnel 'skittles' connection status changed to 'disconnected'
2019-05-30 14:53:40.520216: [APP] startActivation: Entering (tunnel: skittles)
2019-05-30 14:53:40.523432: [APP] startActivation: Starting tunnel
2019-05-30 14:53:40.528092: [APP] startActivation: Success
2019-05-30 14:53:40.536410: [APP] Tunnel 'skittles' connection status changed to 'connecting'
2019-05-30 14:53:40.620031: [NET] App version: 0.0.20190319 (1); Go backend version: 0.0.20181222
2019-05-30 14:53:40.620386: [NET] Starting tunnel from the app
2019-05-30 14:53:41.118450: [NET] Tunnel interface is utun2
2019-05-30 14:53:41.119540: [NET] DNS64: mapped 69.131.49.158 to itself.
2019-05-30 14:53:41.120312: [NET] Attaching to interface
2019-05-30 14:53:41.123298: [NET] Routine: encryption worker - started
2019-05-30 14:53:41.127257: [NET] Routine: event worker - started
2019-05-30 14:53:41.132262: [NET] Routine: decryption worker - started
2019-05-30 14:53:41.137259: [NET] Routine: handshake worker - started
2019-05-30 14:53:41.142257: [NET] Routine: TUN reader - started
2019-05-30 14:53:41.147319: [NET] Routine: decryption worker - started
2019-05-30 14:53:41.152262: [NET] Routine: encryption worker - started
2019-05-30 14:53:41.154513: [NET] Routine: handshake worker - started
2019-05-30 14:53:41.159432: [NET] UAPI: Updating private key
2019-05-30 14:53:41.162956: [NET] UAPI: Removing all peers
2019-05-30 14:53:41.165293: [NET] UAPI: Transition to peer configuration
2019-05-30 14:53:41.168368: [NET] peer(AAAA…AAAA) - UAPI: Updating endpoint
2019-05-30 14:53:41.171341: [NET] peer(AAAA…AAAA) - UAPI: Updating persistent keepalive interval
2019-05-30 14:53:41.174344: [NET] peer(AAAA…AAAA) - UAPI: Removing all allowedips
2019-05-30 14:53:41.177291: [NET] peer(AAAA…AAAA) - UAPI: Adding allowedip
2019-05-30 14:53:41.178520: [NET] Routine: receive incoming IPv4 - started
2019-05-30 14:53:41.181481: [NET] Routine: receive incoming IPv6 - started
2019-05-30 14:53:41.186481: [NET] UDP bind has been updated
2019-05-30 14:53:41.190383: [NET] Device started
2019-05-30 14:53:41.198542: [APP] Tunnel 'skittles' connection status changed to 'connected'
2019-05-30 14:53:41.207024: [NET] UAPI: Processing get operation
2019-05-30 14:53:42.203591: [NET] UAPI: Processing get operation
2019-05-30 14:53:43.203400: [NET] UAPI: Processing get operation
2019-05-30 14:53:44.202770: [NET] UAPI: Processing get operation
2019-05-30 15:01:39.739007: [APP] Status update notification timeout for tunnel 'skittles'. Tunnel status is now 'connected'.
2019-05-30 15:01:39.785087: [NET] UAPI: Processing get operation
2019-05-30 15:01:40.300533: [NET] UAPI: Processing get operation
2019-05-30 15:01:41.285998: [NET] UAPI: Processing get operation
2019-05-30 15:01:41.312810: [APP] startDeactivation: Tunnel: skittles
2019-05-30 15:01:41.321100: [APP] Tunnel 'skittles' connection status changed to 'disconnecting'
2019-05-30 15:01:41.734373: [NET] Stopping tunnel
2019-05-30 15:01:41.734604: [NET] Device closing
2019-05-30 15:01:41.737648: [NET] Routine: event worker - stopped
2019-05-30 15:01:41.741995: [NET] Routine: TUN reader - stopped
2019-05-30 15:01:41.747036: [NET] Routine: receive incoming IPv4 - stopped
2019-05-30 15:01:41.751849: [NET] Routine: receive incoming IPv6 - stopped
2019-05-30 15:01:41.757161: [NET] Routine: decryption worker - stopped
2019-05-30 15:01:41.758924: [NET] Routine: encryption worker - stopped
2019-05-30 15:01:41.764064: [NET] Routine: handshake worker - stopped
2019-05-30 15:01:41.766851: [NET] Routine: decryption worker - stopped
2019-05-30 15:01:41.769993: [NET] Routine: handshake worker - stopped
2019-05-30 15:01:41.772981: [NET] Routine: encryption worker - stopped
2019-05-30 15:01:41.775903: [NET] Interface closed
2019-05-30 15:01:41.784652: [APP] Tunnel 'skittles' connection status changed to 'disconnected'
2019-05-30 15:02:09.207652: [APP] Tunnel 'skittles' connection status changed to 'invalid'
2019-05-30 15:03:17.270406: [APP] startActivation: Entering (tunnel: skittles)
2019-05-30 15:03:17.271613: [APP] startActivation: Starting tunnel
2019-05-30 15:03:17.275506: [APP] startActivation: Success
2019-05-30 15:03:17.285317: [APP] Tunnel 'skittles' connection status changed to 'connecting'
2019-05-30 15:03:17.414544: [NET] App version: 0.0.20190319 (1); Go backend version: 0.0.20181222
2019-05-30 15:03:17.414855: [NET] Starting tunnel from the app
2019-05-30 15:03:22.276331: [APP] Status update notification timeout for tunnel 'skittles'. Tunnel status is now 'connecting'.
2019-05-30 15:03:22.666134: [NET] Tunnel interface is utun2
2019-05-30 15:03:22.667046: [NET] DNS64: mapped 69.131.49.158 to itself.
2019-05-30 15:03:22.669630: [NET] Attaching to interface
2019-05-30 15:03:22.674706: [NET] Routine: encryption worker - started
2019-05-30 15:03:22.678704: [NET] Routine: event worker - started
2019-05-30 15:03:22.680803: [NET] Routine: decryption worker - started
2019-05-30 15:03:22.685800: [NET] Routine: handshake worker - started
2019-05-30 15:03:22.688737: [NET] Routine: TUN reader - started
2019-05-30 15:03:22.691850: [NET] Routine: decryption worker - started
2019-05-30 15:03:22.694775: [NET] Routine: encryption worker - started
2019-05-30 15:03:22.697739: [NET] Routine: handshake worker - started
2019-05-30 15:03:22.700799: [NET] UAPI: Updating private key
2019-05-30 15:03:22.704220: [NET] UAPI: Removing all peers
2019-05-30 15:03:22.704386: [NET] UAPI: Transition to peer configuration
2019-05-30 15:03:22.707856: [NET] peer(AAAA…AAAA) - UAPI: Updating endpoint
2019-05-30 15:03:22.712867: [NET] peer(AAAA…AAAA) - UAPI: Updating persistent keepalive interval
2019-05-30 15:03:22.718221: [NET] Routine: receive incoming IPv6 - started
2019-05-30 15:03:22.722887: [NET] Routine: receive incoming IPv4 - started
2019-05-30 15:03:22.727839: [NET] UDP bind has been updated
2019-05-30 15:03:22.732841: [NET] Device started
2019-05-30 15:03:22.740126: [APP] Tunnel 'skittles' connection status changed to 'connected'
2019-05-30 15:03:22.745188: [NET] UAPI: Processing get operation
2019-05-30 15:03:23.743029: [NET] UAPI: Processing get operation
2019-05-30 15:03:24.742968: [NET] UAPI: Processing get operation
2019-05-30 15:03:25.742815: [NET] UAPI: Processing get operation
2019-05-30 15:03:26.742978: [NET] UAPI: Processing get operation
2019-05-30 15:03:27.276378: [APP] Status update notification timeout for tunnel 'skittles'. Tunnel status is now 'connected'.
2019-05-30 15:03:27.278175: [NET] UAPI: Processing get operation
2019-05-30 15:03:28.279588: [NET] UAPI: Processing get operation
2019-05-30 15:03:29.279341: [NET] UAPI: Processing get operation
2019-05-30 15:03:30.279411: [NET] UAPI: Processing get operation
2019-05-30 15:03:31.279499: [NET] UAPI: Processing get operation
2019-05-30 15:03:32.279276: [NET] UAPI: Processing get operation
2019-05-30 15:03:33.279464: [NET] UAPI: Processing get operation
2019-05-30 15:03:34.279410: [NET] UAPI: Processing get operation
2019-05-30 15:03:35.279496: [NET] UAPI: Processing get operation
2019-05-30 15:03:36.279480: [NET] UAPI: Processing get operation
2019-05-30 15:03:37.279447: [NET] UAPI: Processing get operation
2019-05-30 15:03:38.279342: [NET] UAPI: Processing get operation
2019-05-30 15:03:39.279631: [NET] UAPI: Processing get operation
2019-05-30 15:03:40.279366: [NET] UAPI: Processing get operation
2019-05-30 15:03:41.279377: [NET] UAPI: Processing get operation
2019-05-30 15:03:42.279374: [NET] UAPI: Processing get operation
2019-05-30 15:03:43.279349: [NET] UAPI: Processing get operation
2019-05-30 15:03:44.279174: [NET] UAPI: Processing get operation
2019-05-30 15:03:45.279301: [NET] UAPI: Processing get operation
2019-05-30 15:03:46.279288: [NET] UAPI: Processing get operation
2019-05-30 15:03:47.279306: [NET] UAPI: Processing get operation
2019-05-30 15:03:48.279114: [NET] UAPI: Processing get operation
2019-05-30 15:03:49.279280: [NET] UAPI: Processing get operation
2019-05-30 15:03:50.279313: [NET] UAPI: Processing get operation
2019-05-30 15:03:51.279367: [NET] UAPI: Processing get operation
2019-05-30 15:03:52.279270: [NET] UAPI: Processing get operation
2019-05-30 15:03:53.279235: [NET] UAPI: Processing get operation
2019-05-30 15:03:54.279212: [NET] UAPI: Processing get operation
2019-05-30 15:03:55.279236: [NET] UAPI: Processing get operation
2019-05-30 15:03:56.279205: [NET] UAPI: Processing get operation
2019-05-30 15:03:57.281571: [NET] UAPI: Processing get operation
2019-05-30 15:03:58.279092: [NET] UAPI: Processing get operation
2019-05-30 15:03:59.279183: [NET] UAPI: Processing get operation
2019-05-30 15:04:00.279192: [NET] UAPI: Processing get operation
2019-05-30 15:04:01.279243: [NET] UAPI: Processing get operation
2019-05-30 15:04:02.279236: [NET] UAPI: Processing get operation
2019-05-30 15:04:03.278853: [NET] UAPI: Processing get operation
2019-05-30 15:04:04.279189: [NET] UAPI: Processing get operation
2019-05-30 15:04:05.279148: [NET] UAPI: Processing get operation
trendy
May 30, 2019, 10:15pm
19
Can be lan, if you plan to use it for remote management.
Yes there must be and it is already part of the config I shared with you.
If OpenWrt runs dnsmasq then you can use 192.168.1.1
1 Like
it brings about another question then
trendy
May 30, 2019, 10:22pm
21
Both server and clients generate a pri-pub pair of keys.