Hello guys,
Appreciate your help
instead of screenshots, please post your config in text form...
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/firewall
root@Router:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fde3:d3f0:9ebc::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '1.1.1.1'
list dns '1.0.0.1'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option peerdns '0'
list dns '1.1.1.1'
list dns '1.0.0.1'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'guest'
option proto 'static'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
config interface 'WG0'
option proto 'wireguard'
option peerdns '0'
option mtu '1280'
option private_key 'U'
list addresses '172.16.0.2/32'
list addresses 'fd01:5ca1:ab1e:849e:158f:6b7d:d692:3965/128'
list dns '1.1.1.1'
list dns '1.0.0.1'
list dns '2606:4700:4700::1111'
list dns '2606:4700:4700::1'
config wireguard_WG0
option route_allowed_ips '1'
option endpoint_port '2408'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option description 'cloudflare_warp'
option endpoint_host 'engage.cloudflareclient.com'
option public_key 'b'
option persistent_keepalive '25'
config interface 'wg1'
option proto 'wireguard'
option private_key 'w'
option listen_port '51821'
list addresses '192.168.9.1/24'
list addresses 'fdf1:7610:d152:3a9c::1/64'
config wireguard_wg1 'wgclient'
option preshared_key 'a'
list allowed_ips '192.168.9.0/24'
list allowed_ips 'fdf1:7610:d152:3a9c::1/64'
option description 'home'
option public_key 'jEjf974eLz4fHZ6ovW5g5C/Oj6W9Wp8lVd7oe3TmAiU='
option private_key 'A'
root@Router:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'guest'
option output 'ACCEPT'
option input 'REJECT'
option forward 'REJECT'
list network 'guest'
config rule
option name 'Guest DNS'
option src 'guest'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Guest DHCP'
list proto 'udp'
option src 'guest'
option dest_port '67-68'
option target 'ACCEPT'
config zone
option name 'wgzone'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'WG0'
option forward 'REJECT'
option input 'REJECT'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
option forward 'REJECT'
option input 'REJECT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'WOL'
option src_dport '9'
option dest_ip '192.168.1.233'
option dest_port '9'
option src 'lan'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'WOL2'
option src 'wan'
option src_dport '9'
option dest_ip '192.168.1.233'
option dest_port '9'
config redirect
option dest 'lan'
option target 'DNAT'
option name '8080'
list proto 'tcp'
option src 'wgzone'
option src_dport '8080'
option dest_ip '192.168.1.108'
option dest_port '8080'
option enabled '0'
config forwarding
option src 'lan'
option dest 'wgzone'
config forwarding
option src 'guest'
option dest 'wgzone'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'http'
list proto 'tcp'
option src 'wan'
option src_dport '80'
option enabled '0'
config rule
list proto 'tcp'
option src 'wan'
option src_port '80'
option dest_port '80'
option target 'ACCEPT'
option name 'Allow-HTTP'
option enabled '0'
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option dest_port '51821'
option proto 'udp'
option target 'ACCEPT'
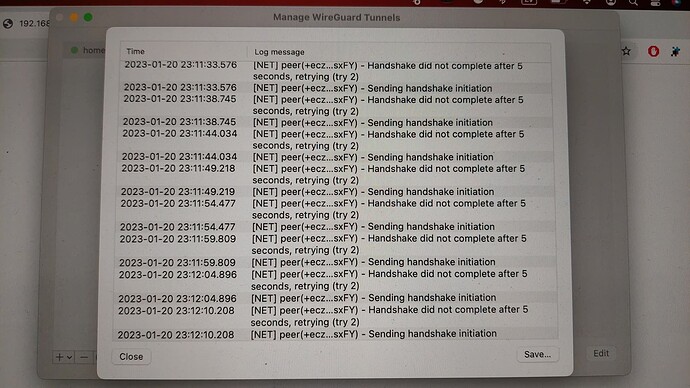
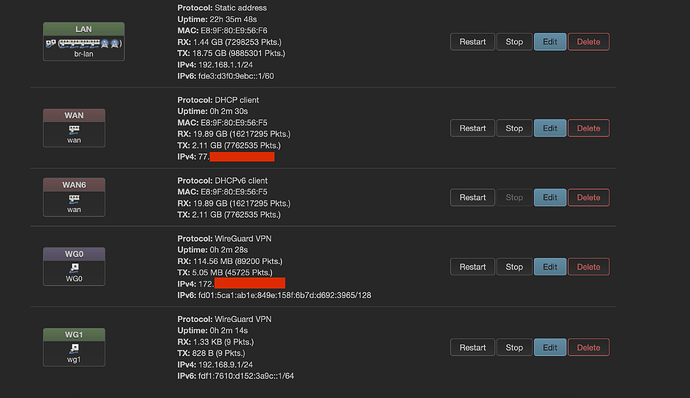
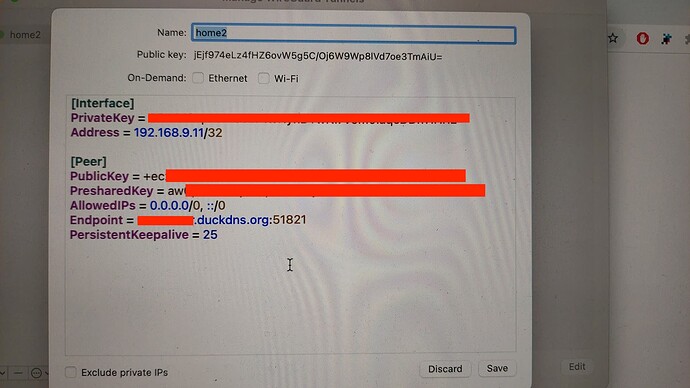
This needs a valid host address with a /32. For example, 192.168.9.11/32 to match the screenshot you've provided.
If your other Wireguard tunnel is running, you won't get a response back because everything gets routed out through that. So you'll need to use policy based routing. But before you start that process, turn off your other VPN and then see if you can connect.
1 Like
what would be the easiest way to switch of VPN client (on router) ?
click the stop button next to the wg0 interface. you may need to restart the wan interface after that.
yes, by directly specifying client ip did the trick.
great!
From here, policy based routing is how you can keep your main outbound VPN going while properly handling the inbound one.
The old vpn-policy-routing thread grew too big and contains a lot of outdated information, now that pbr is available, so I've decided to start a new thread.
pbr is a next generation service supporting split-tunneling for multiple types of VPN tunnels (Openconnect, OpenVPN, PPTP and Wireguard), allowing you to create policies to use a designated VPN tunnel or WAN as a gateway. More information (requirements, full features list, etc.) on the service is available in the README .
Differences bet…
as a local address I guess will need to use 192.168.9.1/24 & interface wan ?
I'm not an expert on PBR, but that sounds right.
1 Like
Still not able to launch it and most likely due to below note. However, I think this is for another topic discussion. Thank you for your help!
If your router is set to use default routing via VPN tunnel and the WAN-targeting policies do not work, you need to stop your VPN tunnel first and ensure that you still have internet connection. If your router is set up to use the default routing via VPN tunnel and when you stop the VPN tunnel you have no internet connection, this package can’t help you. You first need to make sure that you do have internet connection when the VPN tunnel is stopped.
stangri
January 21, 2023, 9:31pm
13
If your default routing out is a VPN tunnel, the only viable solution for a VPN server running on your router known to me is an OpenVPN server in TCP mode. Otherwise, pbr would not be able to properly route VPN server packets (as wg and OpenVPN by default use UDP).
PS. The same can be gathered from the README that @psherman linked earlier.
1 Like
system
January 31, 2023, 9:32pm
14
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.