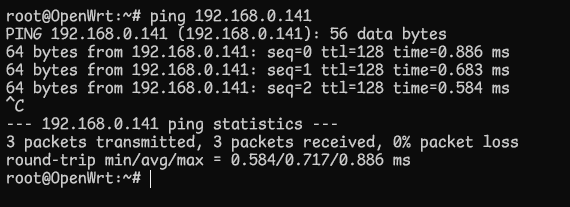
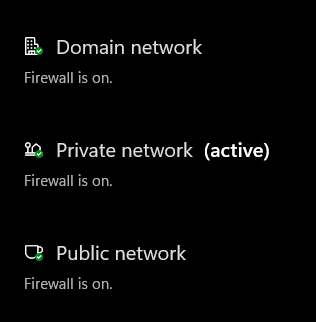
Hello, I have an issue with my Wireguard server which I had just setup recently. I can't seem to ping my LAN devices after connecting my mobile device through Wireguard.
I did a bit of research here and people suggested either going with deploying static routes or enabling masquerading on the LAN -> WAN zone.
I had a doubt regarding if it's safe and wouldn't have an issue to enable masquerading as the default value was unticked. Is there any advantage setting up static routes instead of masquerading or should I just simplify everything by ticking the masquerade option in the LAN -> WAN zone?
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/firewall
wg show
And please also show us your config from the remote peer device.
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.150",
"hostname": "OpenWrt",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "ASUS RT-AX53U",
"board_name": "asus,rt-ax53u",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.3",
"revision": "r23809-234f1a2efa",
"target": "ramips/mt7621",
"description": "OpenWrt 23.05.3 r23809-234f1a2efa"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fdb3:2a6a:9dd4::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.0.1'
option ip6assign '64'
list ip6class 'wan6'
config interface 'wan'
option device 'wan'
option proto 'pppoe'
option username ''
option ipv6 '1'
option password ''
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option sourcefilter '0'
config interface 'wg0'
option proto 'wireguard'
option private_key ''
option listen_port '443'
list addresses '10.14.0.1/24'
list addresses '2001:db8::/48'
config wireguard_wg0
option description 'phone'
option public_key '7+Q'
option persistent_keepalive '25'
list allowed_ips '10.14.0.2/32'
list allowed_ips '2001:db8:0:1::/64'
option route_allowed_ips '1'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option flow_offloading '1'
option flow_offloading_hw '1'
option synflood_protect '1'
option drop_invalid '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg0'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Soulseek'
list proto 'tcp'
option src 'wan'
option src_dport '58378-58379'
option dest_ip '192.168.0.141'
option dest_port '58378-58379'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Plex'
list proto 'tcp'
option src 'wan'
option src_dport '50648'
option dest_ip '192.168.0.141'
option dest_port '32400'
config rule
option name 'Allow-Nginx+Wireguard'
option src 'wan'
option dest_port '443'
option target 'ACCEPT'
option family 'ipv6'
list proto 'tcp'
list proto 'udp'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Nginx+Wireguard'
option src 'wan'
option src_dport '443'
option dest_ip '192.168.0.1'
option dest_port '443'
list proto 'tcp'
list proto 'udp'
config rule
option name 'Allow-Intercept_DNS'
option target 'MARK'
option set_mark '1'
option start_time '05:00:00'
option stop_time '06:00:00'
option src 'lan'
option dest '*'
option dest_port '53'
list src_mac ''
config redirect
option target 'DNAT'
option name 'Intercept-DNS'
option src 'lan'
option src_dport '53'
option mark '1'
list src_mac ''
option dest_ip '213.42.20.20'
config nat
option name 'nat6'
option family 'ipv6'
list proto 'all'
option src 'wan'
option src_ip '2001:db8::/48'
option target 'MASQUERADE'
root@OpenWrt:~# wg show
interface: wg0
public key: /8J
private key: (hidden)
listening port: 443
peer: 7+Q
endpoint: 192.168.0.128:45950
allowed ips: 10.14.0.2/32, 2001:db8:0:1::/64
latest handshake: 1 minute, 2 seconds ago
transfer: 745.35 KiB received, 3.24 MiB sent
persistent keepalive: every 25 seconds
root@OpenWrt:~#
[Interface]
Address = 10.14.0.2/32, 2001:db8:0:1::1/64
DNS = 192.168.0.1
PrivateKey =
[Peer]
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = :443
PersistentKeepalive = 25
PublicKey = /8J
krazeh
June 26, 2024, 5:07pm
4
Is the OpenWRT router behind another device or does it connect directly to the internet? Have you checked the LAN devices for local firewalls that may be blocking pings?
Its behind an ONT, also no my LAN devices accepts ping. When I enable masquerading I can ping my LAN devices through Wireguard but I wanted to know if it's safe to do so.
Based on this post the author seems to say it's a nuance of some sort?
It appears your goal is to setup a VPN endpoint (server) at your home so that you can connect remotely to use your home network resources and/or the internet through your home connection. Further, the OpenWrt router that will have the VPN endpoint running sits behind another router which is responsible for your main LAN. If that is a correct interpretation, there are two ways to accomplish this goal:
if your main router supports adding static routes, you can setup your OpenWrt router such that…
What operating systems are on the target systems (i.e. the ones that you are trying to ping from wireguard)?
By default, windows will not accept pings or connection requests from a different subnet. Check the windows firewall settings (maybe turn it off entirely for a test).
I have configured it to accept ping.
Yes, it may accept ping from the same subnet , but it very likely won't from a different subnet.
Turn off the windows firewall and then test.
3 Likes
Okay yeah your right, this doesn't seem to be an issue of static routing or masquerading... I assume I need to configure my Private firewall to accept ping from Public firewall?
egc
June 26, 2024, 5:29pm
12
Azuriye:
2001:db8::/48
You cannot use a GUA address which is not yours
You can use an ULA address though:
https://en.m.wikipedia.org/wiki/Unique_local_address .
I agree with former speakers look at the firewall of your lan clients.
I was directed to use GUA address when setting up IPv6 access for Wireguard?
Don't use ULAs as @mikma said most endpoint OS don't consider a ULA valid to originate a connection to a GUA on the v6 Internet.
To NAT you need to issue the LAN clients local IPs which look like GUAs but are never going to actually exist on the Internet, as trying to reach a site that has a public IP in the same subnet as your LAN IP will not route properly.
There is no officially reserved block of GUAs for this purpose. I have used "documentation" block this way: 2001:db8:<16 random bits>::…
egc
June 26, 2024, 6:00pm
14
The address does not leave your router so you should use an ULA address, alternatively you can use one of your own GUA addresses in which case you do not have to NAT6
Regarding ULA addresses I assume I need to change both my wg interface and the AllowedIPs for my peers to be an ULA address?
Also wont using my own GUA address be a security concern as I am exposing my IPv6 address which others can ping it?
egc
June 26, 2024, 6:15pm
16
Correct you have to change client and server.
If you want to use one of your own GUA /64 subnets you do not have to NAT6 which is an advantage speedwise, if you think that natting is securing your network, which is debatable, than just use an ULA addres, it is at least the easier way to setup
1 Like
system
July 6, 2024, 6:15pm
17
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.